September 2022 Ransomware Activity Report
Written by: Maor Huli
In the month of September, the following ransomware was introduced:
- Bl00dy
- Ballacks
- BISAMWARE
- BlackBit
EXECUTIVE SUMMARY
Orion is an integral department in Cynet’s research team that works around the clock to track threat intelligence resources, analyze payloads, and automate labs to ensure that our customers are protected against the newest ransomware variants.
In these monthly reports, Orion reviews the latest trends identified in Bleeping Computer – the most up-to-date website that summarizes the newest ransomware variants – and shares how Cynet detects these threats.
CYNET 360 AutoXDR™ vs. RANSOMWARE
Bl00dy Ransomware
- Observed since: Sep 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .bl00dy
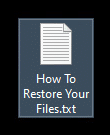
- Ransomware note: How To Restore Your Files.txt
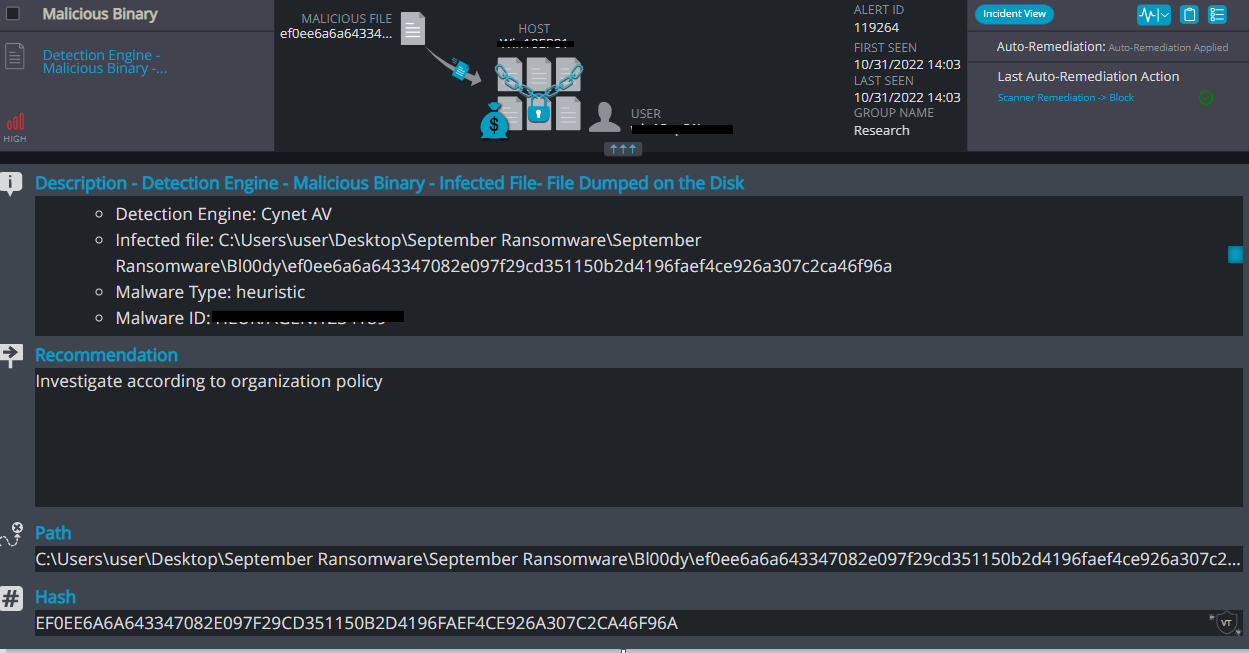
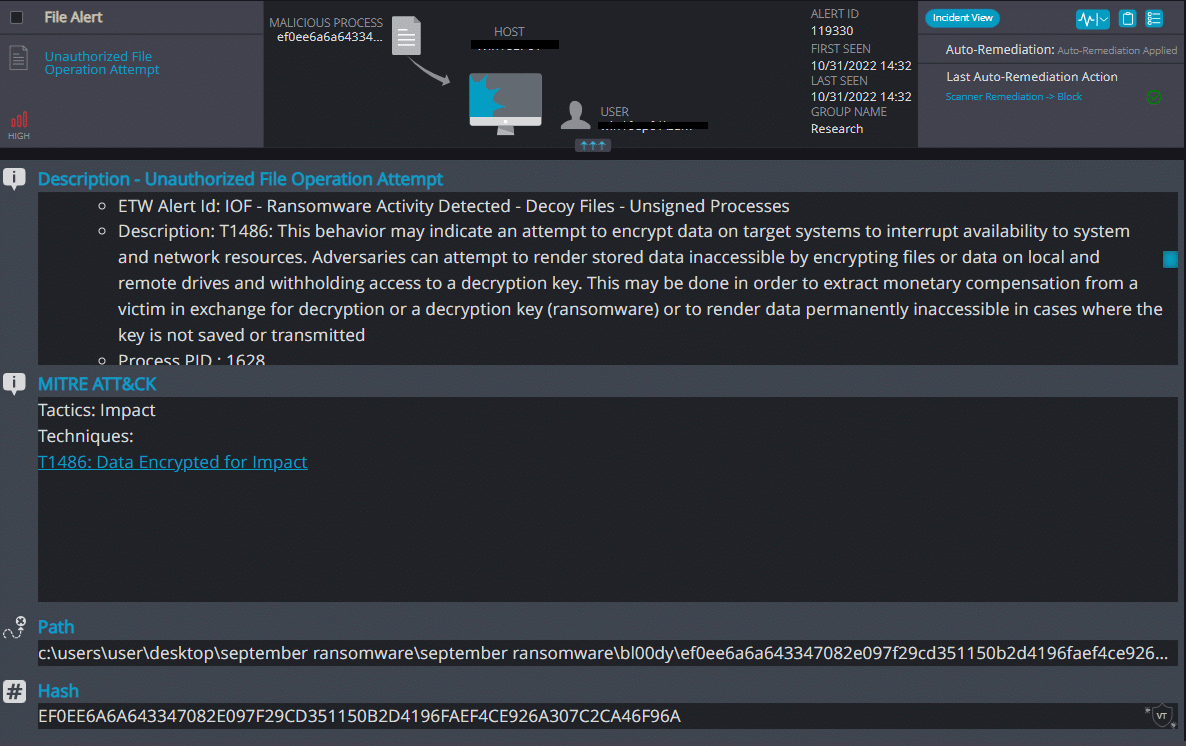
- Sample hash: ef0ee6a6a643347082e097f29cd351150b2d4196faef4ce926a307c2ca46f96a
Cynet 360 AutoXDR™ Detections:
Bl00dy ransomware renames the encrypted files with .bl00dy in the extension.
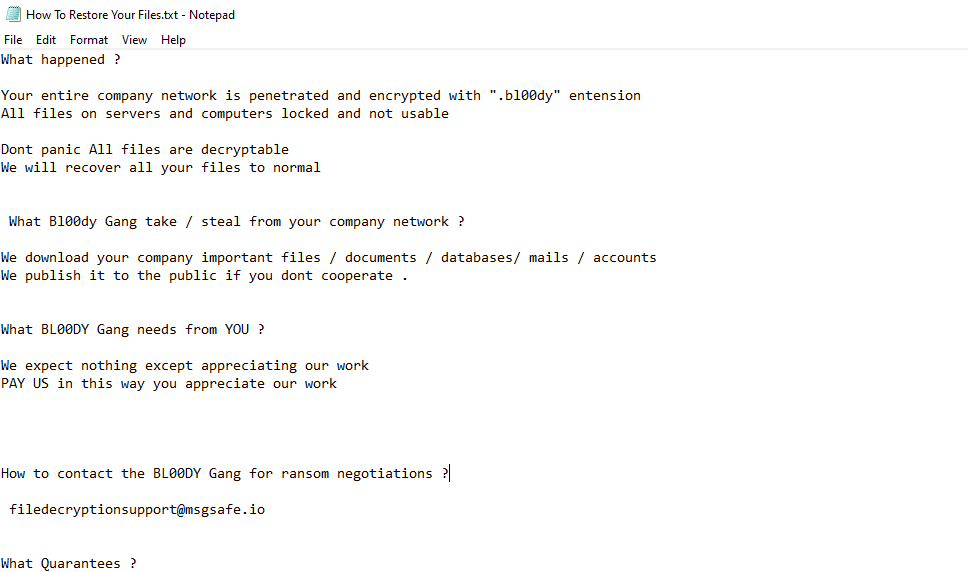
Once a computer’s files have been encrypted and renamed, it drops a note as “How To Restore Your Files.txt”:
The ransomware note contains general information, warnings, and the attacker’s email address:
Ballacks Ransomware
- Observed since: Sep 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .ballacks
- Ransomware note: ReadthisforDecode.txt
- Sample hash: 6e457720acc91317e6318ab1bcc053d67ea3b8082a0b22ea976f6fe299cc8f14
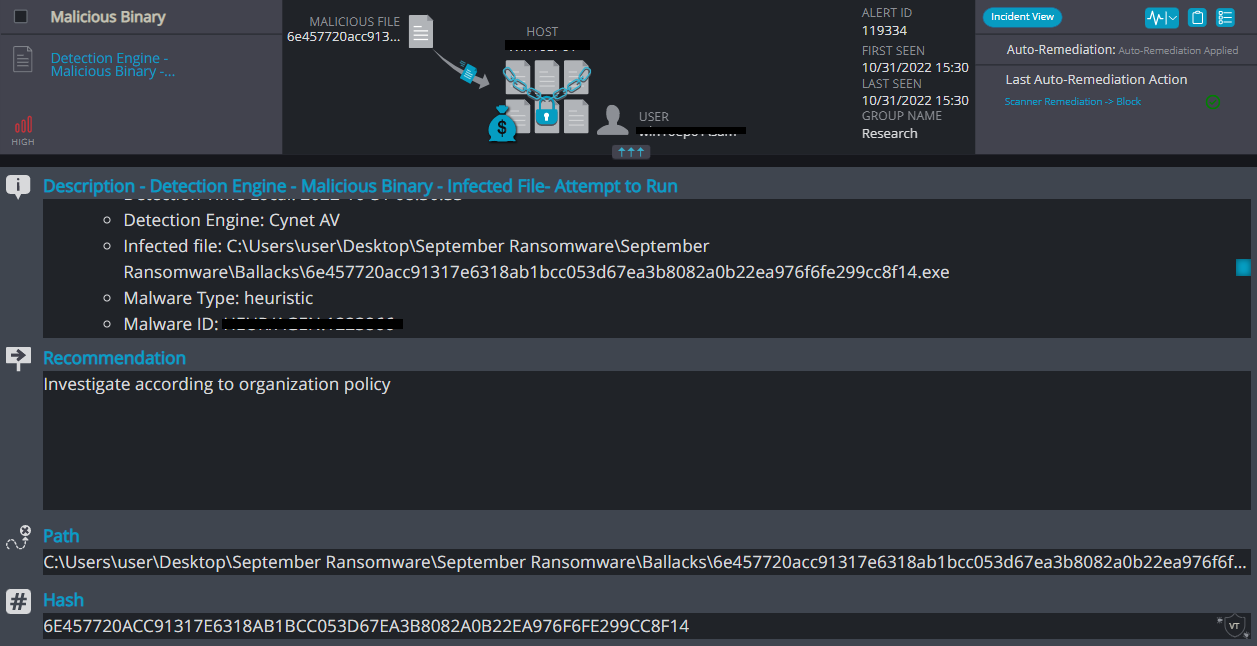
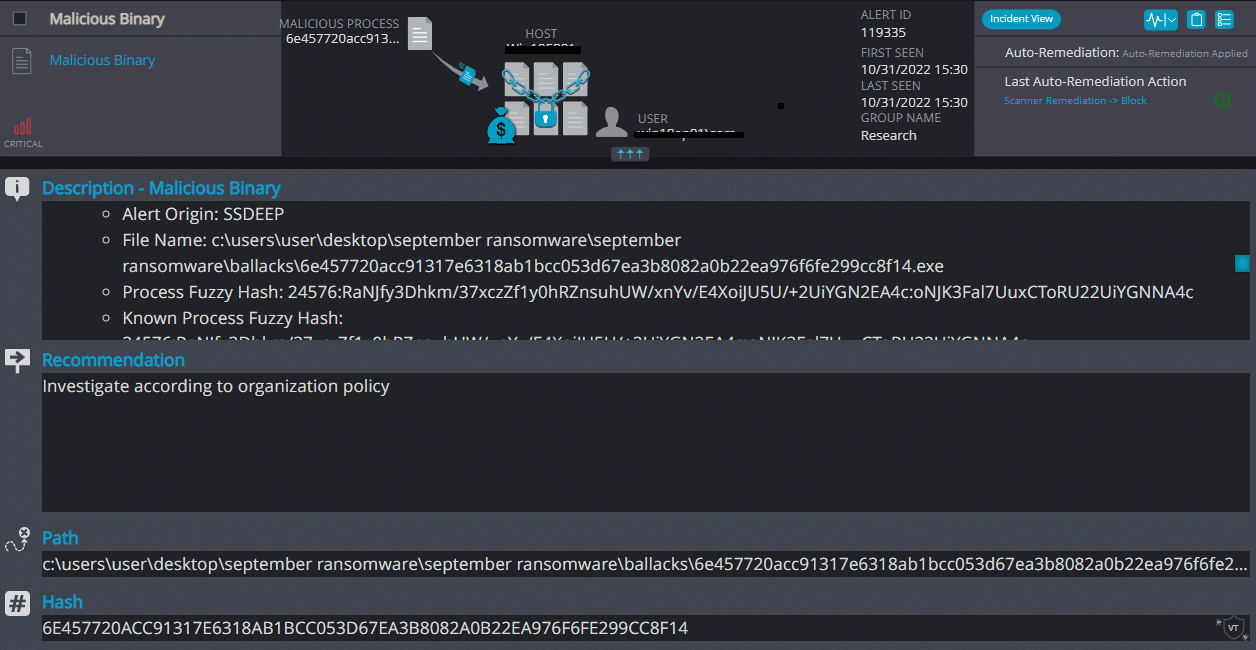
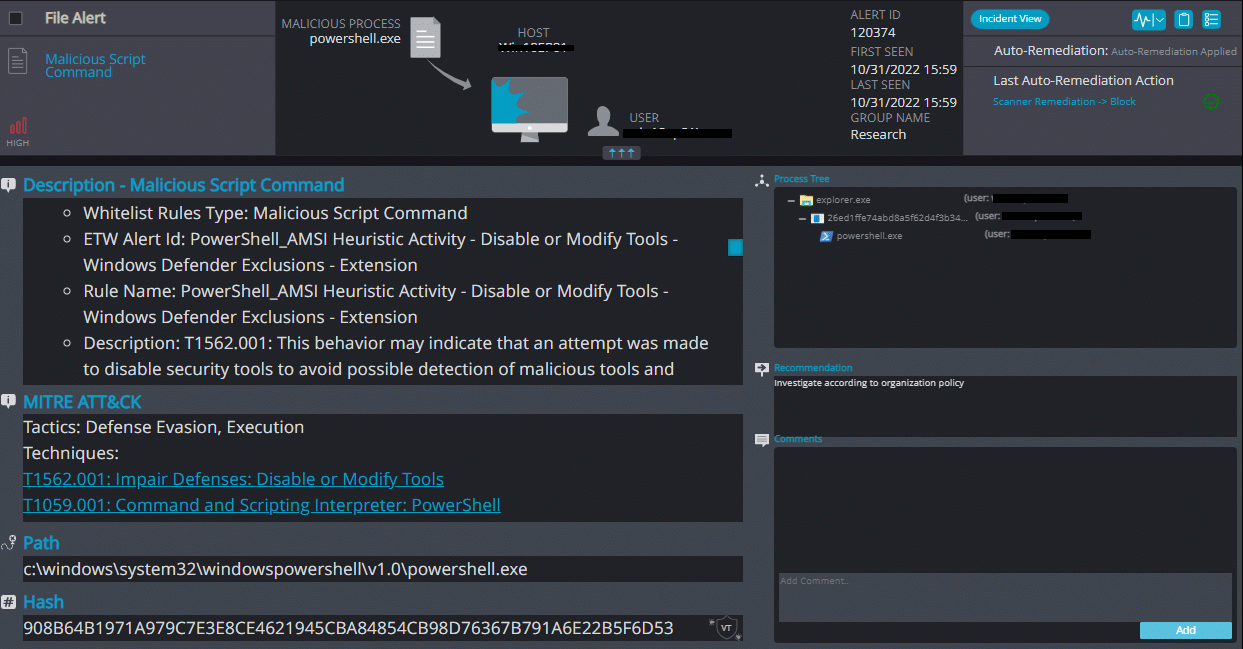
Cynet 360 AutoXDR™ Detections:
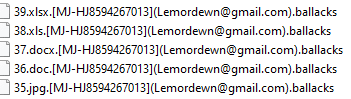
Ballacks ransomware renames the encrypted files with .ballacks in the extension:
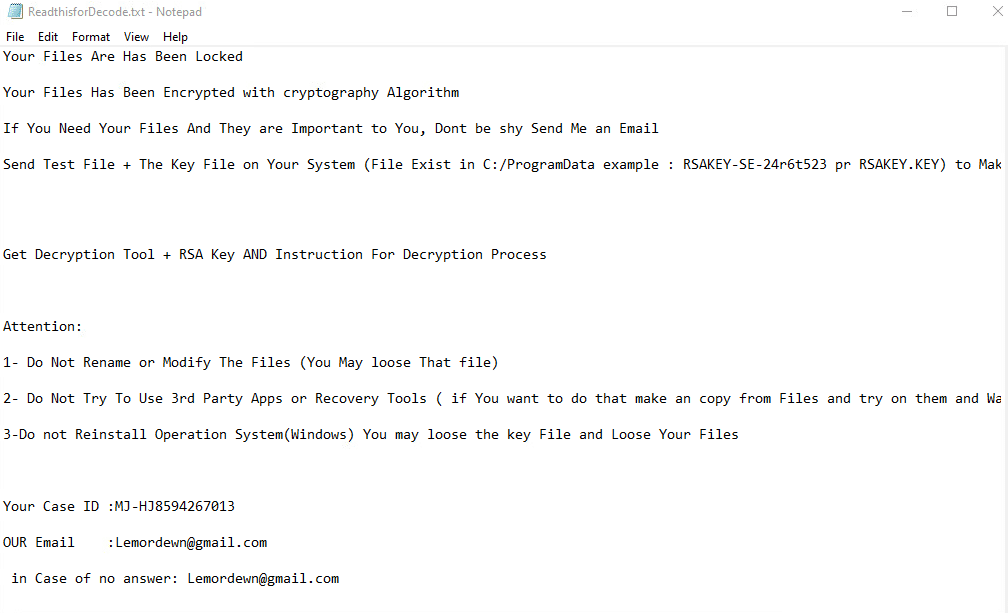
Once a computer’s files have been encrypted and renamed, it drops the ransomware note named ReadthisforDecode.txt:
The ransomware note contains general information, warnings, and the attacker’s email address:
BISAMWARE Ransomware
- Observed since: Sep 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .BISAMWARE
- Ransomware note: SYSTEM=RANSOMWARE=INFECTED.TXT
- Sample hash: 26ed1ffe74abd8a5f62d4f3b341a62ebb1a04d43e7ab9d64b9d283e184b35fd4
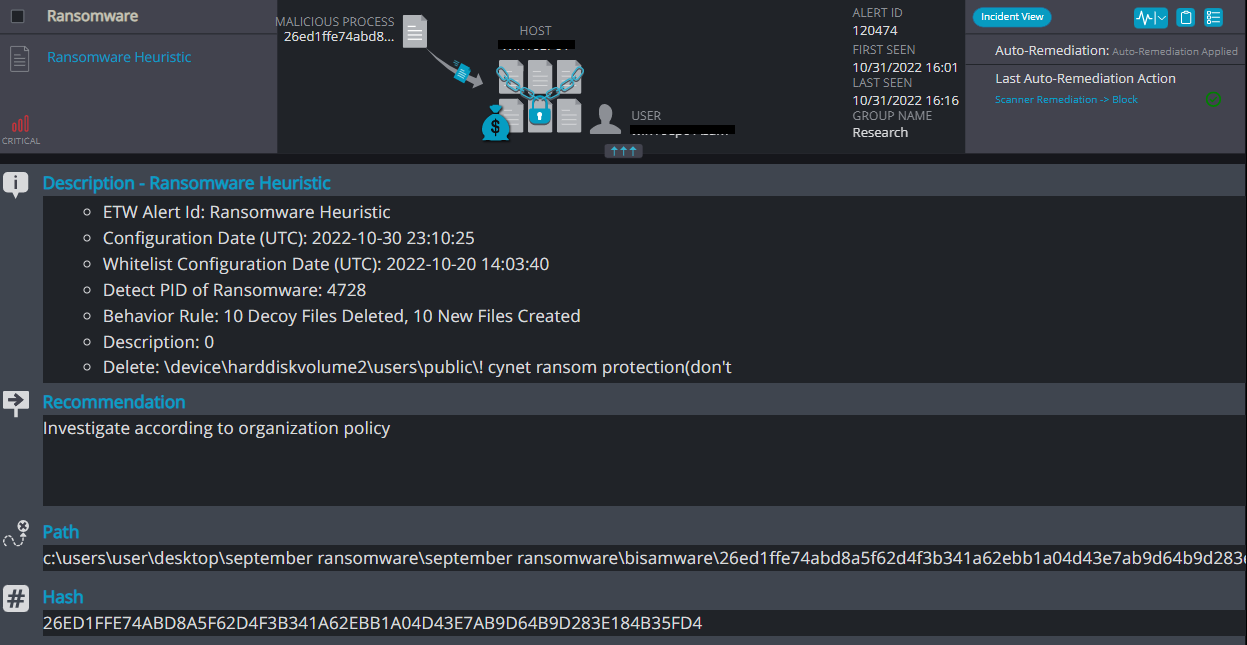
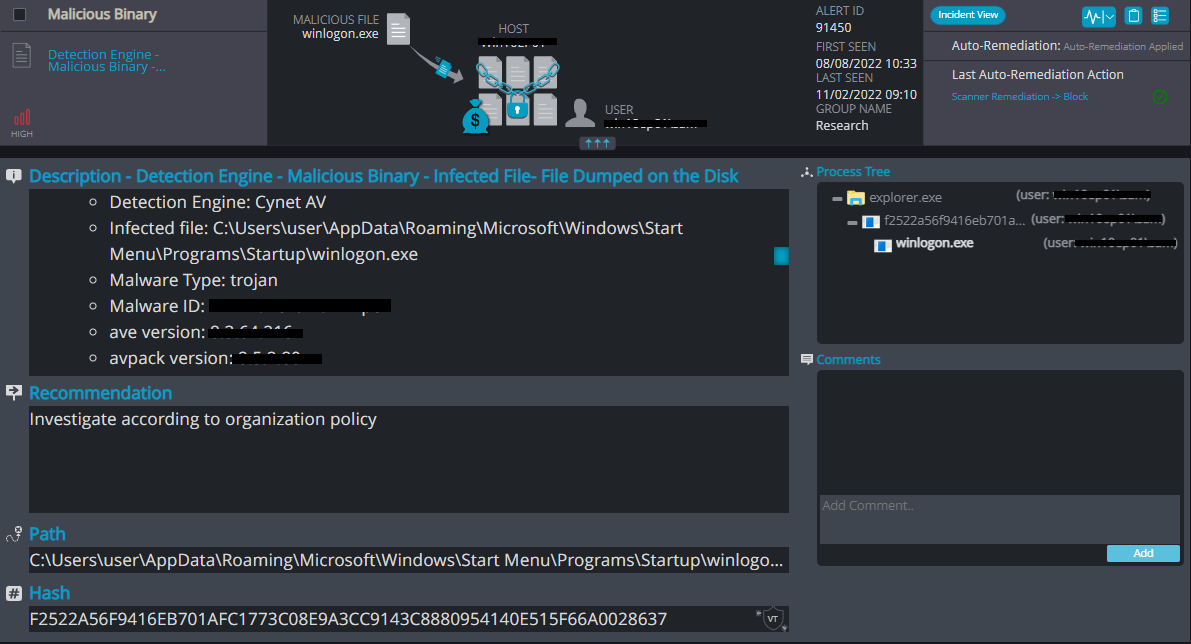
Cynet 360 AutoXDR™ Detections:
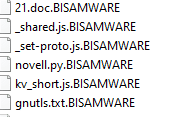
BISAMWARE ransomware renames the encrypted files with .BISAMWARE in the extension:
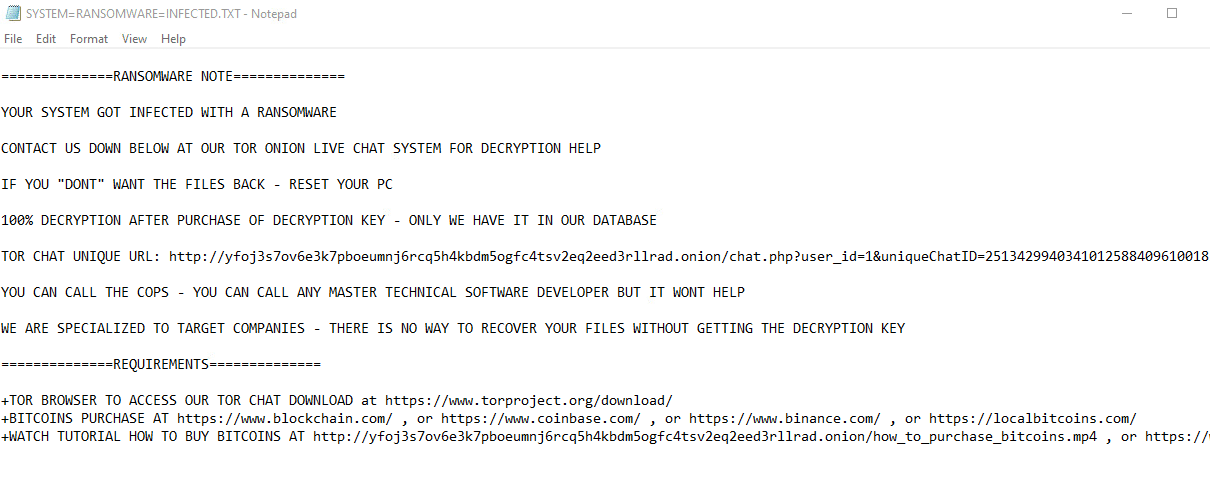
Once a computer’s files have been encrypted and renamed, it drops a note named: SYSTEM=RANSOMWARE=INFECTED.TXT
The ransomware note contains general information, warnings, and the attacker’s Tor chat:
- Observed since: 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .BlackBit
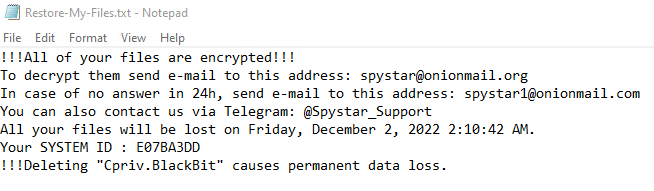
- Ransomware note: Restore-My-Files.txt
- Sample hash: 1d0930fed7eb72f1338b0aed0d47e72731cd599200d83058aec2fd9825fa71c8
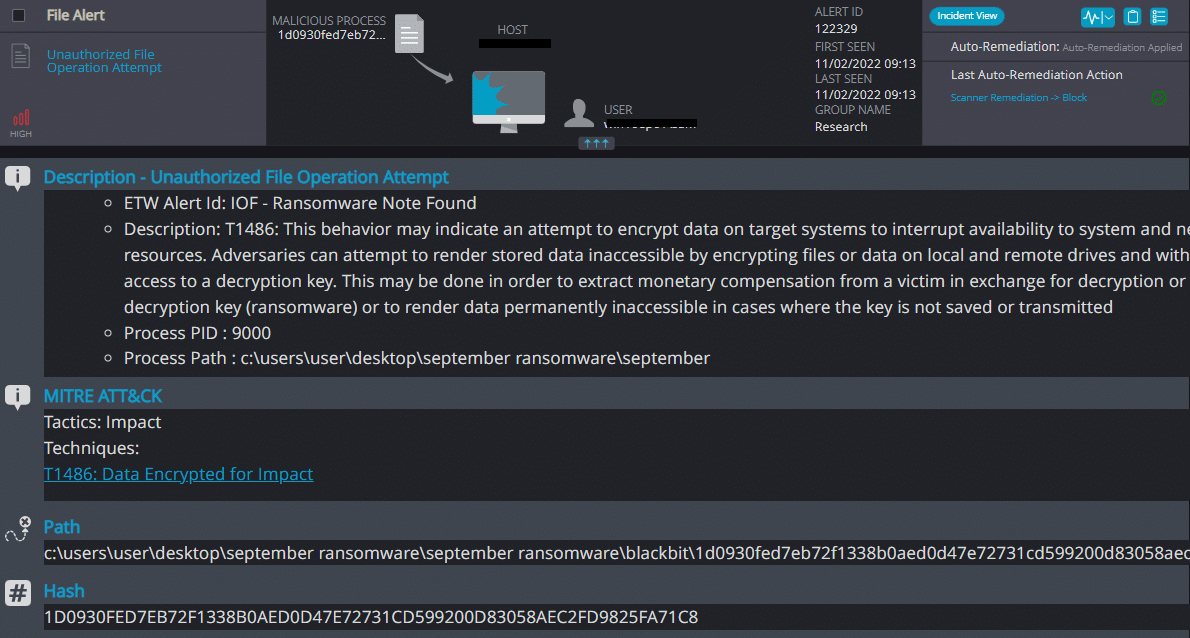
Cynet 360 AutoXDR™ Detections:
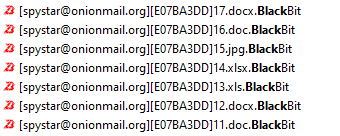
BlackBit ransomware renames the encrypted files with .BlackBit in the extension:
Once a computer’s files have been encrypted and renamed, it drops a note as: Restore-My-Files.txt
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains general information, warnings, and several attacker’s links: