How Cynet Stops EARTH GRASS Ransomware
Below we’ll demonstrate how Cynet detects and blocks EARTH GRASS ransomware. For more, you can review our experts’ static analysis and dynamic analysis of this threat.
Note that during the execution simulation, Cynet 360 AutoXDR is configured in detection mode (without prevention) to allow the EARTH GRASS ransomware to execute its full flow. This lets Cynet detect and log each step of the attack.
Fortunately, Cynet can detect and prevent this malware using multiple mechanisms:
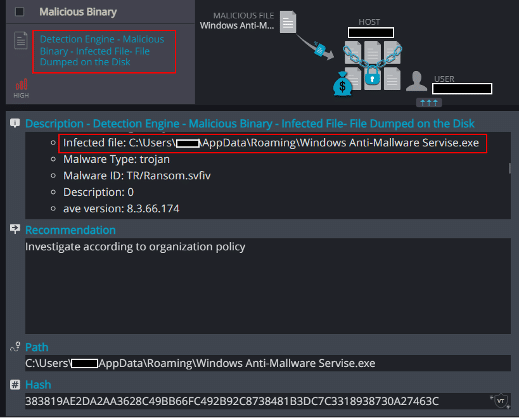
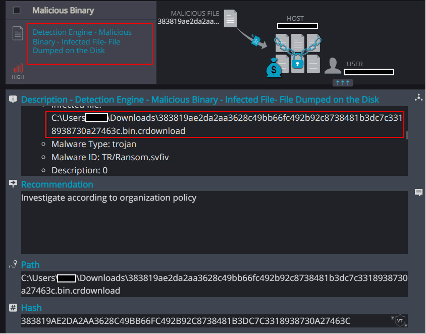
File Dumped on the Disk
Cynet’s AV/AI engine detects that a malicious file was dumped on the disk or is attempting to run:
This mechanism also detects the second stage executable’s creation on the host:
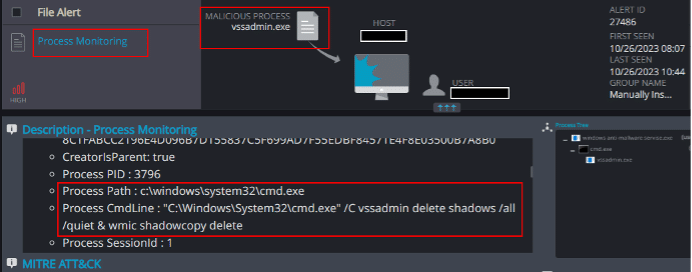
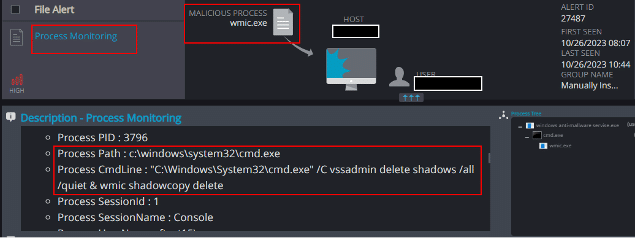
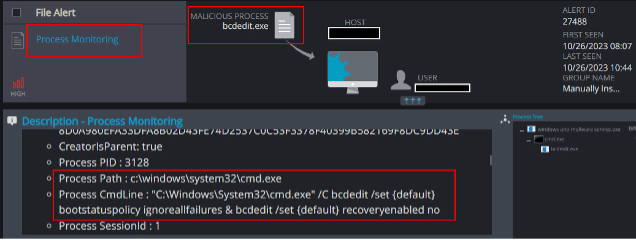
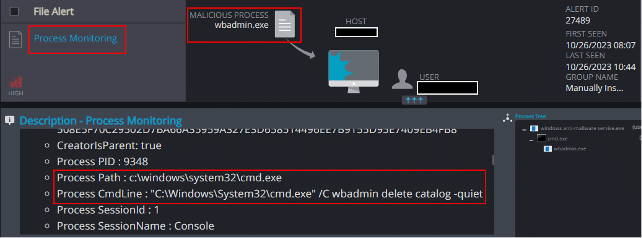
Process Monitoring
The process monitoring detection mechanism is able to detect the process’s attempts to terminate backup services on the host, as well as its attempts to delete the host’s local backup files:
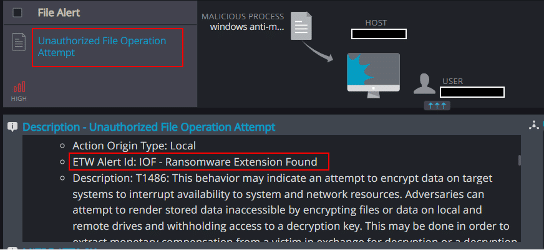
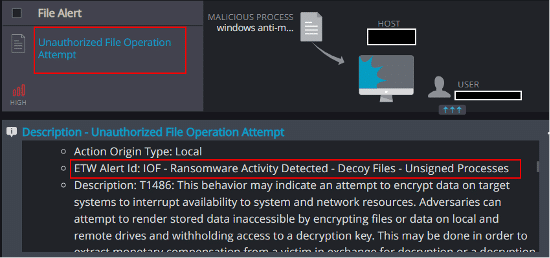
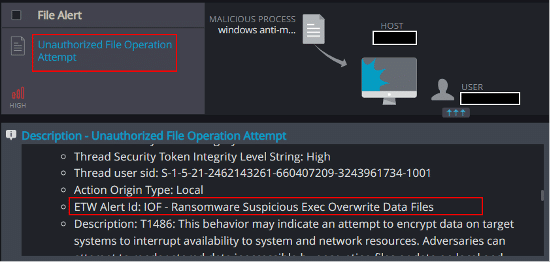
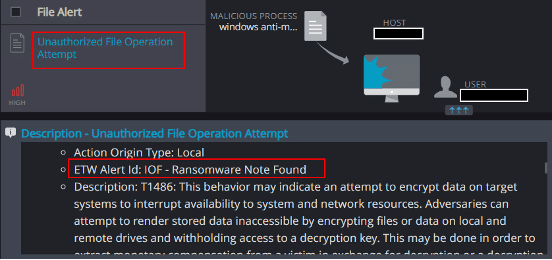
Unauthorized File Operation Attempt
This mechanism is able to detect and report on attempts to modify Cynet’s Ransomware decoy files, the presence of files with suspicious extensions, and the creation of a ransom note on the host:
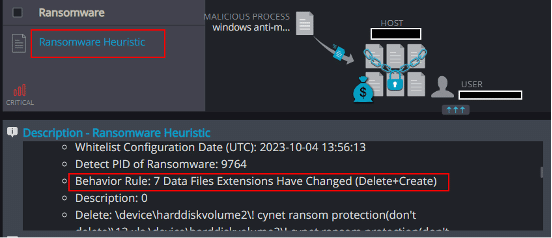
Ransomware Heuristic
An additional detection mechanism is able to detect the modification of file extensions on the host:
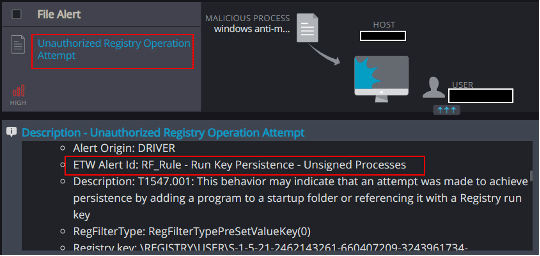
Unauthorized Registry Operation Attempt
This mechanism is able to detect the creation of a persistence registry Run key: