Cynet Deception
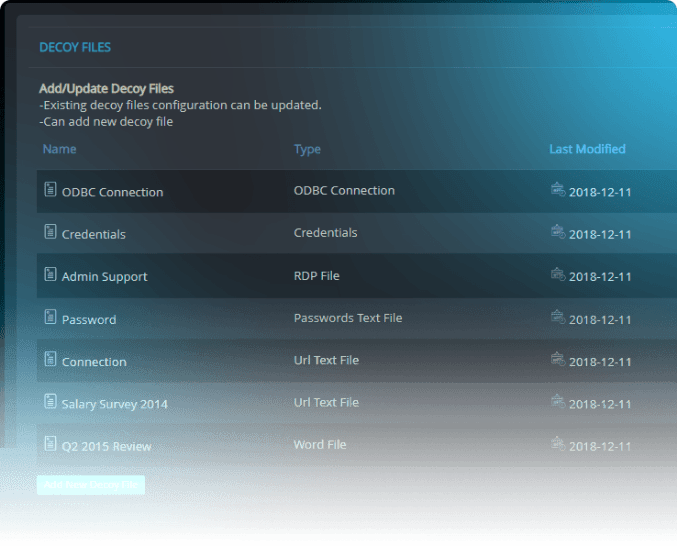
Easily configure decoy files, users, hosts, and networks to expose malicious actors who have gained access to your environment.
Request a DemoDeceive attackers with various honeypots: decoy files, passwords and network connections.
Use off-the-shelf decoys or craft your own
Cynet deception supports various types of decoys, to detect threats in various stages of the attack’s lifecycle: data files, credentials and network connections.
In each type, the consumption action triggers the alert – login attempt with a decoy password, connection attempt with RDP or URL and opening a data file.