August 2022 Ransomware Activity Report

Written by: Maor Huli
The ransomware introduced in August is:
- Payt
- Hydrox
- World2022decoding
- Medusa
- VoidCrypt
EXECUTIVE SUMMARY
As an integral department of Cynet’s research team, Orion works around the clock to track threat intelligence resources, analyze payloads and automate labs to protect customers against the newest ransomware variants. In these monthly reports, Orion reviews the latest trends identified in Bleeping Computer — the most up-to-date website that summarizes the newest ransomware variants — and shares how Cynet detects these threats.
CYNET 360 AutoXDR™ VS RANSOMWARE
Payt Ransomware
- Observed since: Aug 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .Payt
- Ransomware note: ReadthisforDecode.txt
- Sample hash: 3a3c882946ba931c47515463c64389df9d61a90c87d2a0d91ea9288175c7ff8e
Cynet 360 AutoXDR™ Detections:
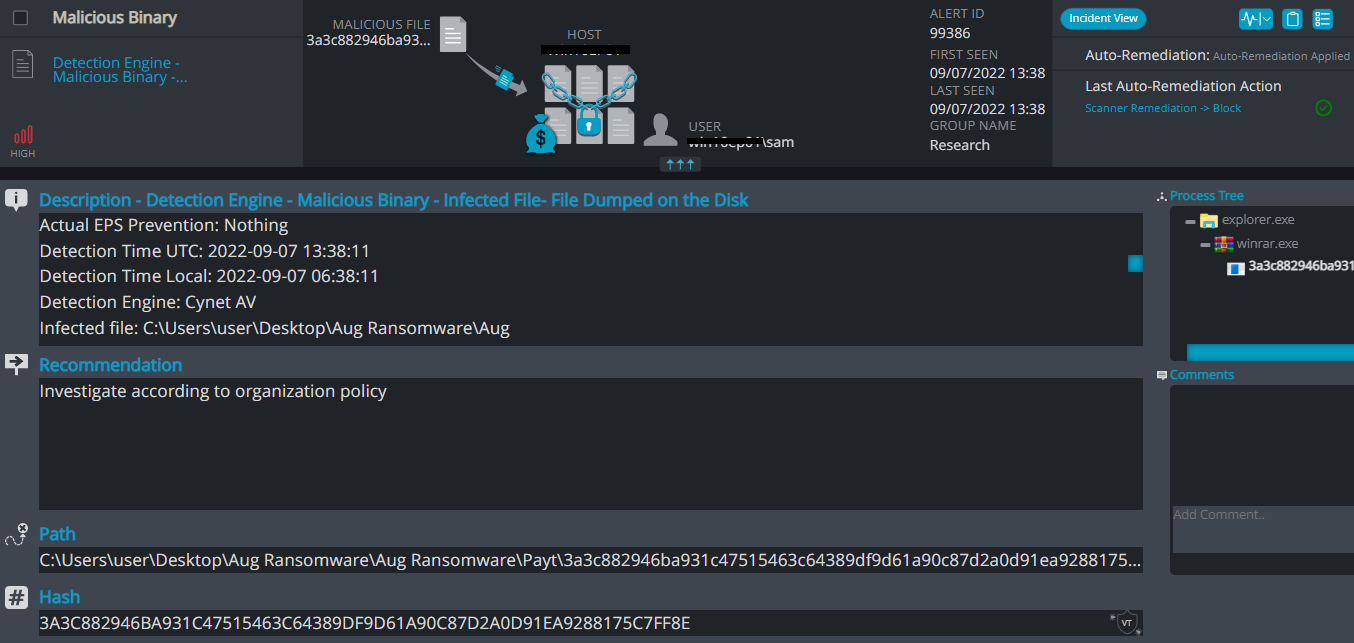
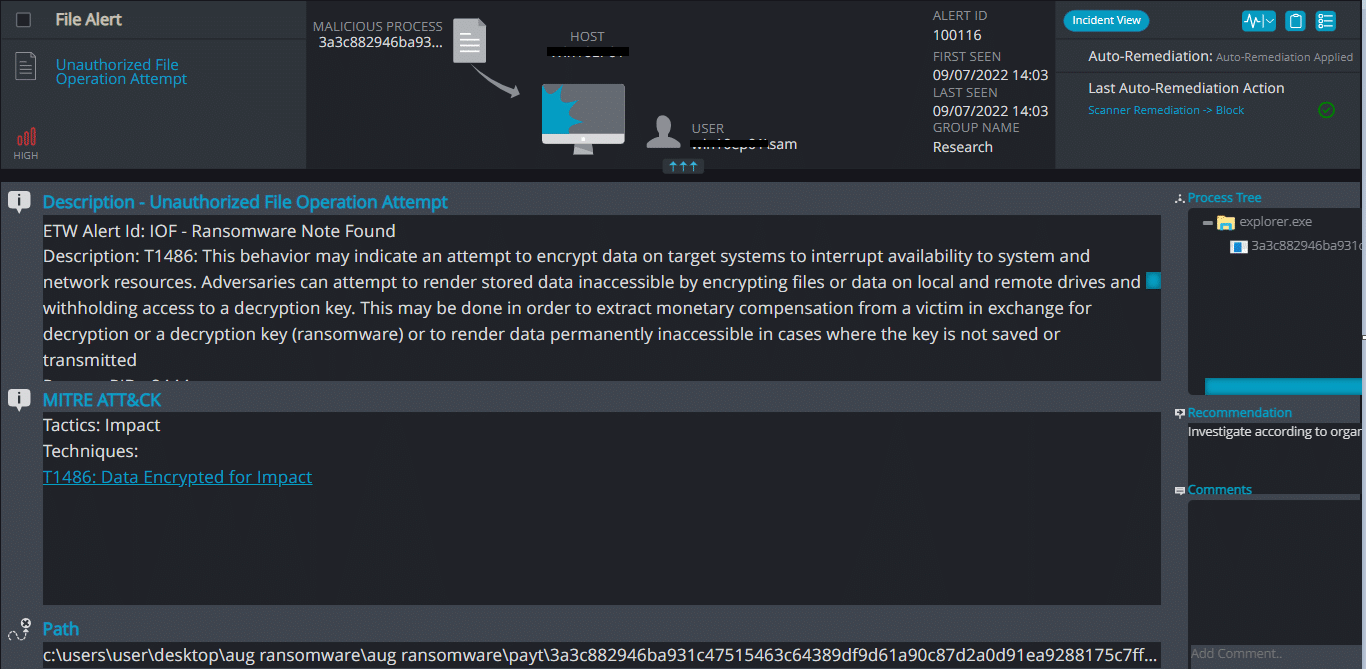
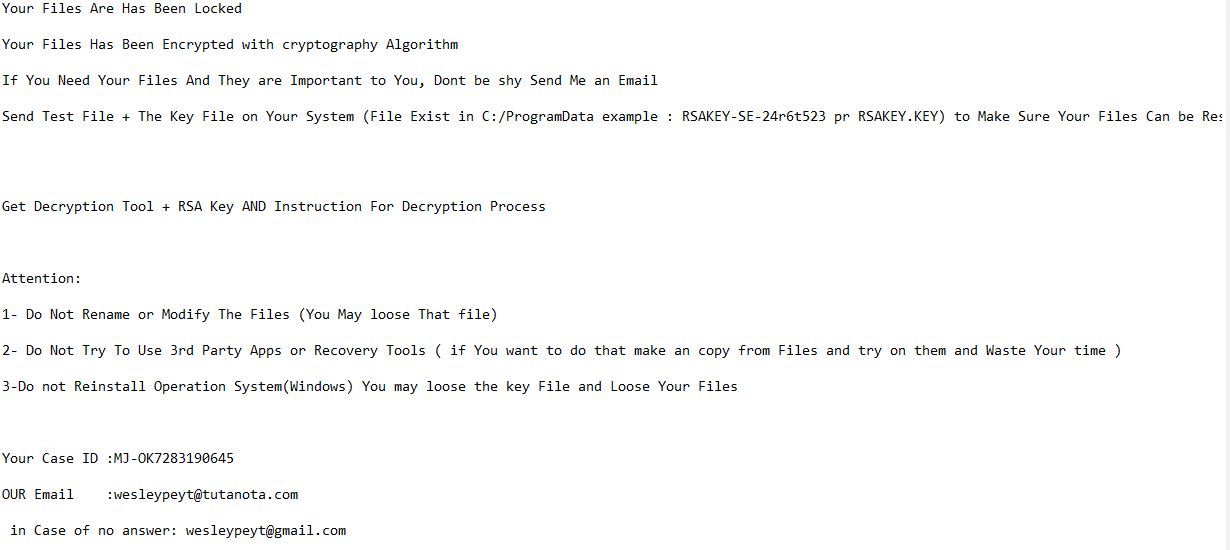
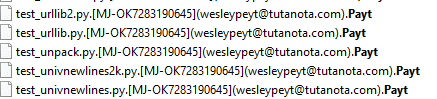
Payt ransomware renames the encrypted files with .Payt along with the attacker’s email and the host ID in the extension.
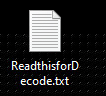
Once a computer’s files have been encrypted and renamed (in approximately 15 minutes), it drops a note as ReadthisforDecode.txt:
The ransomware note contains general information, warnings and the attacker’s email address:
Hydrox Ransomware
- Observed since: Aug 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .hydrox
- Ransomware note: Hydrox Ransomware.txt
- Sample hash: 24d49f947f968c4f654ebfa2d4c0bdd3a8ddf45cfa909dc8b36b557724b14361
Cynet 360 AutoXDR™ Detections:
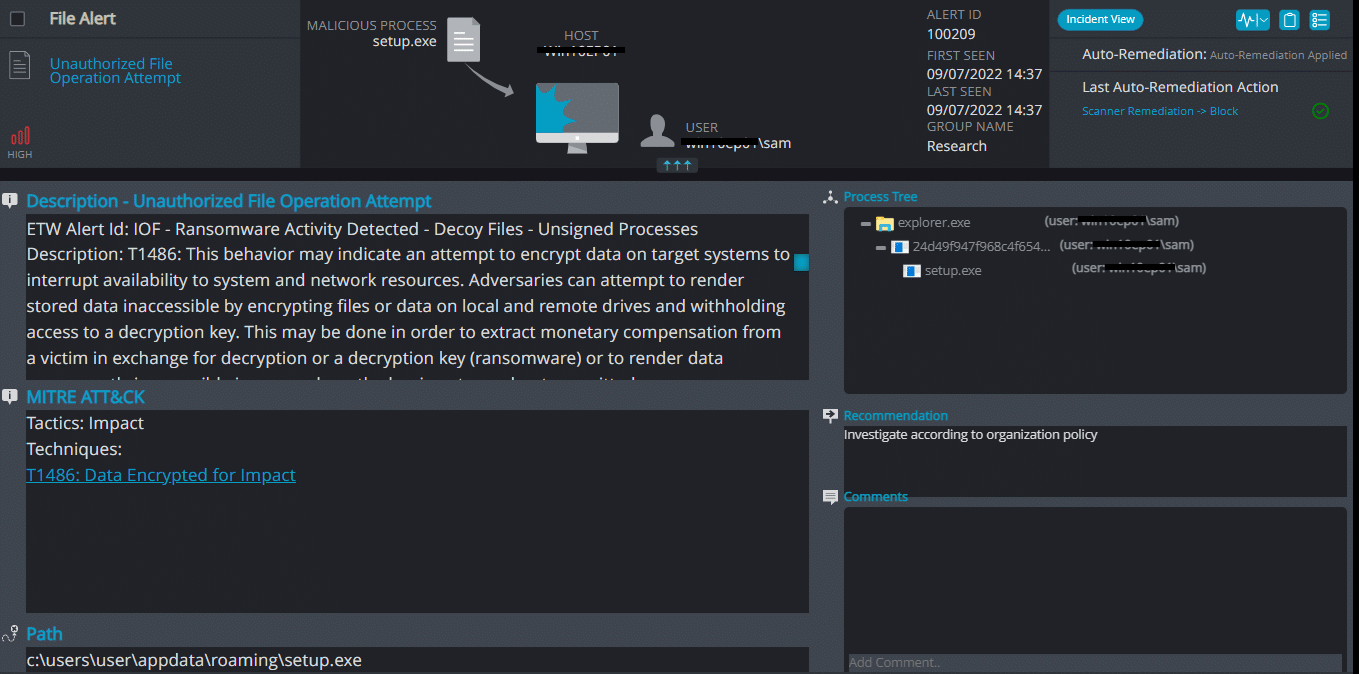
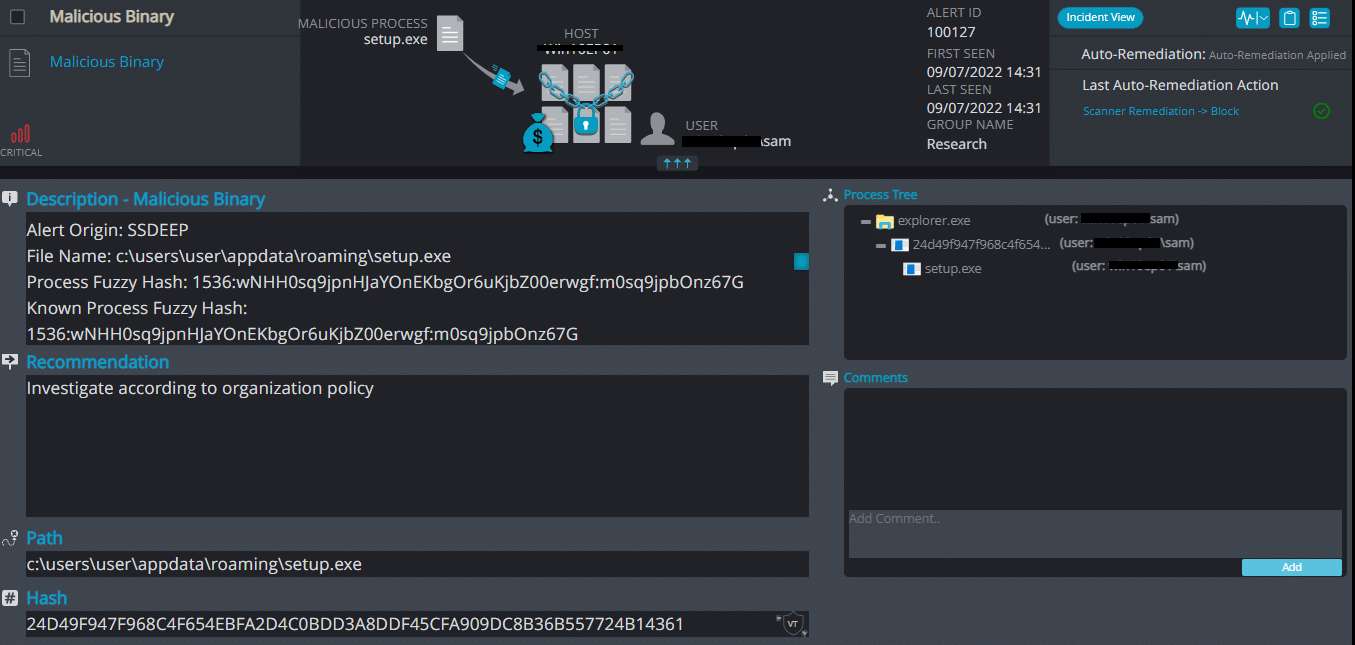
Hydrox ransomware renames the encrypted files with .hydrox in the extension:
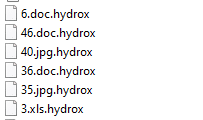
Once a computer’s files have been encrypted and renamed, it attempts to drop the ransomware note named Hydrox Ransomware:
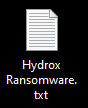
Ransomware note contains general information, warnings and no option whatsoever to decrypt the files:
The ransomware also changes the desktop background:

World2022decoding Ransomware
- Observed since: Aug 2022
- Ransomware encryption method: AES + RSA
- Ransomware extension: .world2022decoding
- Ransomware note: WE CAN RECOVER YOUR DATA.MHT
- Sample hash: 0737ddbd894f37316eee04c6739ac32f0c888535783a1af8c873023bcebbb8e8
Cynet 360 AutoXDR™ Detections:
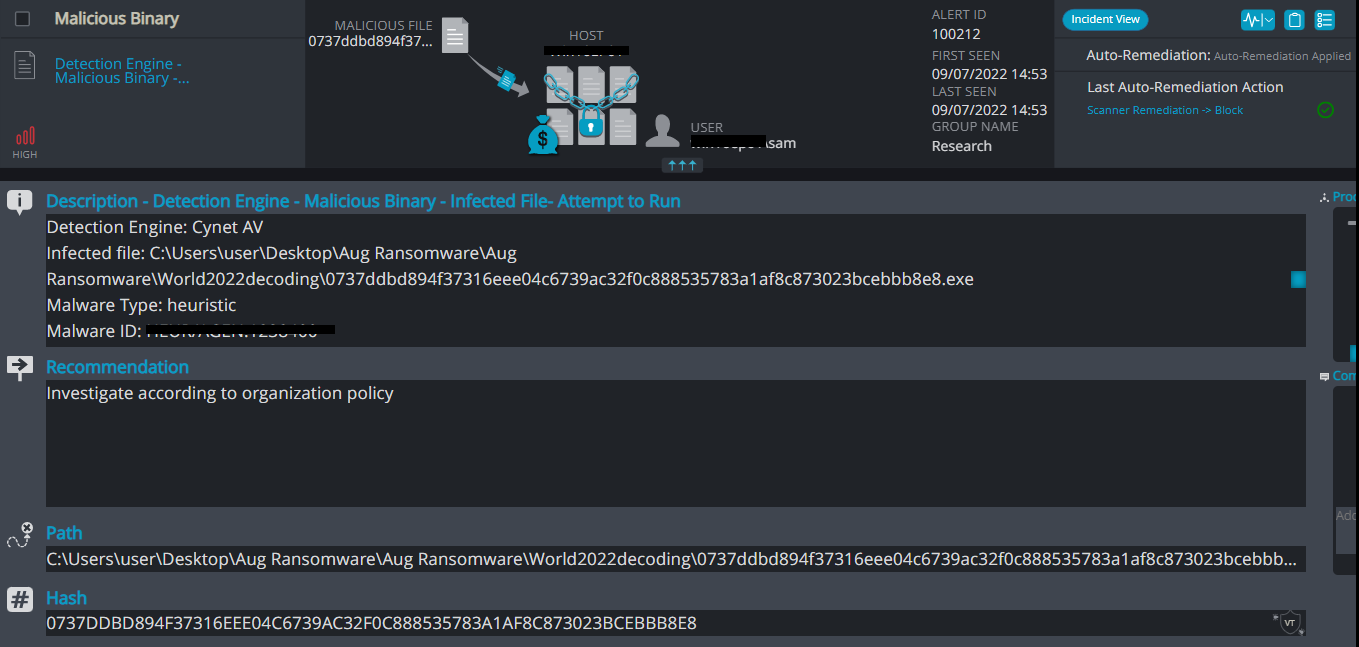
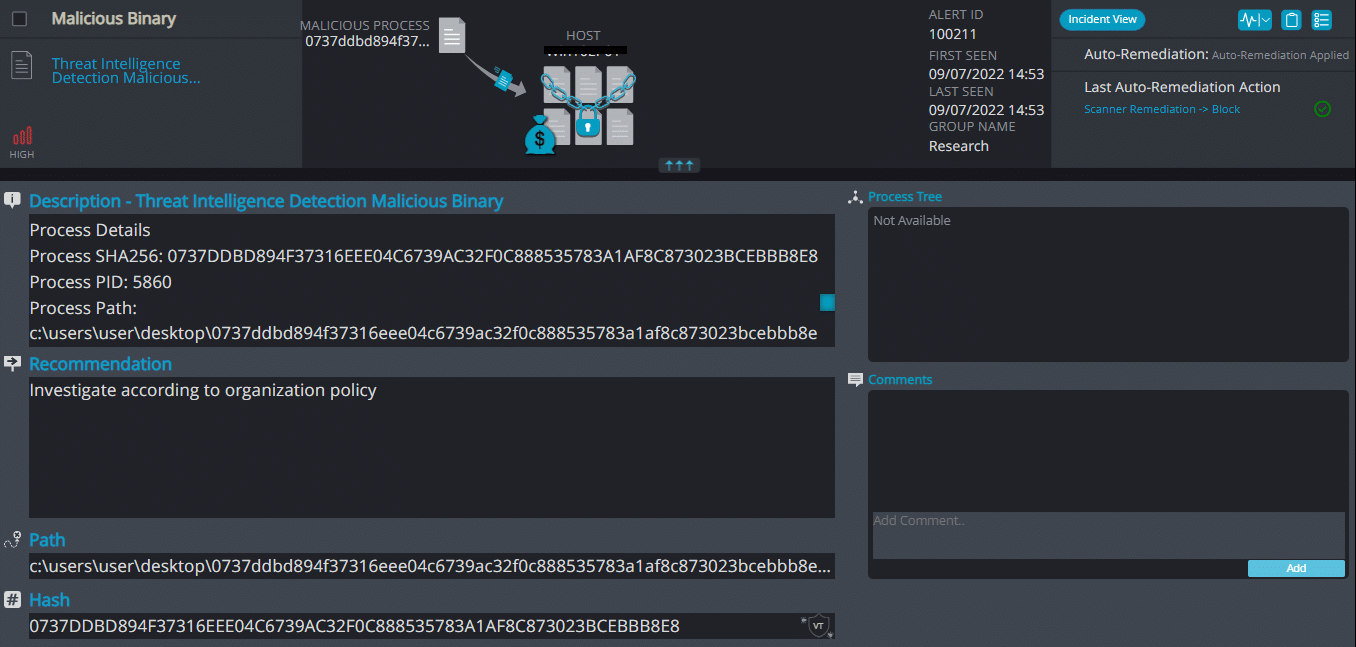
World2022decoding ransomware renames the encrypted files with .world2022decoding in the extension. Once a computer’s files have been encrypted and renamed, it drops a note named: WE CAN RECOVER YOUR DATA.MHT
Note: the ransomware was unable to encrypt the host and collapsed the machine. Therefore, no encryption was detected.
- Observed since: 2019
- Ransomware encryption method: AES + RSA
- Ransomware extension: .readlockfiles
- Ransomware note: HOW_TO_RECOVER_DATA.html
- Sample hash: e9df1201269429887bac3d2ae4069b7ac718306316853d2b3c7b2f4d4e92e09a
Cynet 360 AutoXDR™ Detections:
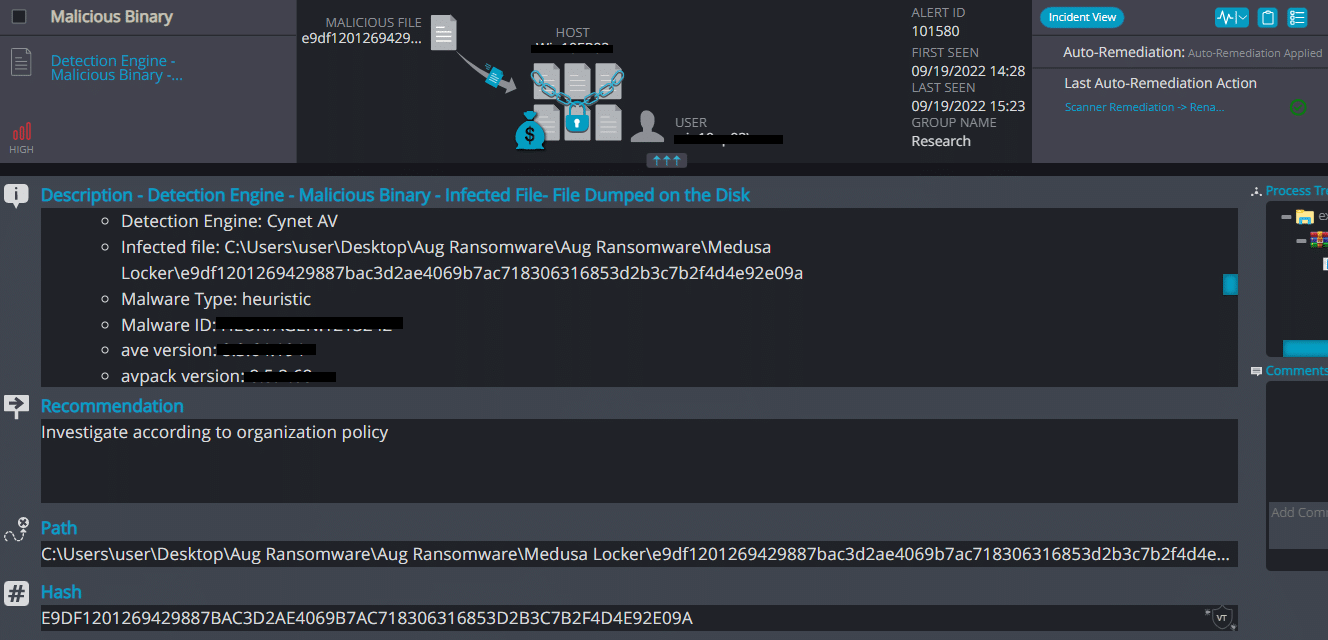
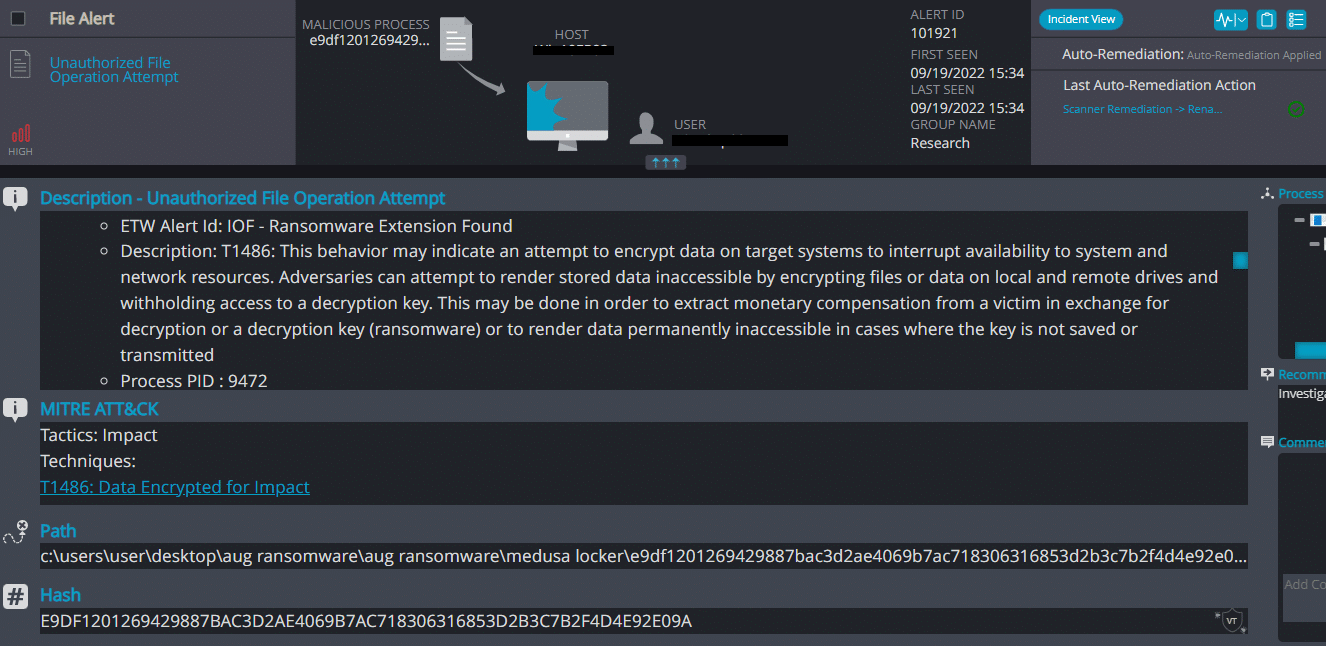
Medusa Locker ransomware renames the encrypted files with .readlockfiles in the extension:
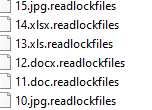
Once a computer’s files have been encrypted and renamed, it drops a note as: HOW_TO_RECOVER_DATA.html

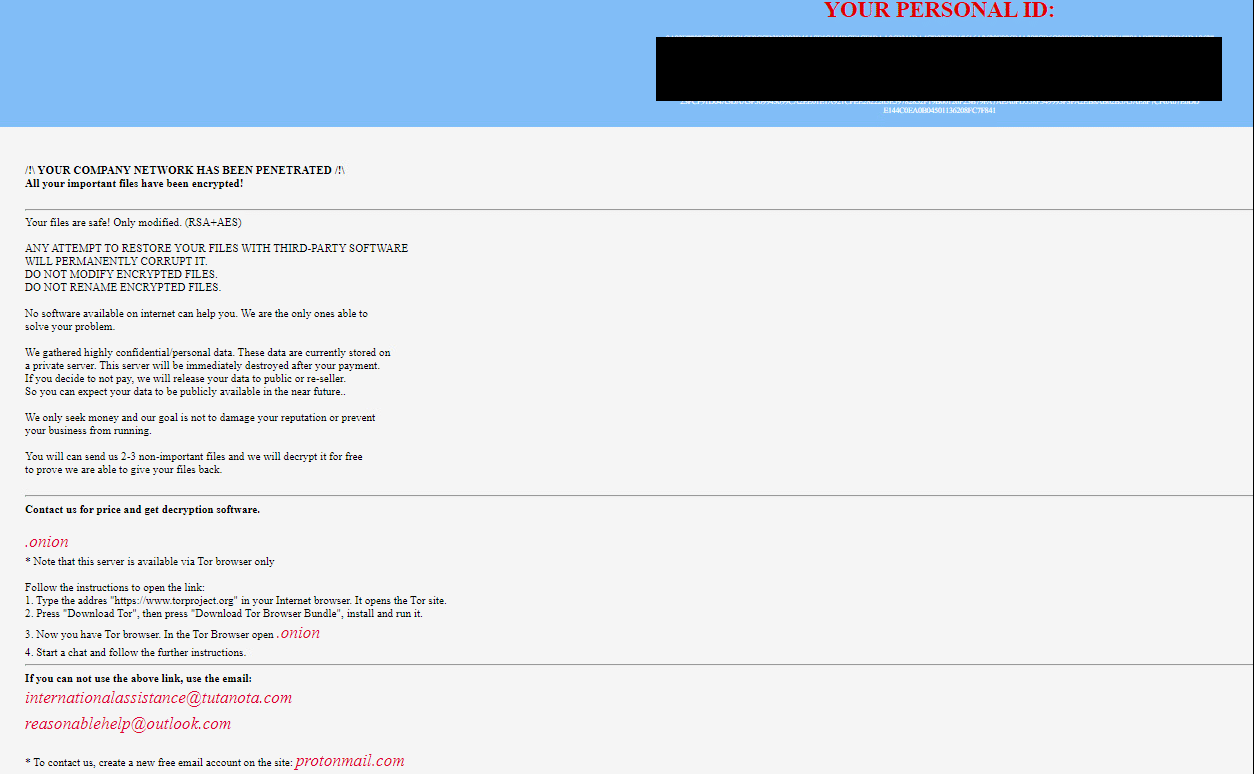
Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains general information, warnings and several attacker’s links:
VoidCrypt Ransomware
- Observed since: 2020
- Ransomware encryption method: AES + RSA
- Ransomware extension: .dark
- Ransomware note: unlock-info.txt
- Sample hash: 50586ef722c6a5c7b28d7b348dcf7003ea458bb1c3e659ddfb182be735daeb3d
