Warning Signs That You May Be Under an APT Attack
For corporate cybersecurity professionals all around the globe, the threat of an APT Attack is something close to a nightmare. With a range of sophisticated and clever techniques, hackers can chip away at a company’s valuable information with dangerous consequences.
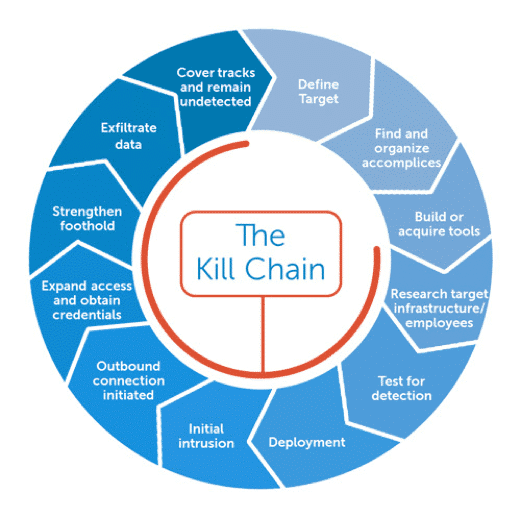
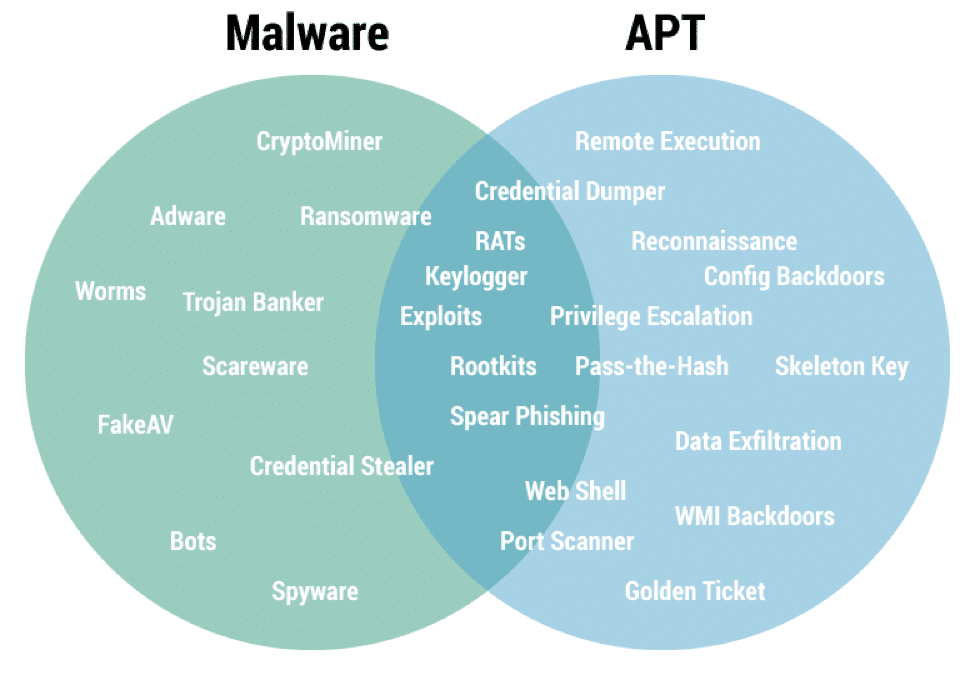
Advanced Persistent Threat (APT) refers to a multi-base attack on a network that belongs to an organization. They tend to enter by avoiding detection and then collecting a large amount of data that contains protected information.
Since APTs are generally varied and very complex, it makes the threat more dangerous as it originates from zero-day malware or phishing campaigns as well. This is the reason why it is important to understand the nature of an APT attack and how to defend against it.
APTs often Exist in Groups
In most circumstances, an APT Attack doesn’t come from an individual hacker due to the sheer amount of advanced resources needed. These hackers work in groups with their persistent methods of slipping into an organization’s network undetected and then slipping out quickly.
Since cyber-attacks are prolonged operations, they need to be stealthier than ordinary hackers. The development of an APT Attack may take months and more than that to be successfully deployed.
(Source: https://sectechno.com/aptsimulator-toolset-to-simulate-apt-attack/)
5 Warning Signs that you may be under an APT Attack
1. Elevated Log-ins at Unusual Hours
This is a clear sign since APT Attackers tend to start their process by aiming at an authentication database. This is where these hackers focus on stealing credentials and reusing them to expand. The threat grows out by infiltrating into an individual computer to a whole system environment within a matter of hours. By finding accounts with the higher privileges and permissions, the hackers use those accounts to get into the surrounding assets of the network. Since these cybercriminals operate from different corners of the world, this attacking process usually occurs at the random and odd hours of the day.
2. The Backdoor Trojans
Trojans can help indicate an APT Attack. They allow access to a compromised system even if the login credentials are changed. It is normally used through the social engineering threats, but it tends to spread rapidly during an APT Attack even when it is hidden. If several employees have been tricked into opening malicious attachments, it is a better option to check for more clues about an APT Attack.
3. The Unusual Flow of Data
One of the major red flags for an ATP Attack is the unusual and large quantities of data being transferred from internal sources. This information can go along from a system to a system or a server to another server. Another warning sign would be detecting some data flow into an unusual location or out of it. It can also include an email login from another country.
4. Odd Data Bundles
The stolen data is often gathered in the internal collection points by the ATP Attackers before it is sent to an external network. If large GBs of data starts to appear in relatively odd places, then it should push you within preventative action immediately. What is more alarming than this case is having unusual data compressed and placed within your network when it has nothing to do with your organization.
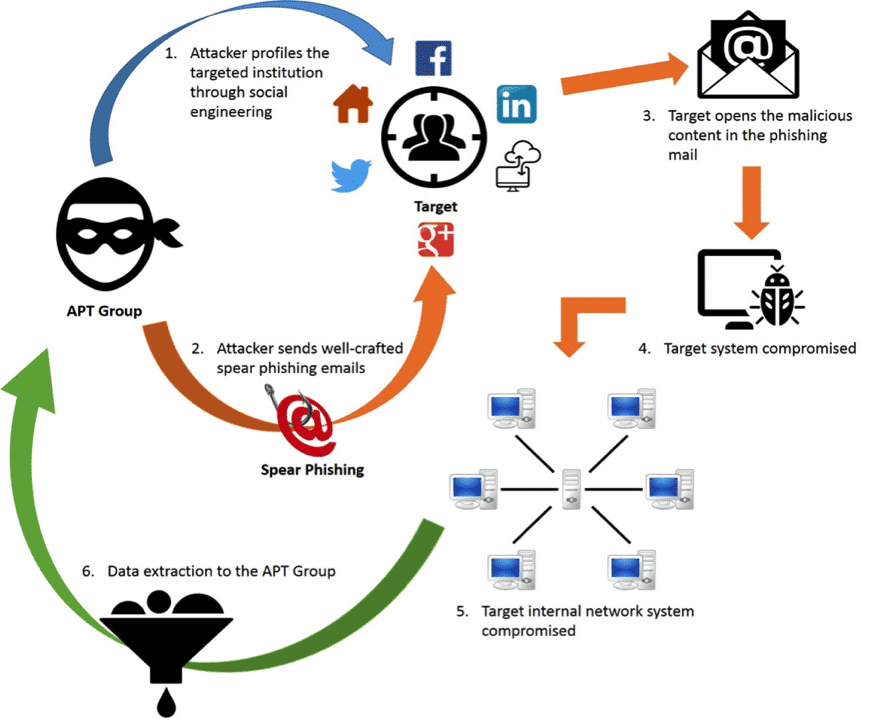
5. The Spear Phishing Campaigns
It is well-known that over 90 percent of the ATP Attacks deal with spear-phishing campaigns in the face of the company’s employees. It involves malicious URL links and executable codes as well. These phishing emails target the people of high value within the organization, such as the CEOs or the leaders of significant projects.
This is a major red flag when malicious email makes use of information that is related to hackers. Typically, such an email would contain some relevant information about an ongoing project, and it would seem to be sent by another one of the team members.
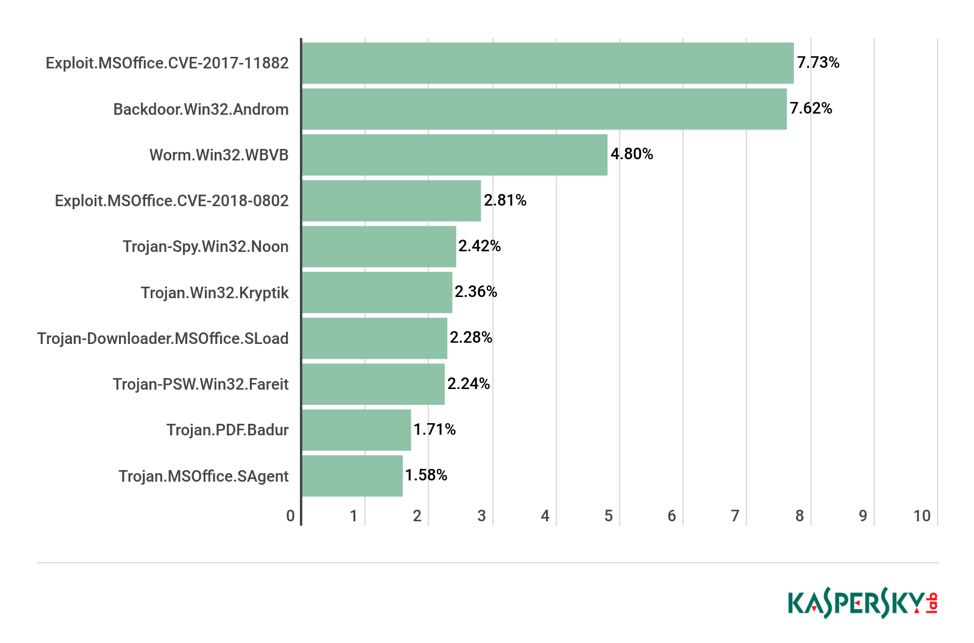
How to detect an APT Attack before the damage is done?
