Search results for:
Incident response is a structured process organizations use to identify and deal with cybersecurity incidents. The NIST framework for incident response includes four stages: preparation and prevention; detection and analysis; containment, eradication, and recovery; and post-incident activity.
We’ll describe the National Institute of Standards and Technology (NIST) framework for incident response, and show how to build your incident response plan according to NIST principles, with templates and real life examples you can follow to get started.
The National Institute of Standards and Technology (NIST) is an agency operated by the United States’ Department of Commerce which provides standards and recommendations for many technology sectors.
Within NIST, the Information Technology Laboratory (ITL) is responsible for developing standards and measurement methods for IT, including information security. ITL developed an influential model for incident response (IR), the Computer Security Incident Handling Guide (Special Publication 800-61).
The NIST incident response process is a cyclical activity featuring ongoing learning and advancements to discover how to best protect the organization. It includes four main stages: preparation, detection/analysis, containment/eradication, and recovery.
NIST is providing recommendations on incident response to help organizations improve their resilience against cyber threats. NIST’s recommendations are based on industry best practices, lessons learned from past incidents, and input from cybersecurity experts. They are designed to be practical and actionable, providing organizations with a clear roadmap for developing and implementing their own incident response plans.
Moreover, NIST’s recommendations are continually updated to reflect the evolving cyber threat landscape. This ensures that the guidelines remain relevant and effective in helping organizations deal with contemporary threats. By providing these recommendations, NIST aims to raise the overall level of cybersecurity preparedness across industries and sectors.
NIST recommendations are also important to align your organization with U.S. government guidelines on cybersecurity. The recent Executive Order 14028 (Improving the Nation’s Cybersecurity) puts in place cybersecurity best practices that are encouraged in both the government and private sectors. This is especially important for organizations planning to do business with U.S. government agencies.
The NIST Computer Security Incident Handling Guide provides in-depth guidelines on how to build an incident response capability within an organization. It covers several models for incident response teams, how to select the best model, and best practices for operating the team.
NIST offers three models for incident response teams:
Within each of these models, staff can be employees, partially outsourced, or fully outsourced. Employees can also be full- or part-time.
NIST provides several considerations for selecting an incident response model:
The NIST Incident Response Guide provides several guidelines for organizing and operating an incident response unit.
Establish a formal incident response capability
Even if your organization is small, take incident response seriously and establish a formal incident response body. If it is not possible to establish a full-time incident response team, create a virtual team with part-time staff, and give this team full authority and responsibility. This will dramatically improve your capability to respond when a cyberattack strikes.
Create an incident response policy
This is a precursor to the incident response plan which lays out the organizational framework for incident response. It specifies what is considered a security incident, who is responsible for incident response, roles and responsibilities, documentation and reporting requirements.
Define an incident response plan
According to NIST methodology, an incident response plan is not merely a list of steps to perform when an incident happens. It is a roadmap for the organization’s incident response program, including short- and long-term goals, metrics for measuring success, training and job requirements for incident response roles.
Develop incident response procedures
These are the detailed steps incident response teams will use to respond to an incident. They should be based on the incident response policy and plan and should address all four phases of the incident response lifecycle: preparation, detection and analysis, containment, eradication and recovery, and post-incident activity.
One more thing that can save you time as you prepare an incident response plan is to use ready-made templates shared by other organizations. You can adapt these templates to your specific needs.
The following templates are not provided by NIST, but are aligned with NIST incident response principles. They can help you get a head start on your incident response plan:
Learn more in our detailed guide to incident response plan templates
NIST defines a four-step process for incident response, illustrated in the diagram below. The NIST process emphasizes that incident response is not a linear activity that starts when an incident is detected and ends with eradication and recovery. Rather, incident response is a cyclical activity, where there is continuing learning and improvement to discover how to better defend the organization.
Source: NIST
After every incident there is a substantial effort to document and investigate what happened during the incident, to feed back to earlier stages and to enable better preparation, detection and analysis for future incidents.
There is also a feedback loop from the containment and eradication step to detection and analysis—many parts of an attack are not fully understood at the detection stage and are only revealed when incident responders “enter the scene”. These lessons can help the team detect and analyze attacks more fully the next time around.
To prepare for incidents, compile a list of IT assets such as networks, servers and endpoints, identifying their importance and which ones are critical or hold sensitive data. Set up monitoring so you have a baseline of normal activity. Determine which types of security events should be investigated, and create detailed response steps for common types of incidents.
Cynet 360 provides all the core capabilities required for sound incident preparation, including a centralized visibility interface showing all endpoint configurations, process execution, installed software, network traffic and user activity.
Detection involves collecting data from IT systems, security tools, publicly available information and people inside and outside the organization, and identifying precursors (signs that an incident may happen in the future) and indicators (data showing that an attack has happened or is happening now).
Analysis involves identifying a baseline or normal activity for the affected systems, correlating related events and seeing if and how they deviate from normal behavior.
