Yet Another MS CVE: Don’t Get Caught In The Storm!

A new vulnerability (CVE-2023-36884) “Office and Windows HTML Remote Code Execution Vulnerability” was announced by Microsoft on July 11. The vulnerability allows an attacker to perform remote code execution if a victim opens a weaponized Microsoft Office document. This vulnerability, which affects Windows and Office products, has reportedly been used to attack NATO Summit attendees since June. The exploitation of this vulnerability has been linked to a threat actor known as Storm-0978 that targets defense and government entities in Europe and North America.
Tune in to our on-demand webinar for more details and expert analysis!
Microsoft does not yet have a patch for the vulnerability. Fortunately, Cynet Zero-Trust logic was able to block the zero-day vulnerability on client devices. Zero-Trust logic allows legitimate activities to take place on the user device, while any other activities are blocked. The Zero-Trust logic is based on deep research of the OS operation and different trusted applications. By practicing “Know Good, Detect Evil”, Cynet can detect the newest attacks in the wild.
Don’t wait for the next exploit!
Book a demo now and boost your defenses against potential threats.
It’s critical to have robust detection and prevention mechanisms in place that protect against zero-day vulnerabilities. There is simply no way for software developers to prevent the software flaws that enable zero-day vulnerabilities, as has been proven by the constant onslaught of zero-day attacks despite all the best efforts by the software development community. Any business that lacks zero-day exploit protection introduces real, yet unnecessary, risks to their organization.
Cynet’s customers are protected and we are monitoring this vulnerability and will provide updates on any developments and measures that need to be taken to mitigate the threat.
