Achieved 100% protection in 2024
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Written by: Moar Huli, Eran Yosef, & Amit Martsiano
WastedLocker is a ransomware operated by a malware exploitation gang, commonly known as the ‘Evil Corp gang.’ The same gang that is associated with Dridex and BitPaymer.
WastedLocker does not share the same traits as other malware variants from ‘Evil Corp gang’ however it has kept the ability to add specific modules for different targets
The attacks performed using WastedLocker are targeted at US based organizations.
It is suspected that during the first penetration attempt, an assessment of active defenses is made, and the next attempt is specifically designed to circumvent the existing security software and other perimeter protection.
The ransomware name is derived from the filename it creates, which includes an abbreviation of the victim’s name and the string “wasted.”
For each encrypted file, the attackers create a separate file that contains the ransomware note. The ransom note has the same name as the associated file with the addition of “_info.”
This is part of an extensive series of guides about Ransomware Protection
These are the alerts that were triggered when we ran the ransomware:
1. Malicious Process Command [ADT Mechanism]:
This alert trigger when Cynet detects a CMD process that executes a command that contains suspicious arguments or is associated with malicious patterns.
In this case, an attempt to delete vssadmin shadow copies triggered an alert. Shadow copies are one of the most valuable targets of ransomware.
2. Unauthorized Memory Access Attempt [Driver Mechanism]:
This alert informs the customer that there was an attempt by a particular process to access a forbidden memory location of another process. The alert also describes what permissions the accessing process requested and permissions that Cynet granted the process to use.
In our case, the ransomware tried to access the memory of vssadmin.exe to executes this command: “C:\WINDOWS\system32\vssadmin.exe Delete Shadows /All /Quiet”
This is a standard ransomware activity, in which the malicious actors are trying to delete the shadow copies of the infected machine.
3. Ransomware Heuristic [ADT Mechanism]:
This alert triggers when Cynet detects suspicious behavior, which can be associated with Ransomware (such as changing file extensions to “.Lock”).
Once the file starts to encrypt the files with their extension [ “.d2lwasted_info”] – A ransomware heuristic alert is triggered.
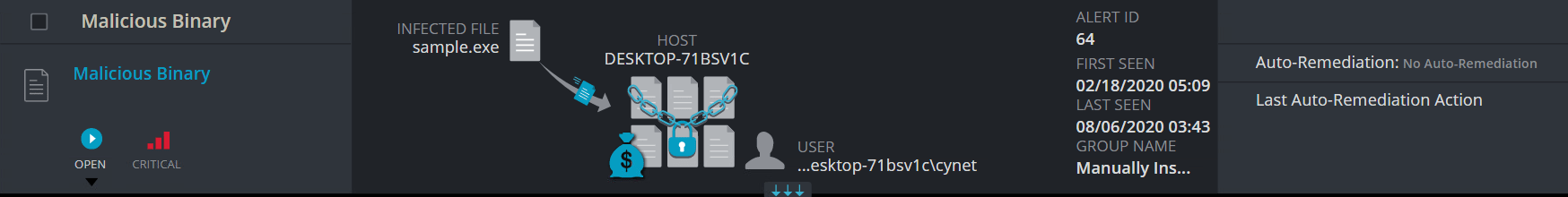
4. Malicious Binary [ADT Mechanism]:
This alert trigger when Cynet detects a file that is flagged as malicious in Cynet’s EPS (endpoint scanner) built-in threat intelligence database. This database contains only critical IoCs (such as IOCs of ransomware, hacking tools, etc.).
Once we executed the ransomware – A Malicious Binary alert is triggered for the malicious file [sample.exe]:
5. File incidents (“Trojan!gen”, “CoinMiner,” PUA! Getn, etc.):
The Cynet agent scans for binary files on protected endpoints. Every file is analyzed by Cynet mechanisms and is given a score. If the file is flagged as “suspicious” (according to pre-defined patterns), the file’s metadata is sent to the Cynet CyOps team. The CyOps analysts manually classify the files after analyzing the file’s metadata.
After execution, the ransomware created several executables and used legitimate Windows programs:
The ransomware note:
The extension of the encrypted files is “.d2lwasted_info”:
The Cynet CyOps is available to clients for any issues 24/7, questions, or comments related to Cynet 360. For additional information, you may contact us directly at:
Phone (US): +1-347-474-0048
Phone (EU): +44-203-290-9051
Phone (IL): +972-72-336-9736
CyOps Email: [email protected]
Search results for: