October 2022 Ransomware Activity Report
Written by: Maor Huli
Ransomware from October to introduce are:
- RedKrypt
- RONALDIHNO
- CMLOCKER
- Killnet
EXECUTIVE SUMMARY
As an integral department in Cynet’s research team, Orion works around the clock to track threat intelligence resources, analyze payloads and automate labs to ensure our customers are protected against the newest ransomware variants. In these monthly reports, Orion reviews the latest trends identified in Bleeping Computer — the most up-to-date website that summarizes the newest ransomware variants — and shares how Cynet detects these threats.
CYNET 360 AutoXDR™ vs. RANSOMWARE
RedKrypt Ransomware
- Observed since: Oct 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .redkrypt
- Ransomware note: RedKrypt-Notes-README.txt
- Sample hash: 16764b173314ddeb7341f18a7b33066a319476847ba715c53c4f0f8e9ed43a20
Cynet 360 AutoXDR™ Detections of RedKrypt:
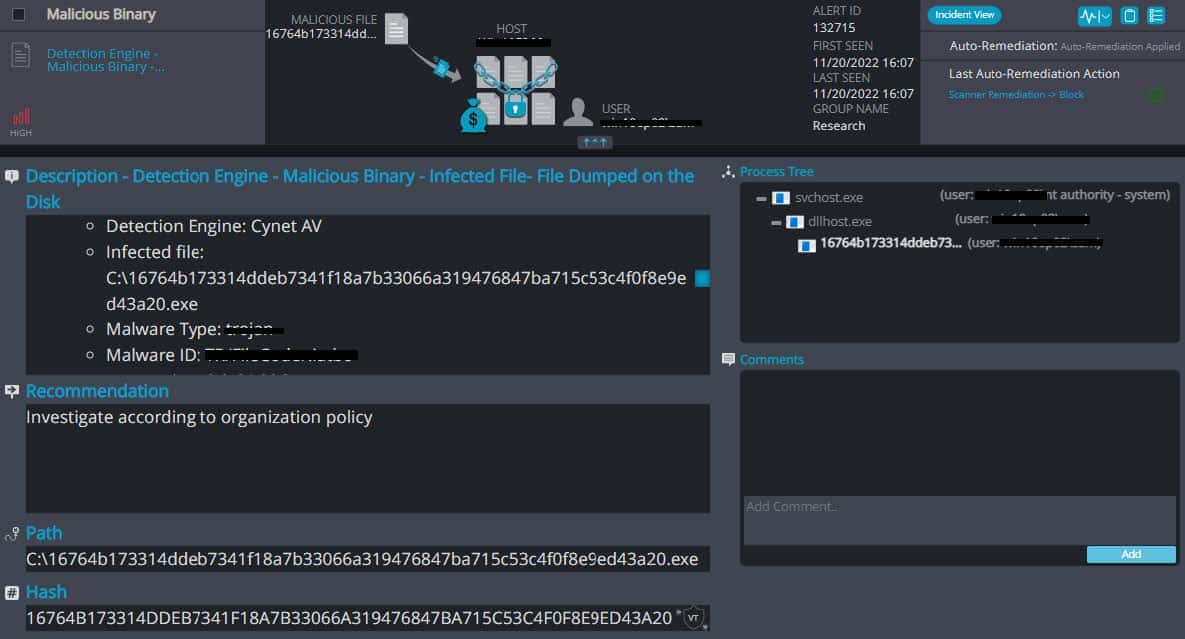
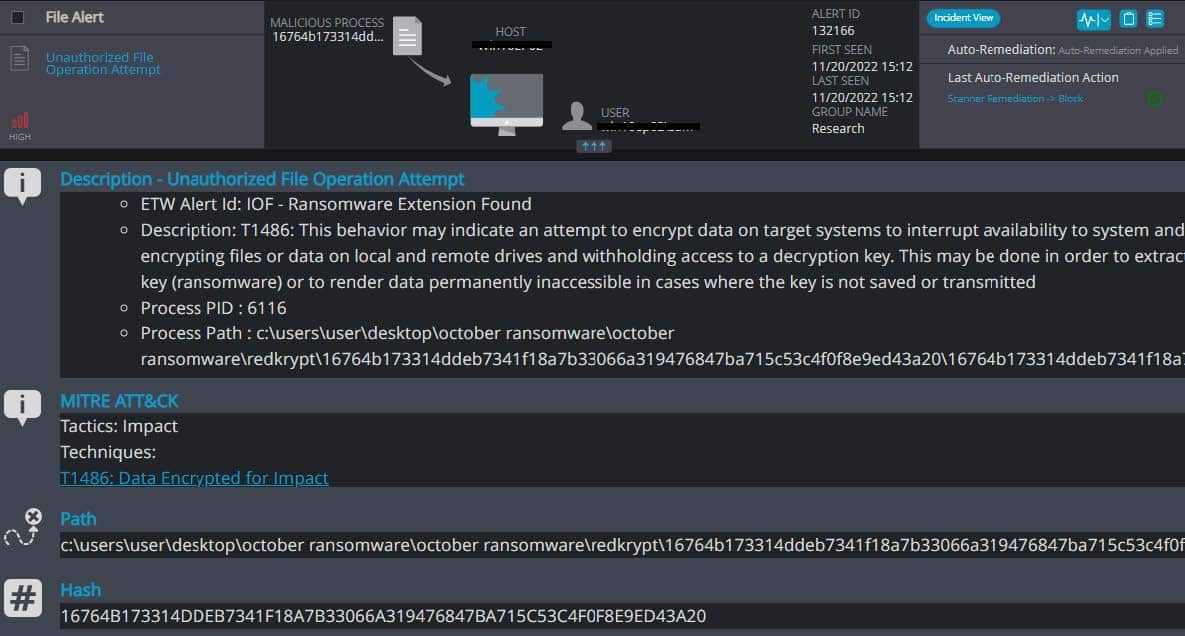
RedKrypt Overview
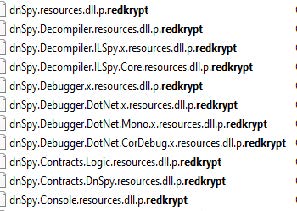
- RedKrypt ransomware renames the encrypted files with .redkrypt in the extension.
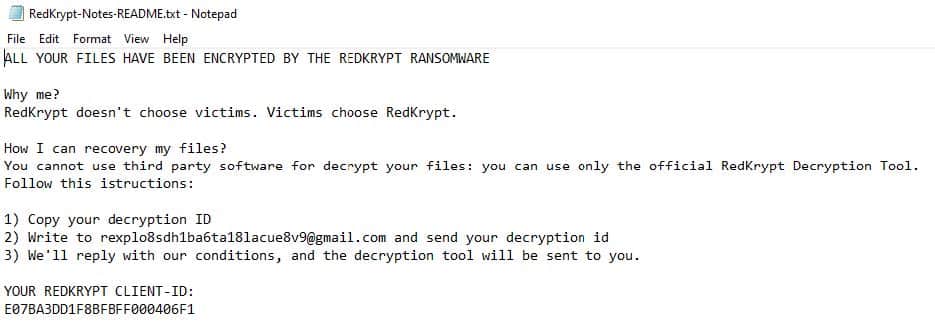
- Once a computer’s files have been encrypted and renamed, it drops a note as “RedKrypt-Notes-README.txt”:
- The ransomware note contains general information, warnings and the attacker’s email address:
RONALDIHNO Ransomware
-
Observed since: Oct 2022
-
Ransomware encryption method: AES + RSA
-
Ransomware extension: .r7
-
Ransomware note: READ_THIS.txt
-
Sample hash: 568ea8c7d3f1ad39e975fac562fc4af41e983f289af092a104c2ec99e8259586
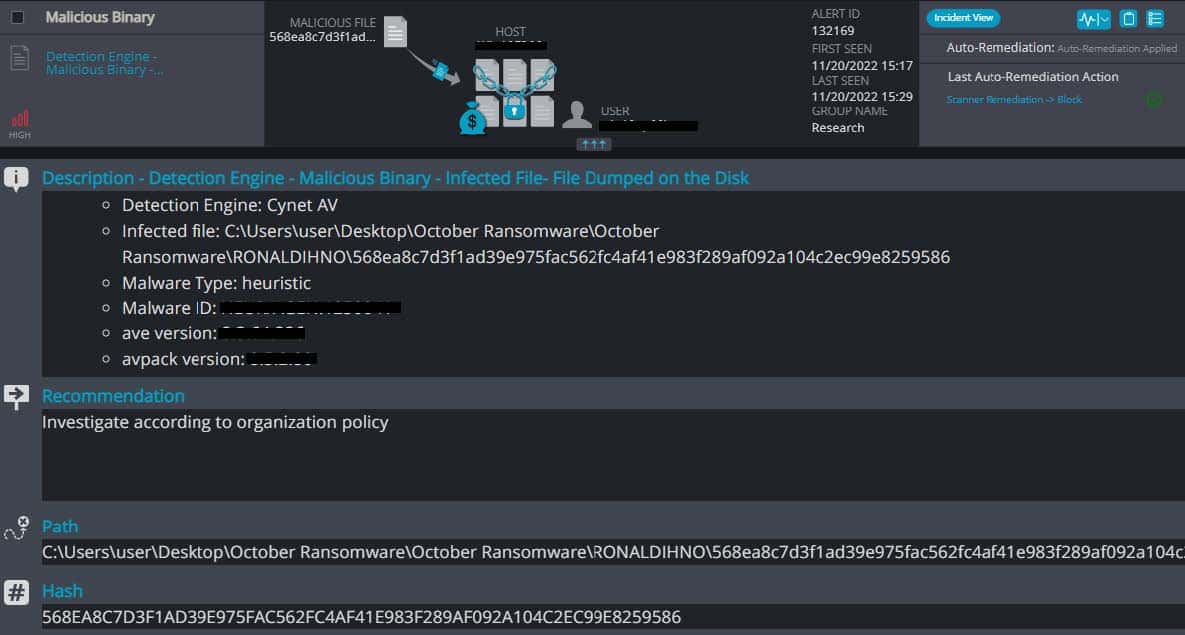
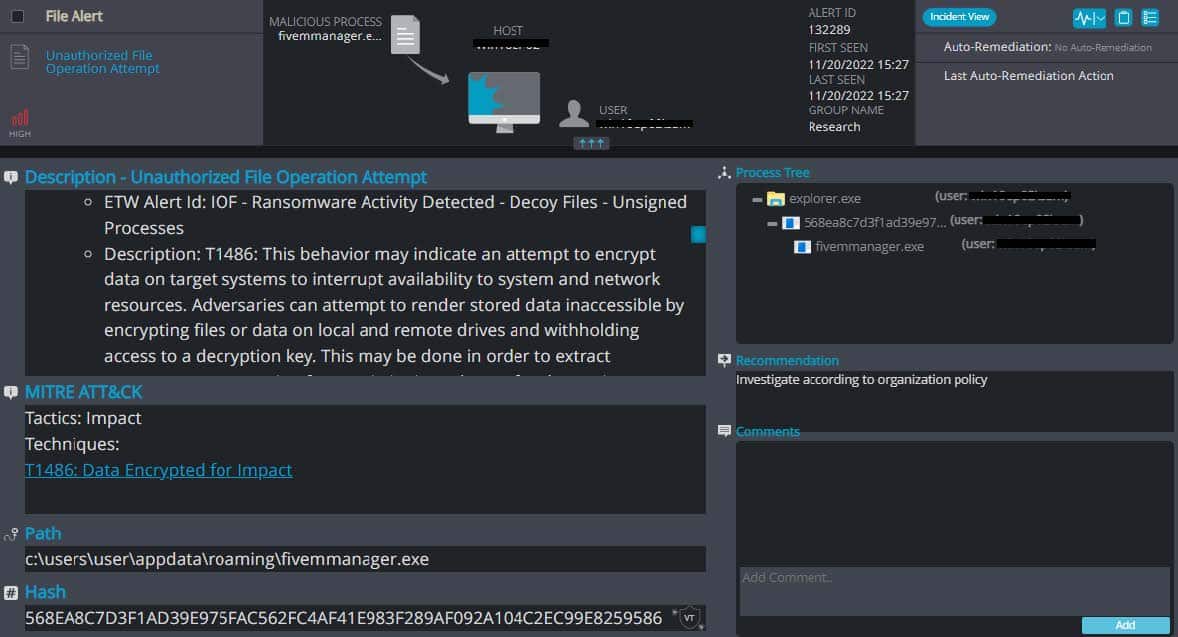
Cynet 360 AutoXDR™ Detections of RONALDIHNO:
RONALDIHNO Overview
- RONALDIHNO ransomware renames the encrypted files with .r7 in the extension:
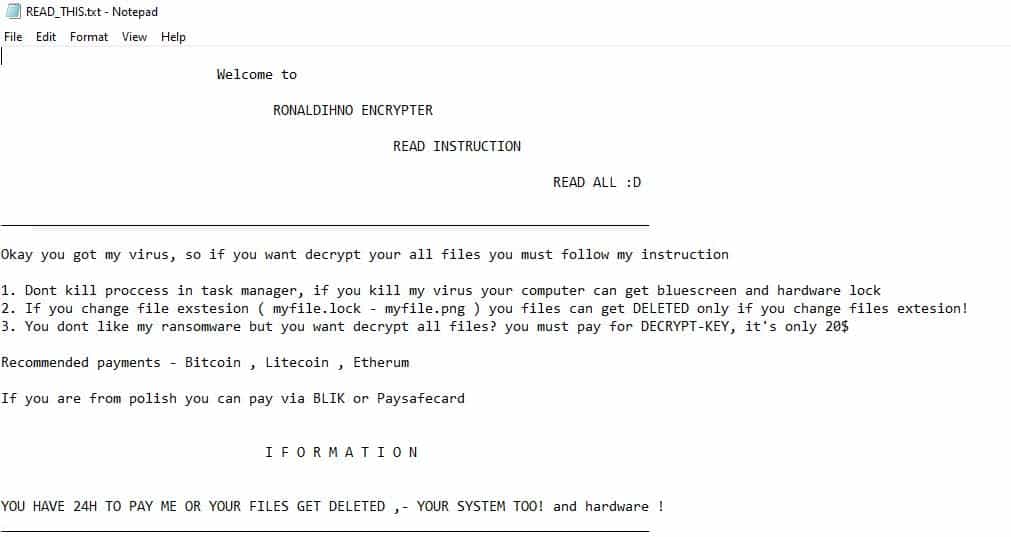
- Once a computer’s files have been encrypted and renamed, it drops a note named “READ_THIS.txt”:
- The ransomware note contains general information and warnings:
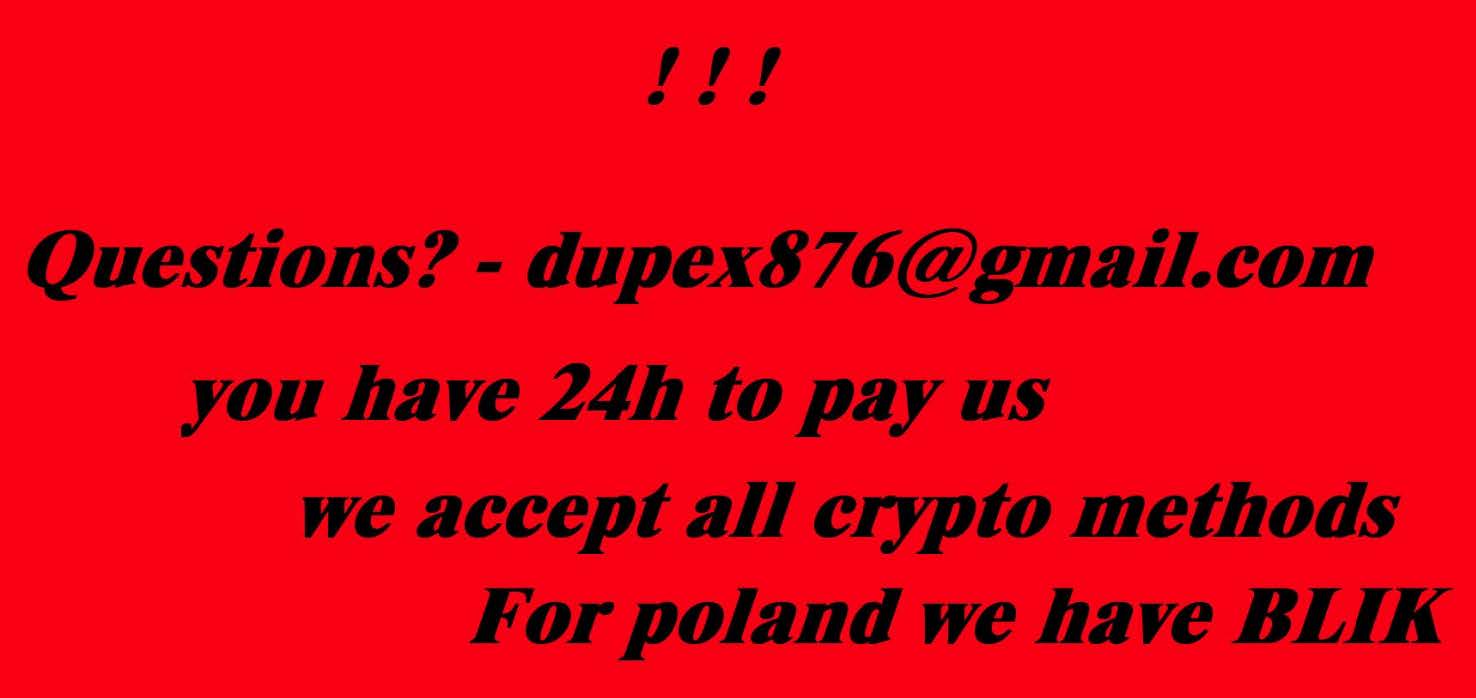
- The attacker’s contact information will eventually appear as a desktop background:
CMLOCKER Ransomware
- Observed since: 2022
-
Ransomware encryption method: AES + RSA
-
Ransomware extension: .CMLOCKER
-
Ransomware note: HELP_DECRYPT_YOUR_FILES.txt
-
Sample hash: 5fef2acf0b0289500ddfcbcbe45c95973c37d30eecdb2f5f20894a5f5b43ef31
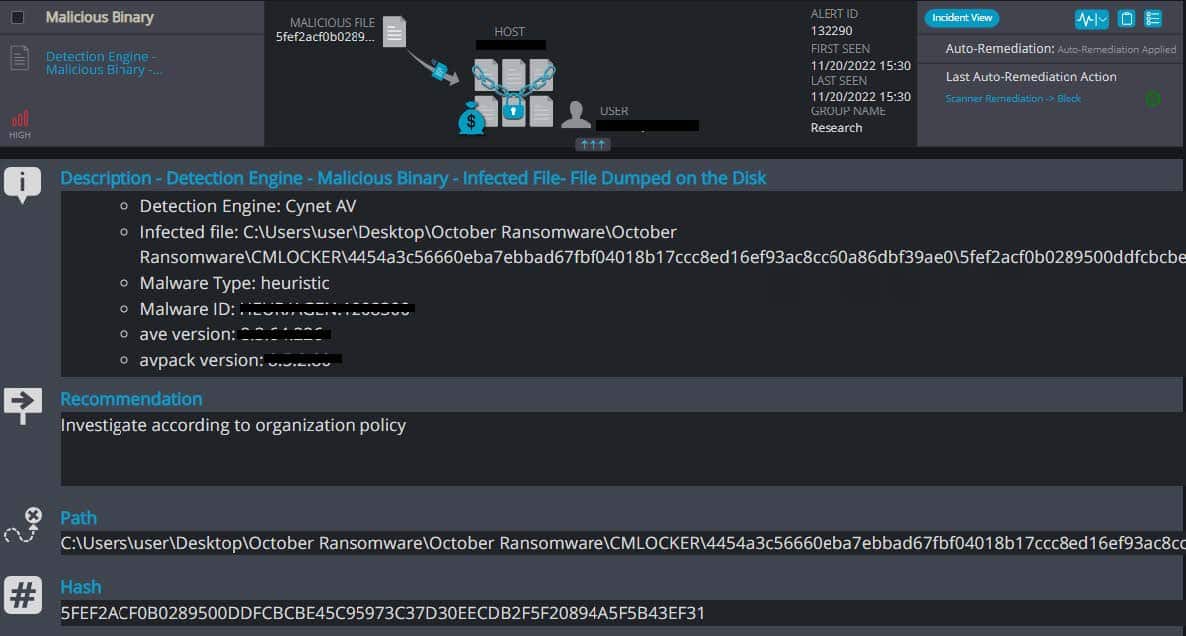
