
MDR Security: Endpoint Protection as a Service
MDR Security: Endpoint Protection as a Service Managed detection and response (MDR) enables organizations... READ MORE
Search results for:
Managed Detection and Response (MDR) is a managed 24/7 service that includes threat monitoring, detection and response. The goal of MDR is to assist enterprises with their incident response (IR) needs. It includes automated technologies which can be deployed at both the network and host layers. MDR employs threat intelligence and advanced analytics in combination with human incident investigation and response experts.
MDR providers offer a wide range of remote response services, including threat containment and support in bringing systems and networks back to normal operations. Its primary advantage is that it allows organizations to rapidly identify and mitigate threats without additional security staff.
This is part of an extensive series of guides about cloud security.
Most organizations face several challenges when trying to implement a comprehensive cybersecurity program. MDR offers services that help meet these challenges:
Learn more in our detailed guide to MDR services
Here are the core capabilities offered by MDR security services:
Managed prioritization, or managed Endpoint Detection and Response (EDR), can help organizations sift through massive volumes of alerts and determine which they should address first. Managed EDR services employ automated rules in combination with human investigation in order to distinguish false positives and benign events from real threats. Managed prioritization uses additional context to distill threats into high-quality alerts.
Human threat hunters have the skills and expertise needed to identify the most evasive threats. Threat hunters provide the insights needed to catch threats that automated defenses miss.
The goal of managed investigation is to help organizations quickly understand the scope and details of threats. This is typically achieved by providing security alerts that contain additional context. Managed investigation services help organizations completely understand what happened and when, as well as who was affected and how far the attack could go. The information can help organizations plan an effective response.
The main purpose of guided response is to deliver actionable advice on how to best contain and remediate a certain threat. Guided response services provide advice on a wide range of security incidents. For example, advising to isolate an affected system from the corporate network, and providing step-by-step instructions on how to eliminate a threat or recover from the attack.
Remediation is the final step performed during incident response. Managed remediation helps restore your system to its pre-attack state. It may involve cleaning a registry, removing malware, removing any persistence mechanisms, and ejecting intruders. Managed remediation helps prevent any additional compromise and return your network to a known good state.
Learn more in our detailed guide to MDR security.
MDR solutions allow companies to drastically reduce their detection and response times – immediately cutting the process from days to just minutes. Faster detection means less impact and less opportunity for the attacker to cause damage.
In addition to reducing the event detection time from months to minutes, MDR allows organizations to:
Managed security service providers (MSSP) offer a basic level of cybersecurity monitoring and management, including antivirus, firewalls, intrusion detection, and management of virtual private networks (VPNs).
However, MSSPs typically do not handle incident response, containment and eradication of threats, or active threat hunting. Here are some of the key capabilities MDR provide beyond the basic MSSP offering:
MDR services incorporate the newest technologies in detection and response, including next-gen antivirus, machine learning, and AI-based automation. In contrast, MSS tends to rely on more traditional technologies and methods. Additionally, MDR cybersecurity services may be more accommodating of cloud services and hybrid systems than MSSPs.
MSSPs are generally not committed to providing a high level of security expertise or guidance. An MSSP typically offers Tier 1 SOC analysts who are focused on supporting automated protection and detection systems.
This is very different from MDR providers, who incorporate whole teams of security professionals of various levels. Rather than simply acting as responsive support staff, MDR professionals proactively monitor systems and take responsibility for threat containment and remediation.
A standard MSSP is only responsible for monitoring systems and forwarding alerts to in-house teams. They do not necessarily filter alerts by priority or spend time confirming whether a threat is legitimate.
In contrast, an MDR security team is responsible for verifying threats and for responding according to agreed-upon guidelines and service level agreements (SLAs). This extra effort and commitment to detection and response makes MDR solutions more expensive but provides an end-to-end solution for cybersecurity threats.
Let’s dive into the differences between MDR and some related security offerings – endpoint detection and response (EDR), eXtended detection and response (XDR), security information and event management (SIEM), and managed security service providers (MSSP).
Learn more in our detailed guide to MDR solutions.
Endpoint detection and response (EDR), formerly known as endpoint threat detection and response (ETDR) platforms are designed especially to protect your endpoints. EDR solutions monitor activity occurring on endpoint devices, such as servers, laptops, and point-of-sale (POS) systems. Note that EDR does not offer complete coverage and must be adopted into the entire security stack.
Learn more in our detailed guide to EDR vs MDR.
Extended detection and response (XDR) solutions offer a layered approach that usually detect and respond to threats on networks as well as endpoints. XDR tools aggregate and correlate telemetry from multiple security controls in order to provide holistic defense across the IT ecosystem.
Security information event management (SIEM) platforms centralize the ingestion of data generated across the entire IT infrastructure. SIEM tools can accept a wide variety of log data types and feeds. For example, logs including records of application and user activity, as well as output from security devices.
SIEM platforms provide a complete view of all data from a single plane. This type of visibility enables organizations to analyze all data and find indicators of compromise (IOCs) across the entire enterprise. SIEM platforms often allow users to configure rules triggered by certain data and may provide several types of analysis, sometimes powered by machine learning (ML).
Cynet offers the leading Cynet 360 AutoXDR cybersecurity platform, including advanced endpoint protection and EDR . Our team of expert threat analysts and security researchers operate a 24/7 Security Operation Center, providing best-of-breed detection and response. Here’s what you can expect from the CyOps team:
Learn more about Cynet MDR services.
EDR vs MDR: How They Compare and the XDR Connection
An endpoint is a point on the network granting access to authorized users. The device connected to the network is called an endpoint device. Managed detection and response (MDR) is a service that provides advanced threat detection and mitigation.
Learn about the differences between Endpoint Detection and Response (EDR) and Managed Detection and Response (MDR), and how they relate to XDR, a new security paradigm.
Read more: EDR vs MDR: How They Compare and the XDR Connection
MDR Solutions: Why They are Critical and How to Choose
Managed Detection and Response (MDR) solutions offer security mitigation and monitoring solutions for organizations. MDR providers monitor their customers’ endpoints, networks and various IT resources for security events. Once a threat is detected, the MDR provider will look into and take care of issues without the direct response for their client. Organizations use MDR services to safeguard themselves from web-based threats without the need for dedicated security staff onsite.
Learn about Managed Detection and Response (MDR) solutions, why they are critical in light of the cybersecurity skills shortage, and what capabilities you can expect from a robust solution.
Read more: MDR Solutions: Why They are Critical and How to Choose
MDR Services: Choosing the Best Option for You
Managed Detection and Response (MDR) refers to a collection of security technologies installed on an organization’s host, network and endpoints, which are managed by a third-party provider. The provider offers technology that clients can install on their on-prem infrastructure, as well as software offering additional automated services.
Learn about 4 types of Managed Detection and Response (MDR) services, and discover how to evaluate an MDR service to find the best match for your organization.
Together with our content partners, we have authored in-depth guides on several other topics that can also be useful as you explore the world of cloud security.
Authored by Cynet
Authored by Faddom
Authored by NetApp Cloud Backup

MDR Security: Endpoint Protection as a Service Managed detection and response (MDR) enables organizations... READ MORE
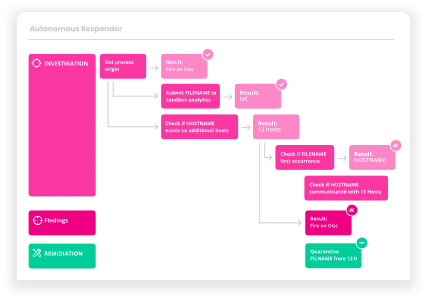
Let’s get started
Ready to extend visibility, threat detection and response?
Prefer a one-on-one demo? Click here
By clicking next I consent to the use of my personal data by Cynet in accordance with Cynet's Privacy Policy and by its partners