Cynet 360 AutoXDR™ Detections:
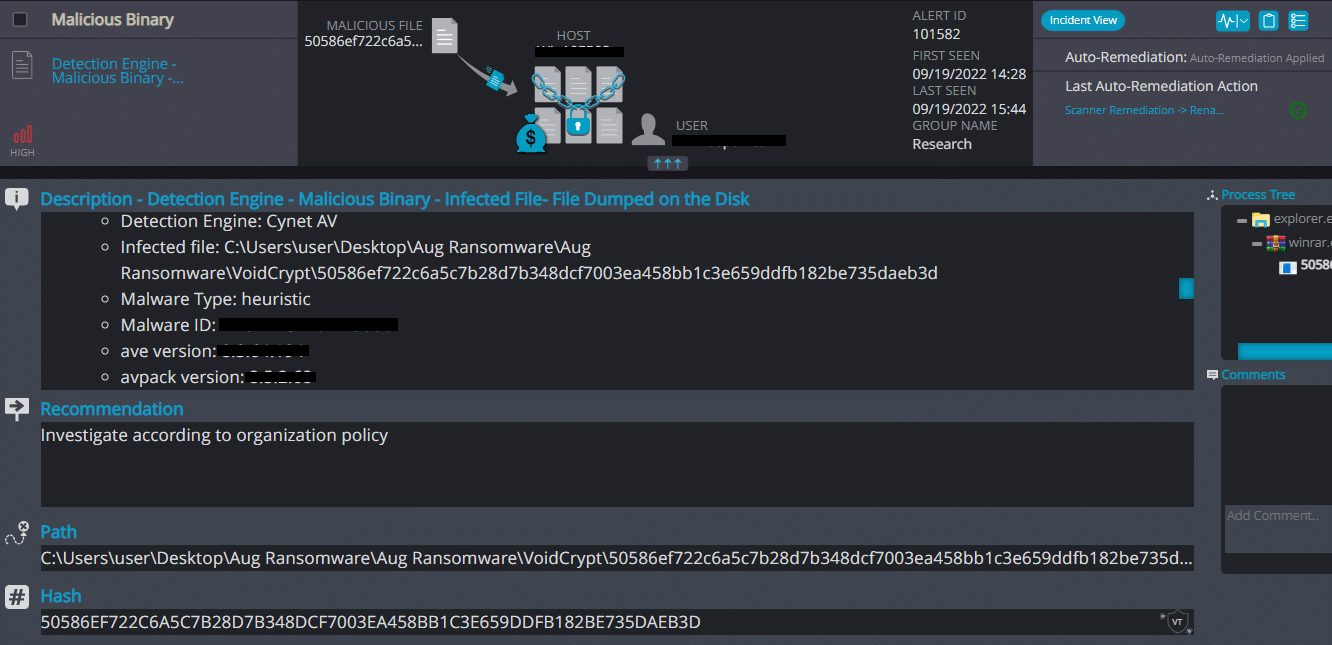
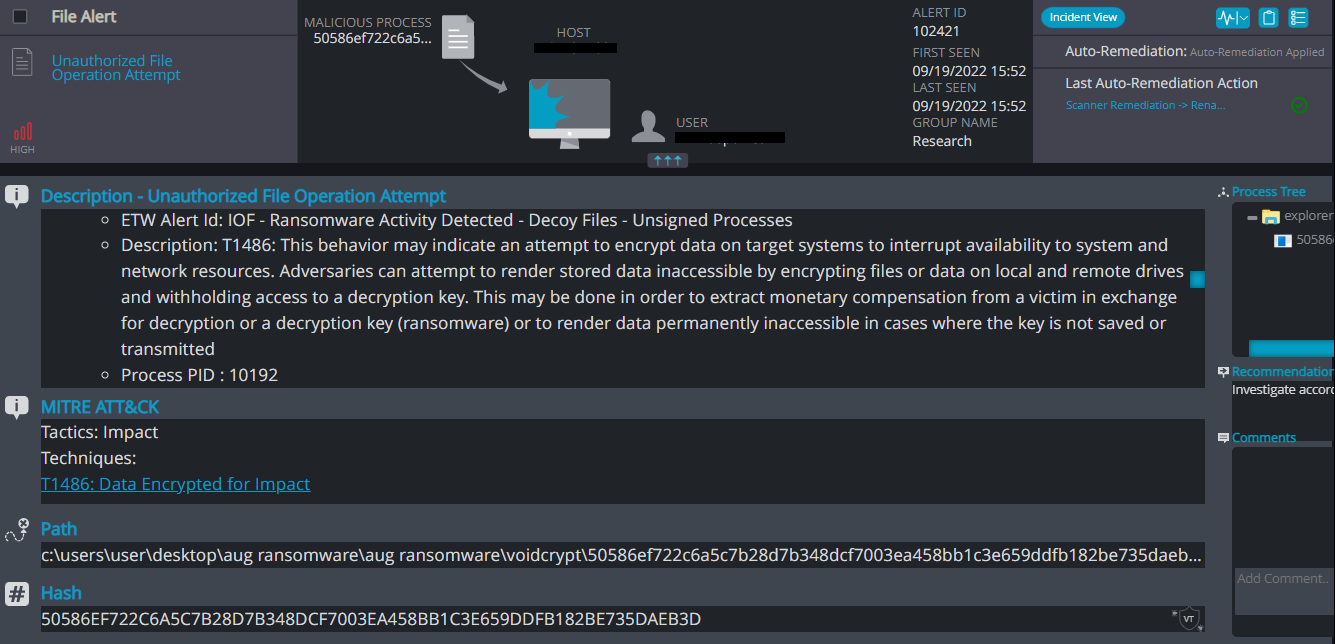
VoidCrypt Overview
VoidCrypt ransomware renames the encrypted files with .dark in the extension:
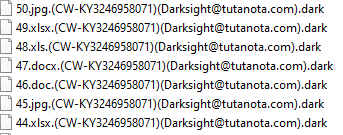
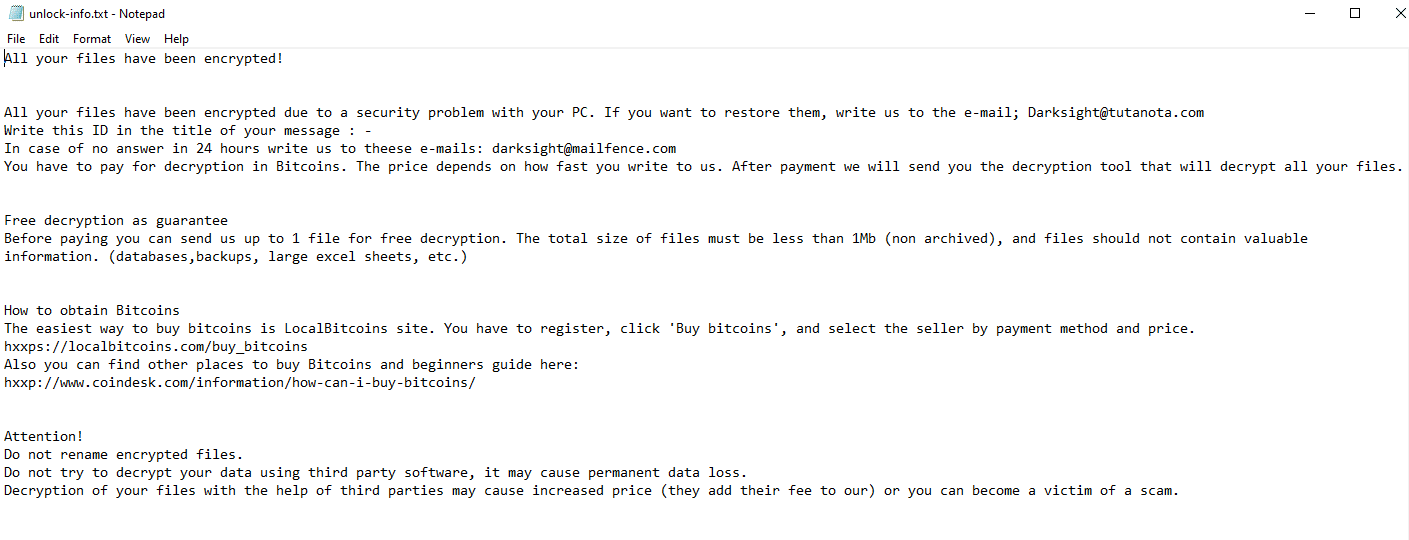
Once a computer’s files have been encrypted and renamed, it drops a note as unlock-info.txt:

Upon execution, it immediately encrypts the endpoint and drops the ransomware note. The ransomware note contains general information, warnings and the attacker’s email: