Introducing Cynet Critical Component Whitelisting
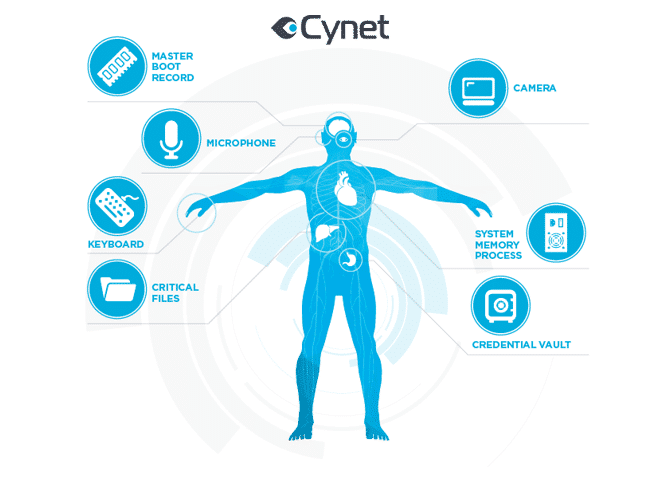
Comprehensive Protection & Detection for Total Cyber Health
There are multiple parallels between the human body and a computer. Vital organs of the human body have been often compared to inner workings of a computer, and vice-versa – the complexity and interweaving of human biological functions can be paralleled to a computer. In the same vein, there has been some comparison between biological viruses and digital viruses. In medicine, we have viruses, bacteria and other pathogens. In software, we have viruses and trojans as equivalents.
Thus, it should not be surprising that new age IT security defenses are mimicking modern medicine in creating biologically-paralleled methodologies and techniques to stop and slow down disease. One such approach is controlled organ isolation.
The Biological Approach
Just as modern medicine has learned to isolate specific organs and treat them independently, strengthening them from external attacks, there is a new approach to security: isolating important components of the computer and individually shielding them from external attacks. This layered approach to protection is unique and gaining momentum.
Cyber threats, like viruses, worms, trojan horses and ransomware, change and constantly evolve. And cyber companies in the EDR, EPP, Anti-Virus and Next-Generation AV niche are continually developing products that search for malicious files and suspicious activity. They scan an organizational system to determine anomalous behavior. But today, these organizations frequently fall prey to cyber criminals who bypass “traditional” security solutions by using obfuscation and other digital manipulation – much in the way that viruses, bacteria and disease learn to bypass the body’s immune system and other biological defenses.
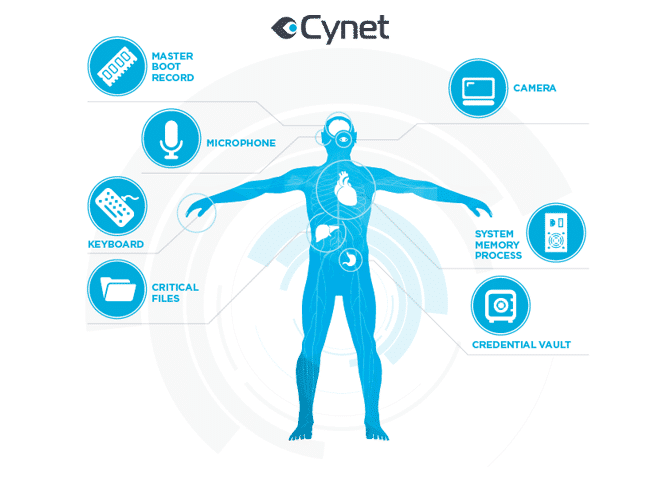
Critical Component Whitelisting (CCW)
The creation of a unique security feature – the Critical Component Whitelisting (CCW) process – secures and isolates vital components in the computer, allowing access only to approved files, processes and communications access. It does this by creating a list of white-listed items, so the computer knows what to allow in, and when to deny entry.
CCW begins with building a list of approved applications and file attributes associated with whitelisted applications. In essence, what CCW does is create a specific whitelisted checklist for each component.
Cynet has adapted this process to create a new and unique approach to securing the inner components of the computer. Today, most cybersecurity organizations are focused on detecting malicious files, anomalous behavior, and other advanced threats using traditional, known methodologies that are easily bypassed by attackers.
With Critical Component Whitelisting, Cynet has taken endpoint protection, threat detection and response to a whole new level. This new and unique approach to security affords organizations greater visibility, speed and control over breach prevention and response.


