Cynet Security Critical Update – SolarWinds Supply-Chain Attack
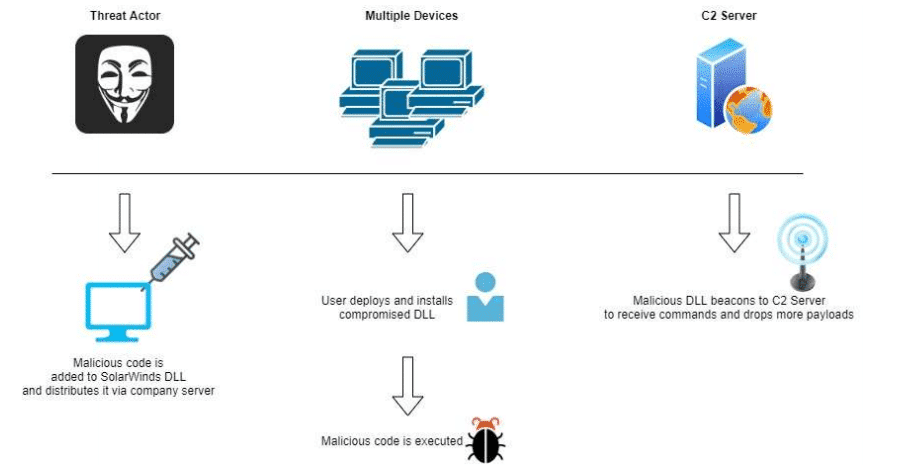
Last Sunday, December 13th, the IT industry in general, and the IT Security sector specifically were shocked to discover that many of them had been exposed to internal vulnerabilities for quite some time. This campaign started, according to current estimations, during early March 2020 when the first malicious SolarWinds Orion software version was distributed with an update of the Orion software released by SolarWinds. SolarWinds, of Austin, Texas, provides network monitoring and technical services to hundreds of thousands of organizations around the world. This attack, which was identified in the last few days as a “Supply Chain attack”, it began when malicious code was implanted into updates that were supplied by the producer of a popular software product called “Orion”, which is responsible for monitoring computer networks of businesses and government entities. The malware (tracked as SUNBURST by FireEye), provided elite hackers with remote access into an organization’s networks, eventually enabling them to exfiltrate information. SolarWinds’ network-monitoring capabilities, and centralized perspective of an organization’s networks, gave the attackers an unprecedented “God-view” into these networks. This large-scale cyber event was related to the FireEye breach, which was disclosed only a few days earlier indicating that nation-state hackers had broken into its network and stolen the
company’s own red-team and hacking tools. FireEye disclosed in a blog post that an investigation of a breach into their own network, had identified “a global campaign” targeting both government and the private sector, utilizing a piece of malware that was slipped into the SolarWinds software update. After discovering the backdoor, FireEye contacted SolarWinds and law enforcement agencies. So far, more than 25 entities have been targeted by the attack.
See the Forest through the Trees
As mentioned above, the Supply Chain attack began when a piece of malicious code was implanted into SolarWinds Orion updates, which were issued by the company. The hackers had been operating a highly sophisticated approach demonstrating nation-state capabilities with a low signature, preferring to steal credentials to perform lateral movements through networks and gain remote access while keeping their malware footprint very low. In order to cover their tracks, the attackers even created Command and Control servers on each victim’s country. To avoid being detected, the attackers used a variety of techniques utilizing
malware variants that had not been introduced before. This malware was loaded directly into the memory, leaving no evidence on the disk. In addition, the attackers created temporary files that, in turn would replace legitimate files on the victim’s system for malicious execution, which would then be replaced by legitimate ones. The same technique was used by temporarily modifying legitimate scheduled tasks to execute the malicious tools.
The FireEye Connection
FireEye is a cybersecurity company headquartered in Milpitas, California. Just one week ago, on December 8th, FireEye disclosed that nation-state hackers had broken into its network and stolen the company’s own hacking tools. The company said hackers used “novel techniques” to hack them with their own tool kit, which could be used in new attacks around the world. Once the investigation kicked in, they found that it was not just FireEye that was attacked, investigators discovered a vulnerability in a product made by one of its software providers— SolarWinds. Charles Carmakal Senior Vice President and Chief Technical Officer at Mandiant, FireEye’s incident response group was quoted saying: “We looked through 50,000 lines of source code, which we were able to determine there was a backdoor within SolarWinds,” After discovering the backdoor, FireEye contacted SolarWinds and law enforcement agencies.
The Russia connection
All current publications indicate that this attack was closely linked to Russia and its FSB. The tactics, techniques, and the procedures that were used by the hackers, seem to be related to the Russians providing indications of being highly disciplined hackers. These hackers only chose targets containing highly sensitive information, while knowing each time their tools were deployed and activated, their chances of being detected were increased. Cybersecurity experts said that the purpose of the months-long effort, appeared to be espionage and not profit or inflicting additional damage, apart from the embarrassment caused by the incident. Until now, no demands were made by the attackers or damage to or encryption of any of the victim’s services. Nation-state attacks have their cyber-espionage priorities, which might also include COVID-19 vaccine development. SolarWinds could have been used within U.S. agencies to protect data related to the COVID-19 vaccines being researched in different facilities.
US Government impact
SolarWinds’ customers include all five branches of the U.S. military, the State Department, NASA, the Pentagon, the Department of Justice and the White House, the National Security Agency, along with the top U.S. telecommunications, and accounting firms. SolarWinds declared that up to 33,000 Orion customers might have been affected, but it seems that only less than 18,000 had installed the infected update earlier this year. U.S. authorities acknowledged that Federal agencies were affected by the breach on Sunday, December 13th, providing few details. The Cybersecurity and Infrastructure Security Agency, known as CISA, declared that the SolarWinds software had been compromised and should be deleted from any system using it. FireEye has confirmed infections in North America, Europe, Asia, and the Middle East, including in the health care and oil and gas industries. The national cybersecurity agencies of Britain and Ireland also issued similar alerts. Members of Congress have pressed the US government for additional information, saying: “If reports are true and state-sponsored hackers successfully snuck malware-riddled software into scores of Federal government systems, our country has suffered a massive national security failure that could have ramifications for years to come”. If indeed it was executed by a foreign government, and the U.S. has the proof, then it becomes a question of what to do about it. Some potential options would include imposing sanctions, expelling diplomats of the offending country, or filing criminal charges for cyber-espionage—steps that Washington and the European Union have already taken against Russia in the past.
Actions taken by Cynet
Cynet XDR has been working to analyze and enrich relevant samples and IOCs to mitigate this attack. We have already released relevant detections for the compromised software and the malicious backdoor, based on multiple detection vectors. We will continue to add additional IOCs as new ones emerge.
After Implementation of all IOC’s (SHA256, SSDEEP and others) to Cynet360 detection mechanisms, Cynet CyOps team had contacted multiple customers where Cynet detected the SUNBURST malware. Additional security endpoint protection recommendations:
– Isolate the vulnerable endpoint using the Cynet Dashboard, and ready for triage.
– Reset any passwords used in the SolarWinds platform, treat them as compromised passwords.
– Enable all detection and remediation mechanisms at Cynet 360 UI.