How to stay safe against attacks like the recent Cisco hack
By Ronen Ahdut – Sr. CyOps Analyst
There is one striking similarity between the recent Cisco, Microsoft, and Nvidia hacks – the attackers all used cleartext credentials as their initial access point.
These companies, each of which is at the top of its game, are no strangers to cybersecurity. In fact, Microsoft and Cisco are listed among the top security vendors. So, how were they hacked, and by whom?
To answer that, we’ll first need to shift our perspective.
In the span of less than six months, three tech titans were the target of a relatively new threat actor: the Lapsus hacking group. In fact, Cisco Talos tied their attacker back to the Lapsus gang. Lapsus’ activity was first spotted in December 2021 when they targeted the Brazilian Health Ministry’s systems. They’ve hacked a number of companies since then and openly discuss their activities in their Telegram group chat.
Most Lapsus members were teenagers. They made up for a lack of degrees, certifications, and experience with determination, sophistication, social engineering skills, and a factor without which none of their larger hacks would have been possible — a global pandemic.
COVID-19 has changed the world as we know it, including the way we work.
Nowadays most, if not all, companies support a hybrid working environment. A lot of people physically go into their offices just several times a week. Some companies have even rejected the notion of an in-person office, operating completely remotely.
While this situation might sound great for employees (and finance teams happy to see slashed expenses on travel, rent, utilities) it’s also a boon for threat actors.
Lockdowns led companies to look for a solution, and fast.
New devices were added to the domain. IT staff rushed to support either BYOD (Bring Your Own Device) or company laptops that make remote work possible. This altered company infrastructure and security guidelines. Companies that relied strictly on an intranet now had to facilitate remote connections to their environments. And, with everybody in lockdown, these computers were often used by family members.
The lockdown affected the underground communities as well. People suddenly had time to learn and develop new skills. Some learned to sew, some learned to cook. Others started hacking…
This dynamic brought a surge of new threat actors to underground communities: forums, telegram groups, and Discord channels were created daily. But even a teenager in lockdown who is fascinated by the appealing world of hacking lacks the years of experience necessary to successfully hack a system, let alone a major company.
So how did they do it?
Malware-as-a-service (MaaS)
In the past, it took a large group of people to support and operate a large hacking operation. Today, more newcomers\SKIDS (“script kiddie,” or a relatively unskilled individual who uses scripts or programs) rely on the MaaS model. These MaaS models are pre-made malware that’s sold as a subscription-like plan.
Newcomers can now rent malware sets previously unavailable to all but APTs or hacking groups for prices between $10-$200 USD.
The “Eternity Project” publications is a great example of this:
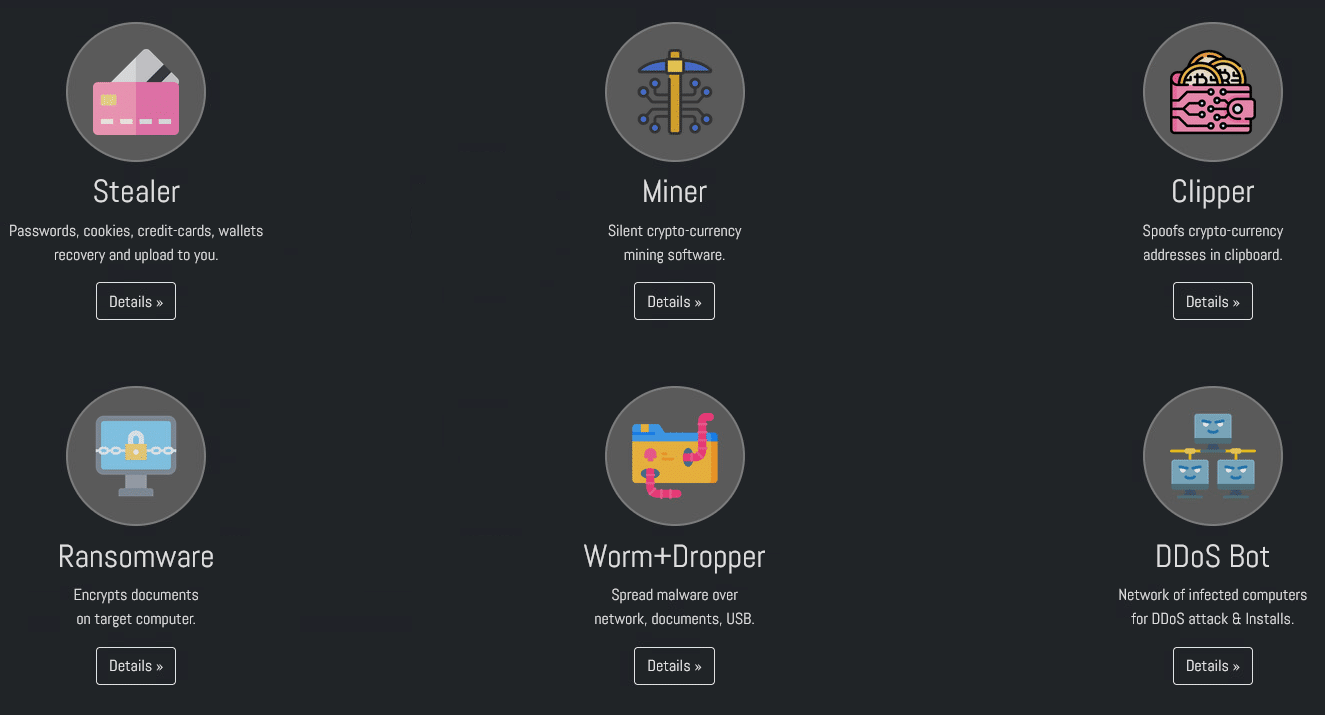
- Stealer ($260) – malware that steals passwords, cookies, credit cards, and crypto wallets from a victim’s computer..
- Miner ($90) – a malicious program that uses the resources of an infected computer to mine cryptocurrency.
- Clipper ($110) – a malware classification that monitors the victim’s clipboard of an infected PC for cryptocurrency wallets and then replaces the copied address with the attacker’s desired destination.
- Ransomware ($470) – a type of malware that prevents or limits users from accessing their system, either by locking the system’s screen or by locking the users’ files until a ransom is paid.
- DDoS Bot – allows the attacker to choose their target and perform DDOS attacks using the infected computers under the Eternity Project.
The Eternity project, one of the newest projects, grew in importance for unexperienced hackers seeking a “one-stop shop.”
Of all the commodity malware available, one has been especially successful: the Info-Stealer malware family, and particularly Redline Stealer.
Info-stealers can steal stored credentials from browsers, cookies (used for session hijacking and to bypass MFA), crypto wallets, and more.
*For more information on Redline, see our analysis here.
The influx of new hackers led to a spike in stolen data. But there is a difference between stealing information and using it.
So, what are they doing with the data?
The data flood evolved into a sub-ecosystem in Darknet marketplaces, which most people associate with drugs, fake ID, credit cards, and guns. Now, more and more Darknet marketplaces focus on one thing – stolen credentials.
While some simply added a “Stealer Logs” section, other marketplaces increasingly focus on info- stealer outputs as their main supply. Credentials, cookies, and remote VPN connections are now offered for sale at mass scale.
Check out this “Russian Market” marketplace menu:
“Genesis Marketplace” specializes in stolen credentials and personal information that might lead to identity theft.
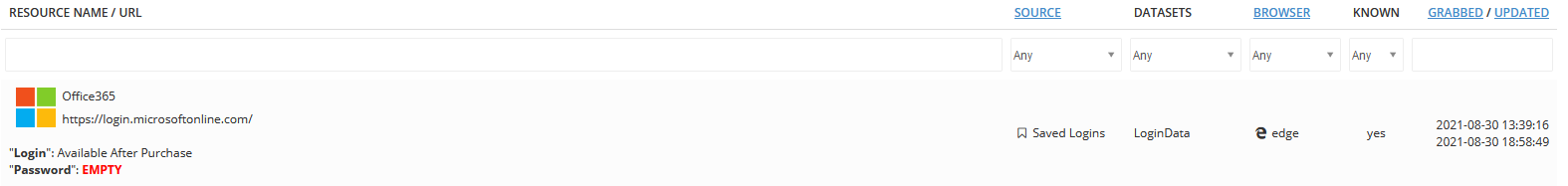
These are only two examples. Users can filter by desired country, domain, or any other useful information, such as Microsoft credentials to an organization’s Office 365:
This new vector has also highlighted a security issue, as seen with Microsoft, Cisco, and Nvidia.
All three companies have the highest standards when it comes to cybersecurity. But they aim at opponents attacking from the outside. What happens when an attacker simply logs into the system as a regular user?
What if he uses legitimate programs to perform his malicious actions? How can the security team be aware of the incoming or ongoing attack?
3 tips to stay safe
Just because the attackers are relentless doesn’t mean there aren’t things you can do right now to avoid being their next victim.
The first and most valuable thing you can do is raise employee awareness. Infections don’t happen on their own. Often, it’s an end-user who isn’t technically savvy that brings a company to its knees. They weren’t educated on cybersecurity best practices which is why they are prime targets for evildoers. We all know the story. An employee downloads and executes a program – the security team loses any hope of sleeping any time soon. But this is the important part that many people forget (or don’t have time to address) – as the environment changes, so too must awareness training. Keep your trainings up-to-date and make sure you’re providing the trainings frequently.
Next tip: As hard as it might be for some, work laptops should remain off-limits in a shared household. Much of the data we’ve uncovered is related to gaming (mostly Minecraft or Roblox) or cracked software.
That means that you have to empower your employees to set guidelines for family members using your company laptop. Employee awareness is insufficient. Everyone who will use your laptop must be wary of digital dangers.
Lastly, don’t solely rely on an identity theft\credentials monitoring system.
Many companies offer a service called Darknet Monitoring that crawls the Darkweb and sends you a notification if your name is mentioned, or if access to your corporation is offered for sale on a marketplace. But most logs don’t reach a marketplace, ending up shared in bulk as large archives that are ignored for various reasons.
Interested in learning more?
Check out CyOps Lighthouse!
Cynet is one of a few companies, currently, to offer a credential theft monitoring system.
Using an in-house system developed at Cynet, we monitor and notify customers whose environment-related credentials are compromised. Why are we excited about it? This monitoring is an added bonus and doesn’t rely on Cynet’s deployment on the compromised system to give our customers a heads up.
The service is currently offered exclusively to Cynet customers. For more on Lighthouse, read our latest post.