Our Cyber Security teams are also working around the clock to add additional detection capabilities to mitigate this vulnerability. Cynet customers should enable the following settings, and make sure they’re set to prevention-mode, to protect against this vulnerability:
- Antivirus
- Memory Protection Mode
- File Operation Protection
- ADT – Behavioral Heuristic
Customers aligned with Cynet’s Best Protection Practices already have these settings enabled and no additional action is required.
The CyOps team is available 24/7 for any question or concern and will gladly assist with a timely resolution to any issue.
Technical Information
This vulnerability was being exploited by the Russian-backed Storm-0978/DEV-0978 group, also known as RomCom based on their backdoor name.
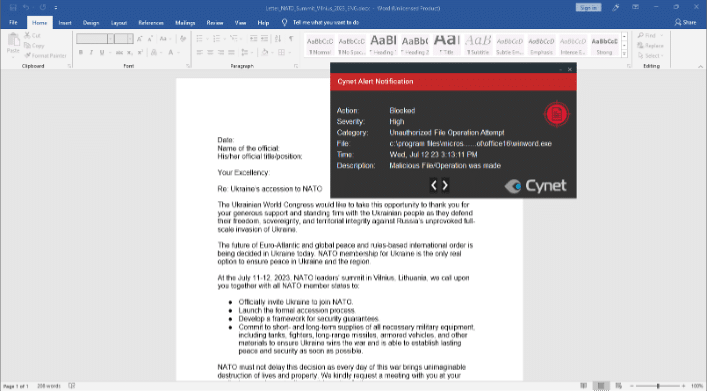
Here is an example of the weaponized office Word document that masqueraded as information about the Ukrainian World Congress:
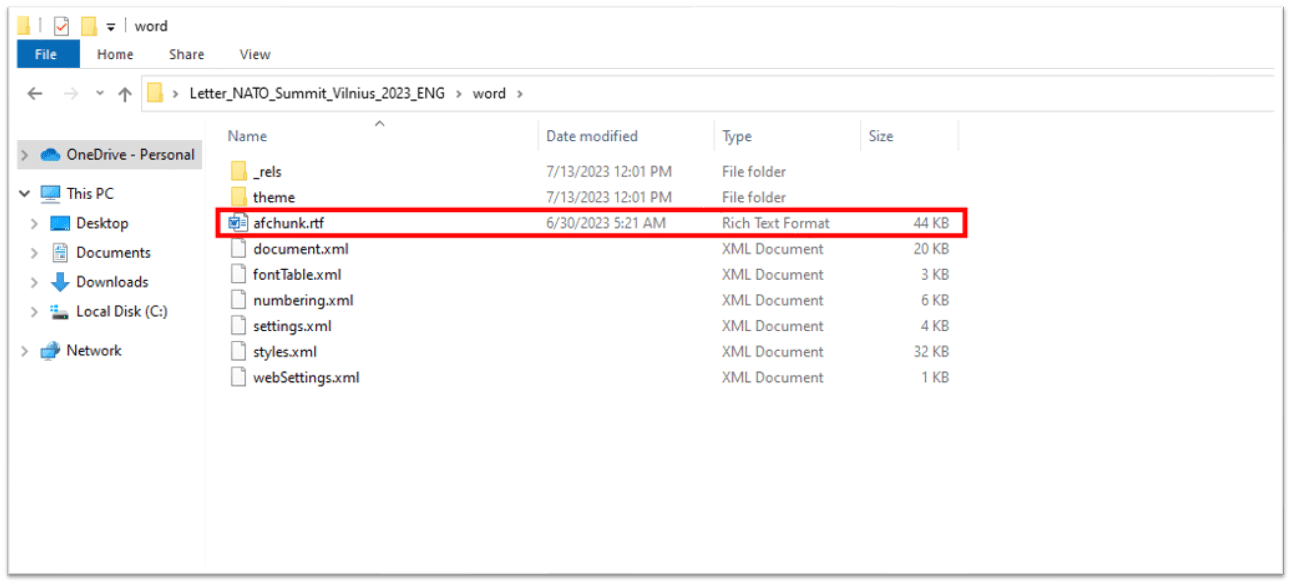
The weaponized office Word document contains a crafted RTF which has some embedded files. By unzipping the malicious document you can find the following artifact:
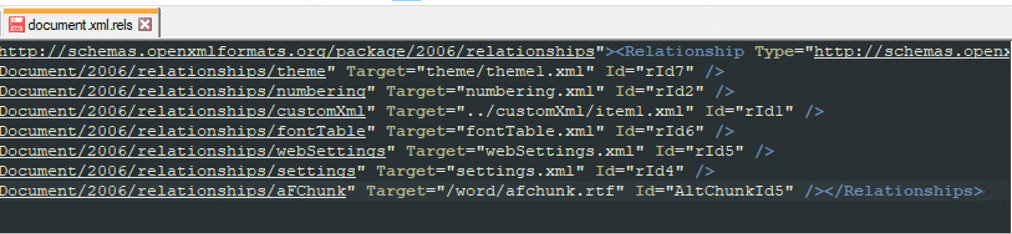
The content of the “document.xml.rels” targets the rtf file, automatically loading it and executing the hidden code.
Once the RTF payload is loaded and executed (when the victim opens the masqueraded Word document), an OLE object from the RTF connects to the C2 IP server of the threat actors.
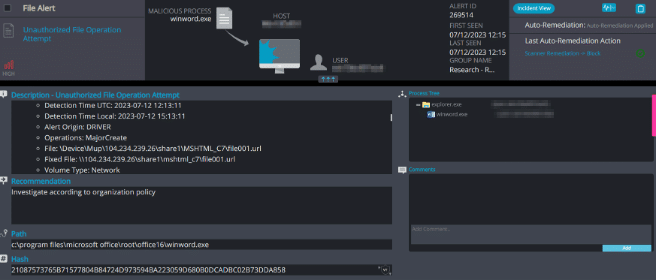
Cynet 360 detected and prevented the malicious network connection, as presented it in the alert information:
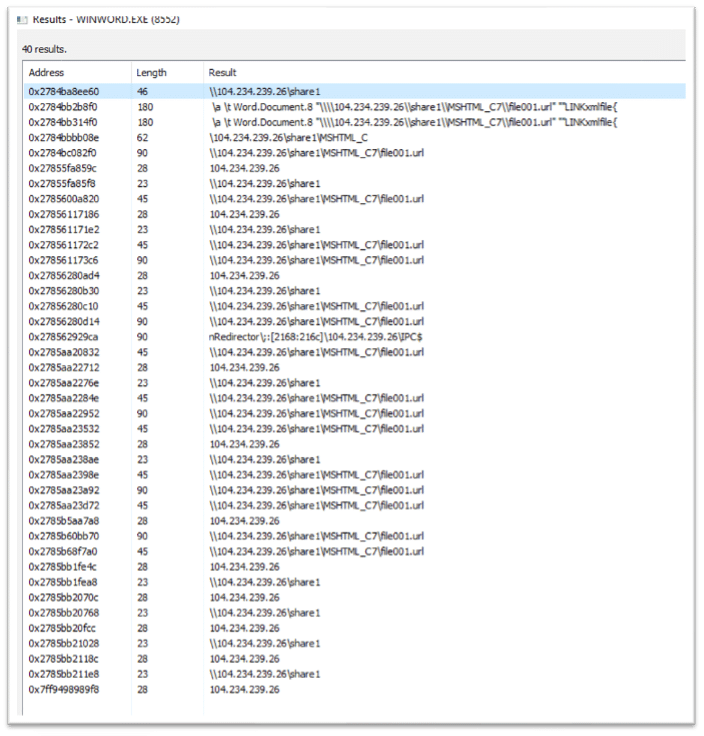
In the alert, we can see the C2 IP address with an SMB connection which attempted to read and execute the “file001.url” file from the attacker C2.
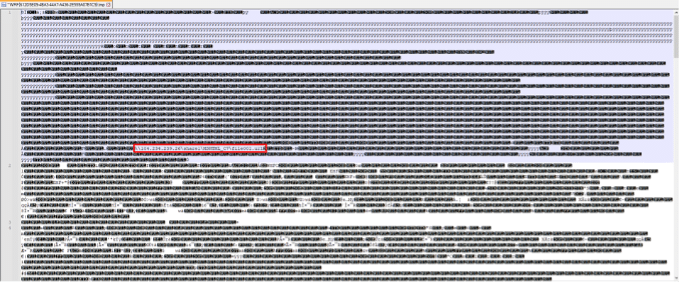
The network artifacts can be extracted from the WinWord process memory:
During the execution flow of the RTF payload, we spotted that a file was written to the disk. This file contains another artifact that is related to the SMB connection:
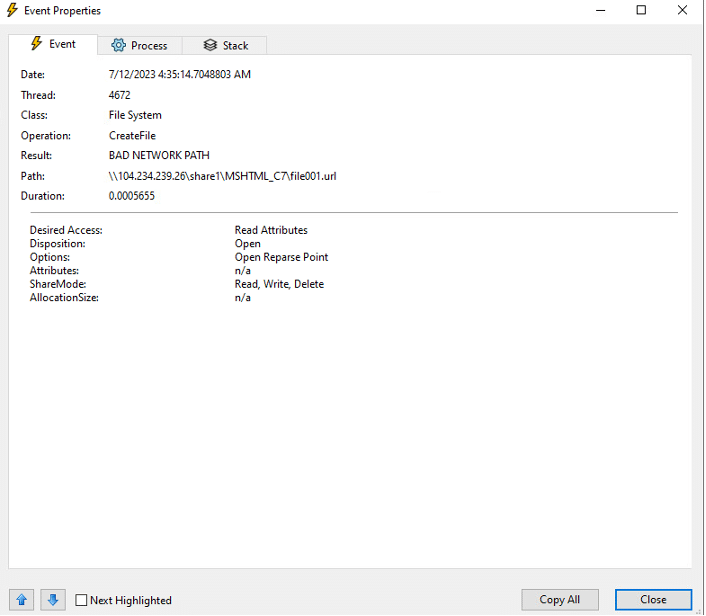
Here are the events recorded by Promon during the execution:
The interesting event presents CreateFile (read action) for an SMB share controlled by the threat actors:
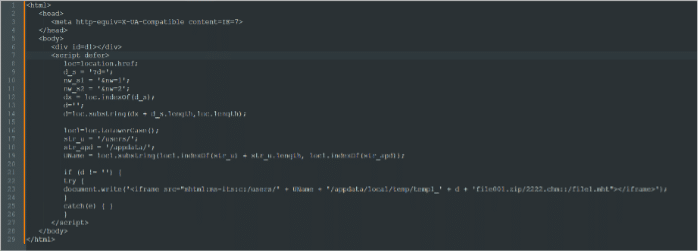
This is the second stage payload, “file001.url.” The file contains HTML content appended to the document, with Follina-style msdt handler execution inside an iframe.
The above execution flow allows threat actors to execute malicious code with minimal user interaction (the user only needs to open the malicious document once) and from this point the threat actors can bring their own malware to the compromised host.
How to stay safe against CVE-2023-36884:
- If your organization is using Microsoft 365 apps (version 2302 or later), you are already protected.
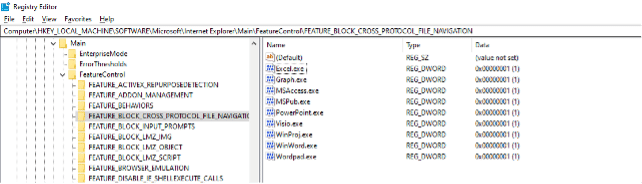
- Set the FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION registry key to avoid exploitation.
Go to HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION in your registry editor
Create the following keys as a type of REG_DWORD and set their values to 1:
- Excel.exe
- Graph.exe
- MSAccess.exe
- MSPub.exe
- PowerPoint.exe
- Visio.exe
- WinProj.exe
- WinWord.exe
- Wordpad.exe
Or run the following commands as administrator to add them:
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “Excel.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “Graph.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “MSAccess.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “MSPub.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “PowerPoint.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “Visio.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “WinProj.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “WinWord.exe” /t REG_DWORD /d 1 /f
reg add “HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATION” /v “Wordpad.exe” /t REG_DWORD /d 1 /f
After creating those keys, no OS restart is required, but the application restart is necessary. Please note that, although this step will help mitigate exploitation, it may impact the regular functionality of certain use cases for those applications.
Indicators of Compromise
a61b2eafcf39715031357df6b01e85e0d1ea2e8ee1dfec241b114e18f7a1163f
e7cfeb023c3160a7366f209a16a6f6ea5a0bc9a3ddc16c6cba758114dfe6b539
d3263cc3eff826431c2016aee674c7e3e5329bebfb7a145907de39a279859f4a
3a3138c5add59d2172ad33bc6761f2f82ba344f3d03a2269c623f22c1a35df97
07377209fe68a98e9bca310d9749daa4eb79558e9fc419cf0b02a9e37679038d