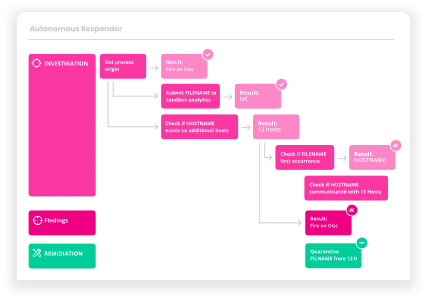
An integrated security platform like Cynet 360 can do this for you, automatically identifying behavioral baselines, detecting anomalies that represent suspicious behavior, and collecting all relevant data across networks, endpoints and users to help you investigate it.
Learn more about how Cynet 360 provides detection capabilities against a wide range of attack vectors with its natively integrated EDR, user behavior rules, network detection rules and deception modules.
The goal of containment is to stop the attack before it overwhelms resources or causes damage. Your containment strategy will depend on the level of damage the incident can cause, the need to keep critical services available to employees and customers, and the duration of the solution—a temporary solution for a few hours, days or weeks, or a permanent solution.
As part of containment, it is important to identify the attacking host and validate its IP address. This allows you to block communication from the attacker and also identify the threat actor to understand their mode of operation, search for and block other communication channels they may be using.
Cynet 360 can help you take remote manual action to contain security incidents, including stopping malicious processes, deleting files, resetting passwords and restarting affected devices. It can also perform automatic containment actions such as stopping rapid encryption of files or automatically isolating endpoints infected by malware from the network.
Cynet response orchestration capabilities provide the means to terminate attackers’ presence and activity from all parts of the environment: infected hosts, malicious files, compromised user accounts and attacker-controlled traffic. Learn more about Cynet 360’s incident containment capabilities.
In the eradication and recovery stage, after the incident has been successfully contained, you should act to remove all elements of the incident from the environment. This might include identifying all affected hosts, removing malware, and closing or resetting passwords for breached user accounts.
Finally, once the threat is eradicated, restore systems and recover normal operations as quickly as possible, taking steps to ensure the same assets are not attacked again.
A central part of the NIST incident response methodology is learning from previous incidents to improve the process.
You should ask, investigate and document the answers to the following questions:
Use your findings to improve the process, adjust your incident response policy, plan, and procedures, and feed the new data into the preparation stage of your incident response process.
When building an incident response plan, it is useful to see examples of real plans created by other organizations which have been fine-tuned over time based on their experience. See the following examples of incident response plans by leading organizations:
| Organization | Example Plan Includes | Link to Example |
| U.S. Department of Homeland Security | Roles and responsibilities, core incident response capabilities, coordinating structures | Open link |
| Carnegie Mellon University | Definitions of incidents, roles and responsibilities, incident response phases, insider threat guidelines | Open link |
| University at Buffalo | Incident response contact information, incident classification and impact, reporting and notifications | Open link |
| Write State University | Incident response steps, security tools, checklist upon detection of intrusion | Open link |
| University of Oklahoma Health Sciences Center | PCI DSS incident response plan including roles and responsibilities, incident response phases, detailed workflow diagram | Open link |
Create a simple, well-defined process
An incident response plan, even if it is very well thought out, must be simple and crystal clear to be effective. Keep details, procedures and explanations to a minimum to ensure that staff can very easily follow the plan in the urgency and confusion of a real security incident.
Create a communication strategy
Clarify who needs to be informed of a security breach, which communication channels should be used and what level of detail should be provided. There should be clear guidelines on how to inform operations, senior management, affected parties inside and outside the organization, law enforcement, and the press. This is a commonly overlooked part of the incident response process.
Use an incident response plan template
Don’t reinvent the wheel. Always start your incident response plan from a template created by others in the industry and adapt it to your specific needs. For example, you can start from this template provided by TechTarget which includes incident scope, planning scenarios, logical sequence of events for incident response, team roles, notification and escalation procedures.
Put your incident response plan to the test
Conduct realistic drills and exercises to see how the incident response plan is carried out in practice, and be ready to adapt the plan according to lessons learned. Test your tools to ensure they are able to detect an attack as early as possible in the kill chain, and ensure the team can identify a threat and contain it before sensitive data leaves your network.
Use a centralized approach
Organizations should not be logging into multiple tools and correlating information between them during the urgency of an attack. Processes and tooling should support a centralized incident response process where an analyst can view all the information about an incident in one place.
Put incident response technology in place
Incident response tools/technology provides you with the means to eradicate discovered malicious presence and activity from your environment as well as optimize response workflows by automating repetitive tasks. They can:
Cynet has an outsourced incident response team available to anyone including small, medium and large organizations. The incident response team provides professional security staff who are equipped to carry out fast, effective incident response activities.
Cynet can deploy the Cynet security platform in just minutes across hundreds to thousands of endpoints. They can scan, identify, analyze and attend to threats before any harm is done. The Cynet incident response team can assist with:
Contact Cynet for immediate help
For emergency assistance from Cynet’s security experts, call them now at US 1-(347)-474-0048, International +44-203-290-9051, or complete this form.
Let’s get started
Ready to extend visibility, threat detection and response?
Prefer a one-on-one demo? Click here
By clicking next I consent to the use of my personal data by Cynet in accordance with Cynet's Privacy Policy and by its partners