Reflections on M&A Cybersecurity Issues
The latest testimonial on the Marriot data breach throws another spotlight on the security risks M&A activity entails. As it appears, the high-profile breach was rooted way back in 2014, when attackers successfully infiltrated Starwood’s IT network. Later in 2016, when Marriot completed the acquisition of Starwood, it unknowingly acquired the breach as well. This is a good opportunity to zoom out of this specific case and reflect on M&A security issues in general.
M&A’s potential security challenges are obvious to understand, yet hard to address. The acquiring entity becomes accountable to the security of an alien environment with its own set of security products and practices that cannot be ripped and replaced.
The two main problems are these:
- Importing malicious presence: when you acquire a new network, you acquire the various threats that are alive in it. The gradual merging between the acquired system with and the native one exposes your systems to these threats.
- Ongoing visibility: there is practically no visibility into the new network. In most to all cases, it’s technically impossible to merge the networking infrastructure and so, the networks stay separate either permanently or throughout a very long migration period.
The Cynet Solution
Cynet provides total environment visibility into all components of the internal environment – user activity, file execution and network traffic – as well as to any malicious activity that might take place. As such it is a preferred solution for many large customers that need to maintain sound cybersecurity during and following M&A:
- Security assessment: to address the problem of importing malicious presence into a secure environment, Cynet provides a security assessment that leverages two core capabilities:
- Extremely rapid deployment – Cynet can distribute up to 50K endpoints in a single day
- Dissolvable execution – deployment mode in which a binary is pushed to the endpoint and runs as a service without writing any files to disk.
Combining the two capabilities provides a fast, powerful and non-intrusive tool to gain immediate insight into the environment’s security posture – indications to live attacks and exposed attack user and endpoint attack surfaces.
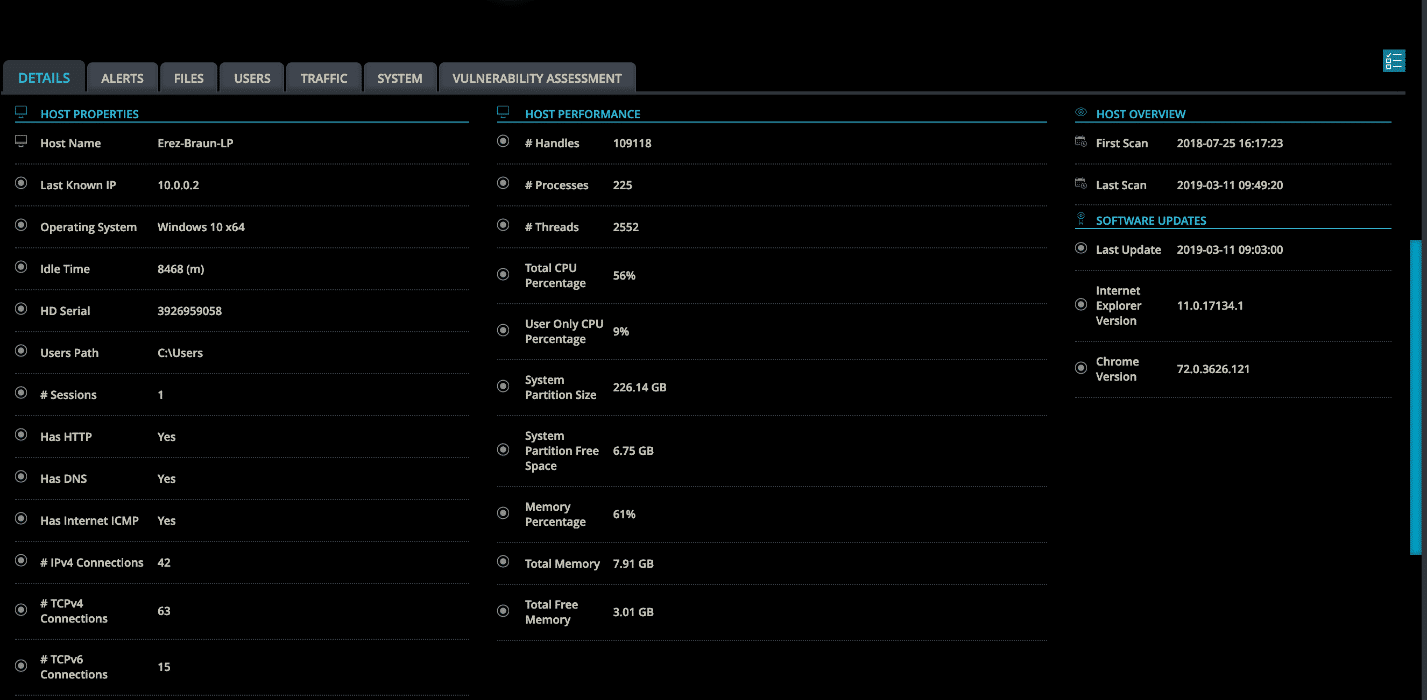
- Ongoing visibility: even when the new environment has been validated as clean from threats, there is still a need for ongoing visibility. Cynet’s light-weight agent continuously collects and aggregates network traffic, process execution and user interactions from all hosts, delivering real-time visibility into all operational activity in the monitored environment. Cynet is the only agent-based solution that continuously collects the full scope of the internal environment activity data as illustrated in the following examples:
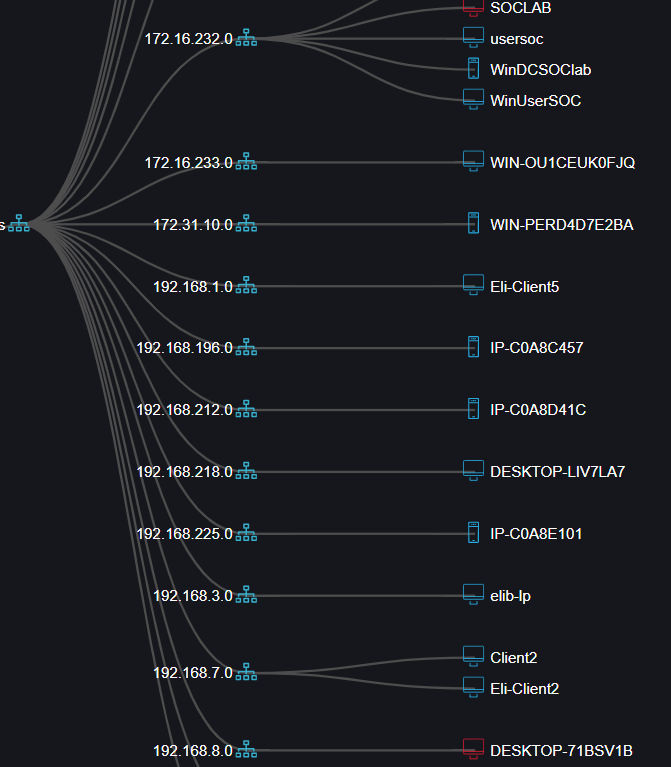
Cynet Network Topology View
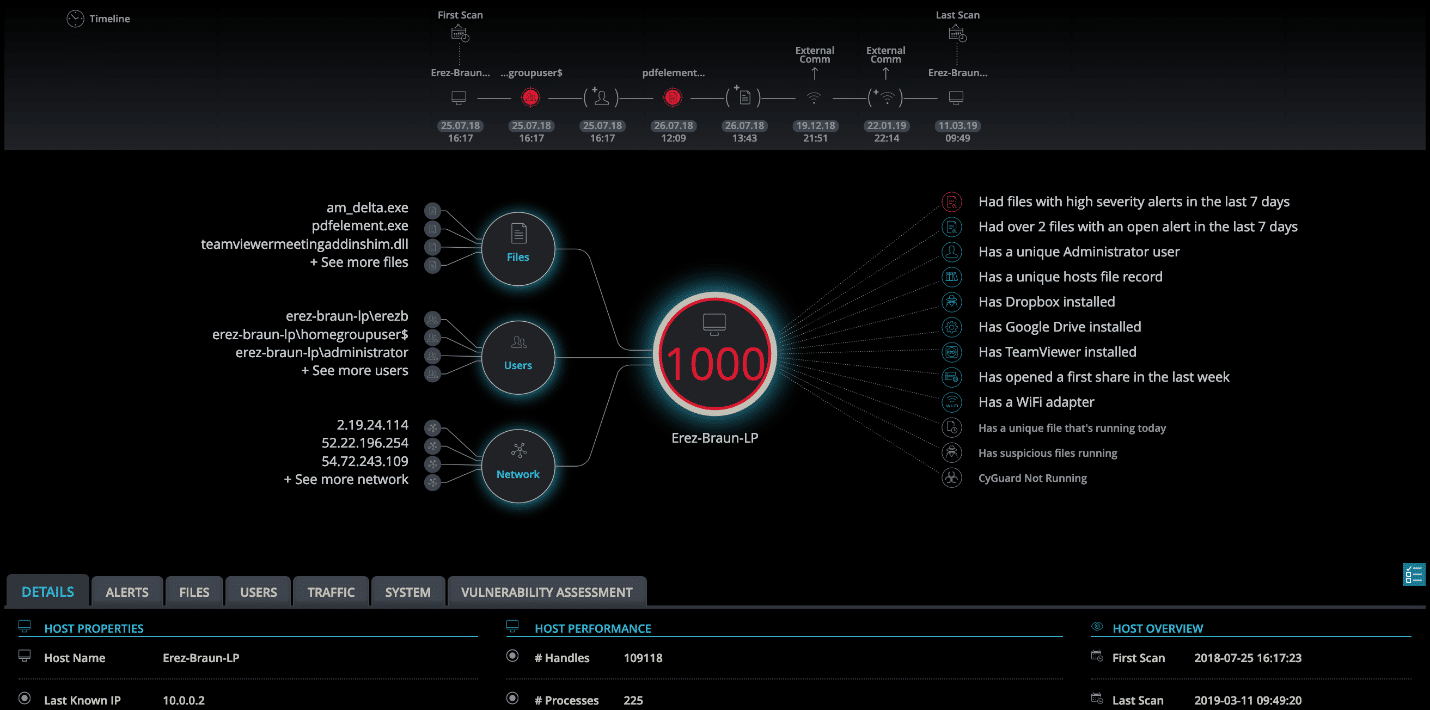
Cynet Single Asset View
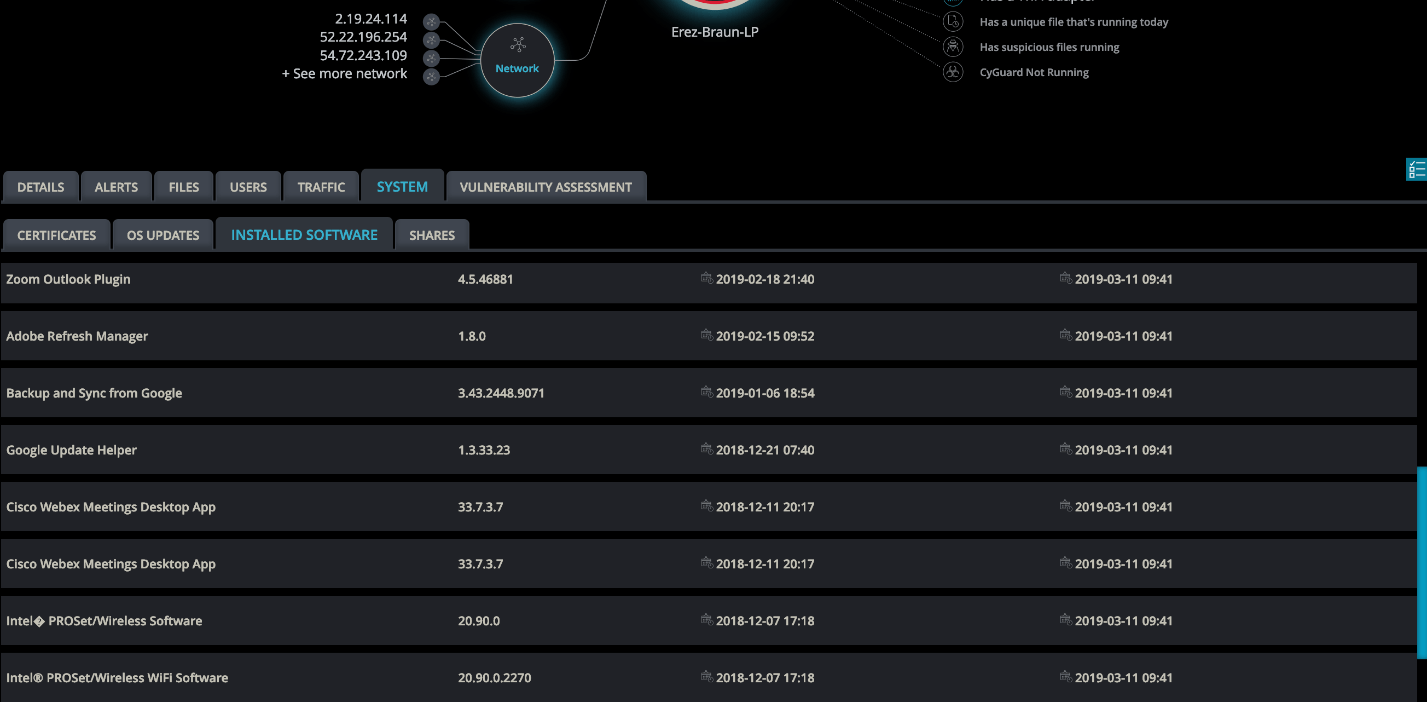
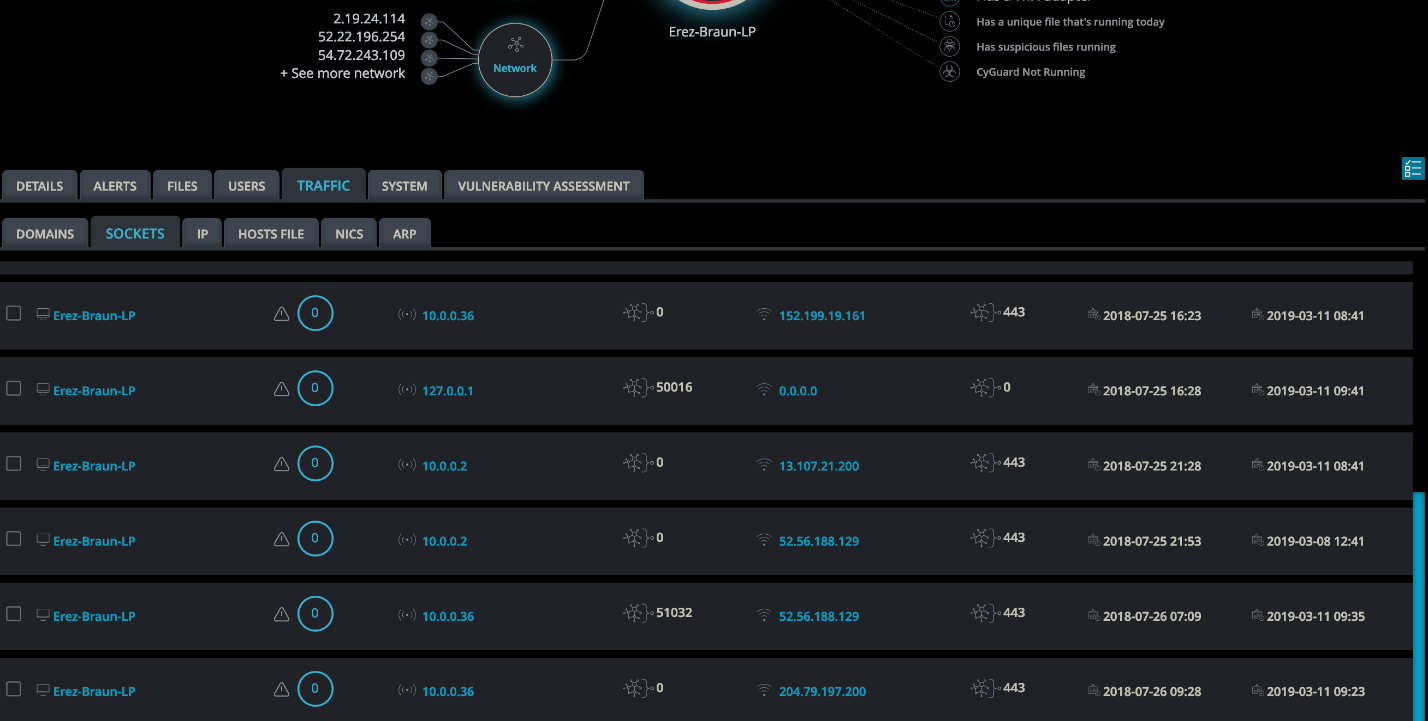
Cynet Single Asset Deep Dive
Cynet Single Asset Deep Dive
Cynet Single Asset Deep Dive
This granular visibility does not entail any change in the acquired environment networking infrastructure, providing IT and security teams with the best of both worlds – the ability to see, monitor and correlate activity across the native and added environments, and getting these abilities instantly through Cynet’s light-speed deployment.
Summary
Typically, any IT infrastructure that increases productivity introduces new, retroactively discovered security gaps. M&A serve well to illustrate how proactively taking security into account can greatly assist in gaining the productivity increase, which is the M&A’s initial target. The Cynet platform is an ideal tool for this.