January 28, 2020
Last Updated:
September 12, 2024
FTCode is a type of ransomware that spreads itself via spam emails, and is able to execute its PowerShell-based malicious payload in memory only, without downloading any files to disk. It was first seen in the wild in 2013, but is now a much more serious network threat because most current Windows workstations have PowerShell installed by default.
This is part of our series of articles about Ransomware protection.
Infected by FTCode ransomware?
Cynet is a trusted partner that deploys powerful endpoint detection and response (EDR) security
software on your endpoints, and can help defend, mitigate and eradicate against a wide range of known and zero-day threats, including ransomware like FTCode, and advanced persistent threats. Cynet provides CyOps, an outsourced incident response team on call 24/7/365 to respond to critical incidents quickly and effectively.
What is FTCode?
FTCode is a strain of ransomware, designed to encrypt data and force victims to pay a ransom to release it. It is fully written in PowerShell, meaning that it can encrypt files on a Windows device without downloading any other components. FTCode loads its executable code only into memory, without saving it to disk, to prevent detection by antivirus.
The first appearance of FTCode was probably in 2013, and it was originally identified by Sophos. However, at the time it did not pose a serious risk because PowerShell is only installed by default from Windows 7 onwards. Today almost all Windows machines have at least Windows 7, and so PowerShell-based malware like FTCode poses a much bigger risk.
FTCode Distribution Method
The FTCode ransomware is primarily distributed via spam emails containing an infected Word template in Italian. The user needs to open the attachment and disable Protected View mode, and then a malicious macro executes which runs FTCode PowerShell code.
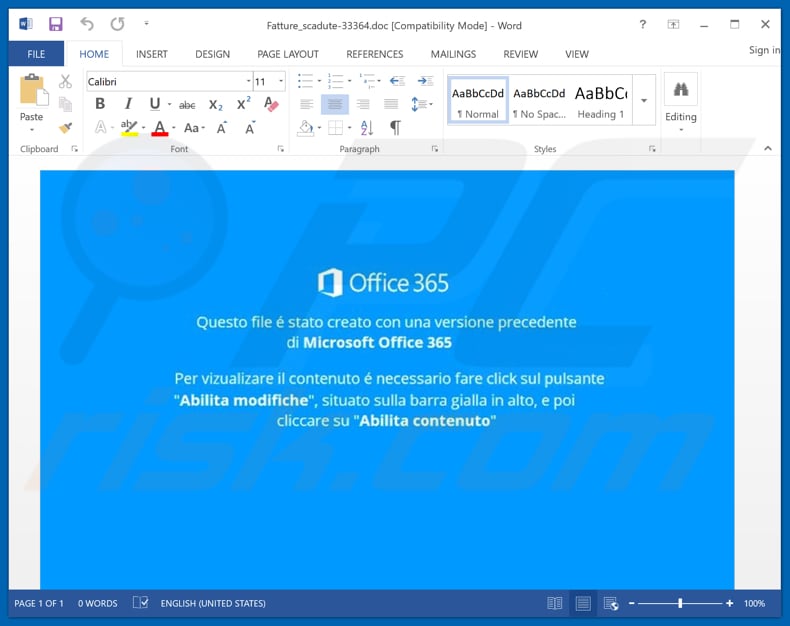
Source:PC Risk
In my experience, here are tips that can help you better defend against FTCode ransomware and other PowerShell-based threats:
- Enable script block logging in PowerShell
Script block logging helps capture malicious scripts in the Windows event logs, even those executed only in memory. Set up centralized log collection to analyze this data in real-time for early detection of threats.
- Implement application whitelisting
Whitelist only trusted applications and scripts using tools like Windows AppLocker or Software Restriction Policies (SRP). This can prevent unauthorized PowerShell scripts, like FTCode’s, from executing.
- Monitor abnormal network activity
FTCode communicates with its C2 server in unencrypted base64. Set up network monitoring tools to inspect outbound traffic for suspicious HTTP requests or base64 encoded strings. This can allow detection of ongoing infections and interception of encryption keys.
- Employ honeytokens for early detection
Deploy fake files or documents with tempting names, such as “Payroll_2023.xlsx,” and monitor access to them. FTCode is likely to target these files early in the attack, providing a valuable alert point.
- Monitor endpoint process creation events
FTCode uses scheduled tasks and creates shortcuts for persistence. Use endpoint detection tools to continuously monitor for suspicious process creation events, such as unusual scheduled tasks or unknown startup programs.
Eyal Gruner is the Co-Founder and CEO of Cynet. He is also Co-Founder and former CEO of BugSec, Israel’s leading cyber consultancy, and Versafe, acquired by F5 Networks. Gruner began his career at age 15 by hacking into his bank’s ATM to show the weakness of their security and has been recognized in Google’s security Hall of Fame.
How Does the FTCode Malware Work?
Once a user is tricked into opening the infected Word template, and the malicious macro executes, the following steps occur.
This discussion is based on research from Certego and represents the behavior of version 930.5 of the malware, future versions may exhibit different behavior.
- The macro triggers the DownloadString function, which loads the PowerShell code into memory, without saving it to disk. It uses the PowerShell iex (invoke expression) command to execute the malicious code.
- FTCode is now running, it performs a GET request to download JasperLoader, a backdoor that will download additional payloads. JasperLoader is a Visual Basic script that is saved to C:\Users\Public\Libraries\WindowsIndexingService.vbs.
- It creates a shortcut file called WindowsIndexingService.lnk in the user’s startup folder, and creates a scheduled task called WindowsApplicationService, in order to run the shortcut after every reboot.
- When the shortcut runs, it first checks for the presence of files with extension .FTCode, and if they are present, it assumes the computer has already been attacked, and exits.
Note:
This creates a way to prevent FTCode from executing—creating a few files with .FTCode extension somewhere on the machine, with any content.
- It generates a globally unique identifier and a password with 50 characters including at least four non-alphanumeric characters. A hardcoded RSA public key is used to encrypt the password, and it can be deciphered only with the attacker’s private key. However, when communicating with the command and control server, FTCode sends an unencrypted version of the password in base64 encoding.
Note:
This means that in current variants of FTCode, monitoring communication with the attacker’s server can yield the password that can decode the user’s encrypted files.
- FTCode performs a POST request to its server and transmits the version number, PowerShell version, the victim’s unique ID and the password encoded in base64.
- It runs the following PowerShell commands that prevent the user from restoring their encrypted files:
bcdedit /set exgdccaxjz bootstatuspolicy ignoreallfailures
bcdedit /set exgdccaxjz recoveryenabled no
wbadmin delete catalog -quiet
wbadmin delete systemstatebackup
wbadmin delete backup
vssadmin delete shadows /all /quiet
- It checks for active disk drives and looks for files with common extensions like .mp4, .wav, .csv, .xls, etc. FTCode starts by encrypting the first bytes of each file using Rijndael symmetric key encryption, and appends the extension .FTCode.
- FTCode now creates the ransom note as a file named READ_ME_NOW.htm in all folders that contain encrypted files.
All-in-One FTCode Protection with Cynet
Cynet 360 is an Advanced Threat Detection and Response platform that provides protection against ransomware like FTCode and other threats, including zero-day attacks, advanced persistent threats (APT), and trojans that can evade signature-based security measures.
Cynet provides a multi-layered approach to stop ransomware from executing and encrypting your data:
- Pre-download —applies multiple mechanisms against exploits and fileless malware, which typically serves as a delivery method for the ransomware payload, preventing it from getting to the endpoint in the first place.
- Pre-execution prevention —applies machine-learning-based static analysis to identify ransomware patterns in binary files before they are executed.
- In runtime —employs behavioral analysis to identify ransomware-like behavior, and kill a process if it exhibits such behavior.
- Threat intelligence —uses a live feed comprising over 30 threat intelligence feeds to identify known ransomware.
- Fuzzy Hash detection— employs a fuzzy hashing detection mechanism to detect automated variants of known ransomware.
- Sandbox —runs any loaded file in a sandbox and blocks execution upon identification of ransomware-like behavior.
- Decoy files —plants decoy data files on the hosts and applies a mechanism to ensure these are the first to be encrypted in a case of ransomware. Once Cynet detects that these files are going through encryption it kills the ransomware process.
- Propagation blocking —identifies the networking activity signature generated by hosts when ransomware is auto-propagating, and isolates the hosts from the network.
Learn more about Cynet’s Next-Generation Antivirus (NGAV) Solution.
How would you rate this article?
