January 2023 Ransomware Activity Report
Written by: Maor Huli
The ransomware from January to introduce are:
- Upsilon
- KoRyA
- Bettercallsaul
- Sickfile
EXECUTIVE SUMMARY
As an integral department in Cynet’s research team, Orion works around the clock to track threat intelligence resources, analyze payloads, and automate labs to ensure that our customers are protected against the newest ransomware variants. In these monthly reports, Orion reviews the latest trends identified in Bleeping Computer — the most up-to-date website that summarizes the newest ransomware variants — and shares how Cynet detects these threats.
CYNET 360 AutoXDR™ VS RANSOMWARE
Upsilon Ransomware
- Observed since: Jan 2023
- Ransomware encryption method: AES + RSA
- Ransomware extension: .upsil0n
- Ransomware note: Upsilon.txt
- Sample hash: ee23f0addbae4b3c384d99c15adda491ed637df33348a090993a23867fa6ee7c
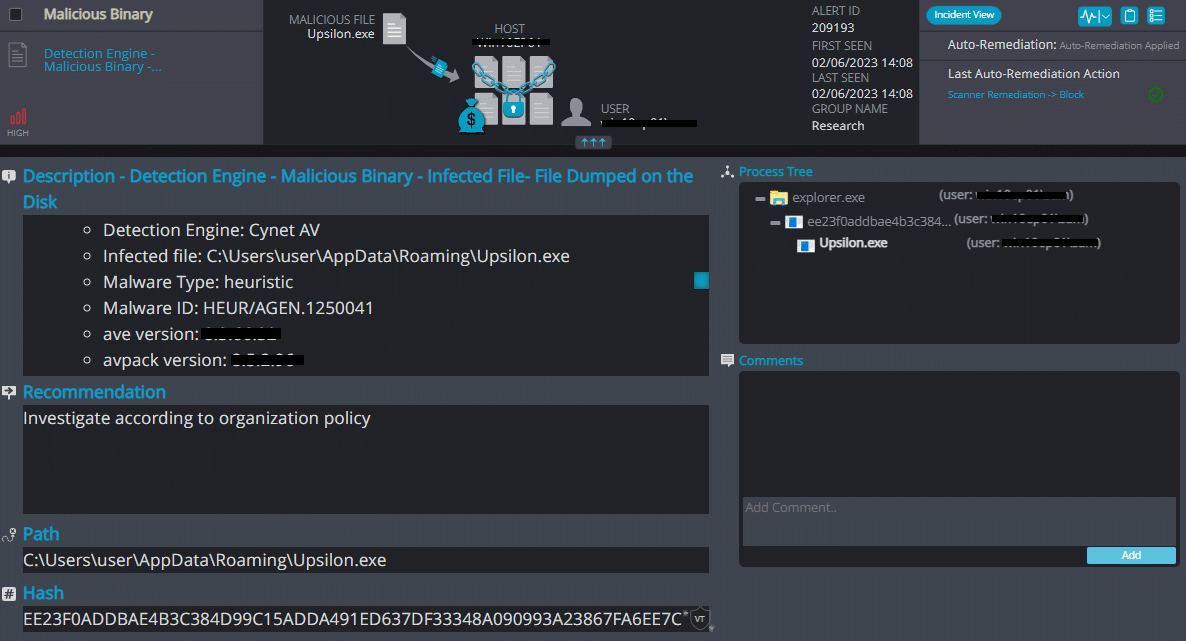
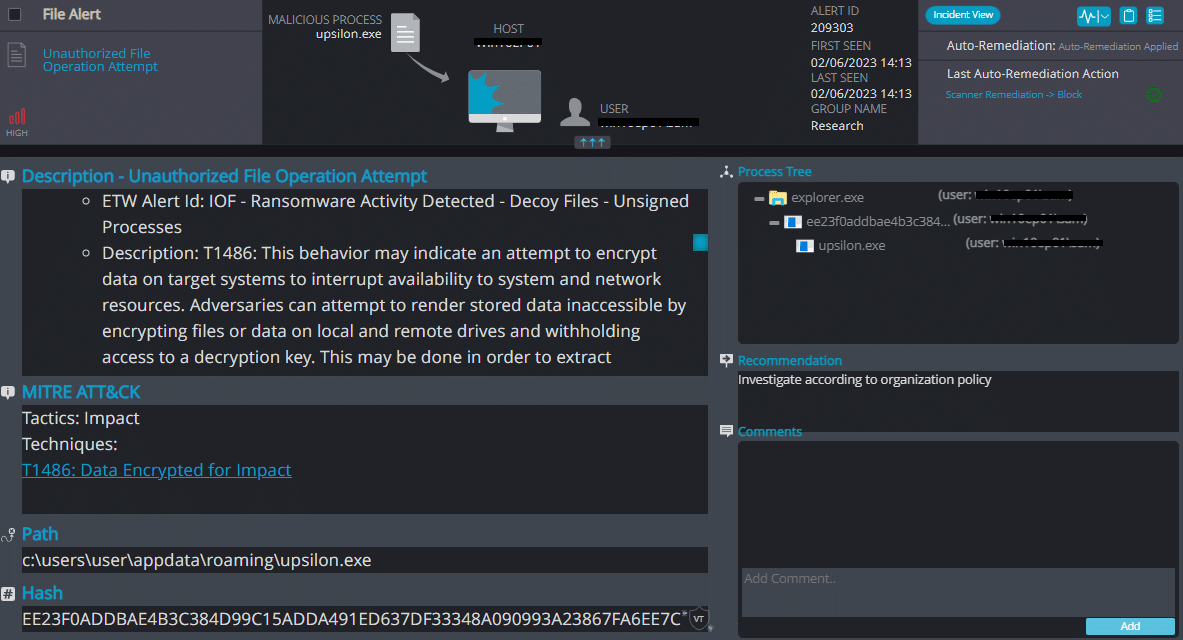
Cynet 360 AutoXDR™ Detections:
Upsilon Overview
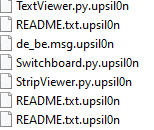
Upsilon ransomware renames the encrypted files with “.upsil0n” in the extension:
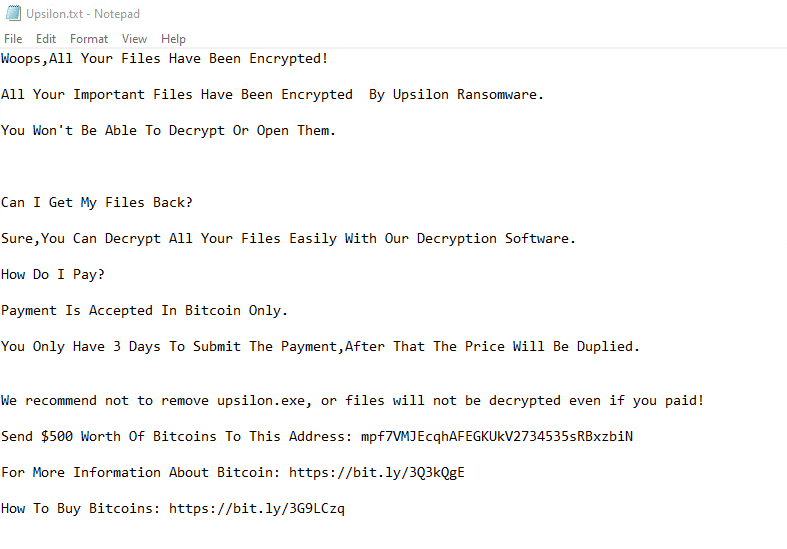
Once a computer’s files have been encrypted and renamed, Upsilon drops a note named “Upsilon.txt”:
Upon execution, Upsilon immediately encrypts the endpoint and drops the ransomware note.
The ransomware note contains general information, warnings, and the attacker’s Bitcoin wallet address:
The ransomware also changes the desktop’s background:
KoRyA Ransomware
- Observed since: Mid-2019
- Ransomware encryption method: AES + RSA
- Ransomware extension: .KoRyA
- Ransomware note: HOW TO DECRYPT FILES.txt
- Sample hash: b2447bb9ef759c890d75e31eb07f0553065d74403f654c9757635b02f1b753be
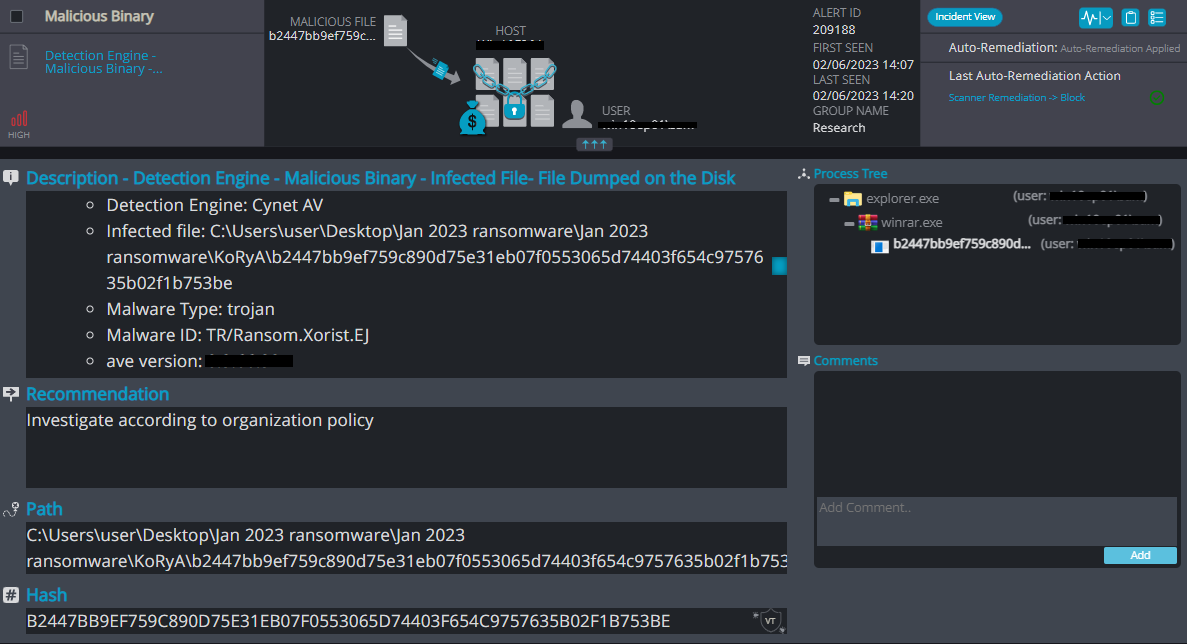
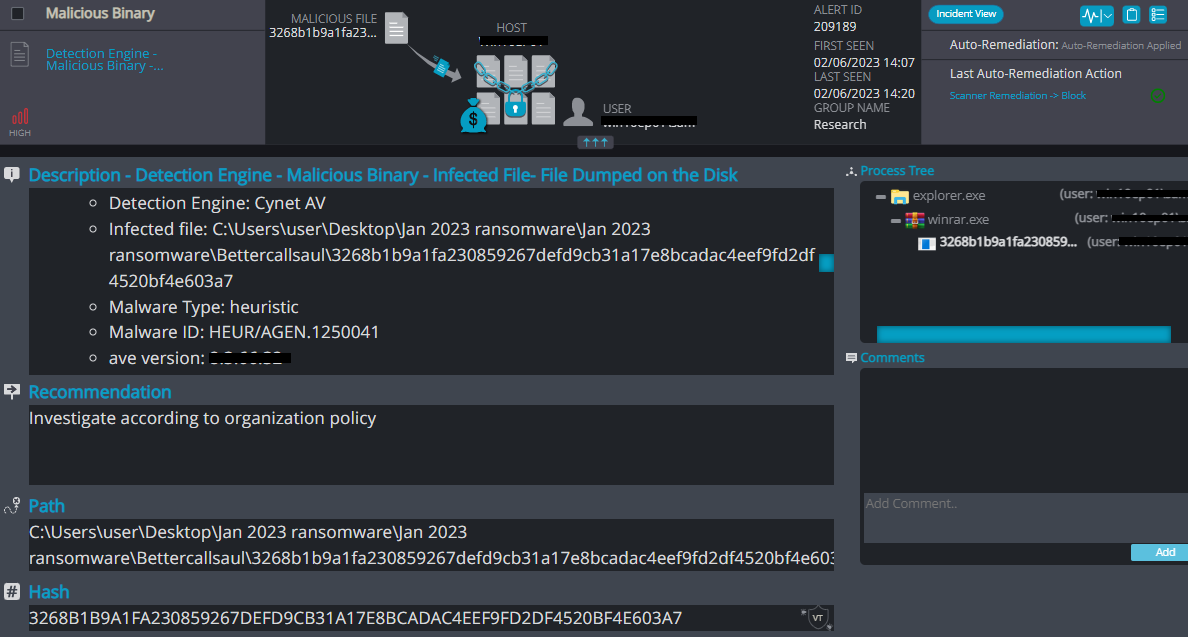
Cynet 360 AutoXDR™ Detections:
Xorist Ransomware variant
KoRyA Overview
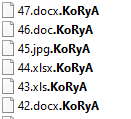
KoRyA ransomware renames the encrypted files with “.KoRyA” in the extension:
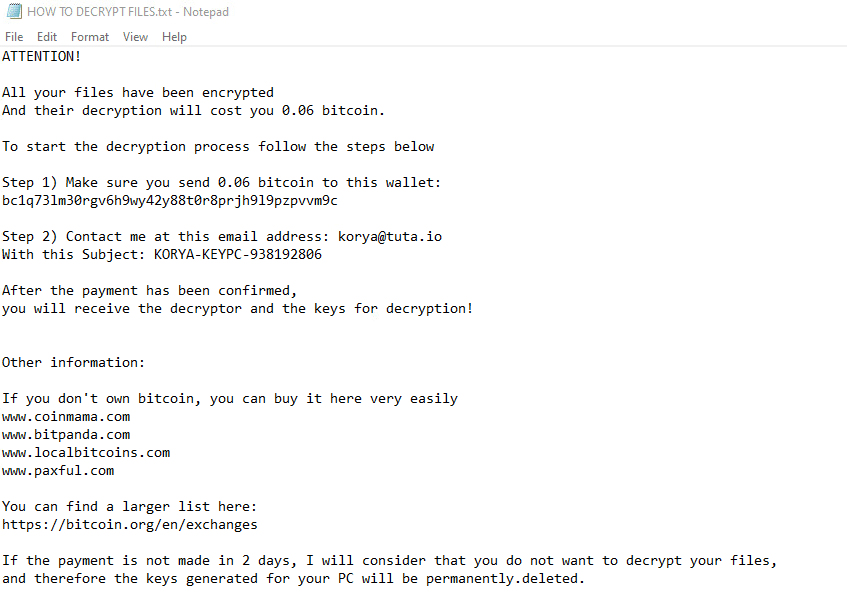
Once a computer’s files have been encrypted and renamed, KoRyA drops a note named “HOW TO DECRYPT FILES.txt”:
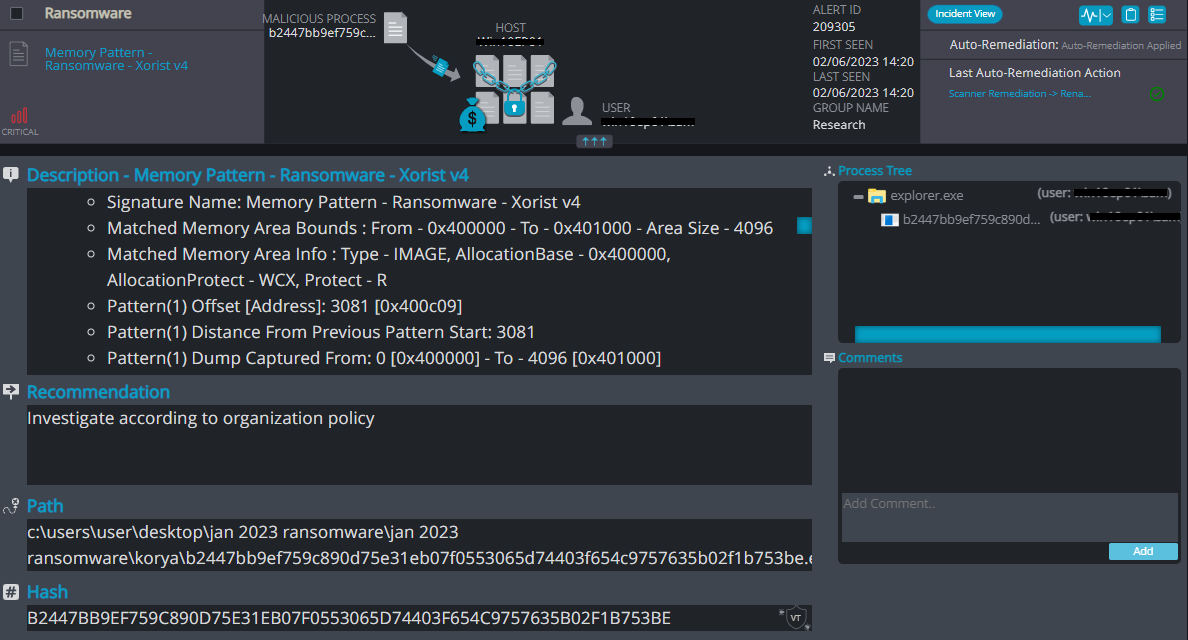
Upon execution, KoRyA immediately encrypts the endpoint and drops the ransomware note.
The ransomware note contains general information, warnings, and the attacker’s email address and Bitcoin wallet:
Bettercallsaul Ransomware
- Observed since: Mid-2021
- Ransomware encryption method: AES-256
- Ransomware extension: .bettercallsaul
- Ransomware note: DECRYPT_MY_FILES.txt
- Sample hash: 3268b1b9a1fa230859267defd9cb31a17e8bcadac4eef9fd2df4520bf4e603a7
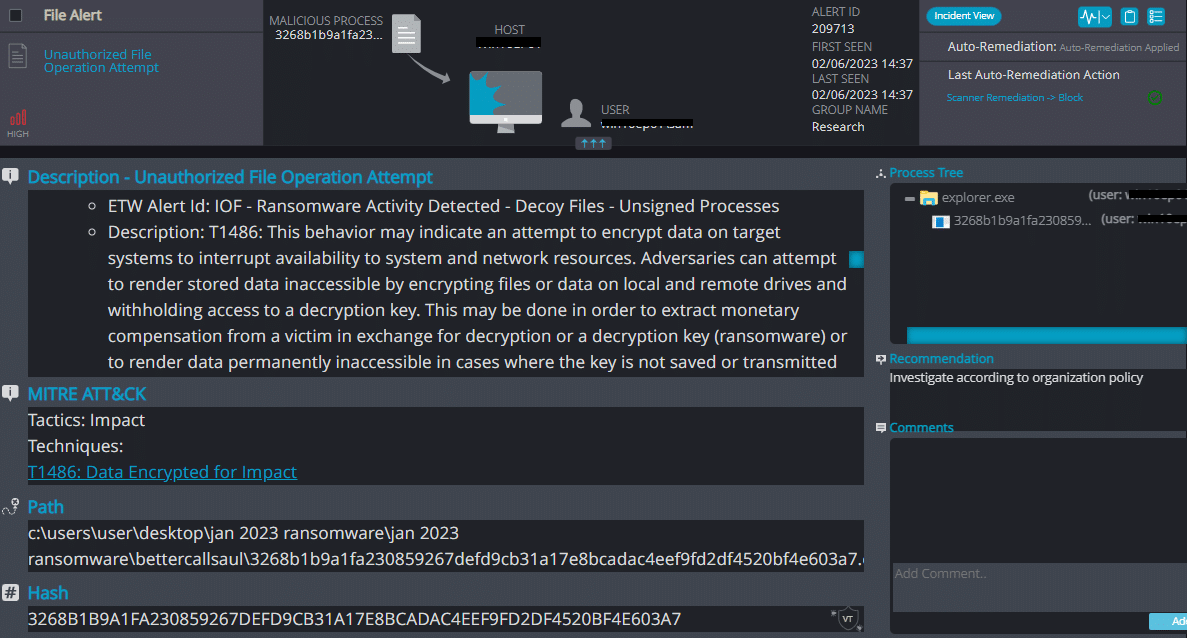
Cynet 360 AutoXDR™ Detections:
Bettercallsaul Overview
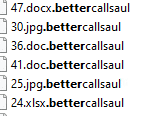
Bettercallsaul ransomware renames the encrypted files with “bettercallsaul” in the extension:
Once a computer’s files have been encrypted and renamed, Bettercallsaul drops a note named “DECRYPT_MY_FILES.txt”:
Upon execution, Bettercallsaul immediately encrypts the endpoint and drops the ransomware note.
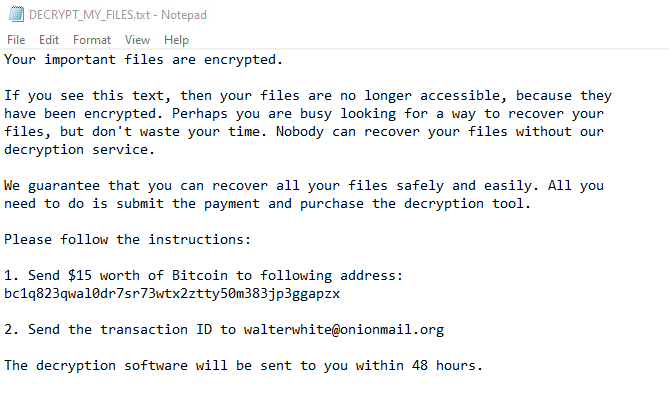
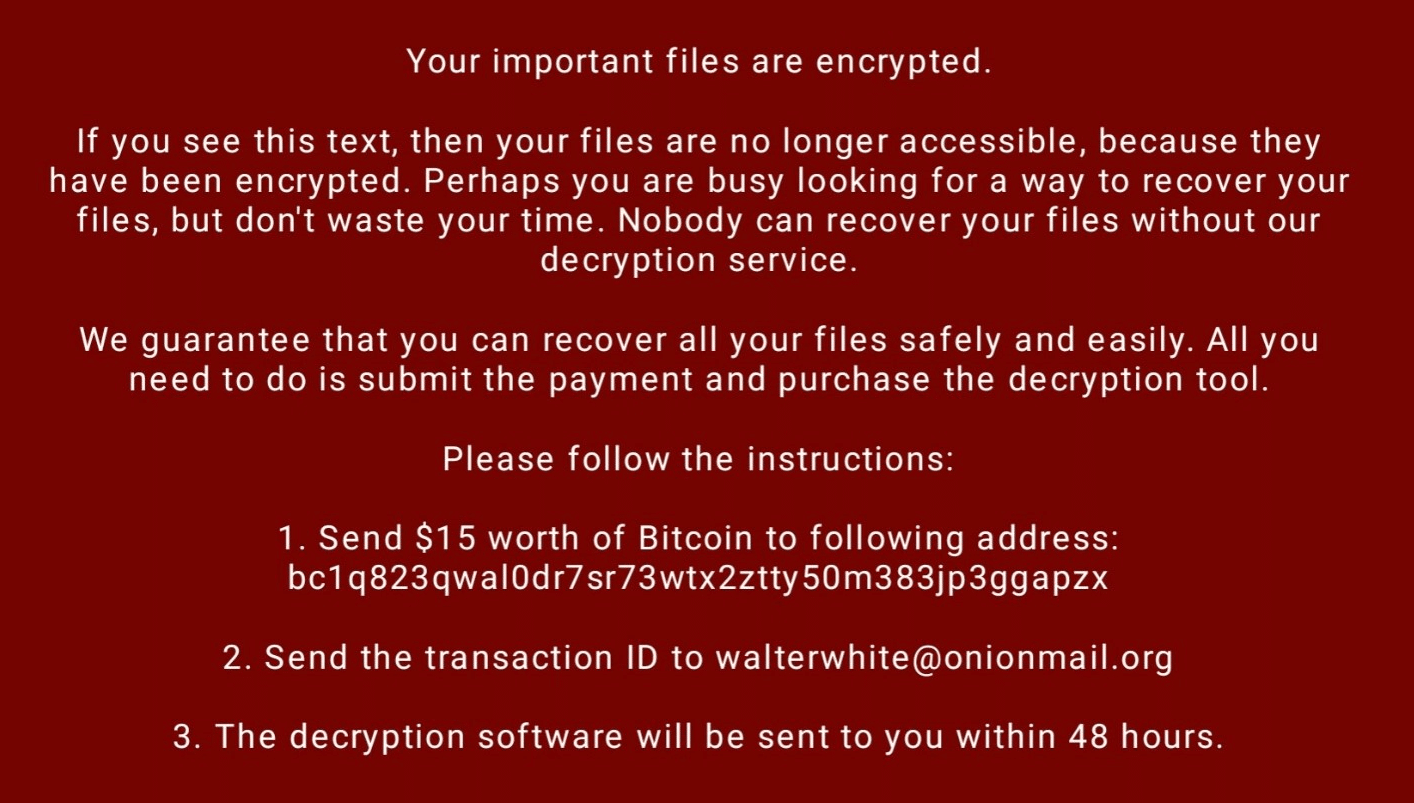
The ransomware note contains general information, warnings, and the attacker’s email address:
The ransomware also changes the desktop background:
SickFile Ransomware
- Observed since: Jan 2023
- Ransomware encryption method: AES + RSA
- Ransomware extension: .sickfile
- Ransomware note: how_to_back_files.html
- Sample hash: 1c2d5cccca58b469351980895c8a2080c8346de09c2f1ab7a123deb3d3e4a539
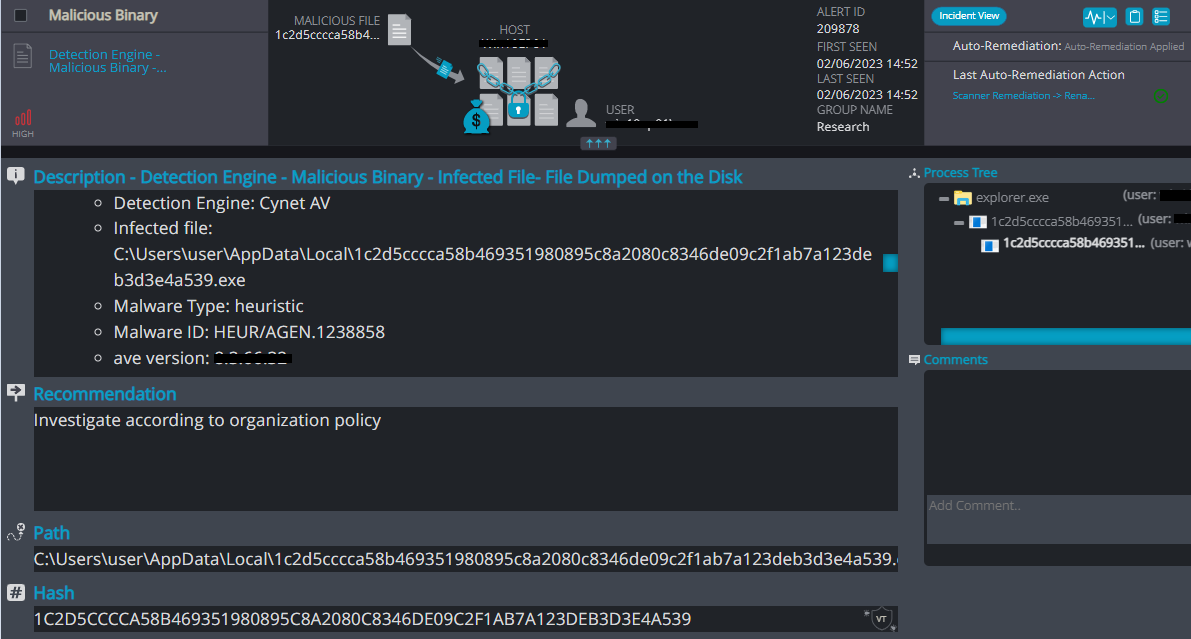
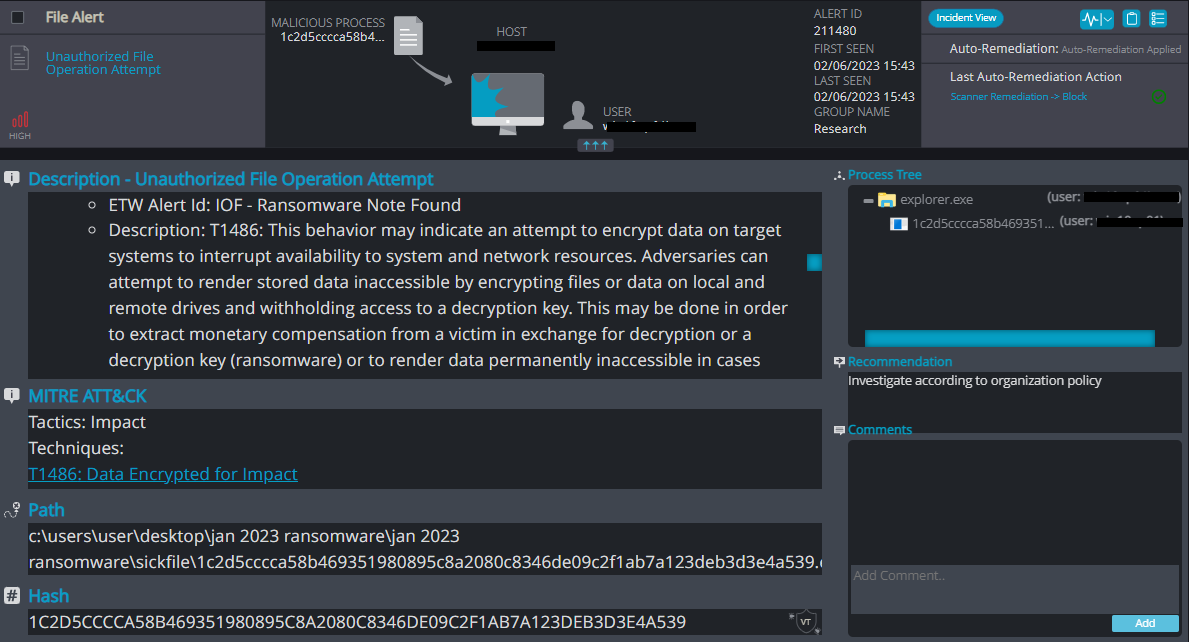
Cynet 360 AutoXDR™ Detections:
SickFile Overview
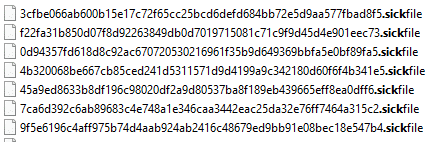
SickFile ransomware renames the encrypted files with “.sickfile” in the extension:
Once a computer’s files have been encrypted and renamed, SickFile drops a note named “how_to_back_files.html”:
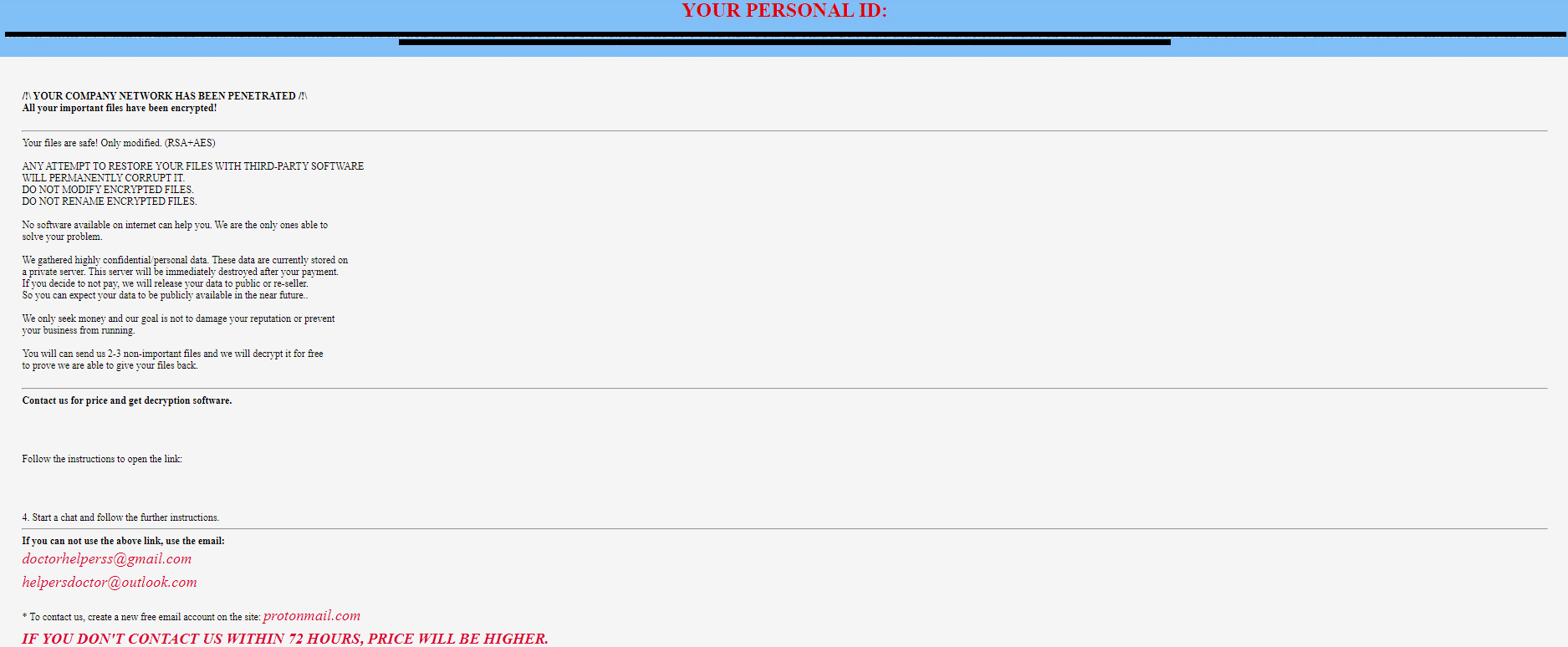
Upon execution, SickFile immediately encrypts the endpoint and drops the ransomware note.
The ransomware note contains general information, warnings, and the attacker’s email address: