April 8, 2021
Last Updated:
November 20, 2024
What is an Incident Response Policy?
An Incident Response Policy is a critical document that outlines the structured approach an organization follows when responding to and managing a cyber security incident. This policy serves as a roadmap for the Incident Response Team, detailing the composition of the team, the specific responsibilities of each member, and the protocols for communicating during an incident. It specifies the strategies for utilizing tools and techniques to address and mitigate security breaches and establishes a clear chain of command, ensuring that there is no ambiguity about who is responsible for overseeing the enforcement of the policy.
By setting these guidelines, an organization ensures that it can react swiftly and effectively to security incidents, minimizing potential damage and facilitating a speedy recovery.
Phases of Incident Response Policy
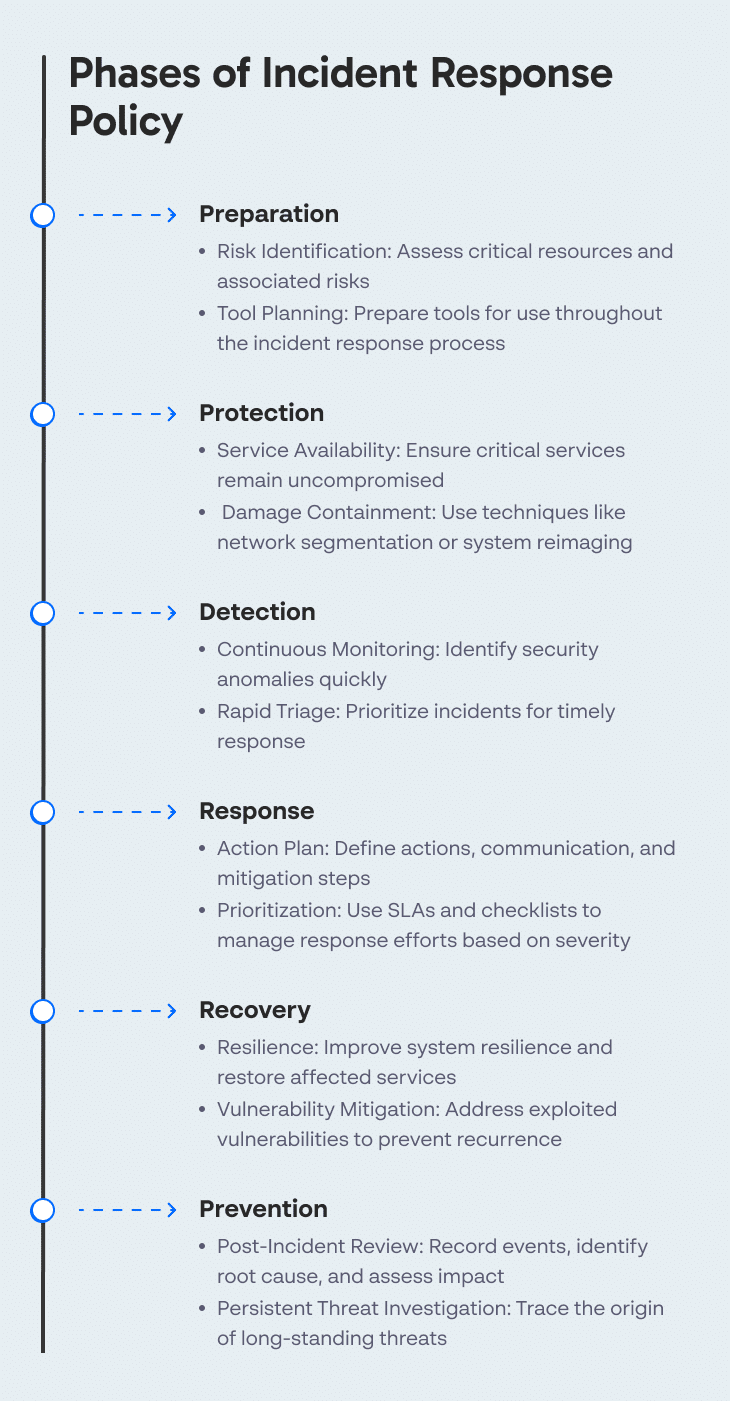
An incident response policy should cover at least the following six phases:
- Preparation—understanding the cybersecurity risks faced by the organization, by identifying critical resources that support business functions, and the cybersecurity risks that may affect them. Preparation also involves planning tools that can be used throughout the incident response process.
- Protection—effective steps that can be taken to ensure important services remain available and uncompromised, and contain the damage caused by a security incident, for example by using network segmentation or wiping and reimaging infected systems.
- Detection—steps to identify that a real security incident is taking place. The detection phase enables continuous security monitoring and ensures that anomalies can be rapidly identified and triaged.
- Response—actions the team will take when a cybersecurity incident is detected. This covers response planning, communication, analysis, and mitigation. An important part of the response phase is defining prioritization of security events, with a service level agreement (SLA) defining how fast a response is needed for each priority level. Another element is an incident response checklist which responders should follow for each type or priority level of events.
- Recovery—steps to prevent or minimize downtime of critical systems. The incident response policy should detail how to improve the resilience of systems, and restore functions or services affected by cybersecurity incidents. This includes identifying and mitigating any exploited vulnerabilities.
- Prevention—steps that should be taken after an incident, including recording events before and during the incident, identifying the root cause, and calculating the cost and other impacts of the incident on the organization. In the event of persistent threats, the investigation should go back to the time the threat is believed to have penetrated the organization.
Related content: read our guide to incident response process.
Tips for an Effective Incident Response Policy
The following tips will help you define a more effective incident response policy.
Update Policies Regularly
Incident response policies should be regularly revised to keep up with new cybersecurity technologies and techniques, and new threats facing the organization. The document should be general enough to cover all types of incidents the organization is likely to face. When a specific type of incident occurs, lessons learned from it should be added to the relevant part of the policy.
Involve Stakeholders in Planning
Successful creation and implementation of incident response strategies requires close collaboration between departments. Responding to large scale incidents, especially those with financial consequences, requires the involvement of legal teams, public relations, human relations, customer support, senior management, and more.
All relevant stakeholders—both internal and external—should participate in incident response policy planning. By allowing all stakeholders a say in the planning of the policy, you are more likely to capture the relevant steps to take in a real event, and ensure closer cooperation with stakeholders when a breach occurs.
Related content: read our guide to building an incident response team.
Continuously Monitor Performance
Use the following metrics to monitor the performance of your organization’s incident response team:
- Mean time to detection (MTTD) and mean time to remediation (MTTR)
- Number of incidents identified and closed in a certain timeframe
- Feedback provided by team members or customers (a qualitative indicator)
- Loss or damage caused by incidents over a certain timeframe
Incident Response Policy Q&A
What Is an Incident Response Plan?
An incident response plan sets up procedures to ensure early identification of incidents, and timely response, to prevent data breaches that can result in service outages, loss or theft of data, unauthorized access, or other damage.
Who Carries Out the Incident Response Plan?
Plans cannot be effective without dedicating personnel to execute them. In larger organizations, a dedicated Computer Security Incident Response Team (CSIRT) is set up, composed mainly of security staff and IT staff trained on the relevant skills. In smaller organizations, an incident response team can be assembled using part-time contribution from employees in other roles, often complemented by outsourced incident response vendors.
The response team is at the focus of an incident and communicates their findings, activities, and conclusions to legal, law and press agencies, other concerned stakeholders, and affected customers.
What Is an Incident Response Service?
An incident response service can assist an organization in detecting, responding, and mitigating cybersecurity threats. In its basic form, service providers are paid a retainer or per-incident fee, and respond to high-profile breaches within a timeframe dictated by a Service Level Agreement (SLA).
Incident response services can also address ongoing minor incidents, remove ransomware, malware, and the like, and hunt for existing or potential threats or vulnerabilities. Most providers follow through with post-breach investigations.
In my experience, here are tips that can help you better adapt to implementing an effective incident response policy:
- Define Escalation Criteria: Clearly specify what constitutes a minor versus a major incident and when to escalate to senior management, external vendors, or law enforcement.
- Address Legal and Regulatory Requirements: Ensure your policy aligns with local and international laws, including breach reporting procedures to regulators and affected parties.
- Account for Third-Party Risk: Define procedures for handling security incidents involving third-party vendors or partners.
- Establish a Decision-Making Framework: Prepare your leadership for tough decisions like ransomware negotiations or system shutdowns with a clear decision-making framework.
- Build Flexibility for Emerging Threats: Ensure your policy is adaptable to evolving threats and can be updated quickly to address new vulnerabilities or attack vectors.
Eyal Gruner is the Co-Founder and CEO of Cynet. He is also Co-Founder and former CEO of BugSec, Israel’s leading cyber consultancy, and Versafe, acquired by F5 Networks. Gruner began his career at age 15 by hacking into his bank’s ATM to show the weakness of their security and has been recognized in Google’s security Hall of Fame.
Automated Incident Response With Cynet
Incident Response Automation
Cynet provides a holistic solution for cybersecurity, including Cynet Response Orchestration which can automate your incident response policy. Users can define automated playbooks, with pre-set or custom remediation actions for multiple attack scenarios.
Cynet Response Orchestration can address any threat that involves infected endpoints, malicious processes or files, attacker-controlled network traffic, or compromised user accounts.
Learn more about Cynet Response Orchestration.
Incident Response Services
Cynet provides Incident Response (IR) services that add deep security experience to its world-class incident response platform. Cynet’s proactive 24/7 security team acts as your extended team, identifying incidents, leading any required analysis, and responding on your behalf. Our incident response services provide:
- Best of breed tech – delivers alerts and insights from endpoints, users and networks. Since everything is automated, we respond faster.
- Fast and scalable IR setup – no need for open source or manual tools. Our platform is easy to deploy, allowing for speed and scale across endpoints.
- Transparent incident response – dedicated IR project manager and point of contact.
- Customized reports – from executive summaries to detailed IoCs that can be exported to CSV for consumption by other systems.
Learn more about Cynet Incident Response Services.




