Pterodo malware analysis
Pterodo, also referred to as Pteranodon, is a type of backdoor malware known as a backdoor Trojan or remote access Trojan (RAT). Its primary function is to grant unauthorized access to a computer system by bypassing standard authentication protocols. Once activated, it establishes a communication link between the compromised device and the attacker’s command-and-control server. This connection enables the attacker to remotely manipulate the infected system, issue commands, transfer files, gather data, and potentially engage in additional malicious actions.
In 2022, the Gamaredon Group, an advanced persistent threat (APT) known by other names like Armageddon or Shuckworm, developed this new backdoor with the aim of targeting entities in Ukraine and neighboring countries. In June 2023, the Gamaredon Group carried out an attack using the Pterodo backdoor, specifically targeting critical organizations within Ukraine’s military and security intelligence sectors.
The attack began with phishing emails containing attachments such as RAR, HTA, DOCX, LNK, and SFX files. Upon opening these attachments, a PowerShell command was executed, initiating the download of the Pterodo payload from the command-and-control server, followed by its execution on the victim’s system. This attack methodology allowed the Gamaredon Group to infiltrate and compromise the targeted organizations, potentially enabling them to carry out various malicious activities.
Static Analysis
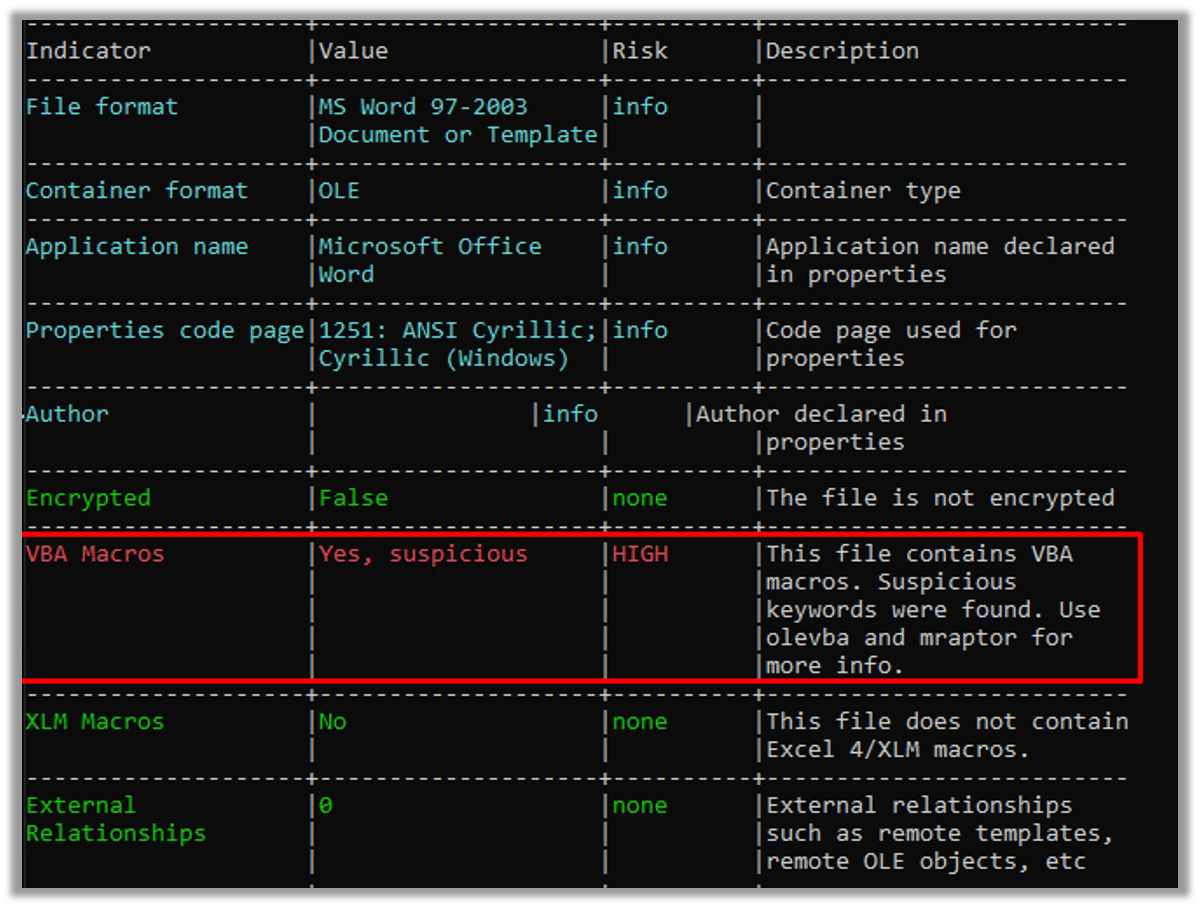
During our investigation of the phishing document, we discovered that VBA macros were present, as revealed by the analysis using oleid. These VBA macros were embedded within the document, indicating that the attackers used this technique to incorporate malicious code and carry out their objectives.
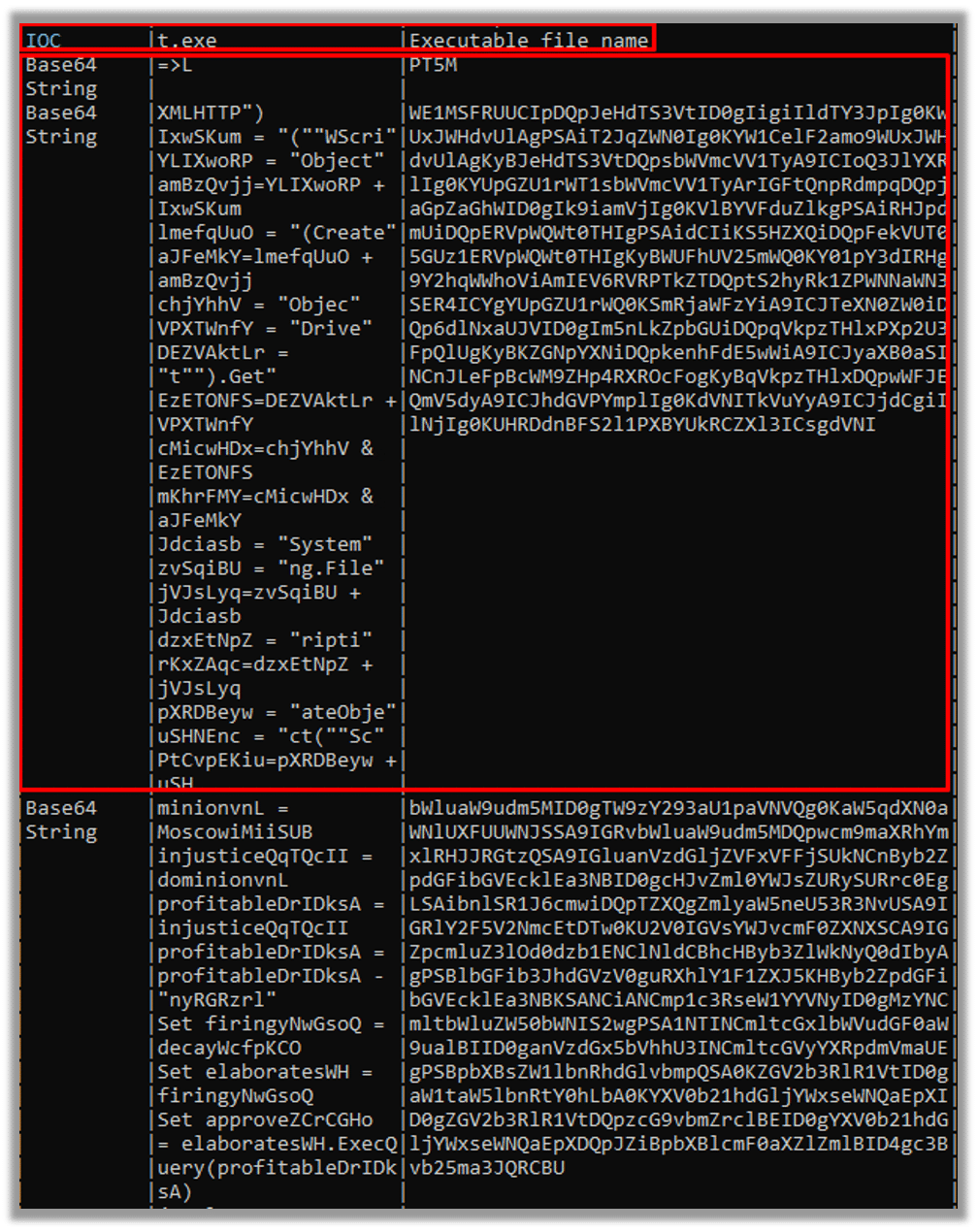
Following that, we employed leVBA to acquire the initial payload.
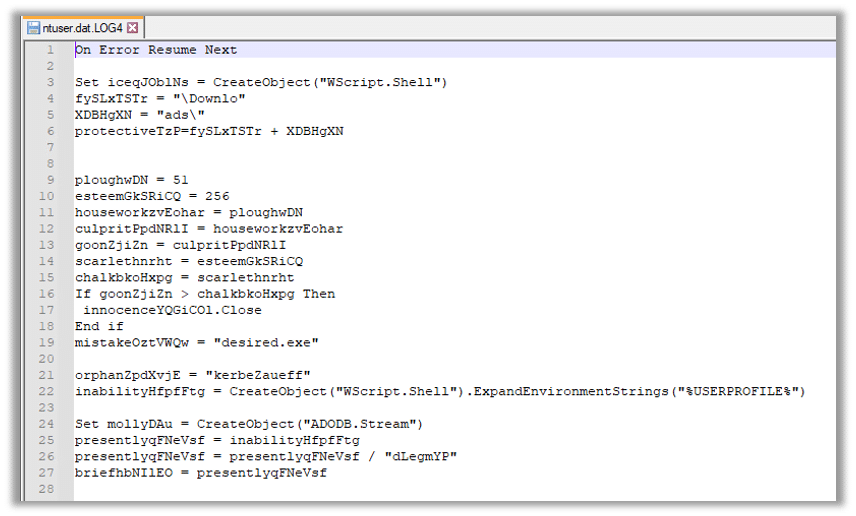
The script employs Wscript.exe to instantiate the Windows Shell object, facilitating the subsequent download of the backdoor from the C2 server:
The provided sample:
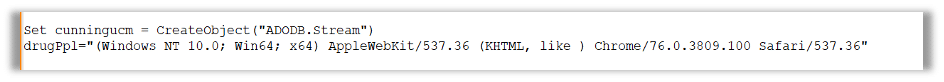
The code will utilize ADODB.stream to create an instance of the ADODB.stream object, which will be responsible for managing the binary data:
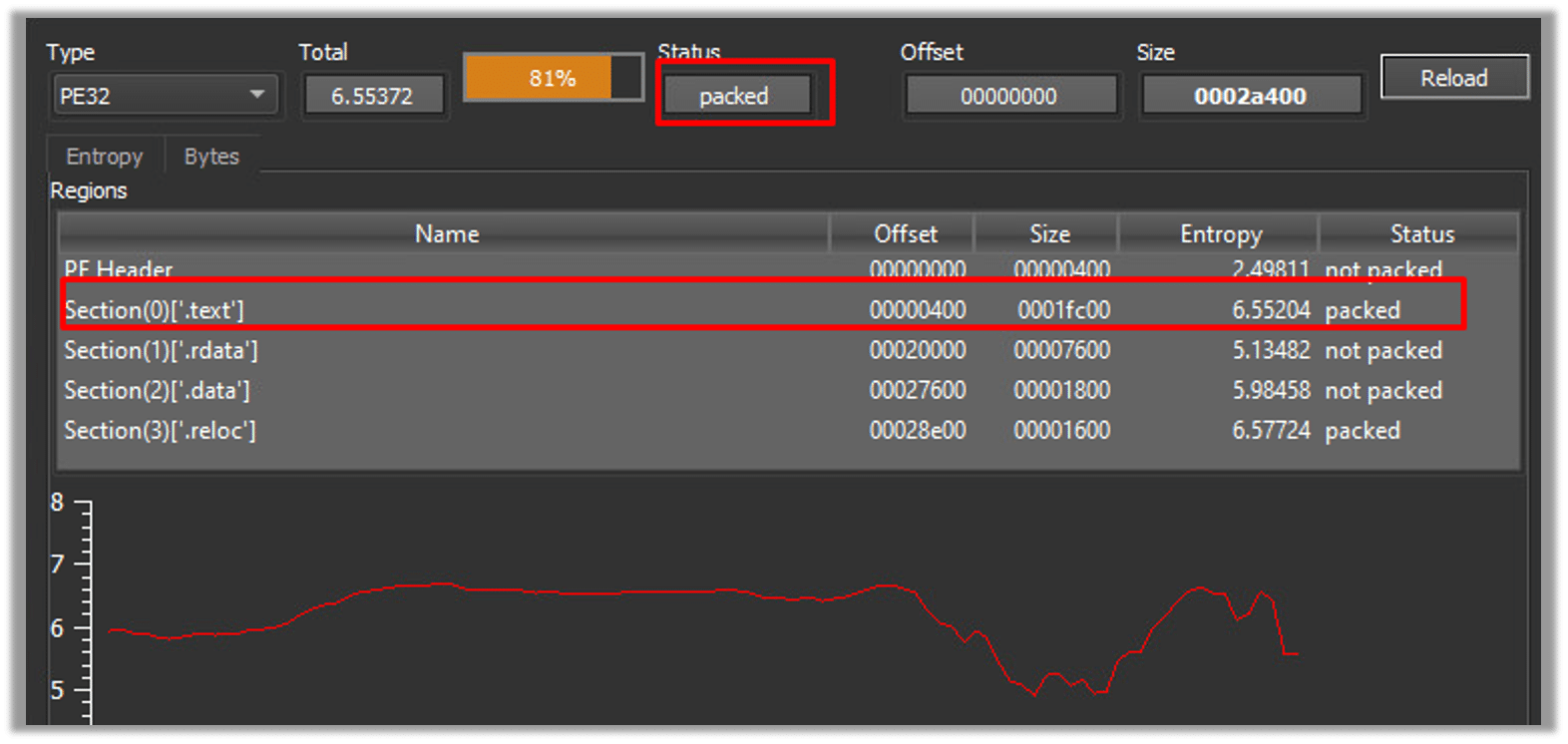
Upon analyzing the sample entropy, we determined that it has been packed with the intention of evading security vendors:
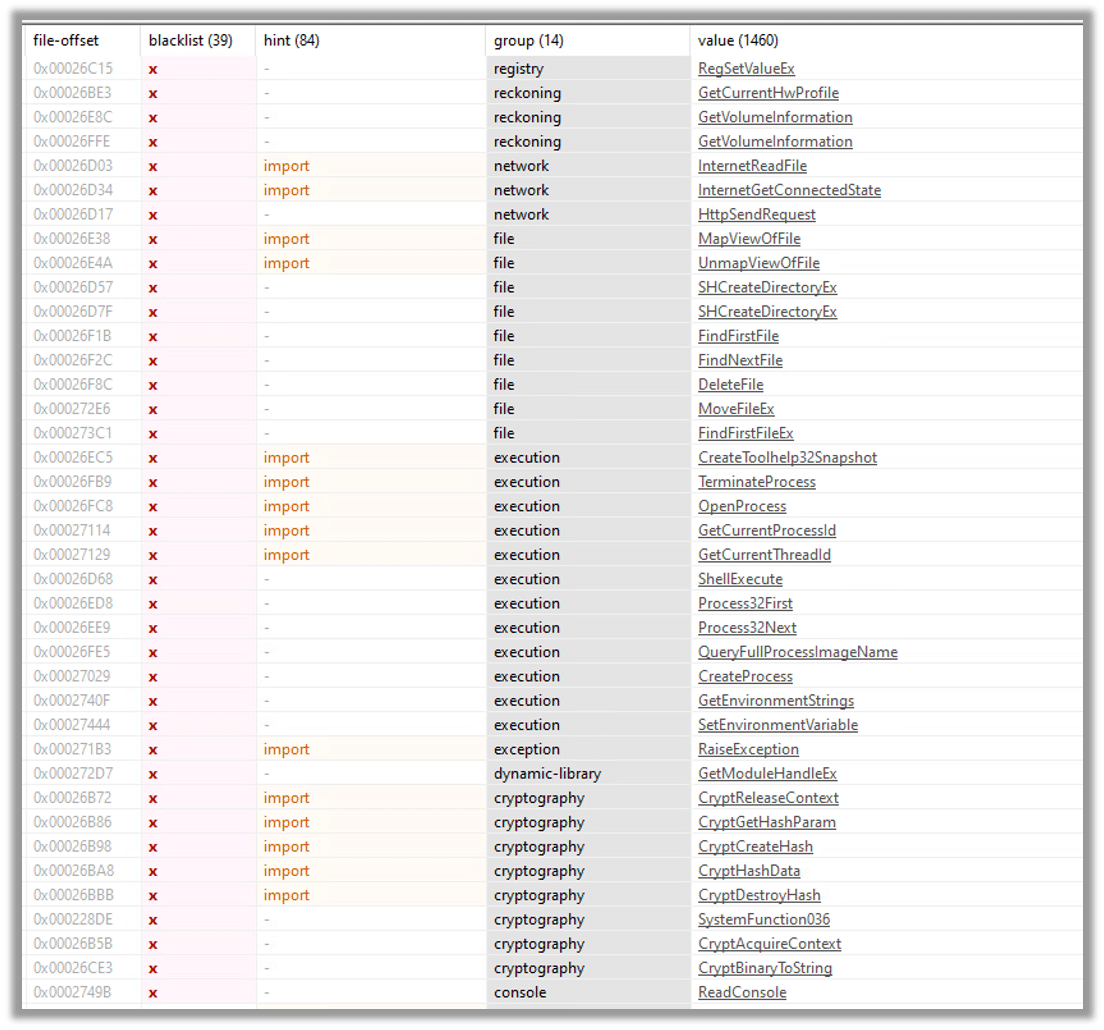
After examining the file using PEStudio, we examined the string section and applied a blacklist string filter, which resulted in the identification of five significant groups:
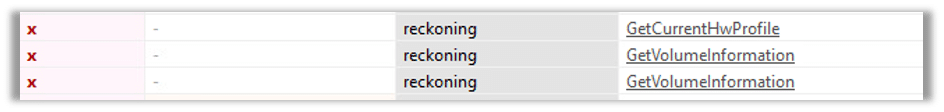
The first group is the reckoning group where we can see API’s such as GetVolumeInformaion and GetCurrentHwProfile, where GetCurrentHwProfile will retrieve information about current hardware profile of the system and GetVolumeInformaion is used to retrieve information about a disk volume.
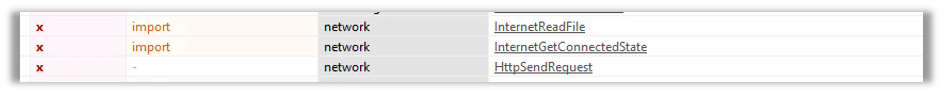
The second group is the network where we can see the API HttpSendRequest that is used to send an HTTP request to the C2 server where InternetReadFile is part of the WinINEt(Windows Internet) API which is a set of funtion for interacting with the internet.
And the WSAStartup and WSACleanup that are used to initialize and clear the Winsock library to allow applications to communicate to the C2 server using TCP/IP protocols:
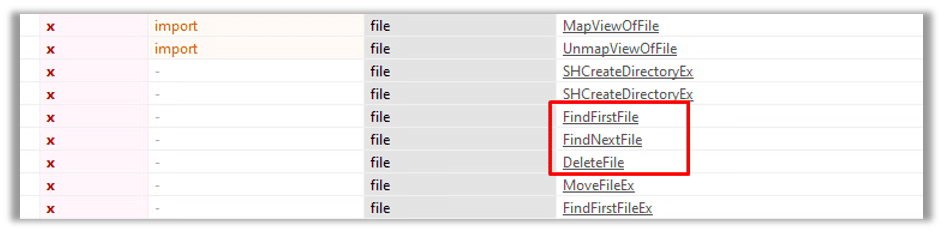
The third group consists of file-related operations that make use of functions such as DeleteFile, FindFirstFile, and FindNextFile to enumerate and potentially data:
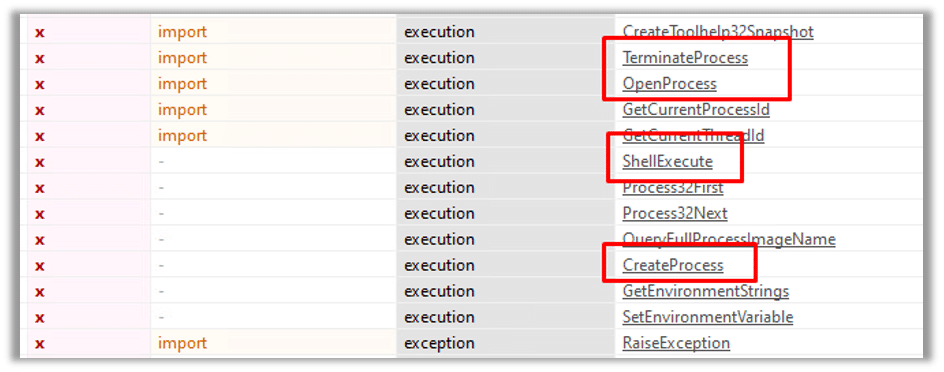
The fourth group is the execution group, which exerts control over the victim host by employing functions such as TerminateProcess, OpenProcess, CreateProcess, and ShellExecute:
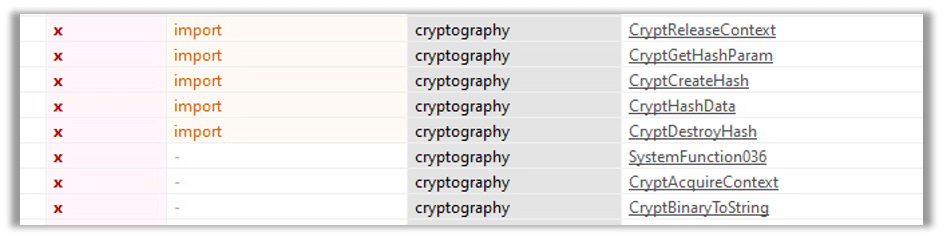
The final groupis the cryptography group, which leverages bcrypt.dll to encrypt data before sending it back to the command-and-control (C2) server:
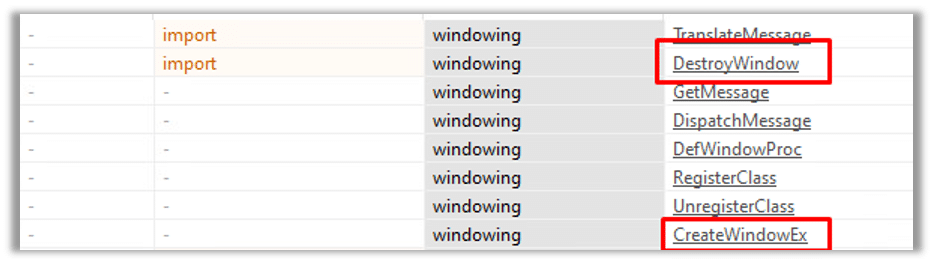
Another noteworthy group is the windowing group, which utilizes the CreateWindowEx and DestroyWindow functions to create windows for applications or to destroy/close existing windows:
Dynamic Analysis
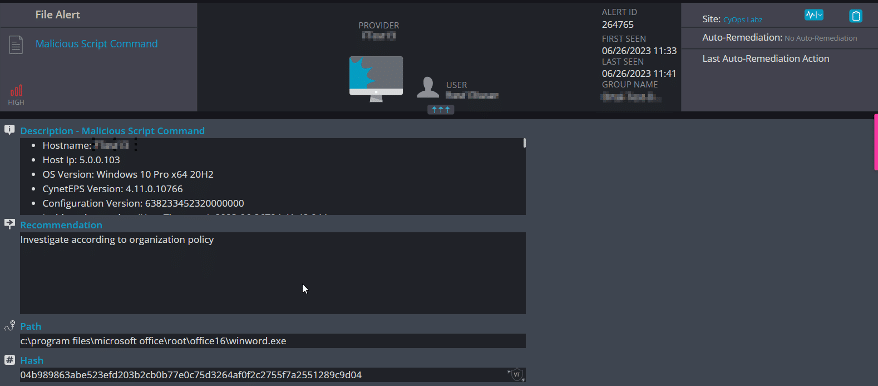
Executing the phishing document by clicking on the “Enable Content” button triggers the execution of the VBA payload:
Upon executing the payload, it proceeds to delete the file ntuser.dat.log4, which serves as a log file for storing user settings, preferences, and configuration data. Subsequently, a new file is created containing the payload:
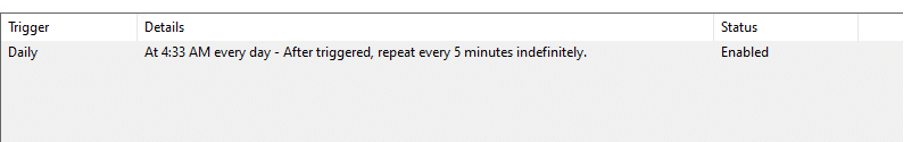
After creating the new ntuser.dat.log4 file, the malware proceeds to create a scheduled task that is set to run every day and repeat every 5 minutes indefinitely. This task ensures that the malicious activities of the payload are executed at regular intervals on the compromised system:
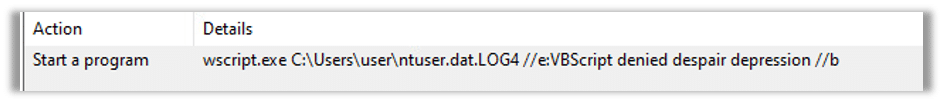
The payload that was written in the ntuser.dat.log4 file will be executed by the scheduled task created by the malware. The scheduled task is responsible for triggering the execution of the payload at the specified intervals. Once the task is triggered, it will launch the payload stored in the ntuser.dat.log4 file, allowing the malware to carry out its intended actions on the compromised system:
This is a well-known persistence technique used by malware to maintain a continuous connection with the command-and-control (C2) server. By creating a scheduled task that runs regularly and repeats at short intervals, the malware ensures that it can establish and maintain communication with the C2 server for command execution, data exfiltration, or receiving further instructions.
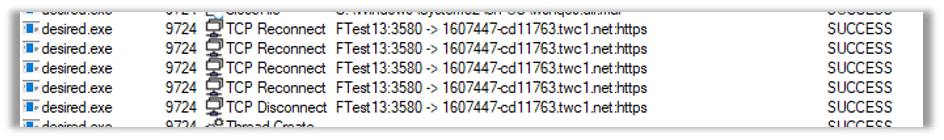
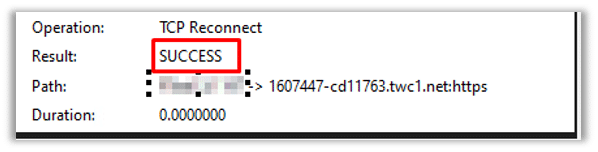
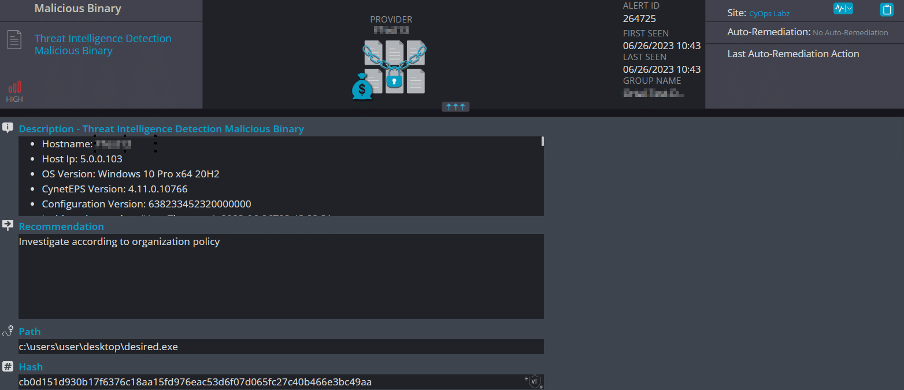
After establishing a connection to the command-and-control (C2) server and successfully downloading the Pterodo backdoor malware, it was immediately executed on the compromised system. This resulted in an immediate connection being established between the infected host and the C2 server. The purpose of this connection is to provide unauthorized remote access and control to the attacker, allowing them to carry out malicious activities on the compromised system. This can include executing commands, uploading and downloading files, gathering sensitive information, or performing other malicious actions as directed by the attacker:
The network packets captured during the communication with the command-and-control (C2) server revealed the presence of additional payloads that were intended to be dropped onto the victim’s host. These payloads are designed to further compromise the system and expand the attacker’s control and capabilities. The exact nature and purpose of these additional payloads may vary, but they typically serve to enhance the attacker’s access, persistence, or functionality on the compromised system:
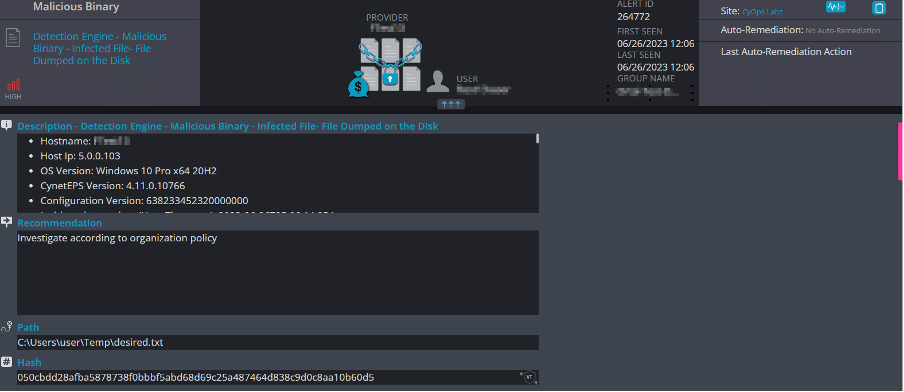
Upon successful execution of the Pterodo backdoor malware, one of its actions involves creating an executable file in a TXT (text) file format:
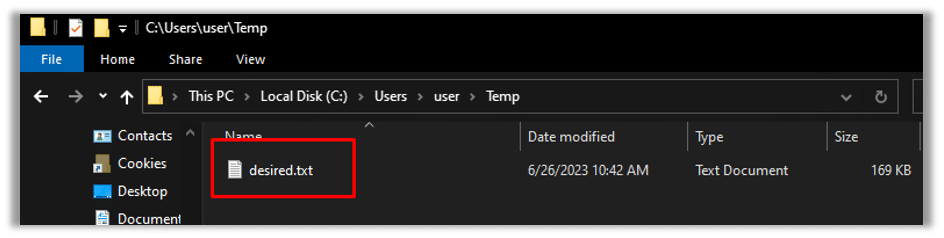
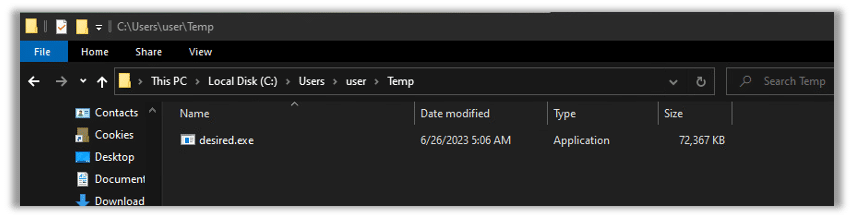
Subsequently, the created executable file will be stored in the system’s temporary folder:
Eventually, the file will undergo a format conversion from TXT to EXE and subsequently delete itself from its original location:
It will operate silently in the background, without drawing any attention:
During this time, it will retrieve and transmit data to the C2 server:
Cynet360 VS Pterodo:
CyOps and Orion teams are working around the clock to enhance detections by implementing IOCs, memory patterns, SSDEEP, etc.
As you can see below, we took an Pterodo sample and executed it in our labs.
Note that our environment action is set to alert only, so as not to interrupt the ransomware flow.
Creating the scheduled task:
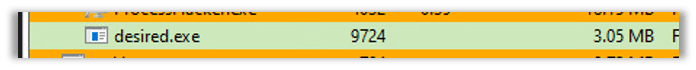
Pterodo sample dumped on the disk:
The txt file dumped via the malware:
Conclusion
The Gamaredon Group continues to create new variants for their Pterodo malware and improving their techniques as they go.
The Gamaredon Group APT (Advanced Persistent Threat) is a sophisticated cyber threat actor known for conducting targeted attacks on government organizations and defense contractors. They are recognized for their advanced malware capabilities and the use of social engineering techniques to gain unauthorized access to sensitive information. The Gamaredon Group APT poses a significant risk to the security and confidentiality of targeted entities, and organizations should implement robust security measures to protect against their malicious activities.