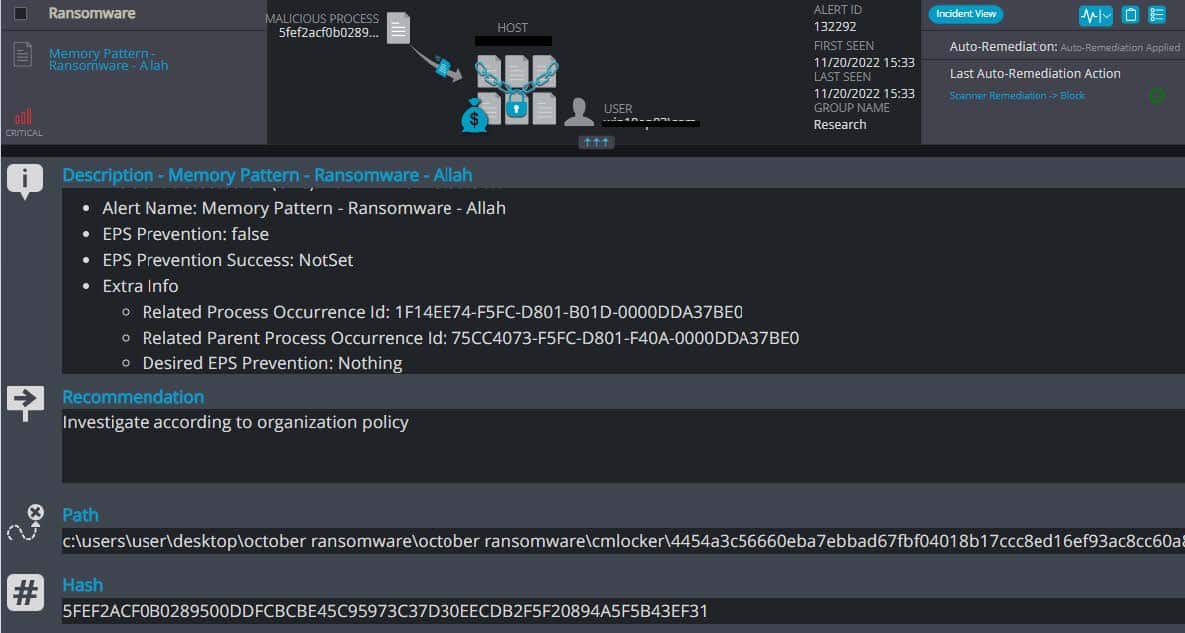
Cynet 360 AutoXDR™ Detections of CMLOCKER:
CMLOCKER Overview
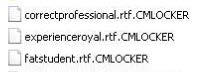
- CMLOCKER ransomware renames the encrypted files with .CMLOCKER in the extension (screenshot has been taken from an outsource sandbox):
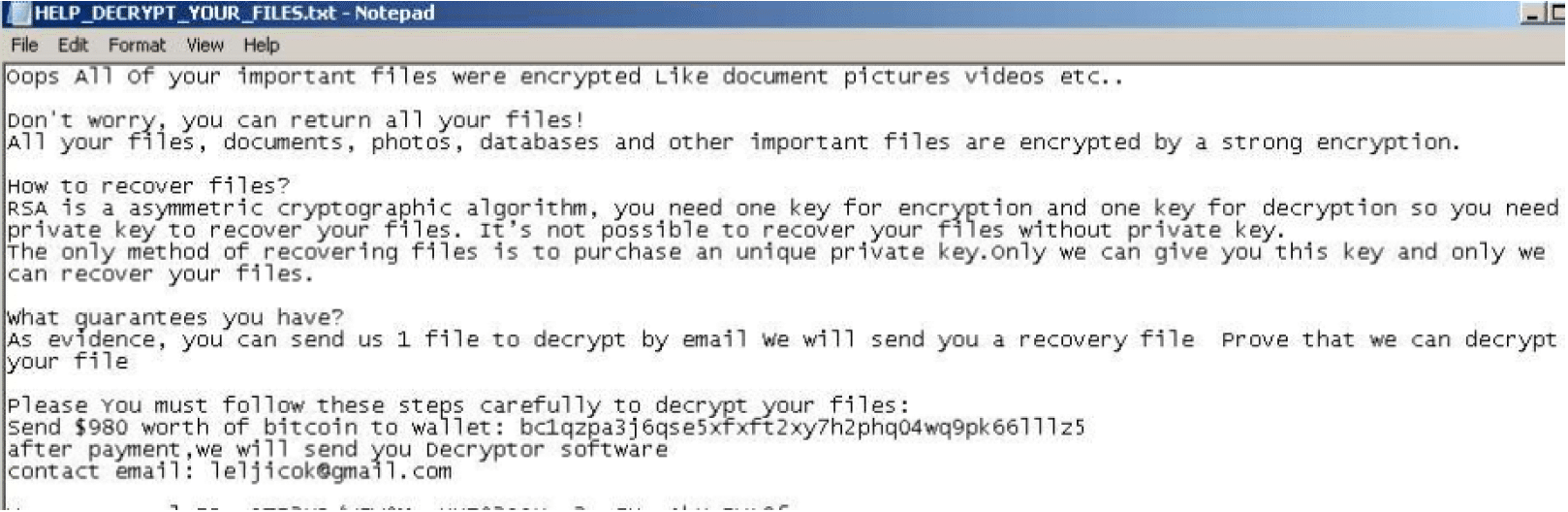
- Once a computer’s files have been encrypted and renamed, it drops a note named “HELP_DECRYPT_YOUR_ FILES.txt” (screenshot has been taken from an outsource sandbox):
- Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains general information, warnings and several attacker’s links (screenshot has been taken from an outsource sandbox):
Killnet Ransomware
- Observed since: 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .killnet
- Ransomware note: Ru.txt
- Sample hash: db1c8ddcdfea93031a565001366ffa9fdb41a689bddab46aec7611a46bb4dc50
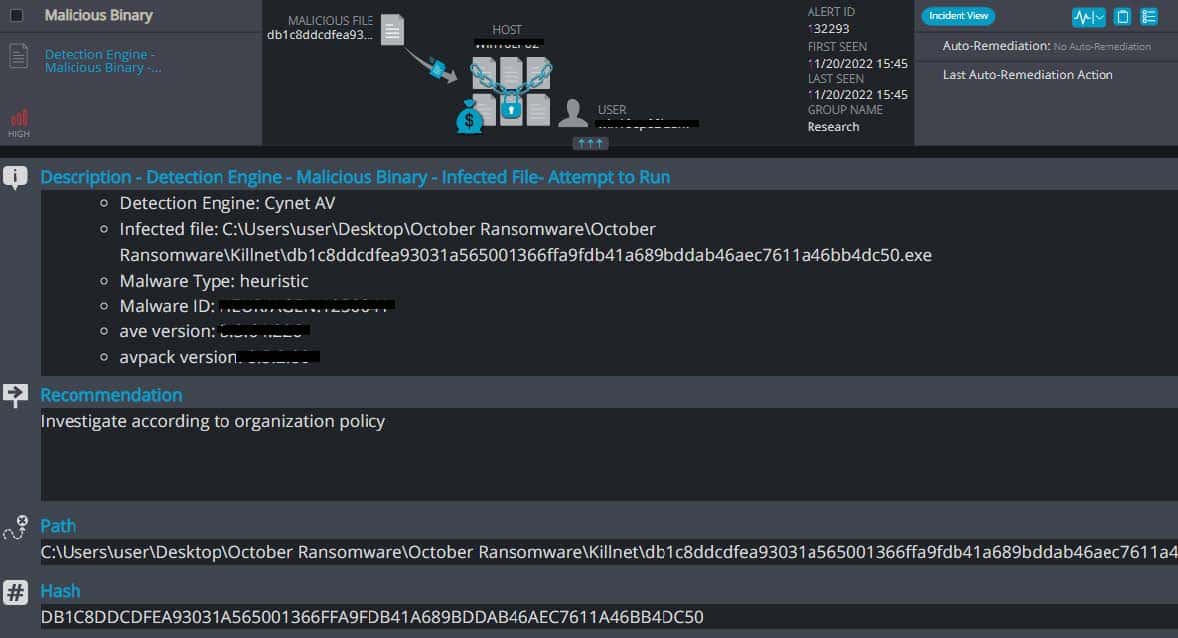
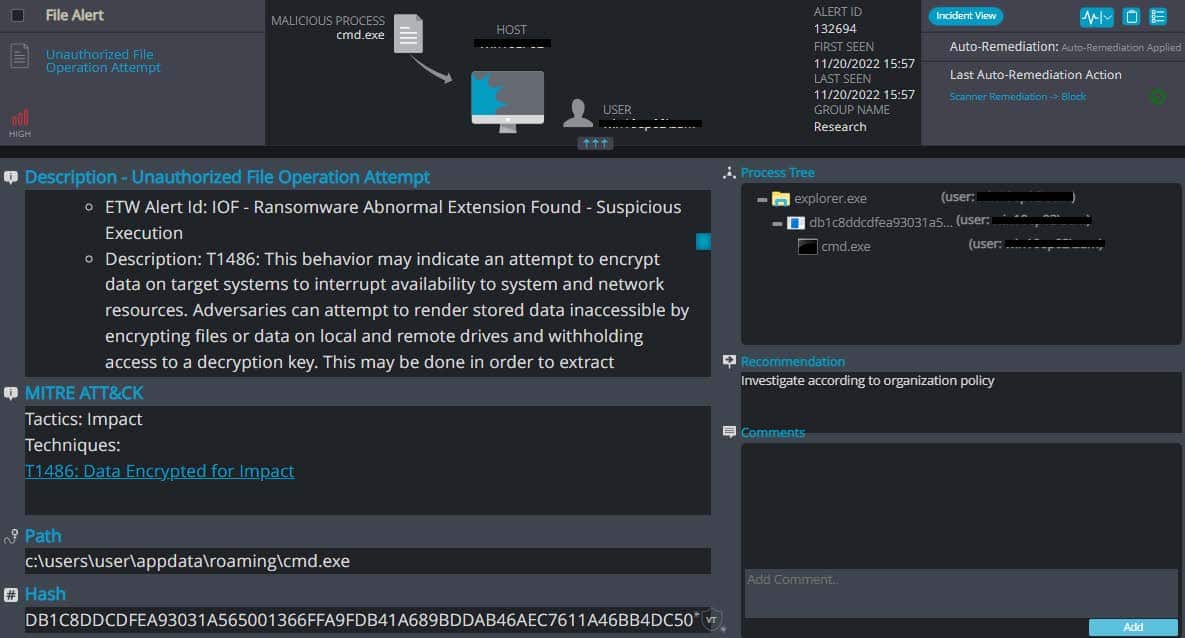
Cynet 360 AutoXDR™ Detections of Killnet:
Killnet Overview
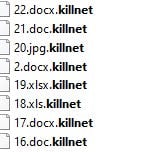
- Killnet ransomware renames the encrypted files with .killnet in the extension:
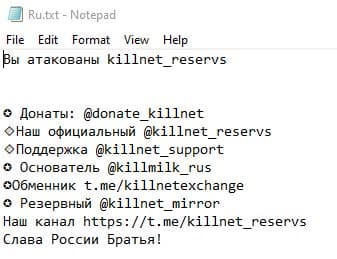
- Once a computer’s files have been encrypted and renamed, it drops a note named “Ru.txt”:
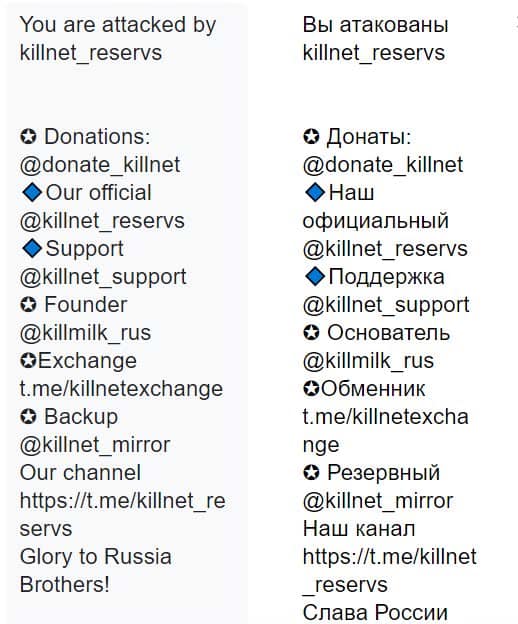
- Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains general information, warnings and several attackers’ links:
- Google Translate:
- The ransomware also changes the desktop wallpaper: