Monthly Ransomware Activity
Written by: Maor Huli
In January, we introduce the following types of ransomware:
- Golang
- WaspLocker
- NightSky
- Chaos
- Paradise
- Exploit
EXECUTIVE SUMMARY
Here at Orion, an integral part of Cynet’s research team, we are working around the clock to ensure our customers are protected against the most recent ransomware variants. We track threat intelligence sources, analyze payloads and automate labs. In this article, we bring to you the latest ransomware variants from January, based on Bleeping Computer – the most up-to-date ransomware news website. We explain how these ransomware variants operate and how the Cynet 360 platform detects and prevents them via several mechanisms.
Bleeping computer is the most up-to-date website that summarizes the newest ransomware variants. Orion team is an integral department of Cynet’s research team. We in Orion’s team are working around the clock, tracking threat intelligence resources, analyzing payloads, automated labs to ensure that our customers are most protected against the newest ransomware variants.
In this article, we have summarized ransomware variants from January based on bleepingcomputer.
We will present the recent ransomware and how Cynet 360 platform detects and prevents it via several mechanisms.
CYNET 360 VS RANSOMWARE
- Observed since: mid 2019
- Ransomware encryption method: AES.
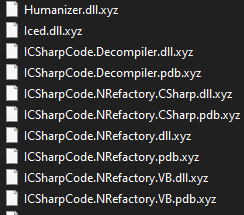
- Ransomware extension: .xyz
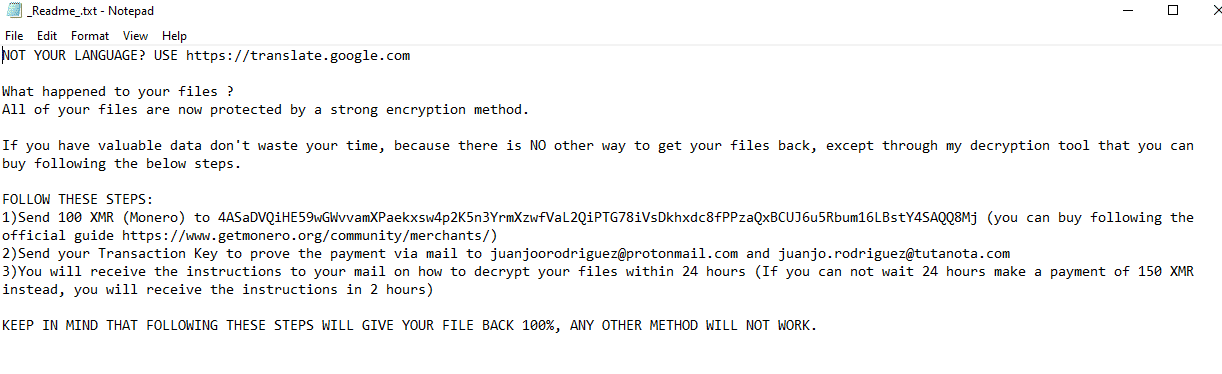
- Ransomware note: _Readme_.txt
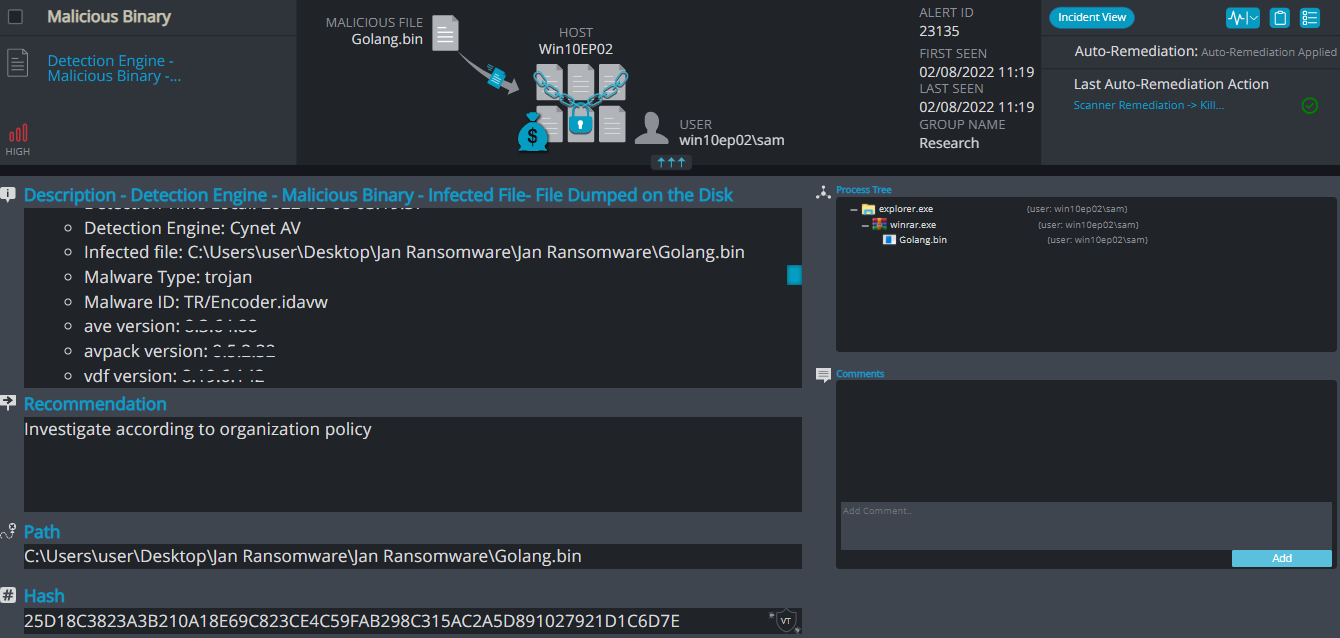
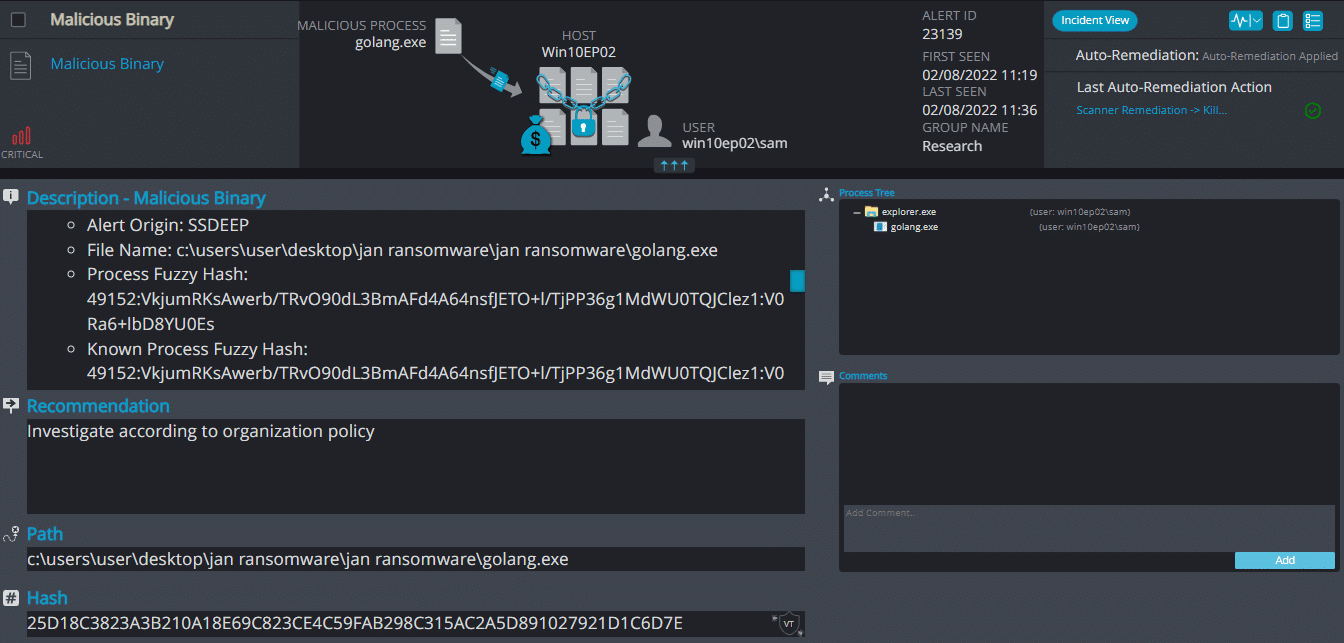
- Sample hash: 25d18c3823a3b210a18e69c823ce4c59fab298c315ac2a5d891027921d1c6d7e
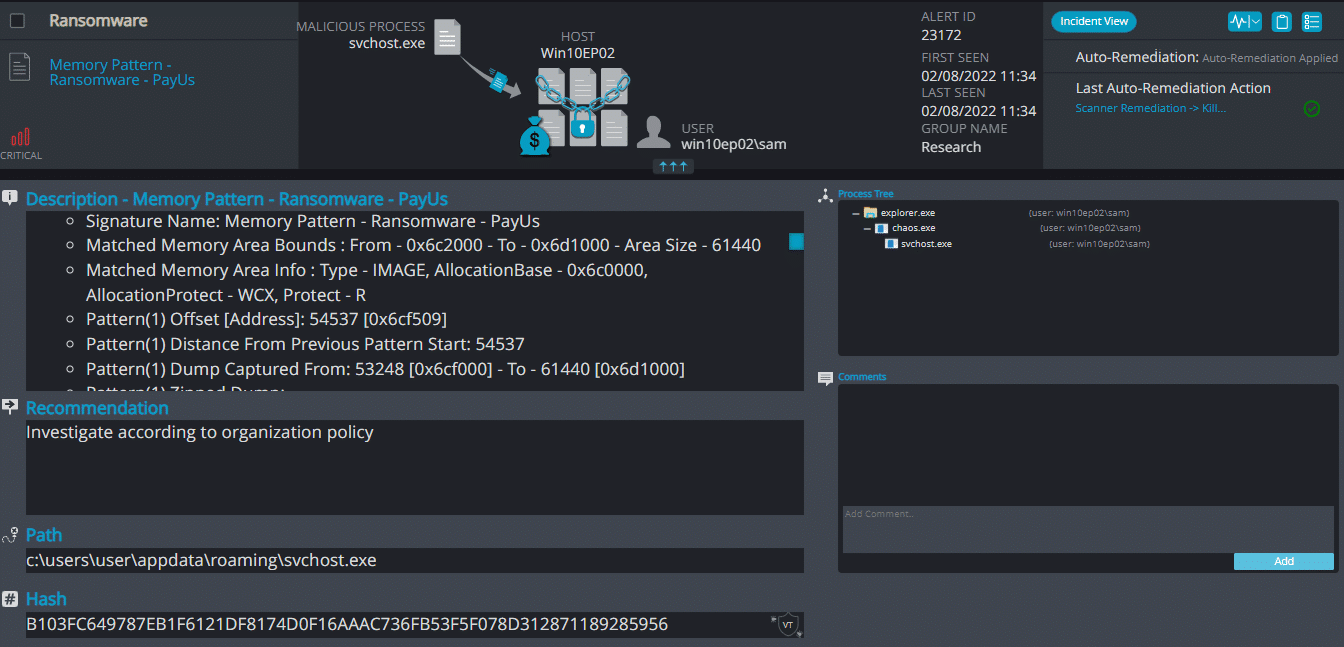
Cynet 360 Detections:
Golang ransomware renames the encrypted files with .xyz in the extension:
Once a computer’s files have been encrypted and renamed, it drops a note as _Readme_.txt.
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains the decryption price (XMR) and the attacker’s wallet address.
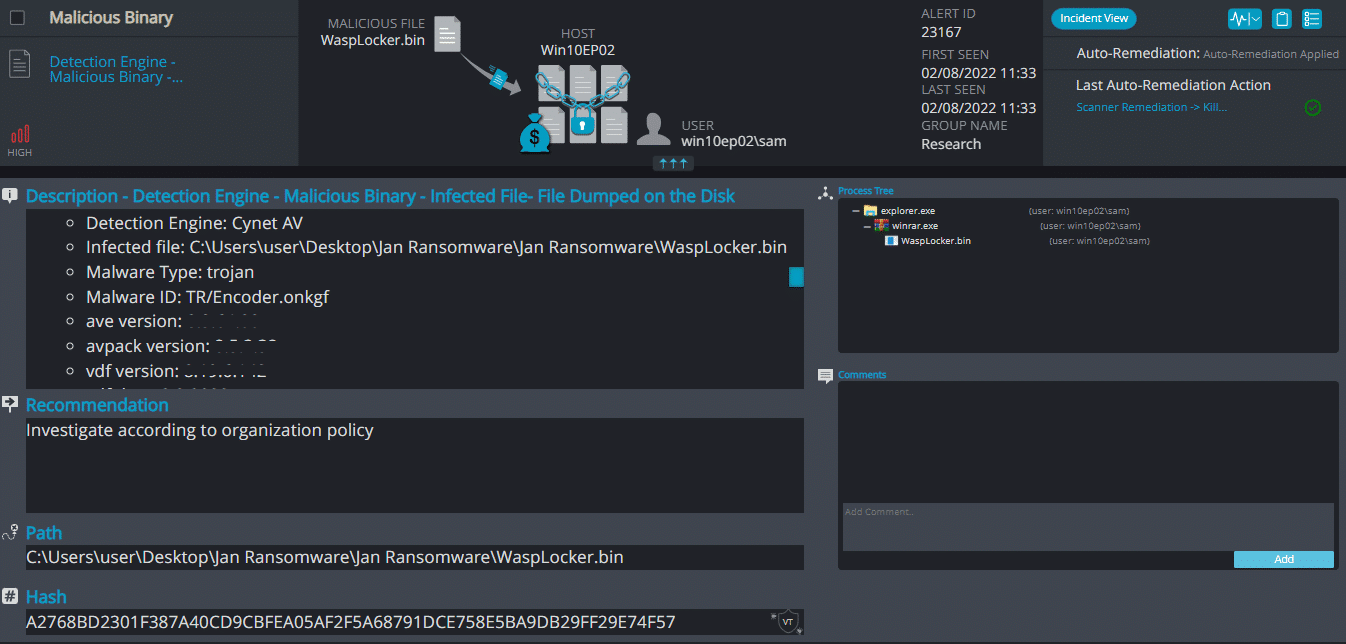
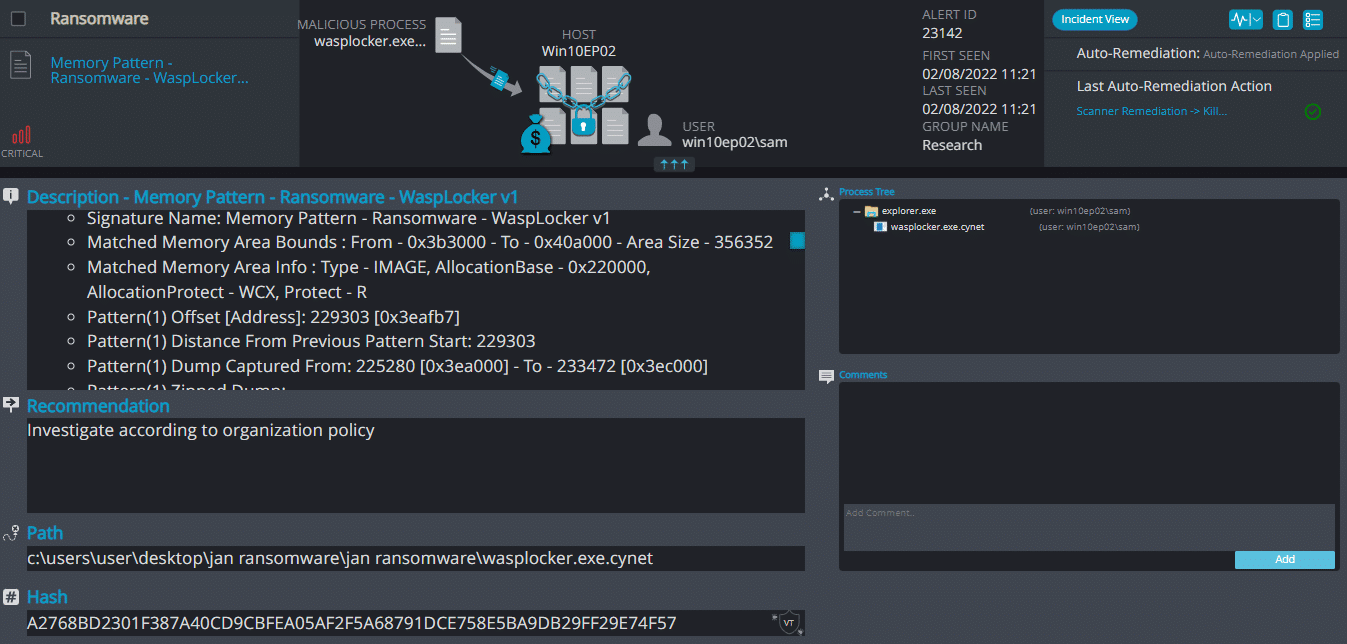
WaspLocker Ransomware
- Observed since: Jan 2021
- Ransomware encryption method: AES + RSA.
- Ransomware extension: .0.locked | .locked (both for folders and files)
- Ransomware note: restore_file.txt
- Sample hash: a2768bd2301f387a40cd9cbfea05af2f5a68791dce758e5ba9db29ff29e74f57
Cynet 360 Detections:
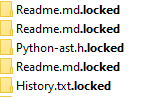
BlueLocker ransomware renames the encrypted files with a .locked extension for each file:
Once a computer’s files have been encrypted and renamed, the ransomware pops up a window with a text within that contains the BTC address and a timer:
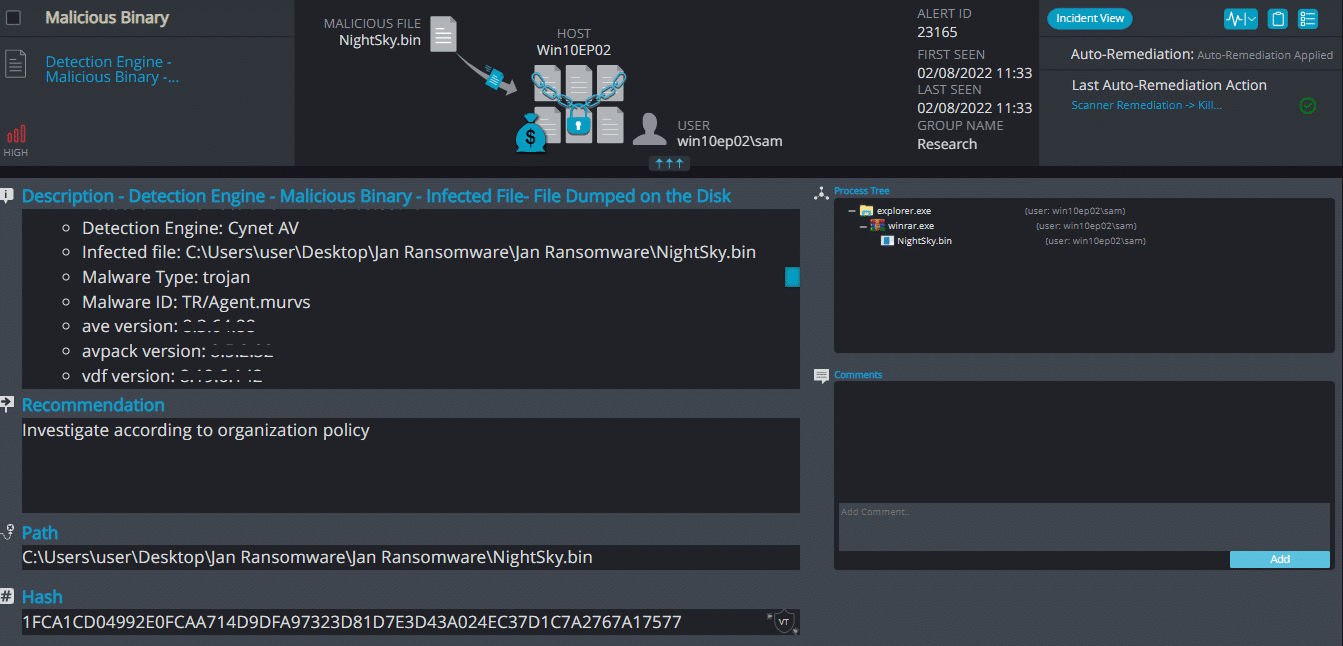
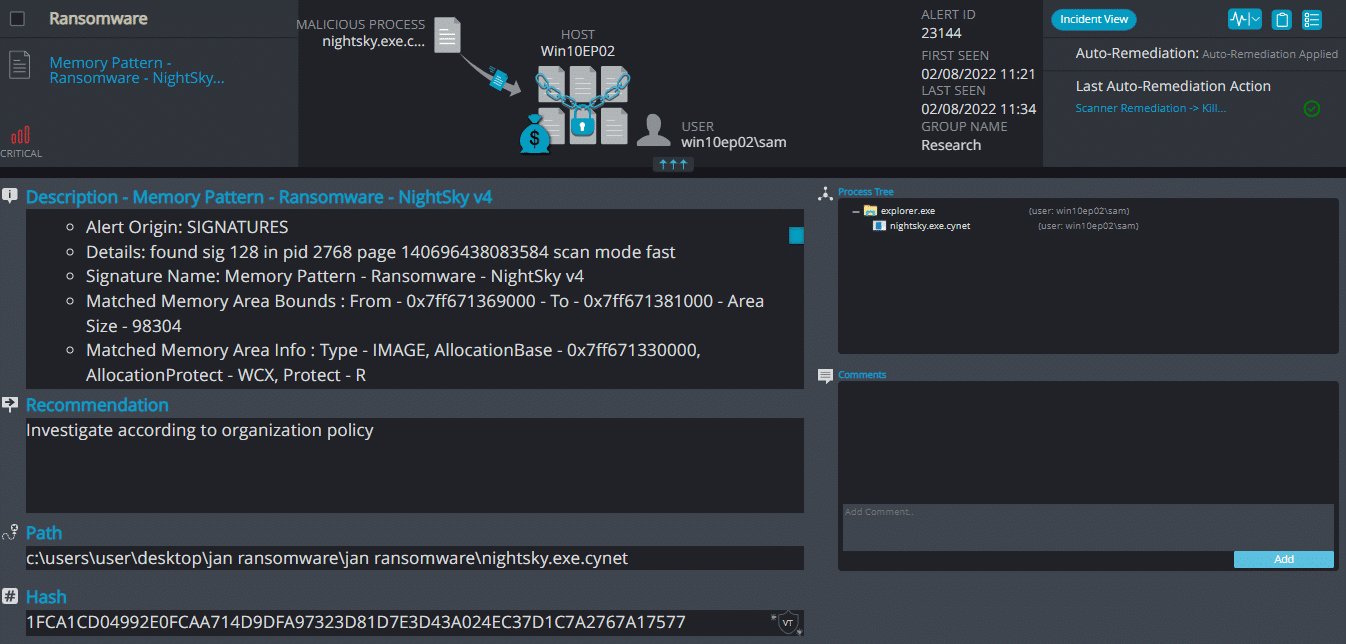
NightSky Ransomware
- Observed since: Dec 2021
- Ransomware encryption method: AES.
- Ransomware extension: .nightsky
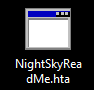
- Ransomware note: NightSkyReadMe.hta
- Sample hash: 1fca1cd04992e0fcaa714d9dfa97323d81d7e3d43a024ec37d1c7a2767a17577
Cynet 360 Detections:
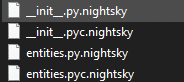
After execution, NightSky ransomware renames the encrypted files with the .nightsky extension.
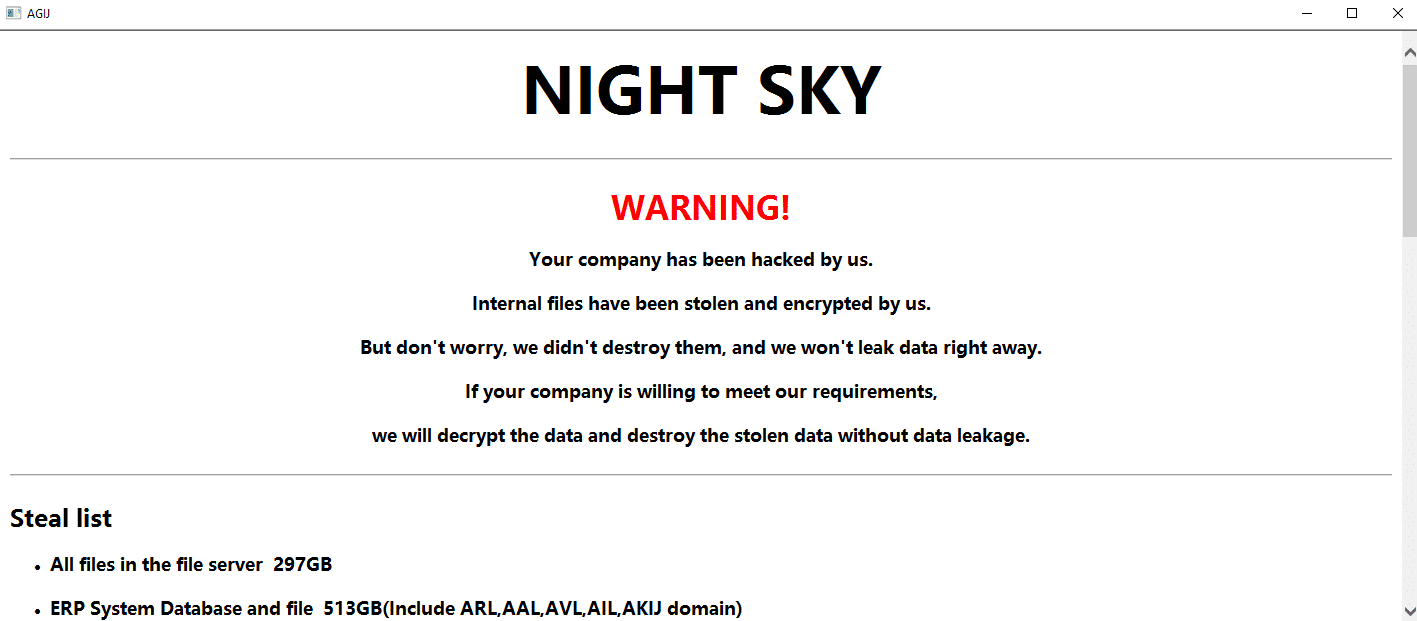
Once a computer’s files have been encrypted and renamed, it drops a note as an hta file named NightSkyReadMe.hta. The file contains instructions on how to pay to get the encrypted files back.
- Observed since: Mid 2021
- Ransomware encryption method: AES.
- Ransomware extension: .GoldenWolf42
- Ransomware note: read_it.txt
- Sample hash: 6a3e60f725d30ab2660c6c9e6928bafe273583e3e501097934e873593a13aee6
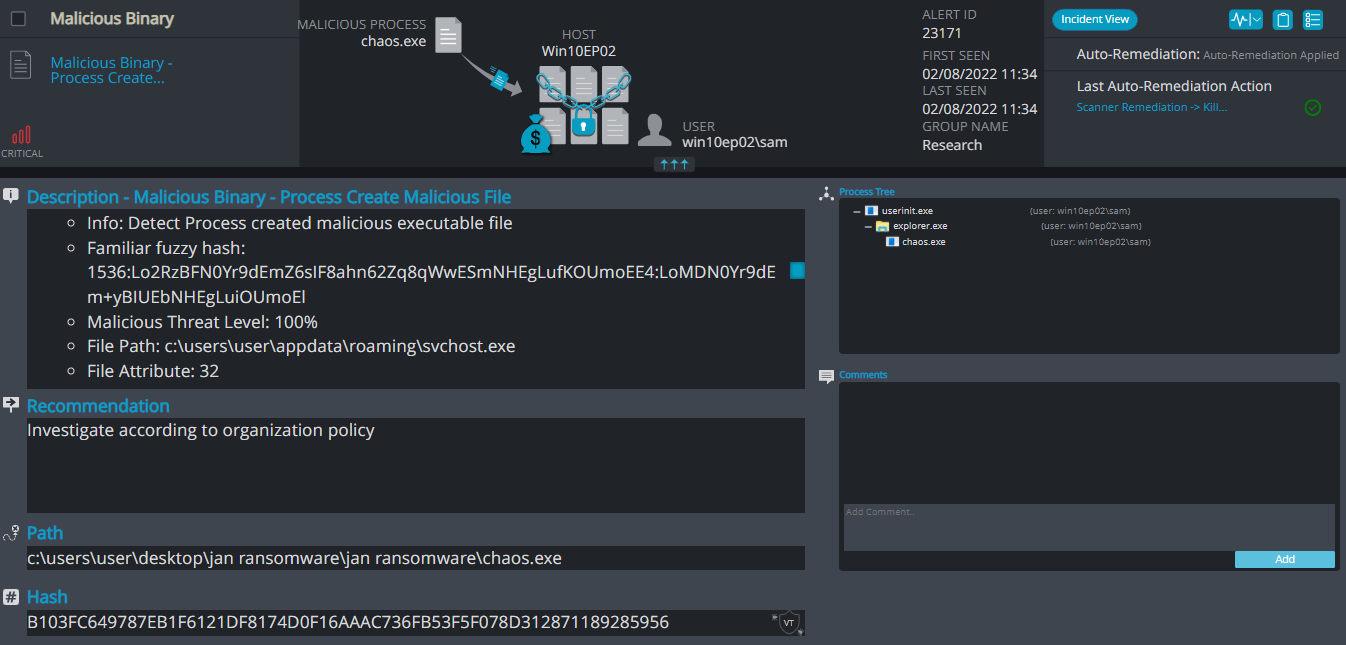
Cynet 360 Detections:
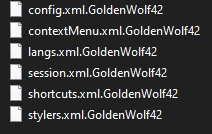
After execution, Chaos ransomware renames the encrypted files with the .GoldenWolf42 extension for each file:
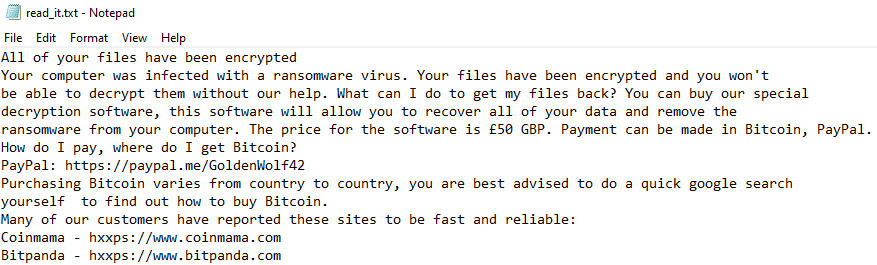
Once a computer’s files have been encrypted and renamed, it drops a note as a text (.txt) file named read_it.txt. In the text file are instructions on how to pay to get the encrypted files back.

- Observed since: Late 2017
- Ransomware encryption method: RSA.
- Ransomware extension: .prt
- Ransomware note: instructions with your files.txt
- Sample hash: a09590420d9f8052f963e7126367ccf9cc56d8f4926096ac88bc85c0a47bb242
Cynet 360 Detections:
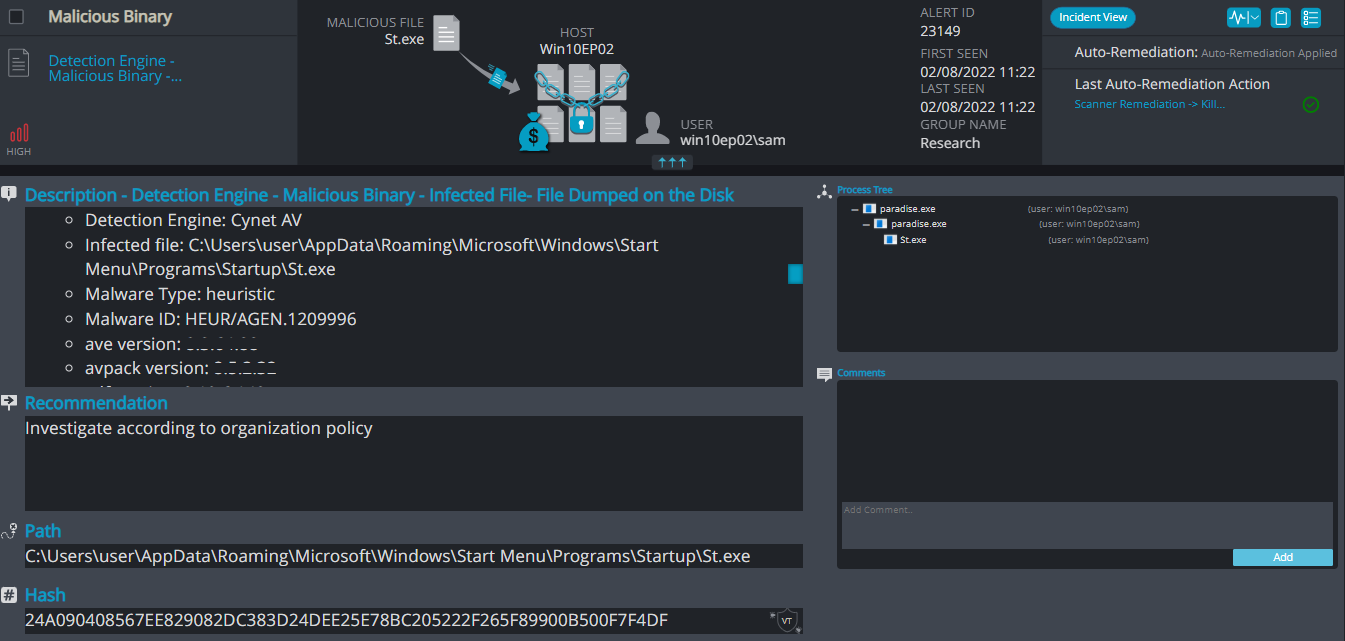
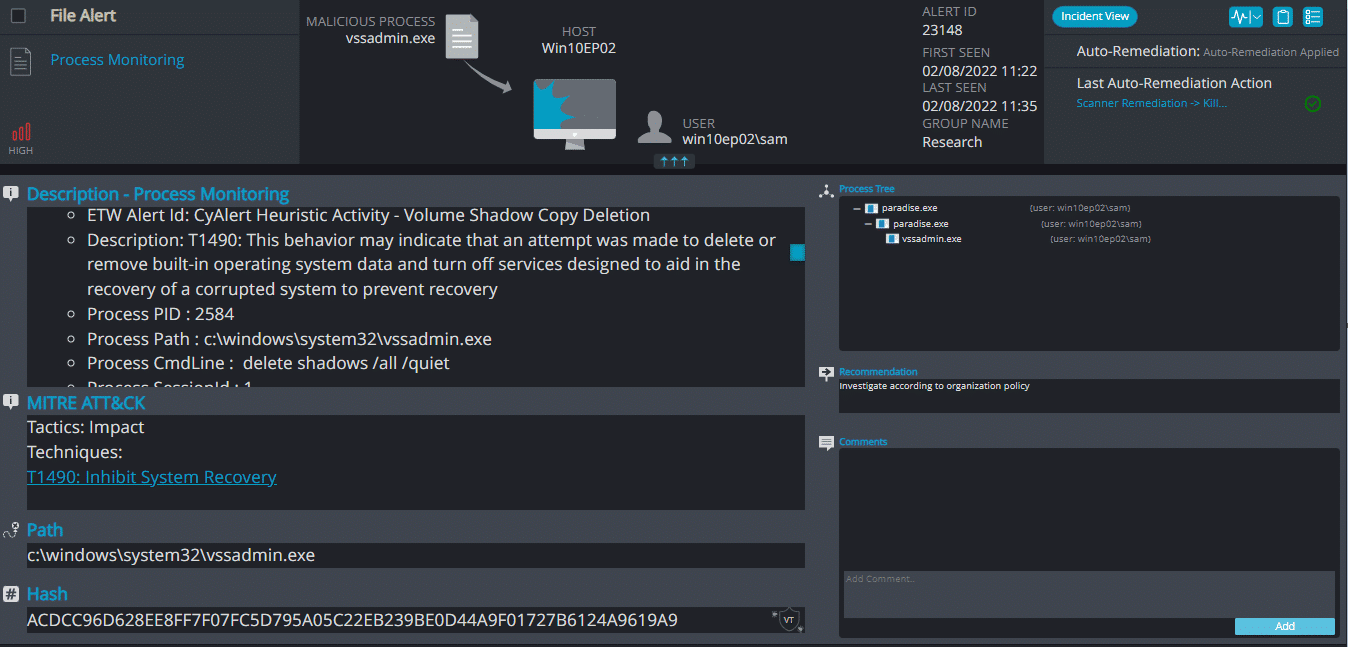
Paradise Overview
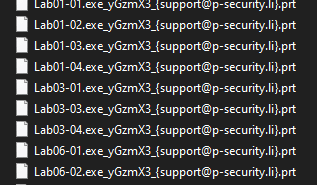
After execution, Paradise ransomware renames the encrypted files with .prt in the extension for each file:
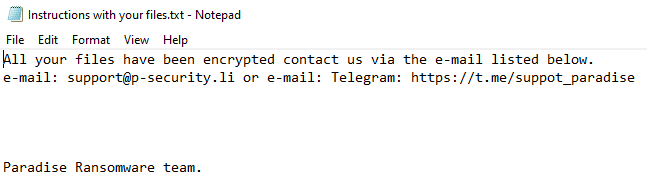
Once a computer’s files have been encrypted and renamed, it drops a note as a text (.txt) file named instructions with your files.txt. In the text file there are instructions on how to pay to get the encrypted files back.

- Observed since: Mid 2020
- Ransomware encryption method: AES
- Ransomware extension: .exploit
- Ransomware note: RECOVERY INFORMATION.txt
- Sample hash: 3f843cbffeba010445dae2b171caaa99c6b56360de5407da71210d007fe26673
Cynet 360 Detections:
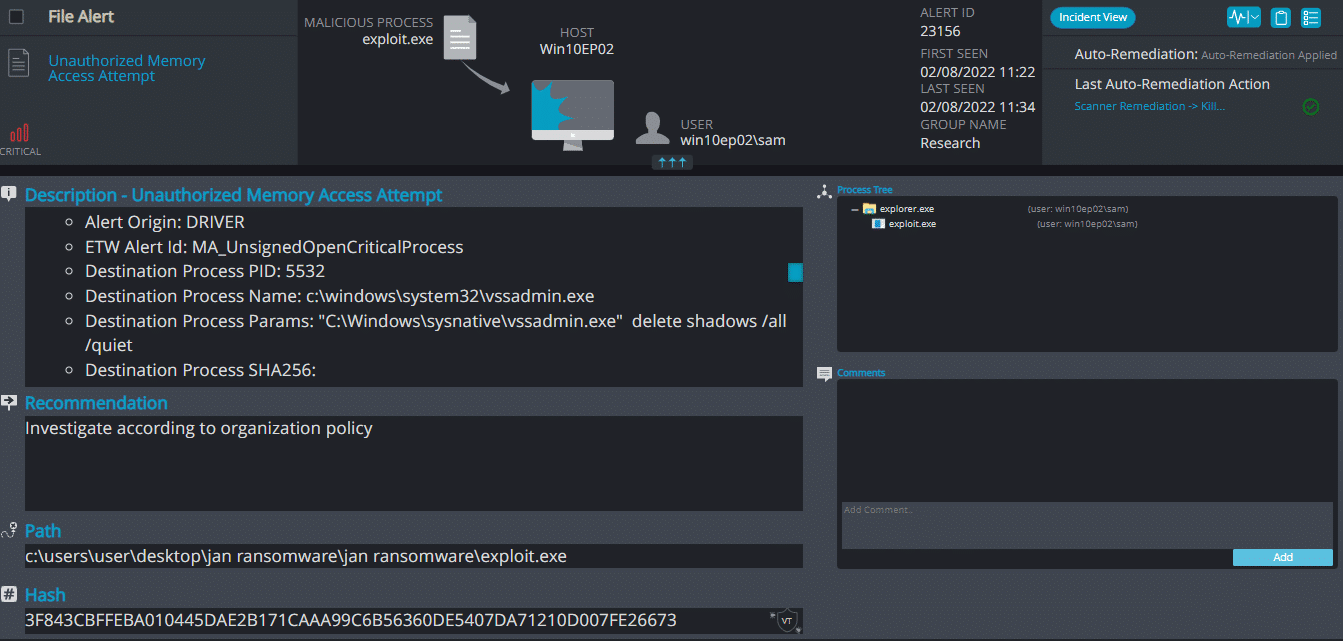
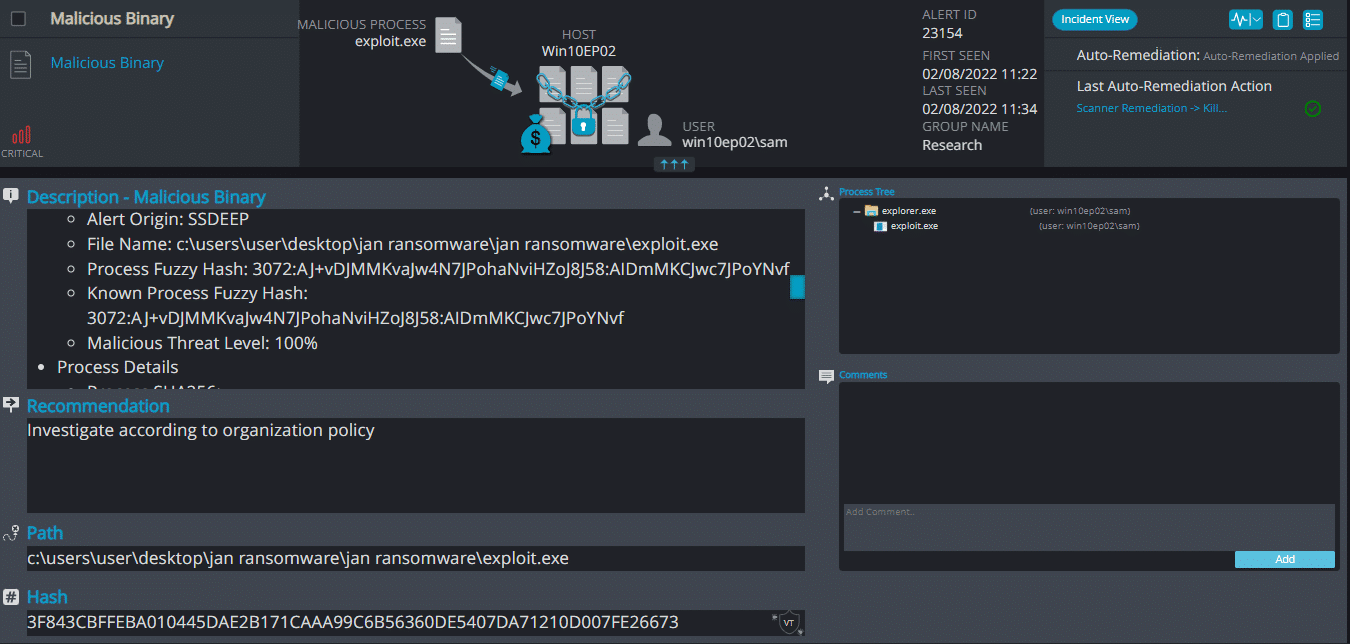
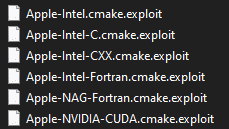
After execution, Exploit ransomware renames the encrypted files with .exploit in the extension for each file:
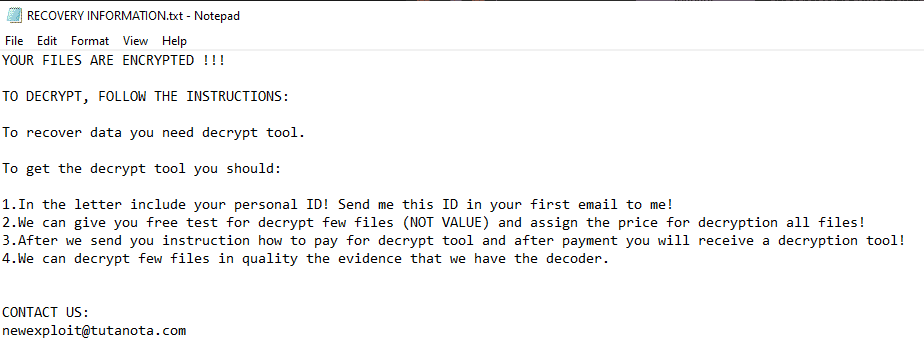
Once a computer’s files have been encrypted and renamed, it drops a note as a text file named RECOVERY INFORMATION.txt. The text file has instructions explaining how to pay to get the encrypted files back.