Outstanding results
in MITRE 2023
- 100% visibility
- 100% analytic coverage
- 100% real-time detection
Search results for:
Put your cybersecurity on autopilot with automated investigation and response to address threats across your environment.
Request a Demo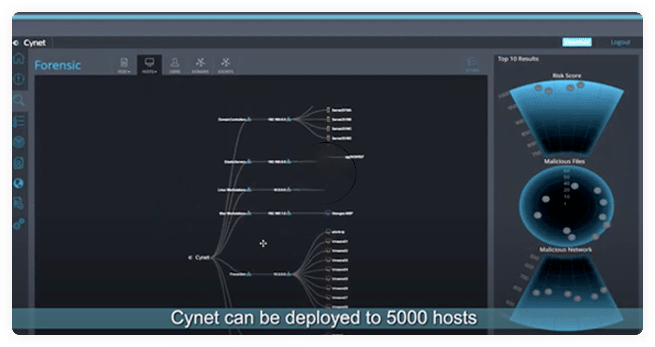
Cynet provides the most extensive array of automated capabilities that allow you to orchestrate incident response across your environment and get all the benefits of SOAR.
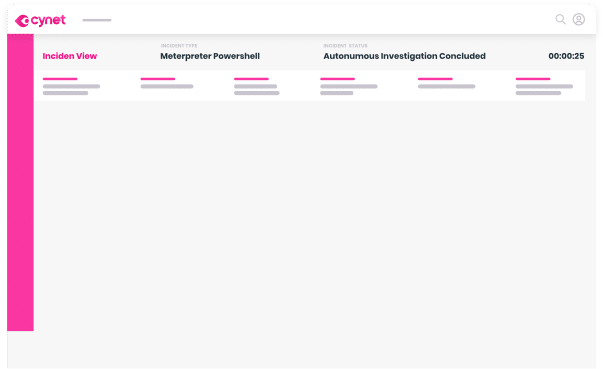
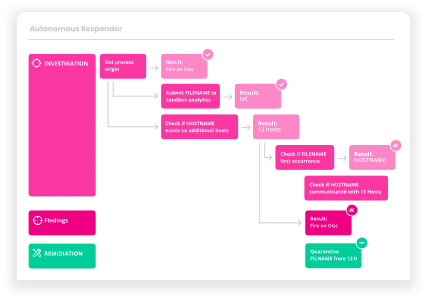
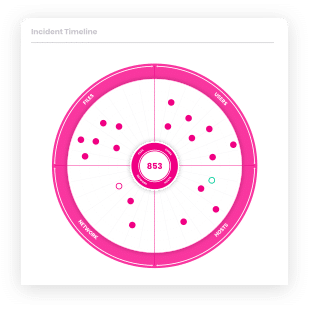
Automatically determine the root cause and full scope of an attack across your environment. Includes a graphical timeline and layout of attacks, along with the automated investigation and response actions
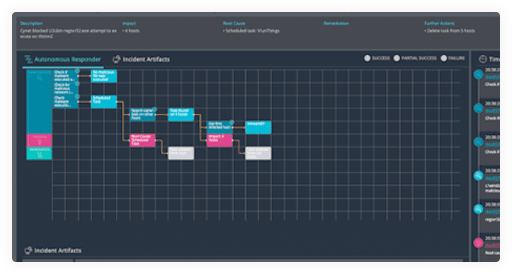
Eliminate malicious presence and activity across endpoints, networks, users, SaaS applications, and other IT components with the broadest set of remediation actions available from an XDR provider
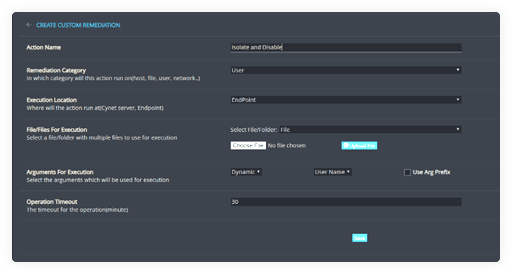
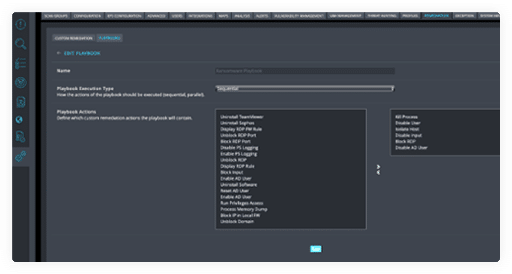
Cynet Remediation Playbooks automate comprehensive multi-action responses across your environment for any attack scenario. Leverage prebuilt playbooks or easily create your own customized playbooks
Investigate alerts, remediate threats, orchestrate, and automate incident response workflows across your environment, all from a single pane of glass

Uncover and resolve all attack components across your environment in seconds – not minutes or hours
Become more productive and eliminate time-consuming manual tasks by automating workflows and accelerating threat detection, investigation, and response
Boost your lean security team’s expertise by leveraging automated best practice investigation and response workflows
Avoid the costly and resource-intensive implementation and support of a complicated SOAR solution – Responder™ is included in Cynet AutoXDR™ platform


Let’s get started
Ready to extend visibility, threat detection and response?
Prefer a one-on-one demo? Click here
By clicking next I consent to the use of my personal data by Cynet in accordance with Cynet's Privacy Policy and by its partners