CyOps Lighthouse: Eternity Project
By Ronen Ahdut – Sr. CyOps Analyst
The Darknet is home to many underground hacking forums. In these forums, cybercriminals talk freely, sharing stories, tactics, success stories, and failures.Their discussions allow us to peek into the politics and ethics behind their recent activities.
CyOps Lighthouse aims to shed a light on those dark places. Apart from the underground forums, we will also provide information regarding ongoing ransomware groups’ publications and worthy mentions from the last month.
Eternity Project – The MaaS supermarket
The underground ecosystem offers multiple options for any desired malicious program, whether it is a stealer, ransomware, loader, or any other tool required for the threat actor’s operation.
Normally, those options would be separated, meaning that you will buy a stealer from one source but a loader from another.
The Eternity team publications started on forums around March of 2022 with their stealer, then evolved into the entire project.
Promising a “one stop shop” for threat actors, their team offers multiple services to buyers.
The Eternity team is slowly gaining a reputation (good and bad) and is active and responsive on underground forums.
Overview
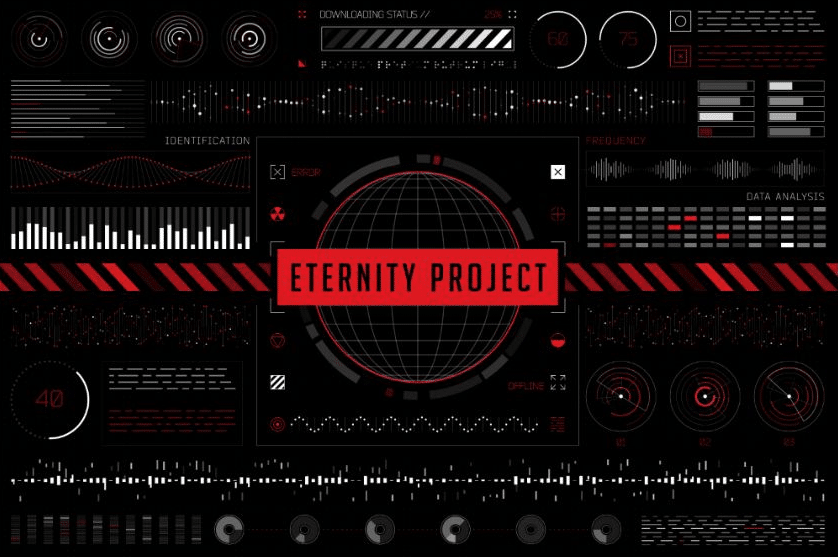
Eternity Project is a malware-as-a-service (MaaS) group and is offered on underground forums, on Eternity Telegram channel, and on their dedicated Tor onion.
The picture above is taken from the groups Telegram channel, and might be an old design, as the Tor website design is different:
The services are based on an annual fee, unlike most MaaS, which are offered at a few different rates.
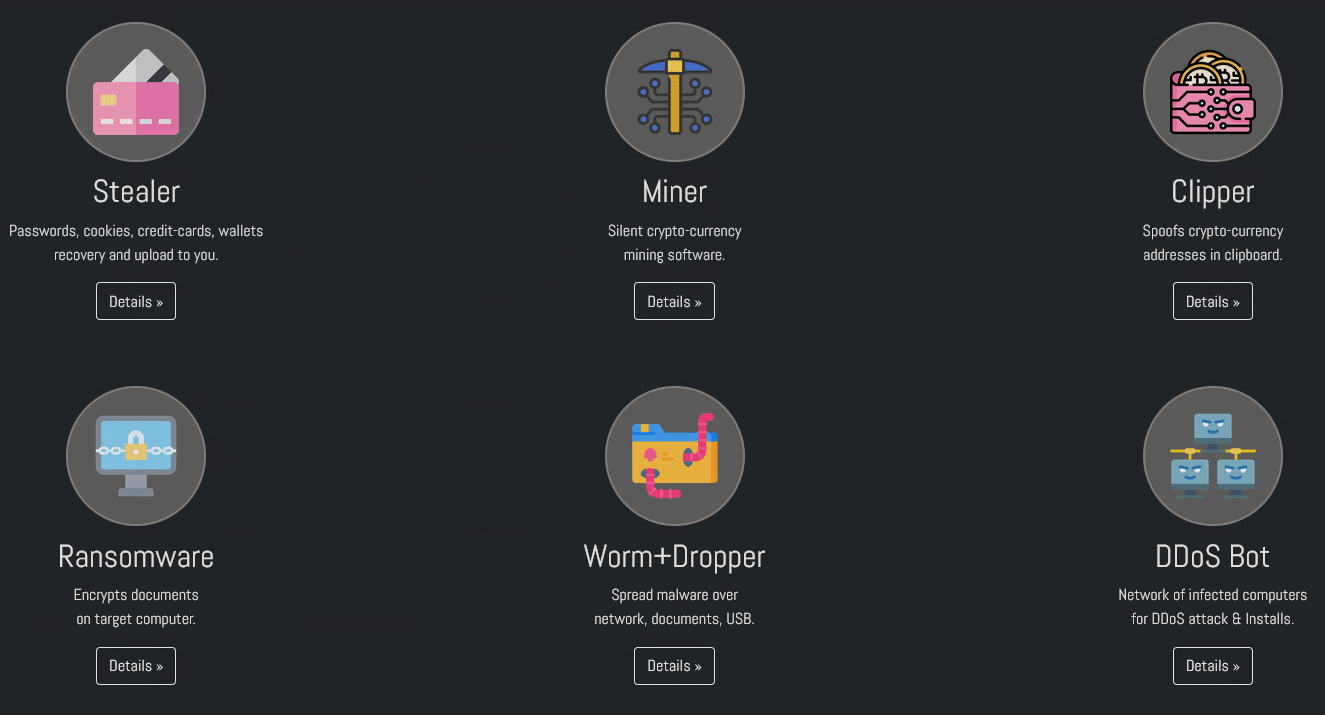
Prices and description of services, as seen on the Onion site:
- Stealer ($260) – is a malware classification which steals passwords, cookies, credit cards, crypto-wallets from a victim’s computer and sends them to you.
- Miner ($90) – is a malicious program using the resources of an infected computer for mining cryptocurrency.
- Clipper ($110) – is a malware classification which monitors the victim’s clipboard of an infected PC for cryptocurrency wallets and then replaces the copied address with the attacker’s desired destination.
- Ransomware ($470) – is a type of malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files until a ransom is paid.
- DDoS Bot – Project in development
While the team offers several services, their main publications to underground forums are focused on the stealer. This is because publishing ransomware is forbidden in some forums, and the stealer market is booming lately:
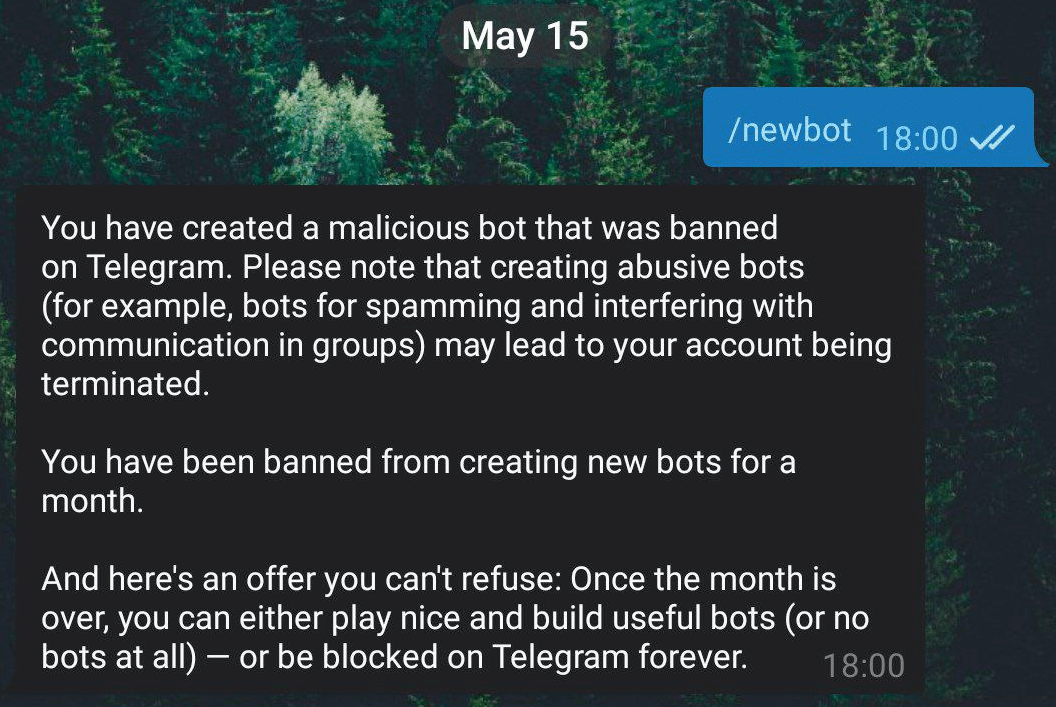
The team previously used a dedicated Telegram bot to create the desired malware build for each operator. But Telegram has been terminating the bots and threatening to permanently ban their creators:
Now the team uses a web builder, a quite common approach for MaaS providers:
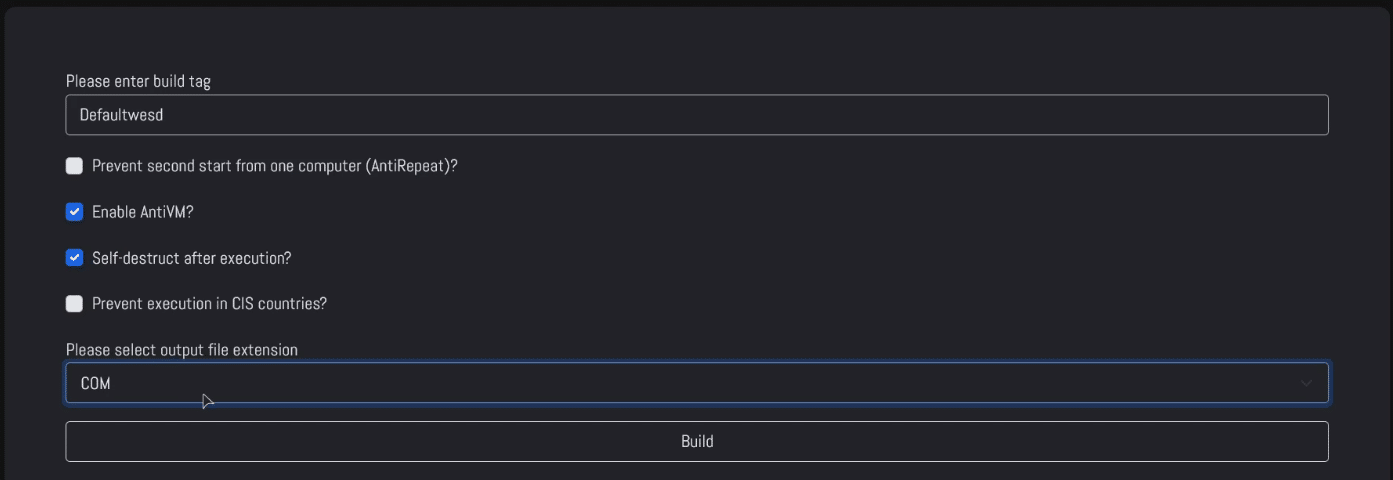
Each builder allows the operator to choose from multiple options, as seen on the Ransomware build page:
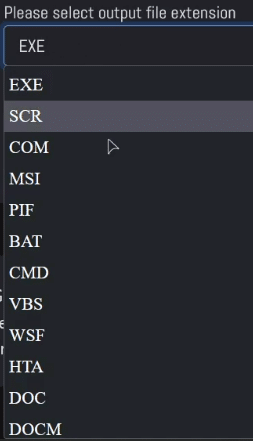
The builder also supports multiple file extensions:
The build will probably still be an executable with a different icon and extension. This is meant to deceive the target that the file is innocent.
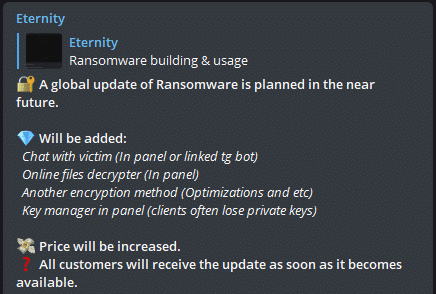
The team constantly improves their ransomware capabilities, updating their users on the Telegram channel:
The stealer is similar:
It includes interesting options like:
- “Self-destruct” – deletes the malware upon execution
- “Prevent second start” – avoids any duplicates
- “Anti-VM” – malware will not run if a virtual environment is detected
With this comes the previously known option to avoid CIS countries, and a similar extensions output.
Recent news
An Eternity Project member/developer was doxed/deanon. Their identity was revealed on an underground forum. This, however, did not seem to hurt the project or income. But it might suggest they have bad operations security (OPSEC).
Also noted in the dox is the developer’s previous projects, prior to working on Eternity:
- StormKitty
- Vulturi
- Jester Stealer
- CyberSuprise
- Agrat
Conclusion
The Eternity Project doesn’t offer unseen services or “top of the line” malware. But they do offer a bundle of services at an affordable rate, with little to no previous knowledge requirements.
And from their dox and previous projects, we can understand that they were constantly improving from a simple stealer to another – eventually building the successful “Eternity Project.”
Again, although they do not offer the best, and APT’s are probably not on their customers list, their services do work according to multiple good reviews from scammers and carders on the forums.
We believe that Eternity will increase its activity and offerings, as the MaaS market is constantly growing. While Redline rates are considerably higher, Eternity offers a reasonable price for those who seek to enter the market.