APT engineers tend to leave different signs behind after an attack, according to InfoWorld’s Grimes. Their clues are different than ordinary hackers because they often approach an organization through slow and persistent infiltration rather than with a sweeping force.
Third-party notifications help in discovering an intrusion or an APT attack rather than the victims finding it out directly. According to CSO Online, this is what happens about ninety percent of the times when infiltration occurs.
(Source: https://www.secureworks.com/blog/general-apt-attacks-new-defenses-against-advanced-malware)
The use of External Servers in an APT Attack
An APT attack involved a series of processes, and one of them is the bundling of data on another server before they move it. This is where a pattern is created that is easily detectable by the Data Security Professionals. This can be done by searching for the data in the most unusual places or the compression formats as well.
APT Hackers utilize ‘Pass-the-Hash’ tools
Pass-the-Hash hacking tools are used by cybercriminals to crack large sets of passwords that have been stolen. They allow attackers to snatch hashed user credentials, which are reused to deceive the authenticating systems.
They are often found in certain cases because the concerned individuals tend to forget to delete these tools. If they are found then, it might easily indicate that they were possibly involved in an APT Attack.
(Source: https://securityaffairs.co/wordpress/41325/cyber-crime/isaca-apt-report-2015.html)
Defense against an APT Attack
Hackers use multiple backdoors
The usual cyber defenses of firewalls and antivirus software are not very effective in protecting against APT Attacks. They may help the organization by noticing and removing an immediate threat, but that isn’t enough because these advanced hackers have several backdoors. These backdoors aid them in returning whenever they prefer.
Higher monitoring for threats
One of the first and foremost steps in protecting your network against an APT Attack is by improving the monitoring of your system and having improved detectors in the infrastructure of your network. Having strong authentications that are also multi-factor can help in making sure that only authorized users can obtain sensitive information.
Improved Awareness of Security
Organizations can also protect themselves by limiting access to valuable data. This makes sure that the staff members are doing the duties that are associated and linked with their jobs directly. This enforces the security of the organization, along with creating more awareness among the responsible people.
Training for Security Awareness can help the employees and executives to detect a spear-phishing attack and protect themselves from it. However, an advanced cybersecurity provider can easily help in pushing up complex defenses to stop APT Attacks before their objectives are fulfilled.
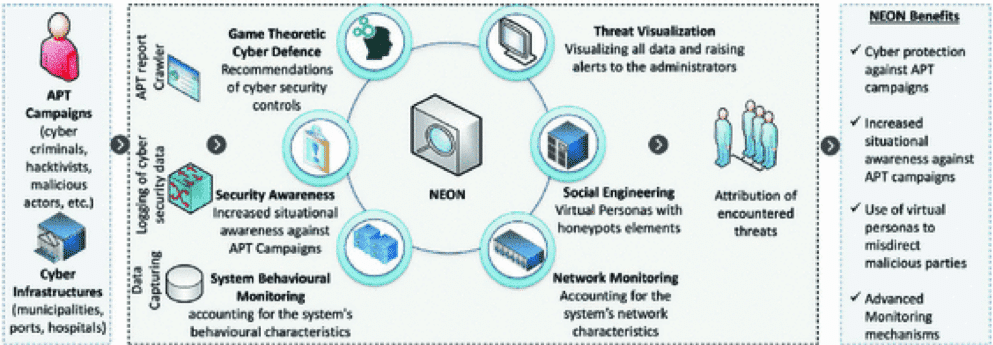
It takes more than a simple awareness of cybercrimes to protect an organization from facing an APT Attack. This is because the hackers involved in this crime are highly skilled and focused on achieving their objectives. The organizations that are better at handling APTs are often prepared by educating their employees and limiting access to sensitive data. According to resources, they also have well-developed response plans.
 (Source:
(Source: